FTOS 8.3.17.0 Configuration Guide for the M I/O Aggregator
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Poweredge M1000e Blade Chassis
PowerEdge M1000e Blade Chassis The Dell PowerEdge M1000e Modular Blade Enclosure is the rock-solid foundation for Dell’s blade server architecture, providing an extremely reliable, flexible and efficient platform for building any IT infrastructure. The Dell PowerEdge M1000e Modular Blade Enclosure M1000e blade slot instead of directly to the blade. By is built from the ground up to combat data center removing the network and storage identity from the sprawl and IT complexity, delivering one of the most server hardware, customers are now able to upgrade and energy efficient, flexible, and manageable blade server replace components or the entire blade server without implementations on the market. being forced to change the identity on the network or rezoning switches. Unlike other solutions, which often Leading energy efficiency require separate management interfaces and proprietary The M1000e enclosure takes advantage of its world- hardware, FlexAddress will work with any network and is class design by coupling ultra-efficient power supplies implemented directly from the integrated CMC by simply with large variable-speed fans and optimized airflow to selecting the chassis slots and fabrics that you want effectively cool the entire chassis while using less power. to enable. FlexAddress delivers persistent network and Effortless scalability storage identities, equipping your data center to handle predictable or even unplanned changes — add, upgrade, Only Dell provides complete, scale-on-demand switch or remove servers without affecting your networks. designs. With additional I/O slots and switch options, you have the flexibility you need to meet ever-increasing Global services and support demands for I/O consumption. -

Dell Openstack Cloud Solution
Dell OpenStack Cloud Solution Peter Jung Senior Solutions Architect & Business Developer Fast. Easy. Now. Dell.com/OpenStack Dell.com/Crowbar Cloud expectations and promises Support the mobile & social marketplace Innovate and grow and workforce Anytime, anywhere, on any device access and Speed time to market when introducing new engagement. (BYOD) increases productivity and goods and services job satisfaction Apps Revenue Data “The Business” BI Cost Speed Efficiency Attract & retain new customers Reduce IT cost, deliver operational results On-demand, self-service and automated access Connect customer data, gain intelligence on lowers costs and decreases demands on IT customers to better target, nurture and solidify leads Cloud - Challenges for SP and Enterprise Service provider challenges Enterprise challenges • Cost-effectively scaling, and competing in the • Lack of infrastructure standardization and emerging public cloud ecosystem automation leading to poor resource utilization, cost escalation, slow application delivery • Ability to quickly launch new cloud services • Locked-in to proprietary vendors and • Keeping license costs down on traditional technologies – increasing license costs with virtualization solutions – costs increase linearly growth and scale with scale (often per node) • Poor understanding of cost allocations • Keeping maintenance costs down on home- grown components that have been built • Long resource provisioning cycle times haphazardly over time • Inflexible and non-adaptive infrastructure • Flexibility to rapidly add/change features in response to customer needs –commercial • Building a cloud is too complex and takes too solutions lack features they need long • Lack of availability and support of the entire end-to-end solution Cloud Taxonomy – Complex? Cloud service PaaS/SaaS management PaaS/SaaS services sit on top of this stack along with other any specific vertical solutions such as VDI, HPC, CDN etc. -

Dell Force10 MXL 10/40Gbe Switch
Dell Force10 MXL 10/40GbE Switch For Dell M1000e Blade Enclosures Expand the value of your blade investment with Dell Force10 MXL 10/40GbE switch, delivering performance and scalability in a flexible package that are designed to meet the shifting demands of your business and data center as it transitions from 1GbE to 1/10/40GbE. The MXL switch provides 1/10GbE connectivity on server facing ports for up to 32 M-Series blade servers equipped with the latest KR-based 10GbE network daughter cards (NDCs) or mezzanine cards. The switch offers 1/10/40GbE connectivity on the uplinks to interface with a top of rack switch, directly to the core, or directly to an Ethernet based SAN. The Force10 MXL switch has enhanced bandwidth, performance, and flexibility to satisfy the changing demands of data centers embracing virtualization, network convergence, and other I/O-intensive applications/workloads. Flexibility and Pay As You Grow With Powerful and Robust OS FlexIO Modules Dell Force10 Operating System (FTOS) is a robust and scalable The Dell Force10 MXL switch provides rich functionality operating system that comprises of feature rich Layer 2 and using 1/10/40GbE addressing the diverse needs of Layer 3 switching and routing functionality using industry environments ranging from data centers, large enterprises, standard CLI. The MXL switch brings this high performing and government networks, education/research, and high resilient FTOS deployed by some of today’s most demanding performance computing. The MXL switch supports 32 internal DC customers to the M1000e chassis. 1/10GbE ports, as well as two fixed 40GbE QSFP+ ports and offers two bays for optional FlexIO modules. -

