Automating Isolation and Least Privilege in Web Services
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Modelagem E Simulação Discreta
Versão 12/05/2021 Brauliro G Leal Modelagem e Simulação Discreta Quarta Edição Juazeiro – BA 2021 Modelagem e Simulação Discreta 2 Copyright© 2016, 2017, 2018, 2019, 2020, 2021 by Brauliro Gonçalves Leal O conteúdo deste livro eletrônico é livre para uso de qualquer natureza desde que citado a fonte. Toda e qualquer parte desta publicação pode ser reproduzida, distribuída ou transmitida de qualquer forma ou por qualquer meio, ou armazenada de qualquer forma ou em qualquer sistema desde que reconhecida a autoria. Atribuição-CompartilhaIgual – esta licença permite que outros remixem, adaptem e criem a partir deste trabalho, mesmo para fins comerciais, desde que lhe atribuam o devido crédito e que licenciem as novas criações sob termos idênticos (creativecommons.org/licenses). e-mail: [email protected] Quarta Edição Eletrônica: maio de 2021 ISBN: a ser feito# O autor Brauliro Gonçalves Leal Professor do Colegiado de Engenharia da Computação Universidade Federal do Vale do São Francisco Avenida Antônio Carlos Magalhães, 510 Santo Antônio Juazeiro/BA – Brasil 48.902-300 e-mail: [email protected] site: www.univasf.edu.br/~brauliro.leal Sobre este documento Este documento foi escrito em LibreOffice (www.libreoffice.org), suas imagens foram produzidas pelo Kolourpaint (www.kolourpaint.org), seus programas foram editados na IDE Code::Blocks (www.codeblocks.org) e compilados com o GNU GCC (gcc.gnu.org). O Sistema Operacional utilizado foi o GNU/Linux Mint Cinnamon. Software livre é a melhor ideia! Modelagem e Simulação Discreta 3 Pois o conforto intelectual e o hábito têm horror das mensagens que os incomodam. Edgar Morin (Le Monde: 20 de abril de 2020) Modelagem e Simulação Discreta 4 Modelagem e Simulação Discreta Prefácio O objetivo principal deste livro é servir de texto para a disciplina Modelagem e Simulação do curso de Engenharia da Computação do Colegiado de Engenharia da Computação da Universidade Federal do Vale do São Francisco. -

TIBCO Iprocess Objects Server Administrator's Guide
TIBCO iProcess® Objects Server Administrator’s Guide Software Release 11.4 July 2013 Two-Second Advantage® Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN THE LICENSE FILE) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. This document contains confidential information that is subject to U.S. and international copyright laws and treaties. No part of this document may be reproduced in any form without the written authorization of TIBCO Software Inc. TIBCO, Two-Second Advantage, TIBCO ActiveMatrix BusinessWorks, TIBCO Business Studio, TIBCO Enterprise Message Service, TIBCO Hawk, TIBCO iProcess, TIBCO iProcess Suite, and TIBCO Rendezvous are either registered trademarks or trademarks of TIBCO Software Inc. in the United States and/or other countries. -

Java Auto Grader Santhoshini Rao Chakrapani Governors State University
Governors State University OPUS Open Portal to University Scholarship All Capstone Projects Student Capstone Projects Spring 2016 Java Auto Grader Santhoshini Rao Chakrapani Governors State University Vasu Babu Dodda Governors State University Sharat Kumar Vasa Governors State University Follow this and additional works at: http://opus.govst.edu/capstones Part of the Computer Sciences Commons Recommended Citation Chakrapani, Santhoshini Rao; Dodda, Vasu Babu; and Vasa, Sharat Kumar, "Java Auto Grader" (2016). All Capstone Projects. 201. http://opus.govst.edu/capstones/201 For more information about the academic degree, extended learning, and certificate programs of Governors State University, go to http://www.govst.edu/Academics/Degree_Programs_and_Certifications/ Visit the Governors State Computer Science Department This Project Summary is brought to you for free and open access by the Student Capstone Projects at OPUS Open Portal to University Scholarship. It has been accepted for inclusion in All Capstone Projects by an authorized administrator of OPUS Open Portal to University Scholarship. For more information, please contact [email protected]. Abstract The aim of the project is to develop a “Java Automatic Grader” for java project assignment. It ensures that every assignment or work given to the students is done in the right way. The student should get automatic evaluation after submitting the assignment. We are implementing each test case in such a way that student should only get marks for satisfying all the requirements of the project assignment in fruitful manner i.e. If the student submits the assignment by reaching all the requirements and the expected result is achieved in the right way, then only the student will get full marks. -

