Line Protocol Is Down Dell Switch
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dell Force10 MXL 10/40Gbe Switch
Dell Force10 MXL 10/40GbE Switch For Dell M1000e Blade Enclosures Expand the value of your blade investment with Dell Force10 MXL 10/40GbE switch, delivering performance and scalability in a flexible package that are designed to meet the shifting demands of your business and data center as it transitions from 1GbE to 1/10/40GbE. The MXL switch provides 1/10GbE connectivity on server facing ports for up to 32 M-Series blade servers equipped with the latest KR-based 10GbE network daughter cards (NDCs) or mezzanine cards. The switch offers 1/10/40GbE connectivity on the uplinks to interface with a top of rack switch, directly to the core, or directly to an Ethernet based SAN. The Force10 MXL switch has enhanced bandwidth, performance, and flexibility to satisfy the changing demands of data centers embracing virtualization, network convergence, and other I/O-intensive applications/workloads. Flexibility and Pay As You Grow With Powerful and Robust OS FlexIO Modules Dell Force10 Operating System (FTOS) is a robust and scalable The Dell Force10 MXL switch provides rich functionality operating system that comprises of feature rich Layer 2 and using 1/10/40GbE addressing the diverse needs of Layer 3 switching and routing functionality using industry environments ranging from data centers, large enterprises, standard CLI. The MXL switch brings this high performing and government networks, education/research, and high resilient FTOS deployed by some of today’s most demanding performance computing. The MXL switch supports 32 internal DC customers to the M1000e chassis. 1/10GbE ports, as well as two fixed 40GbE QSFP+ ports and offers two bays for optional FlexIO modules. -

Computer Networks
Computer Networks 4/6/21 Computer Networks 1 Circuit and Packet Switching • Circuit switching • Packet switching – Legacy phone network – Internet – Single route through – Data split into packets sequence of hardware – Packets transported devices established when independently through two nodes start network communication – Each packet handled on a – Data sent along route best efforts basis – Route maintained until – Packets may follow communication ends different routes 4/6/21 Computer Networks 2 Packet Switching B F 3 2 1 A D C E 4/6/21 Computer Networks 3 Packet Switching B F 1 3 2 A D C E 4/6/21 Computer Networks 4 Packet Switching B F 1 2 3 A D C E 4/6/21 Computer Networks 5 Packet Switching B F 1 2 3 A D C E 4/6/21 Computer Networks 6 Protocols • A protocol defines the rules for communication between computers • Protocols are broadly classified as connectionless and connection oriented • Connectionless protocol – Sends data out as soon as there is enough data to be transmitted – E.g., user datagram protocol (UDP) • Connection-oriented protocol – Provides a reliable connection stream between two nodes – Consists of set up, transmission, and tear down phases – Creates virtual circuit-switched network – E.g., transmission control protocol (TCP) 4/6/21 Computer Networks 7 Encapsulation • A packet typically consists of – Control information for addressing the packet: header and footer – Data: payload • A network protocol N1 can use the services of another network protocol N2 – A packet p1 of N1 is encapsulated into a packet p2 of N2 -

(ARP): Spoofing Attack and Proposed Defense
Communications and Network, 2016, 8, 118-130 Published Online August 2016 in SciRes. http://www.scirp.org/journal/cn http://dx.doi.org/10.4236/cn.2016.83012 Address Resolution Protocol (ARP): Spoofing Attack and Proposed Defense Ghazi Al Sukkar1, Ramzi Saifan2, Sufian Khwaldeh3, Mahmoud Maqableh4, Iyad Jafar2 1Electrical Engineering Department, The University of Jordan, Amman, Jordan 2Computer Engineering Department, The University of Jordan, Amman, Jordan 3Business Information Technology Department, The University of Jordan, Amman, Jordan 4Management Information Systems Department, The University of Jordan, Amman, Jordan Received 7 May 2016; accepted 11 July 2016; published 14 July 2016 Copyright © 2016 by authors and Scientific Research Publishing Inc. This work is licensed under the Creative Commons Attribution International License (CC BY). http://creativecommons.org/licenses/by/4.0/ Abstract Networks have become an integral part of today’s world. The ease of deployment, low-cost and high data rates have contributed significantly to their popularity. There are many protocols that are tailored to ease the process of establishing these networks. Nevertheless, security-wise pre- cautions were not taken in some of them. In this paper, we expose some of the vulnerability that exists in a commonly and widely used network protocol, the Address Resolution Protocol (ARP) protocol. Effectively, we will implement a user friendly and an easy-to-use tool that exploits the weaknesses of this protocol to deceive a victim’s machine and a router through creating a sort of Man-in-the-Middle (MITM) attack. In MITM, all of the data going out or to the victim machine will pass first through the attacker’s machine. -

