Pointing Analysis and Design Drivers for Low Earth Orbit Satellite Quantum Key Distribution Jeremiah A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Astrodynamics
Politecnico di Torino SEEDS SpacE Exploration and Development Systems Astrodynamics II Edition 2006 - 07 - Ver. 2.0.1 Author: Guido Colasurdo Dipartimento di Energetica Teacher: Giulio Avanzini Dipartimento di Ingegneria Aeronautica e Spaziale e-mail: [email protected] Contents 1 Two–Body Orbital Mechanics 1 1.1 BirthofAstrodynamics: Kepler’sLaws. ......... 1 1.2 Newton’sLawsofMotion ............................ ... 2 1.3 Newton’s Law of Universal Gravitation . ......... 3 1.4 The n–BodyProblem ................................. 4 1.5 Equation of Motion in the Two-Body Problem . ....... 5 1.6 PotentialEnergy ................................. ... 6 1.7 ConstantsoftheMotion . .. .. .. .. .. .. .. .. .... 7 1.8 TrajectoryEquation .............................. .... 8 1.9 ConicSections ................................... 8 1.10 Relating Energy and Semi-major Axis . ........ 9 2 Two-Dimensional Analysis of Motion 11 2.1 ReferenceFrames................................. 11 2.2 Velocity and acceleration components . ......... 12 2.3 First-Order Scalar Equations of Motion . ......... 12 2.4 PerifocalReferenceFrame . ...... 13 2.5 FlightPathAngle ................................. 14 2.6 EllipticalOrbits................................ ..... 15 2.6.1 Geometry of an Elliptical Orbit . ..... 15 2.6.2 Period of an Elliptical Orbit . ..... 16 2.7 Time–of–Flight on the Elliptical Orbit . .......... 16 2.8 Extensiontohyperbolaandparabola. ........ 18 2.9 Circular and Escape Velocity, Hyperbolic Excess Speed . .............. 18 2.10 CosmicVelocities -

Electric Propulsion System Scaling for Asteroid Capture-And-Return Missions
Electric propulsion system scaling for asteroid capture-and-return missions Justin M. Little⇤ and Edgar Y. Choueiri† Electric Propulsion and Plasma Dynamics Laboratory, Princeton University, Princeton, NJ, 08544 The requirements for an electric propulsion system needed to maximize the return mass of asteroid capture-and-return (ACR) missions are investigated in detail. An analytical model is presented for the mission time and mass balance of an ACR mission based on the propellant requirements of each mission phase. Edelbaum’s approximation is used for the Earth-escape phase. The asteroid rendezvous and return phases of the mission are modeled as a low-thrust optimal control problem with a lunar assist. The numerical solution to this problem is used to derive scaling laws for the propellant requirements based on the maneuver time, asteroid orbit, and propulsion system parameters. Constraining the rendezvous and return phases by the synodic period of the target asteroid, a semi- empirical equation is obtained for the optimum specific impulse and power supply. It was found analytically that the optimum power supply is one such that the mass of the propulsion system and power supply are approximately equal to the total mass of propellant used during the entire mission. Finally, it is shown that ACR missions, in general, are optimized using propulsion systems capable of processing 100 kW – 1 MW of power with specific impulses in the range 5,000 – 10,000 s, and have the potential to return asteroids on the order of 103 104 tons. − Nomenclature -
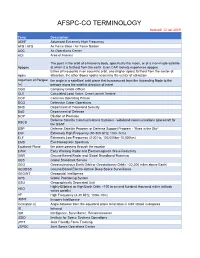
AFSPC-CO TERMINOLOGY Revised: 12 Jan 2019
AFSPC-CO TERMINOLOGY Revised: 12 Jan 2019 Term Description AEHF Advanced Extremely High Frequency AFB / AFS Air Force Base / Air Force Station AOC Air Operations Center AOI Area of Interest The point in the orbit of a heavenly body, specifically the moon, or of a man-made satellite Apogee at which it is farthest from the earth. Even CAP rockets experience apogee. Either of two points in an eccentric orbit, one (higher apsis) farthest from the center of Apsis attraction, the other (lower apsis) nearest to the center of attraction Argument of Perigee the angle in a satellites' orbit plane that is measured from the Ascending Node to the (ω) perigee along the satellite direction of travel CGO Company Grade Officer CLV Calculated Load Value, Crew Launch Vehicle COP Common Operating Picture DCO Defensive Cyber Operations DHS Department of Homeland Security DoD Department of Defense DOP Dilution of Precision Defense Satellite Communications Systems - wideband communications spacecraft for DSCS the USAF DSP Defense Satellite Program or Defense Support Program - "Eyes in the Sky" EHF Extremely High Frequency (30-300 GHz; 1mm-1cm) ELF Extremely Low Frequency (3-30 Hz; 100,000km-10,000km) EMS Electromagnetic Spectrum Equitorial Plane the plane passing through the equator EWR Early Warning Radar and Electromagnetic Wave Resistivity GBR Ground-Based Radar and Global Broadband Roaming GBS Global Broadcast Service GEO Geosynchronous Earth Orbit or Geostationary Orbit ( ~22,300 miles above Earth) GEODSS Ground-Based Electro-Optical Deep Space Surveillance -