Middleware to Integrate Heterogeneous Learning Management Systems and Initial Results
(IJACSA) International Journal of Advanced Computer Science and Applications, Vol. 5, No. 10, 2014 Middleware to integrate heterogeneous Learning Management Systems and initial results J.A. Hijar Miranda Daniel Vazquez´ Sanchez´ Dario Emmanuel Vazquez´ Ceballos Instituto Politecnico´ Nacional Instituto Politecnico´ Nacional Instituto Politecnico´ Nacional SEPI-ESCOM SEPI-ESCOM SEPI-ESCOM Mexico´ D.F. Mexico´ D.F. Mexico´ D.F. Erika Hernandez´ Rubio Amilcar Meneses Viveros Elena Fabiola Ruiz Ledezma Instituto Politecnico´ Nacional Departamento de Computacion´ Instituto Politecnico´ Nacional SEPI-ESCOM CINVESTAV-IPN SEPI-ESCOM Mexico´ D.F. Mexico´ D.F. Mexico´ D.F. Abstract—The use of the Learning Management Systems The report [1], also indicates that mobile devices are being (LMS) has been increased. It is desirable to access multiple adopted in education as means of access to online courses. learning objects that are managed by Learning Management When trying to access the LMS from a tablet, there are several Systems. The diversity of LMS allow us to consider them as issues. These issues include: poor usability user interfaces heterogeneous systems; each ones with their own interface to to access unsuitable for tablet; the diversity of mechanisms manage the provided functionality. These interfaces can be Web of interaction via internet; heterogeneity of the features of services or calls to remote objects. The functionalities offered by LMS depend on their user roles. A solution to integrate diverse the LMS, and the type of Application Programming Interface heterogeneous platforms is based on a middleware architecture. (API) offered. In this paper, a middleware architecture is presented to inte- Some studies suggest using a repository of learning objects grate different Learning Management Systems. -

Efficient RDF Storage and Retrieval in Jena2
Efficient RDF Storage and Retrieval in Jena2 Kevin Wilkinson1, Craig Sayers1, Harumi Kuno1, Dave Reynolds2 HP Laboratories 1 1501 Page Mill Road Palo Alto, CA, 94304 USA 2 Filton Road, Stoke Gifford Bristol BS34 8QZ United Kingdom [email protected] Abstract. RDF and related Semantic Web technologies have been the recent focus of much research activity. This work has led to new specifications for RDF and OWL. However, efficient implementations of these standards are needed to realize the vision of a world-wide semantic Web. In particular, implementations that scale to large, enterprise-class data sets are required. Jena2 is the second generation of Jena, a leading semantic web programmers’ toolkit. This paper describes the persistence subsystem of Jena2 which is intended to support large datasets. This paper describes its features, the changes from Jena1, relevant details of the implementation and performance tuning issues. Query optimization for RDF is identified as a promising area for future research. 1.0 Introduction Jena is a leading Semantic Web programmers’ toolkit[1]. It is an open-source project, implemented in Java, and available for download from SourceForge. Jena offers a simple abstraction of the RDF graph as its central internal interface. This is used uniformly for graph implementations, including in-memory, database-backed, and inferred graphs. Jena2 is the second generation of the Jena toolkit. It conforms to the revised RDF specification, has new capabilities and a new internal architecture. A design principle for Jena2 was to minimize changes to the API. This simplifies migration from Jena1 to Jena2. This paper describes Jena2 persistent storage; details on other aspects of Jena2 are available in [2]. -