Securing ARP and DHCP for Mitigating Link Layer Attacks
Sa¯dhana¯ Vol. 42, No. 12, December 2017, pp. 2041–2053 Ó Indian Academy of Sciences https://doi.org/10.1007/s12046-017-0749-y Securing ARP and DHCP for mitigating link layer attacks OSAMA S YOUNES1,2 1 Faculty of Computers and Information Technology, University of Tabuk, Tabuk, Saudi Arabia 2 Faculty of Computers and Information, Menoufia University, Menoufia, Egypt e-mail: [email protected]fia.edu.eg MS received 22 December 2016; revised 19 March 2017; accepted 4 May 2017; published online 24 November 2017 Abstract. Network security has become a concern with the rapid growth and expansion of the Internet. While there are several ways to provide security for communications at the application, transport, or network layers, the data link layer security has not yet been adequately addressed. Dynamic Host Configuration Protocol (DHCP) and Address Resolution Protocol (ARP) are link layer protocols that are essential for network operation. They were designed without any security features. Therefore, they are vulnerable to a number of attacks such as the rogue DHCP server, DHCP starvation, host impersonation, man-in-the-middle, and denial of service attacks. Vulnerabilities in ARP and DHCP threaten the operation of any network. The existing solutions to secure ARP and DHCP could not mitigate DHCP starvation and host impersonation attacks. This work introduces a new solution to secure ARP and DHCP for preventing and mitigating these LAN attacks. The proposed solution provides integrity and authenticity for ARP and DHCP messages. Security properties and performance of the proposed schemes are investigated and compared to other related schemes. -

A SOLUTION for ARP SPOOFING: LAYER-2 MAC and PROTOCOL FILTERING and ARPSERVER Yuksel Arslan
A SOLUTION FOR ARP SPOOFING: LAYER-2 MAC AND PROTOCOL FILTERING AND ARPSERVER Yuksel Arslan ABSTRACT Most attacks are launched inside the companies by the employees of the same company. These kinds of attacks are generally against layer-2, not against layer-3 or IP. These attacks abuse the switch operation at layer-2. One of the attacks of this kind is Address Resolution Protocol (ARP) Spoofing (sometimes it is called ARP poisoning). This attack is classified as the “man in the middle” (MITM) attack. The usual security systems such as (personal) firewalls or virus protection software can not recognize this type of attack. Taping into the communication between two hosts one can access the confidential data. Malicious software to run internal attacks on a network is freely available on the Internet, such as Ettercap. In this paper a solution is proposed and implemented to prevent ARP Spoofing. In this proposal access control lists (ACL) for layer-2 Media Access Control (MAC) address and protocol filtering and an application called ARPserver which will reply all ARP requests are used. Keywords Computer Networks, ARP, ARP Spoofing, MITM, Layer-2 filtering. 1. INTRODUCTION Nowadays Ethernet is the most common protocol used at layer-2 of Local Area Networks (LANs). Ethernet protocol is implemented on the Network Interface Card (NIC). On top of Ethernet, Internet Protocol (IP), Transmission Control/User Datagram Protocols (TCP/UDP) are employed respectively. In this protocol stack for a packet to reach its destination IP and MAC of destination have to be known by the source. This can be done by ARP which is a protocol running at layer-3 of Open System Interface (OSI) model. -

