A Practical Introduction to Unix
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Brief Introduction to Unix-2019-AMS
Brief Intro to Linux/Unix Brief Intro to Unix (contd) A Brief Introduction to o Brief History of Unix o Compilers, Email, Text processing o Basics of a Unix session o Image Processing Linux/Unix – AMS 2019 o The Unix File System Pete Pokrandt o Working with Files and Directories o The vi editor UW-Madison AOS Systems Administrator o Your Environment [email protected] o Common Commands Twitter @PTH1 History of Unix History of Unix History of Unix o Created in 1969 by Kenneth Thompson and Dennis o Today – two main variants, but blended o It’s been around for a long time Ritchie at AT&T o Revised in-house until first public release 1977 o System V (Sun Solaris, SGI, Dec OSF1, AIX, o It was written by computer programmers for o 1977 – UC-Berkeley – Berkeley Software Distribution (BSD) linux) computer programmers o 1983 – Sun Workstations produced a Unix Workstation o BSD (Old SunOS, linux, Mac OSX/MacOS) o Case sensitive, mostly lowercase o AT&T unix -> System V abbreviations 1 Basics of a Unix Login Session Basics of a Unix Login Session Basics of a Unix Login Session o The Shell – the command line interface, o Features provided by the shell o Logging in to a unix session where you enter commands, etc n Create an environment that meets your needs n login: username n Some common shells n Write shell scripts (batch files) n password: tImpAw$ n Define command aliases (this Is my password At work $) Bourne Shell (sh) OR n Manipulate command history IHateHaving2changeMypasswordevery3weeks!!! C Shell (csh) n Automatically complete the command -

Student Number: Surname: Given Name
Computer Science 2211a Midterm Examination Sample Solutions 9 November 20XX 1 hour 40 minutes Student Number: Surname: Given name: Instructions/Notes: The examination has 35 questions on 9 pages, and a total of 110 marks. Put all answers on the question paper. This is a closed book exam. NO ELECTRONIC DEVICES OF ANY KIND ARE ALLOWED. 1. [4 marks] Which of the following Unix commands/utilities are filters? Correct answers are in blue. mkdir cd nl passwd grep cat chmod scriptfix mv 2. [1 mark] The Unix command echo HOME will print the contents of the environment variable whose name is HOME. True False 3. [1 mark] In C, the null character is another name for the null pointer. True False 4. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod a=x abc.dat is equivalent to the command: a. chmod 755 abc.dat b. chmod 711 abc.dat c. chmod 155 abc.dat d. chmod 111 abc.dat e. none of the above 5. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod ug+w abc.dat is equivalent to the command: a. chmod 766 abc.dat b. chmod 764 abc.dat c. chmod 754 abc.dat d. chmod 222 abc.dat e. none of the above 2 6. [3 marks] The protection code for def.dat is currently dr-xr--r-- , and the protection code for def.dat/ghi.dat is currently -r-xr--r-- . Give one or more chmod commands that will set the protections properly so that the owner of the two files will be able to delete ghi.dat using the command rm def.dat/ghi.dat chmod u+w def.dat or chmod –r u+w def.dat 7. -

Pingdirectory Administration Guide Version
Release 7.3.0.3 Server Administration Guide PingDirectory | Contents | ii Contents PingDirectory™ Product Documentation................................................ 20 Overview of the Server............................................................................. 20 Server Features.................................................................................................................................20 Administration Framework.................................................................................................................21 Server Tools Location....................................................................................................................... 22 Preparing Your Environment....................................................................22 Before You Begin.............................................................................................................................. 22 System requirements..............................................................................................................22 Installing Java......................................................................................................................... 23 Preparing the Operating System (Linux).......................................................................................... 24 Configuring the File Descriptor Limits.................................................................................... 24 File System Tuning.................................................................................................................25 -