Estudio De Factibilidad Para La Implementación De La
UNIVERSIDAD DE EL SALVADOR FACULTAD DE CIENCIAS ECONÓMICAS MAESTRÍA EN ADMINISTRACIÓN FINANCIERA “ESTUDIO DE FACTIBILIDAD PARA LA IMPLEMENTACIÓN DE LA MAESTRÍA EN ADMINISTRACIÓN FINANCIERA DE LA UNIVERSIDAD DE EL SALVADOR EN MODALIDAD SEMI PRESENCIAL (BLENDED LEARNING)” TRABAJO DE GRADUACIÓN PRESENTADO POR: LIC. GÁLVEZ RIVERA, RONALD EDGARDO INGA. PONCE HERNÁNDEZ, ILIANA ISABEL PARA OPTAR AL GRADO DE MAESTRO (A) EN ADMINISTRACIÓN FINANCIERA ENERO DE 2015 CIUDAD UNIVERSITARIA, SAN SALVADOR, EL SALVADOR, CENTROAMÉRICA UNIVERSIDAD DE EL SALVADOR AUTORIDADES UNIVERSITARIAS RECTOR : ING. MARIO ROBERTO NIETO LOVO SECRETARIO GENERAL: DRA. ANA LETICIA ZAVALETA DE AYALA AUTORIDADES DE LA FACULTAD DE CIENCIAS ECONÓMICAS DECANO : M.Sc. ROGER ARMANDO ÁRIAS ÁLVARADO VICEDECANO : LIC. ÁLVARO EDGARDO CALERO SECRETARIO : M.Sc. JOSÉ CIRIACO GUTIÉRREZ ADMINISTRADOR ACADÉMICO: DIRECTOR DE LA MAESTRÍA:M.Sc. CARLOS ALVARENGA BARRERA ASESORA : MAF. DAISY BEATRIZ DE MUÑOZ ENERO 2015 CIUDAD UNIVERSITARIA, SAN SALVADOR, EL SALVADOR, CENTROAMÉRICA RESUMEN EJECUTIVO La educación es un proceso dinámico, no puede aferrarse a esquemas preestablecidos y suponer que permanecerán válidos para siempre, a medida que se descubre nuevo conocimiento, debe procurarse la adopción en los procesos de enseñanza-aprendizaje, esto conllevará a elevar la calidad del desempeño laboral de los nuevos profesionales, y principalmente contribuye a mejorar las condiciones de un país. Los avances en las Tecnologías de Información y Comunicación (TIC´s), están contribuyendo grandemente para -

SWAD Is Free Software Since 2010 Swad-Core Swadroid
18 YEARS OF DEVELOPMENT AND USE OF THE SWAD EDUCATIONAL PLATFORM Antonio Cañas1,2, Daniel J. Calandria2, Juan M. Boyero2, Eva M. Ortigosa1,2, Javier Fernández1,2, Francisco A. Ocaña3 1Department of Computer Architecture and Technology, University of Granada (SPAIN), 2OpenSWAD Association (SPAIN) 3Department of Statistics and Operations Research, University of Granada (SPAIN) SWAD is a free-software educational web platform to support face-to-face or blended learning, including course information, syllabus, calendar, documents, shared files, portfolio, grades, assignments, projects, quizzes, surveys, games, exam announcements, groups, lists of students and teachers, attendance control using QR codes, social network, forums, notifications, notices, messaging system, statistics, agenda and preferences. Some of these features are also available as an m-learning app for Android: SWADroid. SWAD has been developed from scratch and used at the University of Granada, UGR (SPAIN) since 1999. It was released as free software in 2010. Since 2012 it is also available free of charge in the OpenSWAD.org portal without the need for local installation. swad.ugr.es January 2005 - November 2017 � 437.1 million clicks (page views) � 352 � 23 � 61 � 0.8 million million million million (81%) (5%) (14%) (<1%) students teachers others admins Page views and unique users per week in SWAD- UGR from 2005 to 2017 In 2015, the UGR decided to bet on another 177,570 platform as the only official. This is the cause of users have logged in the decline of SWAD-UGR in -