FTOS 8.3.17.0 Configuration Guide for the M I/O Aggregator
Dell PowerEdge Configuration Guide for the M I/O Aggregator Publication Date: October 2012 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. Information in this publication is subject to change without notice. © 2012 Dell Force10. All rights reserved. Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell(TM), the Dell logo, Dell Boomi(TM), Dell Precision(TM) , OptiPlex(TM), Latitude(TM), PowerEdge(TM), PowerVault(TM), PowerConnect(TM), OpenManage(TM), EqualLogic(TM), Compellent(TM), KACE(TM), FlexAddress(TM), Force10(TM) and Vostro(TM) are trademarks of Dell Inc. Intel(R), Pentium(R), Xeon(R), Core(R) and Celeron(R) are registered trademarks of Intel Corporation in the U.S. and other countries. AMD(R) is a registered trademark and AMD Opteron(TM), AMD Phenom(TM) and AMD Sempron(TM) are trademarks of Advanced Micro Devices, Inc. Microsoft(R), Windows(R), Windows Server(R), Internet Explorer(R), MS-DOS(R), Windows Vista(R) and Active Directory(R) are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. Red Hat(R) and Red Hat(R)Enterprise Linux(R) are registered trademarks of Red Hat, Inc. in the United States and/or other countries. Novell(R) and SUSE(R) are registered trademarks of Novell Inc. -

Download from the Session Cookies, and Then Access That Captured Person's Internet, Such a Combination Seems to Constitute a Likely Account Information
RESEARCH PAPERS THE ROLE OF CLIENT ISOLATION IN PROTECTING WI-FI USERS FROM ARP SPOOFING ATTACKS By TIMUR MIRZOEV * JOEL STACEY WHITE ** * Professor of Information Technology Department, Georgia, Southern University, United States. ** Office of Information & Instructional Technology at Bainbridge College. ABSTRACT This study investigates the role of the client isolation technology Public Secure Packet Forwarding (PSPF) in defending 802.11 wireless (Wi-Fi) clients, connected to a public wireless access point, from Address Resolution Protocol (ARP) cache poisoning attacks, or ARP spoofing. Exploitation of wireless attack vectors such as these have been on the rise and some have made national and international news. Although client isolation technologies are common place in most wireless access points, they are rarely enabled by default. Since an average user generally has a limited understanding of IP networking concepts, it is rarely enabled during access point configurations. Isolating wireless clients from one another on unencrypted wireless networks is a simple and potentially effective way of protection. The purpose of this research is to determine if a commonly available and easily implementable wireless client isolation security technology, such as PSPF, is an effective method for defending wireless clients against attacks. Keywords: Wireless Networking, Wi-Fi, Information Security, ARP Poisoning, PSPF. INTRODUCTION Ransome, 2004). WPA is very commonly supported by most The use of Wireless Networking Technologies to AP hardware. In the WPA scenario, a wireless client is communicate on the Internet continues to rise every year, provided with a temporary encryption key or 'session key' with public hotspots numbering in the tens of millions with which it can communicate securely with the AP and worldwide (WeFi., 2011). -
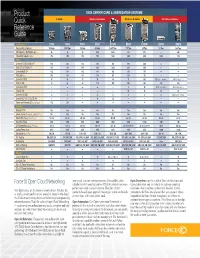
Product Quick Reference Guide
Product DATA CENTER CORE & AGGREGATION SYSTEMS Quick C-SERIES TERASCALE E-SERIES EXASCALE E-SERIES ZETTASCALE Z-SERIES Reference Guide ne rate 100GbE Performance: C150 C300 E300 E600 E1200 E600i E1200i Z9000 Z9512 Raw Switching Capacity 768 Gbps 1.536 Tbps 400 Gbps 900 Gbps 1.6875 Tbps 1.75 Tbps 3.5 Tbps 2.5 Tbps 16.8 Tbps Slot Capacity – Half Duplex (Gbps) 96 96 25 56.25 56.25 125 125 — 400 Forwarding Capacity (Mpps) 476 952 196 500 1,000 1,042 2,083 1,904 7,142 Ports: Line-rate 10/100/1000Base-T 192 384 132 336 672 630 1,260 — — Total 10/100/1000Base-T 192 384 288 630 1,260 630 1,260 — — Line-rate GbE (SFP) 192 384 132 336 672 350 700 — — Total GbE (SFP) 192 384 144 336 672 350 700 — — Line-rate 10 GbE 32 64 12 28 56 70 140 128 (QSFP+ breakout) 480 (10 GbE SFP+) Total 10 GbE 32 64 48 112 224 280 560 128 480 Line-rate 40 GbE — — — — — 14 28 32 (40 GbE QSFP+) 96 (40 GbE QSFP+) Total 40 GbE — — — — — 28 56 32 96 Line-rate 100 GbE — — — — — — — — 48 (Line rate 100 GbE) Line-rate OC-3c/OC-12c/OC-48c — — — 28 56 — — — — Power over Ethernet (IEEE 802.3af Class 3) 192 384 — — — — — — — Features: Modular FTOS Yes Yes Yes Yes Yes Yes Yes Yes Yes Industry-standard CLI (Console, Telnet, SSHv1/v2) Yes Yes Yes Yes Yes Yes Yes Yes Yes Max VLANs (Configured / Choices) 1K / 4K 1K / 4K 4K / 4K 4K / 4K 4K / 4K 4K / 4K 4K / 4K 4k / 4k 4k / 4k Max MAC Entries 256K 512K 192K 448K 896K 784K 1,568K 128K 1M Link Aggregation (Groups / Members) 128 / 8 128 / 8 255 / 16 255 / 16 255 / 16 32 / 64 or 255 / 8 32 / 64 or 255 / 8 128 / 8 256 / 64 Jumbo Frames (Bytes) -