Install and Run External Command Line Softwares
job monitor and control top: similar to windows task manager (space to refresh, q to exit) w: who is there ps: all running processes, PID, status, type ps -ef | grep yyin bg: move current process to background fg: move current process to foreground jobs: list running and suspended processes kill: kill processes kill pid (could find out using top or ps) 1 sort, cut, uniq, join, paste, sed, grep, awk, wc, diff, comm, cat All types of bioinformatics sequence analyses are essentially text processing. Unix Shell has the above commands that are very useful for processing texts and also allows the output from one command to be passed to another command as input using pipe (“|”). less cosmicRaw.txt | cut -f2,3,4,5,8,13 | awk '$5==22' | cut -f1 | sort -u | wc This makes the processing of files using Shell very convenient and very powerful: you do not need to write output to intermediate files or load all data into the memory. For example, combining different Unix commands for text processing is like passing an item through a manufacturing pipeline when you only care about the final product 2 Hands on example 1: cosmic mutation data - Go to UCSC genome browser website: http://genome.ucsc.edu/ - On the left, find the Downloads link - Click on Human - Click on Annotation database - Ctrl+f and then search “cosmic” - On “cosmic.txt.gz” right-click -> copy link address - Go to the terminal and wget the above link (middle click or Shift+Insert to paste what you copied) - Similarly, download the “cosmicRaw.txt.gz” file - Under your home, create a folder -

Manipulating Files and Directories
MANIPULATING FILES AND DIRECTORIES At this point, we are ready for some real work! This chapter will introduce the following commands: z cp—Copy files and directories. z mv—Move/rename files and directories. z mkdir—Create directories. z rm—Remove files and directories. z ln—Create hard and symbolic links. These five commands are among the most frequently used Linux com- mands. They are used for manipulating both files and directories. Now, to be frank, some of the tasks performed by these commands are more easily done with a graphical file manager. With a file manager, we can drag and drop a file from one directory to another, cut and paste files, delete files, and so on. So why use these old command-line programs? www.it-ebooks.info The answer is power and flexibility. While it is easy to perform simple file manipulations with a graphical file manager, complicated tasks can be easier with the command-line programs. For example, how could we copy all the HTML files from one directory to another—but only those that do not exist in the destination directory or are newer than the versions in the destination directory? Pretty hard with a file manager. Pretty easy with the command line: cp -u *.html destination Wildcards Before we begin using our commands, we need to talk about the shell fea- ture that makes these commands so powerful. Because the shell uses file- names so much, it provides special characters to help you rapidly specify groups of filenames. These special characters are called wildcards. -
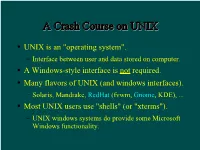
A Crash Course on UNIX
AA CCrraasshh CCoouurrssee oonn UUNNIIXX UNIX is an "operating system". Interface between user and data stored on computer. A Windows-style interface is not required. Many flavors of UNIX (and windows interfaces). Solaris, Mandrake, RedHat (fvwm, Gnome, KDE), ... Most UNIX users use "shells" (or "xterms"). UNIX windows systems do provide some Microsoft Windows functionality. TThhee SShheellll A shell is a command-line interface to UNIX. Also many flavors, e.g. sh, bash, csh, tcsh. The shell provides commands and functionality beyond the basic UNIX tools. E.g., wildcards, shell variables, loop control, etc. For this tutorial, examples use tcsh in RedHat Linux running Gnome. Differences are minor for the most part... BBaassiicc CCoommmmaannddss You need these to survive: ls, cd, cp, mkdir, mv. Typically these are UNIX (not shell) commands. They are actually programs that someone has written. Most commands such as these accept (or require) "arguments". E.g. ls -a [show all files, incl. "dot files"] mkdir ASTR688 [create a directory] cp myfile backup [copy a file] See the handout for a list of more commands. AA WWoorrdd AAbboouutt DDiirreeccttoorriieess Use cd to change directories. By default you start in your home directory. E.g. /home/dcr Handy abbreviations: Home directory: ~ Someone else's home directory: ~user Current directory: . Parent directory: .. SShhoorrttccuuttss To return to your home directory: cd To return to the previous directory: cd - In tcsh, with filename completion (on by default): Press TAB to complete filenames as you type. Press Ctrl-D to print a list of filenames matching what you have typed so far. Completion works with commands and variables too! Use ↑, ↓, Ctrl-A, & Ctrl-E to edit previous lines. -