Why the Dell / EMC Combination Makes Sense for Customers
Why the Dell / EMC Combination Makes Sense for Customers Synergistic product portfolio and go-to-market strategies have potential to set IT customers up for success in the digital economy Executive Summary One of the biggest technology deals in history at over $60 billion is about to unfold as Dell prepares to buy EMC. At EMC World in May 2016, Michael Dell made this acquisition more real than ever when he announced the new entity’s name, Dell Technologies, which will be an umbrella brand for the collection of companies that will include enterprise and client solutions and services, and other strategic assets including VMware, Pivotal, RSA, Virtustream, and SecureWorks. With just a few major milestones to go, it appears that all is on track for the companies to merge the enterprise organizations as Dell EMC under the umbrella brand and to begin operating as one by around mid-year. Dell and EMC are positioning themselves as the path to the cloud for IT customers. Moor Insights & Strategy (MI&S) believes Dell’s leadership in compute and EMC’s leadership in storage and converged infrastructure have the potential to become building blocks for a one-stop shop for enterprise datacenter customers. Other assets such as security, virtualization software, and cloud solutions can help round out the portfolio. Moreover, Dell’s client computing business and IoT practices can bring insight into client computing and IoT models that will be key drivers for future datacenter requirements. Dell EMC should focus on continuing to build up their networking business and making it a more cohesive part of their end-to-end datacenter story. -

Dell™ Poweredge™ 6950 Systems Hardware Owner’S Manual
Dell™ PowerEdge™ 6950 Systems Hardware Owner’s Manual www.dell.com | support.dell.com Notes, Notices, and Cautions NOTE: A NOTE indicates important information that helps you make better use of your computer. NOTICE: A NOTICE indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. CAUTION: A CAUTION indicates a potential for property damage, personal injury, or death. ____________________ Information in this document is subject to change without notice. © 2006 Dell Inc. All rights reserved. Reproduction in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell, the DELL logo, Inspiron, Dell Precision, Dimension, OptiPlex, Latitude, PowerEdge, PowerVault, PowerApp, Dell OpenManage, and Dell XPS are trademarks of Dell Inc.; Intel, Pentium, Xeon, and Celeron are registered trademarks of Intel Corporation; Microsoft and Windows are registered trademarks of Microsoft Corporation. Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own. Model EMU01 September 2006 P/N PM296 A00 Contents 1 About Your System. 9 Other Information You May Need . 9 Accessing System Features During Startup . 10 Front-Panel Features and Indicators . 11 Hard-Drive Indicator Codes. 13 Back-Panel Features and Indicators . 14 Connecting External Devices . 14 Power Indicator Codes. 15 NIC Indicator Codes . 16 LCD Status Messages . 16 Solving Problems Described by LCD Status Messages . 23 Removing LCD Status Messages . 24 System Messages . -

Buyer's Guide to Dell Power Distribution Units
Buyer’s Guide to Dell Power Distribution Units With data center devices smaller than ever, often served by dual- or triple-power supplies, a single rack of equipment might produce 80 or more power cords to manage. You want to minimize the number of expensive power drops to each rack, yet power consumption keeps rising—from 600 to 1000 watts per U and growing. Furthermore, power demands can easily double or triple during peak periods and fluctuate with every move, addition, or change. Adding a 1U or 2U server used to mean drawing 300 to 500 more watts from the branch circuit; now, a new blade server can consume ten times as much current. Traditional power strips simply do not deliver enough power, flexibility, or control for today’s realities. You need an effective way to manage the tangle of power cords, deliver the required power without taking up valuable rack space, and have visibility into current draw at any time. Dell™ power distribution units (PDUs) were designed with your needs in mind. These rugged, space-saving devices distribute from 3.6kW to 22kW of power (single-phase or three-phase) to up to 42 sockets/receptacles in a single unit, with or without onboard metering and remote communications. Dell PDUs offer the following key advantages: Right out of the box, Dell PDUs work seamlessly with your Dell servers, storage, and desktop equipment. All models that support network communications integrate with the Dell Management Console powered by Altiris™ from Symantec™ to enable a consolidated infrastructure overview. Vertical models feature true toolless rack mounting. -