Cislunar Tether Transport System
FINAL REPORT on NIAC Phase I Contract 07600-011 with NASA Institute for Advanced Concepts, Universities Space Research Association CISLUNAR TETHER TRANSPORT SYSTEM Report submitted by: TETHERS UNLIMITED, INC. 8114 Pebble Ct., Clinton WA 98236-9240 Phone: (206) 306-0400 Fax: -0537 email: [email protected] www.tethers.com Report dated: May 30, 1999 Period of Performance: November 1, 1998 to April 30, 1999 PROJECT SUMMARY PHASE I CONTRACT NUMBER NIAC-07600-011 TITLE OF PROJECT CISLUNAR TETHER TRANSPORT SYSTEM NAME AND ADDRESS OF PERFORMING ORGANIZATION (Firm Name, Mail Address, City/State/Zip Tethers Unlimited, Inc. 8114 Pebble Ct., Clinton WA 98236-9240 [email protected] PRINCIPAL INVESTIGATOR Robert P. Hoyt, Ph.D. ABSTRACT The Phase I effort developed a design for a space systems architecture for repeatedly transporting payloads between low Earth orbit and the surface of the moon without significant use of propellant. This architecture consists of one rotating tether in elliptical, equatorial Earth orbit and a second rotating tether in a circular low lunar orbit. The Earth-orbit tether picks up a payload from a circular low Earth orbit and tosses it into a minimal-energy lunar transfer orbit. When the payload arrives at the Moon, the lunar tether catches it and deposits it on the surface of the Moon. Simultaneously, the lunar tether picks up a lunar payload to be sent down to the Earth orbit tether. By transporting equal masses to and from the Moon, the orbital energy and momentum of the system can be conserved, eliminating the need for transfer propellant. Using currently available high-strength tether materials, this system could be built with a total mass of less than 28 times the mass of the payloads it can transport. -

GEO, MEO, and LEO How Orbital Altitude Impacts Network Performance in Satellite Data Services
GEO, MEO, AND LEO How orbital altitude impacts network performance in satellite data services COMMUNICATION OVER SATELLITE “An entire multi-orbit is now well accepted as a key enabler across the telecommunications industry. Satellite networks can supplement existing infrastructure by providing global reach satellite ecosystem is where terrestrial networks are unavailable or not feasible. opening up above us, But not all satellite networks are created equal. Providers offer different solutions driving new opportunities depending on the orbits available to them, and so understanding how the distance for high-performance from Earth affects performance is crucial for decision making when selecting a satellite service. The following pages give an overview of the three main orbit gigabit connectivity and classes, along with some of the principal trade-offs between them. broadband services.” Stewart Sanders Executive Vice President of Key terms Technology at SES GEO – Geostationary Earth Orbit. NGSO – Non-Geostationary Orbit. NGSO is divided into MEO and LEO. MEO – Medium Earth Orbit. LEO – Low Earth Orbit. HTS – High Throughput Satellites designed for communication. Latency – the delay in data transmission from one communication endpoint to another. Latency-critical applications include video conferencing, mobile data backhaul, and cloud-based business collaboration tools. SD-WAN – Software-Defined Wide Area Networking. Based on policies controlled by the user, SD-WAN optimises network performance by steering application traffic over the most suitable access technology and with the appropriate Quality of Service (QoS). Figure 1: Schematic of orbital altitudes and coverage areas GEOSTATIONARY EARTH ORBIT Altitude 36,000km GEO satellites match the rotation of the Earth as they travel, and so remain above the same point on the ground. -