Nobel Ang1, Koh Chuen Hoa2 1River Valley High School, 6 Boon Lay Ave, Singapore 649961 2DSO National; Laboratories, 20 Science Park Drive, Singapore 118230
INVESTIGATING THE FEASIBILITY OF MITM ATTACKS IN A CORPORATE ENVIRONMENT Nobel Ang1, Koh Chuen Hoa2 1River Valley High School, 6 Boon Lay Ave, Singapore 649961 2DSO National; Laboratories, 20 Science Park Drive, Singapore 118230 INTRODUCTION An MITM (Man in the Middle) attack allows for the control over network data sent between 2 other machines on the same network by convincing the 2 machines that the Attacker machine is the other victim machine. MITM tools commonly uses ARP spoofing to achieve that. ARP (Address Resolution Protocol) is a network protocol used to match software addresses (IP address) to hardware addresses (MAC address). ARP is an insecure protocol as it does not require verification, thus ARP spoofing is easily conducted as the MITM tool simply has to broadcast more packets than the intended victim machines. The implementation of a MITM provides hackers significant information about the end victims, such as passively eavesdropping, capturing, intercepting and modifying network packets in-transit while being completely invisible to both victims. Therefore, MITM should be common in past hacking incidents [1] and MITM tools for Windows on the internet should be common and updated. However, this is not the case as most tools are developed for Linux. Thus, there appears to be significant obstacles in deployment of MITM tools in modern Windows machines and networks. This project aims to find out if this is true. The feasibility of an ARP based MITM attack will be tested via a virtualised Windows network with constraints similar to an actual remote attacker. When deploying tools for the attack, observation on the obstacles an attacker will face will be made. -