TIBCO Iprocess Objects Server Administrator,Aos Guide
TIBCO iProcess® Objects Server Administrator’s Guide Software Release 11.5 April 2015 Two-Second Advantage® Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO SOFTWARE IS SOLELY TO ENABLE THE FUNCTIONALITY (OR PROVIDE LIMITED ADD-ON FUNCTIONALITY) OF THE LICENSED TIBCO SOFTWARE. THE EMBEDDED OR BUNDLED SOFTWARE IS NOT LICENSED TO BE USED OR ACCESSED BY ANY OTHER TIBCO SOFTWARE OR FOR ANY OTHER PURPOSE. USE OF TIBCO SOFTWARE AND THIS DOCUMENT IS SUBJECT TO THE TERMS AND CONDITIONS OF A LICENSE AGREEMENT FOUND IN EITHER A SEPARATELY EXECUTED SOFTWARE LICENSE AGREEMENT, OR, IF THERE IS NO SUCH SEPARATE AGREEMENT, THE CLICKWRAP END USER LICENSE AGREEMENT WHICH IS DISPLAYED DURING DOWNLOAD OR INSTALLATION OF THE SOFTWARE (AND WHICH IS DUPLICATED IN THE LICENSE FILE) OR IF THERE IS NO SUCH SOFTWARE LICENSE AGREEMENT OR CLICKWRAP END USER LICENSE AGREEMENT, THE LICENSE(S) LOCATED IN THE “LICENSE” FILE(S) OF THE SOFTWARE. USE OF THIS DOCUMENT IS SUBJECT TO THOSE TERMS AND CONDITIONS, AND YOUR USE HEREOF SHALL CONSTITUTE ACCEPTANCE OF AND AN AGREEMENT TO BE BOUND BY THE SAME. This document contains confidential information that is subject to U.S. and international copyright laws and treaties. No part of this document may be reproduced in any form without the written authorization of TIBCO Software Inc. TIBCO, Two-Second Advantage, TIBCO ActiveMatrix BusinessWorks, TIBCO Business Studio, TIBCO Enterprise Message Service, TIBCO Hawk, TIBCO iProcess, TIBCO iProcess Suite, and TIBCO Rendezvous are either registered trademarks or trademarks of TIBCO Software Inc. in the United States and/or other countries. -

Recursos TIC Para Docencia
Recursos TIC para docencia septiembre de 2009 Antonio Cañas Vargas Reflexión inicial Generación Google Jóvenes nacidos después de 1993 Han crecido en un mundo dominado por internet 11/ene/2008, British Library y Joint Information Systems Committee Reflexión inicial Prefieren información visual frente a textual Prefieren los sistemas interactivos a los pasivos 11/ene/2008, British Library y Joint Information Systems Committee Reflexión inicial Son competentes en general con la tecnología Pero no son “expertos buscadores”, y suelen plagiar (copy-paste) de sitios donde la información no siempre está 11/ene/2008, British Library y Joint Information Systems correctamente editada Committee ni es del todo exacta Reflexión inicial Son impacientes, incapaces de esperar, demandan una gratificación instantánea, y ante cualquier retardo o necesidad de esfuerzo hacen clic en otro sitio, ¡y esto no sólo 11/ene/2008, British Library es aplicable a los y Joint Information Systems Committee jóvenes! Reflexión inicial El tiempo que se permanece en un sitio es muy escaso, insuficiente para ver el contenido completo de una página o de un articulo concebido para el formato en papel El usuario salta entre páginas siguiendo enlaces de forma caótica La lectura como ejercicio de procesamiento sucesivo es un arquetipo en extinción Contenido Recursos TIC en docencia Desde software para hacer presentaciones hasta mundos virtuales en 3D Plataformas de teleformación PRADO - SWAD ¿Qué ofrece SWAD? Uso de SWAD en la UGR Taller práctico de uso de SWAD Presentaciones -