Low Earth Orbit Slotting for Space Traffic Management Using Flower
Low Earth Orbit Slotting for Space Traffic Management Using Flower Constellation Theory David Arnas∗, Miles Lifson†, and Richard Linares‡ Massachusetts Institute of Technology, Cambridge, MA, 02139, USA Martín E. Avendaño§ CUD-AGM (Zaragoza), Crtra Huesca s / n, Zaragoza, 50090, Spain This paper proposes the use of Flower Constellation (FC) theory to facilitate the design of a Low Earth Orbit (LEO) slotting system to avoid collisions between compliant satellites and optimize the available space. Specifically, it proposes the use of concentric orbital shells of admissible “slots” with stacked intersecting orbits that preserve a minimum separation distance between satellites at all times. The problem is formulated in mathematical terms and three approaches are explored: random constellations, single 2D Lattice Flower Constellations (2D-LFCs), and unions of 2D-LFCs. Each approach is evaluated in terms of several metrics including capacity, Earth coverage, orbits per shell, and symmetries. In particular, capacity is evaluated for various inclinations and other parameters. Next, a rough estimate for the capacity of LEO is generated subject to certain minimum separation and station-keeping assumptions and several trade-offs are identified to guide policy-makers interested in the adoption of a LEO slotting scheme for space traffic management. I. Introduction SpaceX, OneWeb, Telesat and other companies are currently planning mega-constellations for space-based internet connectivity and other applications that would significantly increase the number of on-orbit active satellites across a variety of altitudes [1–5]. As these and other actors seek to make more intensive use of the global space commons, there is growing need to characterize the fundamental limits to the capacity of Low Earth Orbit (LEO), particularly in high-demand orbits and altitudes, and minimize the extent to which use by one space actor hampers use by other actors. -

SATELLITES ORBIT ELEMENTS : EPHEMERIS, Keplerian ELEMENTS, STATE VECTORS
www.myreaders.info www.myreaders.info Return to Website SATELLITES ORBIT ELEMENTS : EPHEMERIS, Keplerian ELEMENTS, STATE VECTORS RC Chakraborty (Retd), Former Director, DRDO, Delhi & Visiting Professor, JUET, Guna, www.myreaders.info, [email protected], www.myreaders.info/html/orbital_mechanics.html, Revised Dec. 16, 2015 (This is Sec. 5, pp 164 - 192, of Orbital Mechanics - Model & Simulation Software (OM-MSS), Sec 1 to 10, pp 1 - 402.) OM-MSS Page 164 OM-MSS Section - 5 -------------------------------------------------------------------------------------------------------43 www.myreaders.info SATELLITES ORBIT ELEMENTS : EPHEMERIS, Keplerian ELEMENTS, STATE VECTORS Satellite Ephemeris is Expressed either by 'Keplerian elements' or by 'State Vectors', that uniquely identify a specific orbit. A satellite is an object that moves around a larger object. Thousands of Satellites launched into orbit around Earth. First, look into the Preliminaries about 'Satellite Orbit', before moving to Satellite Ephemeris data and conversion utilities of the OM-MSS software. (a) Satellite : An artificial object, intentionally placed into orbit. Thousands of Satellites have been launched into orbit around Earth. A few Satellites called Space Probes have been placed into orbit around Moon, Mercury, Venus, Mars, Jupiter, Saturn, etc. The Motion of a Satellite is a direct consequence of the Gravity of a body (earth), around which the satellite travels without any propulsion. The Moon is the Earth's only natural Satellite, moves around Earth in the same kind of orbit. (b) Earth Gravity and Satellite Motion : As satellite move around Earth, it is pulled in by the gravitational force (centripetal) of the Earth. Contrary to this pull, the rotating motion of satellite around Earth has an associated force (centrifugal) which pushes it away from the Earth. -