Dell Networking Openmanage Network Manager 6.0 Powerful Management for Dell and Third-Party Networking Environments
Dell Networking OpenManage Network Manager 6.0 Powerful management for Dell and third-party networking environments Easily manage your entire Dell network • Resource group management provides one-to-many switching infrastructure with Dell OMNM switch configuration • Inventory reporting shows what you have and where is Growing networks can be a headache for today’s IT located organizations. Keeping track of the devices in your network and how they relate to each other and to other parts of your • Advanced scheduling schedules key tasks, such as backup infrastructure can be difficult and time consuming. OMNM and configuration changes is designed to make it easier to plan and manage your Dell, • Event management filters and forwards events and traps Cisco, HP, Juniper and Brocade network devices. • Customizable web based user interface Single pane of glass for all your Dell networking • Monitoring provides flexible dashboards for fault, management requirements availability and performance monitoring Unify your network element management and simplify Supported operating system (64-bit) deployment of Dell and third-party networking environments • MSFT Window 2012 with a rich suite of tools available in OMNM, an integrated • Windows Server 2008 R2 management console for all your important network management functions. • Linux for Redhat and CentOS v6.2/v6.4 OMNM’s centralized management solution for Dell networking Supported web browsers environments provides discovery, configuration management, • Chrome (version 6 and above) monitoring and reporting for the entire Dell Networking family • Safari (version 5 and above of products and select third-party products • Firefox (version 3.6 and above) — right out of the box and at no cost to you. -

Dell Poweredge M420
www.dell.com/QRL/Server/PEM420 Dell PowerEdge M420 The Dell™ PowerEdge™ M420 quarter-height blade server delivers unprecedented computational density, allowing up to 32 individually serviceable blade servers per chassis, with no compromise on enterprise-class features. Enjoy remarkable computational density with the PowerEdge M-series blade PowerEdge M420, capable of deploying 32 server nodes in just 10U of rack space. Scaling up to 16 server line processor cores and 192GB of RAM, each M420 Implement the right combination of features and couples processing power and memory capacity with performance scalability with the PowerEdge M-series tremendous I/O throughput, with up to four ports of blade servers, which can handle tough workloads in 10Gb ethernet available in an exceptionally compact, any size data centers. In addition to the world-class individually serviceable form factor. From entry and management features provided in all PowerEdge mid-tier business applications, to high node-count servers, the M420 also takes advantage of the virtual environments, and even distributed workloads capabilities of the M1000e Chassis Management such as cloud or high perfromance computing Controller (CMC). The CMC allows M-series blades (HPC) environments, the M420 provides advantages to be managed individually or as groups, in single for virtually any data center where a large number or multiple chassis, and within a data center or of computational nodes need to be deployed in in multiple geographically dispersed locations minimal space. around the globe without requiring a single agent or additional hardware. In addition to the existing Ensure business continuity networking infrastructure, the new Dell Force10 Dell’s no-compromise approach towards MXL 10Gb switch provides next-generation port enterprise-class features on our M-series blade density and bandwidth for exceptional throughput. -

Dell EMC Poweredge T440 Technical Guide
Dell EMC PowerEdge T440 Technical Guide December 2020 Rev. A06 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2019 - 2020 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. Contents Figures..........................................................................................................................................5 Tables........................................................................................................................................... 6 Chapter 1: System overview.......................................................................................................... 7 Introduction...........................................................................................................................................................................7 New technologies................................................................................................................................................................ 7 Chapter 2: System features.......................................................................................................... 9 Product comparison............................................................................................................................................................9 -