Great Lakes Cheat Sheet Less File Prints Content of File Page by Page Guide to General L Inux (Bash) a Nd S Lurm C Ommands Head File Print First 10 Lines of File
Viewing and editing text files cat file Print entire content of file Great Lakes Cheat Sheet less file Prints content of file page by page Guide to general L inux (Bash) and S lurm c ommands head file Print first 10 lines of file tail file Print last 10 lines of file Accessing Great Lakes nano Simple, easy to use text editor Logging in from a terminal (Duo required) vim Minimalist yet powerful text editor ssh uniqname @greatlakes.arc-ts.umich.edu emacs Extensible and customizable text editor Transferring files between Great Lakes and your system scp input uniqname@ greatlakes-xfer.arc-ts.umich.edu: output Advanced file management scp -r i nput uniqname@ greatlakes-xfer.arc-ts.umich.edu:o utput scp uniqname@ greatlakes-xfer.arc-ts.umich.edu:i nput output chmod Change read/write/execute permissions which cmd List the full file path of a command GUI Clients PuTTY SSH client for Windows whereis cmd List all related file paths (binary, source, manual, etc.) of a command WinSCP SCP client for Windows du dir List size of directory and its subdirectories FileZilla FTP client for Windows, Mac, and Linux find Find file in a directory Basic Linux file management Aliases and system variables man command Display the manual page for command alias Create shortcut to command pwd Print out the present working directory env Lists all environment variables ls List the files in the current directory export var = val Create environment variable $ var with value ls -lh Show long, human-readable listing val ls dir List files inside directory dir echo $var Print the value of variable $var rm file Delete file .bashrc File that defines user aliases and variables mkdir dir Create empty directory called dir Input and output redirection rmdir dir Remove empty directory dir $( command) Runs command first, then inserts output to the rm -r dir Remove directory dir and all contents rest of the overall command cd dir Change working directory to dir < Standard input redirection cd . -

Cloud Computing and Unix: an Introduction
Cloud Computing and Unix: An Introduction Dr. Sophie Shaw University of Aberdeen, UK [email protected] Aberdeen London Exeter What We’re Going To Do • Why Unix? • Cloud Computing • Connecting to AWS • Introduction to Unix Commands Etiquette • PowerPoint interspersed with Challenges • Ask me questions • Ask demonstrators • Work together • Cheat! What is Unix? • Operating System Why Unix? • Bioinformatics software designed to run on Unix platforms. • Large amounts of data. • Much faster than your Windows PC. How Can We Use Unix? • Linux computers or servers. • Compute clusters. • The cloud. – What we’re going to use this week So What is Cloud Computing? Cloud Computing Solutions AWS “Availability Zones” and Data Centres How it Works AMI (“Amazon Machine Image”) Base computer with all data and software How it Works Own copy of the AMI = Instance (Virtual Machine or VM) Terminology • Creating an instance – buying a brand new computer with software already installed. • Starting an instance – turning that computer on. • Stopping an instance – turning that computer off. • Terminating an instance – setting that computer on fire and throwing it out of the window. The Rules • Only create one instance each. • Stop your instance at the end of each day (unless you have software running). • Name your instance (with YOUR name! No Bruce Waynes please) • Only start or stop your own instance. • Only terminate your own instance. Connecting to Your Instance Remote Desktop Secure Shell – Software “SSH” e.g. X2Go e.g. SSH or PuTTY Now What?! • You’re each going -

CS160A EXERCISES-FILEUTILS2 Boyd
CS160A EXERCISES-FILEUTILS2 Boyd Exercises-Fileutils2 Part One Description In this exercise set you will practice the mv command. mv is used to rename and rearrange files and directories. Begin by creating a directory to work in beneath your home directory on hills. (This is your work area for this exercise). Here are the forms of the mv command: Synopsis Meaning mv file1 file2 file2 is deleted if it exists. Then file1 is renamed file2 mv a [b c ...] dir move one or more existing files or directories into an existing a,b,c,... can be files or directories directory. If a directory is moved, everything beneath it goes with it,. mv dir1 dir2 if dir2 does not exist, rename dir1 to dir2. If dir2 exists, this is the previous form, and dir1 is moved into dir2 other options -i - interactive copy. Asks for verification for each individual copy operation before proceeding -v: verbose. Reports each individual copy operation as it is done. Procedure In this part you create a directory structure by taking parts from an existing directory. Begin by getting a copy of the existing directory structure by copying (recursively) the directory located at fileutils/test beneath the class public data area on hills to your work area. You should begin by examining the test structure and perhaps making a drawing of it. Then make a new directory test1 in your work area and connect to it. (Note: test1 and your copy of test are assumed to be at the same level (i.e., they are both in the same directory) 1. -