Orbital Mechanics
Danish Space Research Institute Danish Small Satellite Programme DTU Satellite Systems and Design Course Orbital Mechanics Flemming Hansen MScEE, PhD Technology Manager Danish Small Satellite Programme Danish Space Research Institute Phone: 3532 5721 E-mail: [email protected] Slide # 1 FH 2001-09-16 Orbital_Mechanics.ppt Danish Space Research Institute Danish Small Satellite Programme Planetary and Satellite Orbits Johannes Kepler (1571 - 1630) 1st Law • Discovered by the precision mesurements of Tycho Brahe that the Moon and the Periapsis - Apoapsis - planets moves around in elliptical orbits Perihelion Aphelion • Harmonia Mundi 1609, Kepler’s 1st og 2nd law of planetary motion: st • 1 Law: The orbit of a planet ia an ellipse nd with the sun in one focal point. 2 Law • 2nd Law: A line connecting the sun and a planet sweeps equal areas in equal time intervals. 3rd Law • 1619 came Keplers 3rd law: • 3rd Law: The square of the planet’s orbit period is proportional to the mean distance to the sun to the third power. Slide # 2 FH 2001-09-16 Orbital_Mechanics.ppt Danish Space Research Institute Danish Small Satellite Programme Newton’s Laws Isaac Newton (1642 - 1727) • Philosophiae Naturalis Principia Mathematica 1687 • 1st Law: The law of inertia • 2nd Law: Force = mass x acceleration • 3rd Law: Action og reaction • The law of gravity: = GMm F Gravitational force between two bodies F 2 G The universal gravitational constant: G = 6.670 • 10-11 Nm2kg-2 r M Mass af one body, e.g. the Earth or the Sun m Mass af the other body, e.g. the satellite r Separation between the bodies G is difficult to determine precisely enough for precision orbit calculations. -

A Delta-V Map of the Known Main Belt Asteroids
Acta Astronautica 146 (2018) 73–82 Contents lists available at ScienceDirect Acta Astronautica journal homepage: www.elsevier.com/locate/actaastro A Delta-V map of the known Main Belt Asteroids Anthony Taylor *, Jonathan C. McDowell, Martin Elvis Harvard-Smithsonian Center for Astrophysics, 60 Garden St., Cambridge, MA, USA ARTICLE INFO ABSTRACT Keywords: With the lowered costs of rocket technology and the commercialization of the space industry, asteroid mining is Asteroid mining becoming both feasible and potentially profitable. Although the first targets for mining will be the most accessible Main belt near Earth objects (NEOs), the Main Belt contains 106 times more material by mass. The large scale expansion of NEO this new asteroid mining industry is contingent on being able to rendezvous with Main Belt asteroids (MBAs), and Delta-v so on the velocity change required of mining spacecraft (delta-v). This paper develops two different flight burn Shoemaker-Helin schemes, both starting from Low Earth Orbit (LEO) and ending with a successful MBA rendezvous. These methods are then applied to the 700,000 asteroids in the Minor Planet Center (MPC) database with well-determined orbits to find low delta-v mining targets among the MBAs. There are 3986 potential MBA targets with a delta- v < 8kmsÀ1, but the distribution is steep and reduces to just 4 with delta-v < 7kms-1. The two burn methods are compared and the orbital parameters of low delta-v MBAs are explored. 1. Introduction [2]. A running tabulation of the accessibility of NEOs is maintained on- line by Lance Benner3 and identifies 65 NEOs with delta-v< 4:5kms-1.A For decades, asteroid mining and exploration has been largely dis- separate database based on intensive numerical trajectory calculations is missed as infeasible and unprofitable. -