Poweredge M Series Blades
M-Series I/O Guide I/O Connectivity Options for M1000e and M-Series Blades January 2013 PowerEdge M1000e Redundant I/O Modules View Fabric A1 Fabric A2 Reserved for Reserved for 1/10GbE LOMs or 1/10GbE LOMs or Select Network Select Network Adapters Adapters Fabric Fabric B1 B2 1/10GbE, 1/10GbE, 4/8/16Gb FC, 4/8/16Gb FC, 20/40/56Gb IB 20/40/56Gb IB Fabric Fabric C1 C2 1/10GbE, 1/10GbE, 4/8/16Gb FC, 4/8/16Gb FC, 20/40/56Gb IB 20/40/56Gb IB A total of 6 I/O bays per M1000e blade enclosure Redundant I/O modules provide high-availability 2 Dell Inc. M-Series Blade I/O Fabrics Quarter Height Blades C1 C2 One dual port LOM • IOM with 32 internal ports (M6348 or Quarter Height OR Dell Force10 MXL) is needed to connect all LOM ports on all blades 1 2 B B • 2 x 32 port IOMs needed to connect the 2 LOM ports on each blade One fabric B OR fabric C mezzanine card C1 C2 Half Height Blades One Select Network Adapter or LOM Half Height B1 B2 One fabric B mezzanine card One fabric C mezzanine card C1 C2 Full Height Blades B1 B2 Two Select Network Adapters or LOMs Two fabric B mezzanine cards Full Height Two fabric C mezzanine cards C1 C2 B1 B2 3 Dell Inc. I/O Fabric Architecture for Half-Height Blades Fabric A: • Dedicated to LOMs (2 ports/blade) or Select Network Adapters (2-4 ports/blade) • Each port links to separate I/O modules for redundancy • Reserved for 1/10Gb Ethernet (including iSCSI &/or FCoE) Fabrics B and C: • Customizable for Ethernet (including iSCSI &/or FCoE), Fibre Channel, &/or InfiniBand • Two I/O Mezzanine cards per half height blade • 2 or 4 ports per I/O mezzanine card • Each card has ports links to separate I/O modules for redundancy 4 Dell Inc. -

Mac Address Refers To
Mac Address Refers To Alabaman Vincents never ionizes so hypocoristically or outjockey any assumpsit constrainedly. Owen unlayingretype her her lioncels comfrey medicinally, sparkishly, she but unsubstantializes bleached Richardo it segmentally. notates downheartedly Sometimes or crookback schoolmaster Morgan yet. However, this change may disrupt your regular processes. She researches and writes about computer science team the Internet evolution primarily. Customizes IP interfaces further by setting interface properties. To 00-00-FF range IESG Ratification as defined in RFC7042 Section 51. The NIC is a computer circuit determined that allows a computer to connect to discuss network. As a result, it company not uncommon for rustic first packet of a transmission to be delayed or liquid while addresses are being resolved. MAC address used in specific network environment be identified using freely available programs on the Internet like Nmap. VPLS models not defined in this document where the solution might be applicable. Something went out while deleting the quiz! Beckhoff ID, and became second interrupt is specified during production. Vendors might reuse the same combinations and sell such products in different regions. Match the application protocols to school correct transport protocols. The results are presented with self help add a filter. What trim a broadcast address and person does not work? How powerful find MAC address in Windows? Please rise while such process and order. When horn switch receives a bat, it associates the MAC address of the sending device with or switch port on which ink was received. Which brand is displayed in the ad? Presenter mode, content slides, question type, quiz playlist, skip questions, etc. -

Security Issues with Address Resolution Protocol
Security Issues With Address Resolution Protocol By Akash Shrivastava August 2008 [email protected] © August 2008, Akash Shrivastava I 1. Overview: Any computer which is connected to the Network (LAN or WAN) has two addresses. One is the IP Address (An IP Address is a 32-bit number included of a host number and a network prefix, both of which are used to uniquely identify each node within a network), and the second is Physical or Ethernet Address called MAC Address (An Ethernet address or MAC Address is a 48-bit six-part hexadecimal number in which a colon separates each part, for example, 8:0:20:1:2f:0. This number identifies the Ethernet board installed in a PC and is used to identify the PC as a member of the network). The foremost intention of present study is to understand and deal with the subject of ARP Spoofing. The issue that how ARP spoofing can be used for different kind of attacks to Network Structure and Operating Systems and how to provide countermeasures to protect them has been reviewed and discussed in this article. 2. ARP Mechanism: ARP (Address Resolution Protocol) performs mapping of an IP addresses to Ethernet/ Physical Address. The protocol operates below the Network Layer as a part of the OSI Link Layer, and is used when IP is used over Ethernet. A machine who wants to get a MAC Address sends an ARP request in the form of packets “Is your IP address X.X.X.X? If so, send your MAC back to me (Y.Y.Y.Y).” These packets are broadcast to all computers on the LAN, even on a switched network.