Standard TECO (Text Editor and Corrector)
Standard TECO TextEditor and Corrector for the VAX, PDP-11, PDP-10, and PDP-8 May 1990 This manual was updated for the online version only in May 1990. User’s Guide and Language Reference Manual TECO-32 Version 40 TECO-11 Version 40 TECO-10 Version 3 TECO-8 Version 7 This manual describes the TECO Text Editor and COrrector. It includes a description for the novice user and an in-depth discussion of all available commands for more advanced users. General permission to copy or modify, but not for profit, is hereby granted, provided that the copyright notice is included and reference made to the fact that reproduction privileges were granted by the TECO SIG. © Digital Equipment Corporation 1979, 1985, 1990 TECO SIG. All Rights Reserved. This document was prepared using DECdocument, Version 3.3-1b. Contents Preface ............................................................ xvii Introduction ........................................................ xix Preface to the May 1985 edition ...................................... xxiii Preface to the May 1990 edition ...................................... xxv 1 Basics of TECO 1.1 Using TECO ................................................ 1–1 1.2 Data Structure Fundamentals . ................................ 1–2 1.3 File Selection Commands ...................................... 1–3 1.3.1 Simplified File Selection .................................... 1–3 1.3.2 Input File Specification (ER command) . ....................... 1–4 1.3.3 Output File Specification (EW command) ...................... 1–4 1.3.4 Closing Files (EX command) ................................ 1–5 1.4 Input and Output Commands . ................................ 1–5 1.5 Pointer Positioning Commands . ................................ 1–5 1.6 Type-Out Commands . ........................................ 1–6 1.6.1 Immediate Inspection Commands [not in TECO-10] .............. 1–7 1.7 Text Modification Commands . ................................ 1–7 1.8 Search Commands . -

MV-1 DOR Motor Vehicle Title/Tag
MV-1 (Revised 6-2020) Georgia Department of Revenue - Motor Vehicle Division Form MV-1 Motor Vehicle Title Application For instructions on how to complete this form see page 2. A VEHICLE INFORMATION Vehicle ID (VIN): _____________________________ Current Title #: _________________________ _ Year: ______ _ Make: _____________________________ Current Title’s State of Issue: _______________ _ Color: ______ _ Model: _____________________________ GA County of Residence: ________________ _ Cylinders: ______ _ Body Style: _____________________________ District #: __________________________ __ Fuel Type: ______ _ Odometer Exceptions: EXEMPT Exceeds Mechanical Limits of Odometer Not the Actual Mileage, Warning Odometer Discrepancy Odometer Reading: _____________________________ Date Purchased: _____________________________ COMPLETE FOR ALL COMMERCIAL VEHICLES Gross Vehicle Weight & Load: __________________________ Straight Truck? Yes No Used for Hire? Yes No Type of Trailer Pulled? _____________________ Product Hauled? ____________________ Is this a Farm Vehicle? Yes No B OWNER INFORMATION Number of Owners: _______ Leased Vehicle: No Yes (If yes, complete Section D) If purchased from an out-of-state business, did you pick up the vehicle out of state? Yes No *Owner’s signature below warrants: I do solemnly swear or affirm under criminal penalty of a felony for fraudulent use of a false or fictitious name or address or for making a material false statement punishable by fine up to $5,000 or by imprisonment of up to five years, or both that the statements -

Midterm Test #1 − 10% Ian! D
45 M/C Questions -1- 45 minutes 45 M/C Questions -2- 45 minutes 6. [66/167] If mt is an empty sub-directory,what is true after this: PRINT Name: LAB Section: touch bar ; mkdir foo ; mv bar mt/foo Test Version: ___ One-Answer Multiple Choice 45 Questions − 10 of 10% a. the directory foo nowcontains a file named bar the directory mt nowcontains a file named foo ☞ b. Read all the words of these instructions and both sides (back and front) of all pages. c. the directory mt nowcontains a file named bar ☞ Manage your time. Answer questions you know, first. One Answer per question. d. the command fails because mt/foo is not a directory ☞ Put your Name and Lab on this Question Sheet. Youmay write or drawonthis sheet. e. the directory mt is still empty ☞ Use your full, unabbreviated name on the mark-sense form. Do not abbreviate your name. ☞ Put the three-digit Test Version above into NO. OF QUESTIONS and NO. OF STUDENTS 7. [67/168] What is the output of this in an empty directory: ☞ Fill in the bubbles with pencil only,nopen. Enter your NAME, Test Version, and answers. touch 1 13 .13 2 213 3 30 31 .31 ; echo [13]* ☞ Taip The answer to the last question about reading/doing all these test instructions is: a. 13 b. an error message from echo saying [13]* does not exist c. [13]* 1. [49/169] If file foo contains 8 lines, and file bar contains 9 lines, then how manylines are output on your screen by this: cat bar | echo foo d.