Why Atens Enjoy Enhanced Accessibility for Human Space Flight
(Preprint) AAS 11-449 WHY ATENS ENJOY ENHANCED ACCESSIBILITY FOR HUMAN SPACE FLIGHT Daniel R. Adamo* and Brent W. Barbee† Near-Earth objects can be grouped into multiple orbit classifications, among them being the Aten group, whose members have orbits crossing Earth's with semi-major axes less than 1 astronomical unit. Atens comprise well under 10% of known near-Earth objects. This is in dramatic contrast to results from recent human space flight near-Earth object accessibility studies, where the most favorable known destinations are typically almost 50% Atens. Geocentric dynamics explain this enhanced Aten accessibility and lead to an understanding of where the most accessible near-Earth objects reside. Without a com- prehensive space-based survey, however, highly accessible Atens will remain largely un- known. INTRODUCTION In the context of human space flight (HSF), the concept of near-Earth object (NEO) accessibility is highly subjective (Reference 1). Whether or not a particular NEO is accessible critically depends on mass, performance, and reliability of interplanetary HSF systems yet to be designed. Such systems would cer- tainly include propulsion and crew life support with adequate shielding from both solar flares and galactic cosmic radiation. Equally critical architecture options are relevant to NEO accessibility. These options are also far from being determined and include the number of launches supporting an HSF mission, together with whether consumables are to be pre-emplaced at the destination. Until the unknowns of HSF to NEOs come into clearer focus, the notion of relative accessibility is of great utility. Imagine a group of NEOs, each with nearly equal HSF merit determined from their individual characteristics relating to crew safety, scientific return, resource utilization, and planetary defense. -

TLE-Tools's Documentation!
TLE-tools Release 0.2.3 Federico Stra May 24, 2020 CONTENTS: 1 Purpose 3 2 Installation 5 3 Links 7 4 Indices and tables 9 4.1 API Documentation...........................................9 Python Module Index 15 Index 17 i ii TLE-tools, Release 0.2.3 TLE-tools is a small library to work with two-line element set files. CONTENTS: 1 TLE-tools, Release 0.2.3 2 CONTENTS: CHAPTER ONE PURPOSE The purpose of the library is to parse TLE sets into convenient TLE objects, load entire TLE set files into pandas. DataFrame’s, convert TLE objects into poliastro.twobody.orbit.Orbit’s, and more. From Wikipedia: A two-line element set (TLE) is a data format encoding a list of orbital elements of an Earth-orbiting object for a given point in time, the epoch. The TLE data representation is specific to the simplified perturbations models (SGP, SGP4, SDP4, SGP8 and SDP8), so any algorithm using a TLE as a data source must implement one of the SGP models to correctly compute the state at a time of interest. TLEs can describe the trajectories only of Earth-orbiting objects. Here is an example TLE: ISS (ZARYA) 1 25544U 98067A 19249.04864348.00001909 00000-0 40858-40 9990 2 25544 51.6464 320.1755 0007999 10.9066 53.2893 15.50437522187805 Here is a minimal example on how to load the previous TLE: from tletools import TLE tle_string= """ ISS (ZARYA) 1 25544U 98067A 19249.04864348 .00001909 00000-0 40858-4 0 9990 2 25544 51.6464 320.1755 0007999 10.9066 53.2893 15.50437522187805 """ tle_lines= tle_string.strip().splitlines() t= TLE.from_lines( *tle_lines) Then t is: TLE(name='ISS (ZARYA)', norad='25544', classification='U', int_desig='98067A', epoch_year=2019, epoch_day=249.04864348, dn_o2=1.909e-05, ddn_o6=0.0, bstar=4.0858e- ,!05, set_num=999, inc=51.6464, raan=320.1755, ecc=0.0007999, argp=10.9066,M=53.2893, n=15.50437522, rev_num=18780) and you can then access its attributes like t.argp, t.epoch.. -

The UCS Satellite Database
UCS Satellite Database User’s Manual 1-1-17 The UCS Satellite Database The UCS Satellite Database is a listing of active satellites currently in orbit around the Earth. It is available as both a downloadable Excel file and in a tab-delimited text format, and in a version (tab-delimited text) in which the "Name" column contains only the official name of the satellite in the case of government and military satellites, and the most commonly used name in the case of commercial and civil satellites. The database is updated roughly quarterly. Our intent in producing the Database is to create a research tool by collecting open-source information on active satellites and presenting it in a format that can be easily manipulated for research and analysis. The Database includes basic information about the satellites and their orbits, but does not contain the detailed information necessary to locate individual satellites. The UCS Satellite Database can be accessed at www.ucsusa.org/satellite_database. Using the Database The Database is free and its use is unrestricted. We request that its use be acknowledged and referenced in written materials. References should include the version of the Database that was used, which is indicated by the name of the Excel file, and a link to or URL for the webpage www.ucsusa.org/satellite_database. We welcome corrections, additions, and suggestions. These can be emailed to the Database manager at [email protected] If you would like to be notified when updated versions of the Database are completed, please send an email request to this address.