Analizamos 19 Plataformas De E-Learning
Analizamos 19 plataformas de e-Learning En este libro, en el que se analizan 19 plataformas de e learning (también llamados sistemas de gestión de aprendizaje y entornos para la creación de aulas virtuales o de educación a distancia) se realizó en el marco de las iniciativas y proyectos colaborativos surgidos en el Congreso Virtual Mundial de eLearning, entre ellas: el Primer MOOC de habla hispana y GEIPITE (Grupo de Estudio abierto y colaborativo en Investigación y Prácticas sobre la Influencia de las TIC en la Educación). Es por eso que este monográfico se convierte en la primera investigación académica colaborativa (por lo menos de habla hispana y en América Latina, pero posiblemente a nivel mundial) realizada íntegramente de forma sincrónica y conjunta (excepto la edición y el formato final para la Editorial) con herramientas de escritura en tiempo real. Su elaboración incluye tanto la investigación teórica como el trabajo de campo, con todo lo que ello implica: seguramente hayan muchos errores, procesos y elementos a mejorar en futuras ediciones, pero es sin duda otro precedente que hace nuevamente precursor a Investigación colaborativa sobre LMS nivel global al Congreso Virtual Mundial de eLearning. ISBN 978-1-291-53343-9 90000 9 781291 533439 ANALIZAMOS 19 PLATAFORMAS DE E-LEARNING Investigación colaborativa sobre LMS Dirección: Claudio Ariel Clarenc Investigadores y redactores: Silvina Mariel Castro Claudio Ariel Clarenc Carmen López de Lenz María Eugenia Moreno Norma Beatriz Tosco Edición y corrección: Claudio Ariel Clarenc -
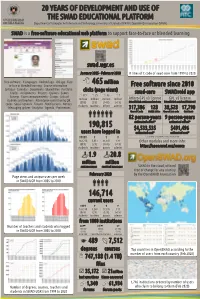
20 Years of Development and Use of the Swad
20 YEARS OF DEVELOPMENT AND USE OF THE SWAD EDUCATIONAL PLATFORM Department of Computer Architecture and Technology, University of Granada (SPAIN) / OpenSWAD Association (SPAIN) SWAD is a free-software educational web platform to support face-to-face or blended learning swad.ugr.es January 2005 - February 2020 # lines of C code of swad-core from 1999 to 2020 Free-software · 9 languages · Android app · iOS app · Face- 465 million to-face or blended learning · Course information · Free software since 2010 Syllabus · Calendar · Documents · Shared files · Portfolio clicks (page views) · Grades · Assignments · Projects · Quizzes · Games swad-core SWADroid app · Surveys · Exam announcements · Groups · Lists of 373 25 66 1 million million million million Affero GPL v3 license GPL v3 license students and teachers · Attendance control using QR https://github.com/acanas/swad-core https://github.com/Amab/SWADroid codes · Social network · Forums · Notifications · Notices (80%) (5%) (14%) (<1%) students teachers others admins · Messaging system · Analytics · Agenda · Preferences 317,306 128 38,528 17,790 lines of C code MySQL tables lines of Java code downloads 82 person-years 9 person-years estimated effort* estimated effort* 190,815 $4,533,535 $491,496 users have logged in estimated cost* estimated cost* * according to COCOMO model in Open Hub 168,270 3,831 31,447 131 Other modules and more info: (88%) (2%) (16%) (<1%) students teachers guests admins https://openswad.org/source 1.9 20.8 million million sent messages received messages SWAD -

Ontologia Del CRTM I D'elements D'interès De La Ciutat De Madrid
Ontologia del CRTM i d’elements d’interès de la ciutat de Madrid Autor: David Mor España Tutor: Felipe Geva Urbano Professor: Ferran Prados Carrasco Grau d’Enginyeria Informàtica Sistemes d’Informació 10/01/2019 Ontologia del CRTM i d’elements d’interès de la ciutat de Madrid Aquesta obra està subjecta a una llicència de Reconeixement-NoComercial-CompartirIgual 3.0 Espanya de CreativeCommons 2 Ontologia del CRTM i d’elements d’interès de la ciutat de Madrid FITXA DEL TREBALL FINAL Ontologia del CRTM i d’elements d’interès de la ciutat Títol del treball: de Madrid Nom de l’autor: David Mor España Nom del col·laborador/a docent: Felipe Geva Urbano Nom del PRA: Ferran Prados Carrasco Data de lliurament (mm/aaaa): 01/2019 Titulació o programa: Grau d’Enginyeria Informàtica Àrea del Treball Final: Web semàntica Idioma del treball: Català Web semàntica, Ontologia, Open Data, RDF, OWL, Paraules clau SPARQL, PHP Resum del Treball: El present treball consisteix en l’estudi teòric de la web semàntica i tot el que l’envolta (estàndards, Open Data, etc.), i en la creació d’una ontologia mitjançant la metodologia de la Universitat de Stanford, que conté dades de tots els mitjans de transport públic que ofereix el Consorcio Regional de Transportes de Madrid i d’elements d’interès de la ciutat. Així doncs, l’objectiu del desenvolupament pràctic és permetre que aquesta pugui ser nodrida a partir de diversos repositoris de dades i, per tant, unificar la terminologia de l’estructura d’aquestes fonts amb la finalitat que l’ontologia pugui ser utilitzada per programaris externs que cerquin generar coneixement i proporcionar suport a l’hora de prendre decisions.