Active Voice
SUCCESS STORY GSD&M Advertising CHALLENGE SOLUTION BENEFIT Devise an IT strategy to support the fast growth of Deploy Dell™ PowerEdge™ servers running the Standardized Dell and Microsoft¨ server infra- GSD&M Advertising, as well as keep up with the Microsoft¨ Windows Server™ operating system, structure delivers excellent reliability, allowing the fast-paced nature of the advertising business; pro- Oracle 10g and VMware¨ virtualization software; IT department to think highly strategically; Dell vide an IT infrastructure that enables the agency a Dell/EMC CX700 storage area network (SAN); scalable enterprise strategy helps GSD&M to to be more creative than the competition Dell OptiPlex™ desktops and Latitude™ notebooks; respond rapidly to the needs of new clients; Dell Dell OpenManage™ software, with the Altiris¨ delivers a very positive ROi—“with an uppercase Management Suite¨; Dell Enterprise Platinum ‘R’ and a lowercase ‘i’” Support; Dell Financial Services™ How to Get Ahead in Advertising A complete portfolio of Dell servers, storage, personal computers, and services sends GSD&M on its excellent ad venture ustin, Texas, is a long way from Madison Avenue, but that has storage. Then, it went shopping for an alternative supplier that Anot stopped GSD&M from rising to the top of the ad game. could keep up with the breakneck speed of the ad business. Maybe that explains why the full-service advertising agency— “The impetus for switching to Dell was fast delivery of which has 750 employees and $14 billion in annual billings—calls equipment—from the factory and to our employees,” Rios explains. its hometown in the Lone Star State “Idea City.” To be sure, the big “With our previous suppliers, it seemed like it would take a long ideas at GSD&M have helped it attract an all-star client list that time from the time when the order was placed to the time we includes Wal-Mart, Southwest Airlines, and the PGA TOUR. -

Poweredge C Series Platforms Deliver the Latest High Speed Memory, Fast Nvme Storage and Workload-Based BIOS Tuning
PowerEdge Quick Reference Guide PowerEdge C-Series Data centers are undergoing a transformation to meet the demands of the digital economy. Built for scale-out workloads like high performance computing, deep learning and data analytics, Dell EMC PowerEdge C series platforms deliver the latest high speed memory, fast NVMe storage and workload-based BIOS tuning. Scale efficiently and predictably with flexible configurations and advanced connectivity options. Take advantage of new factory integrated Direct Contact Liquid Cooling for improved power efficiency.* And with intelligent automation, you can empower your team, freeing them from routine maintenance. Future- proof your data center with the worry-free and flexible PowerEdge C Series portfolio. Specifications C6520 C6525 C6420 C4140 Dense compute server designed to boost High Performance Dense-computing Dense, performance-optimized compute Faster time to insights with data center performance and address node for scale-out workloads. ultra-dense accelerator optimized server extreme compute at scale platform. High performance computing, Web scale Ideal workloads High Performance Computing (CAE, Cognitive workloads such as artificial High performance computing, Digital applications and SaaS, high performance big Research, Geophysics and massive parallel intelligence, machine learning, deep learning Manufacturing, Research, Web Tech/Hosting, data analytics, financial modeling and high computing), Web Tech, Financial Modeling, and for technical computing in for financial hyper-converged -
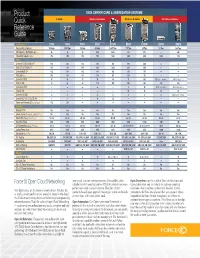
Product Quick Reference Guide
Product DATA CENTER CORE & AGGREGATION SYSTEMS Quick C-SERIES TERASCALE E-SERIES EXASCALE E-SERIES ZETTASCALE Z-SERIES Reference Guide ne rate 100GbE Performance: C150 C300 E300 E600 E1200 E600i E1200i Z9000 Z9512 Raw Switching Capacity 768 Gbps 1.536 Tbps 400 Gbps 900 Gbps 1.6875 Tbps 1.75 Tbps 3.5 Tbps 2.5 Tbps 16.8 Tbps Slot Capacity – Half Duplex (Gbps) 96 96 25 56.25 56.25 125 125 — 400 Forwarding Capacity (Mpps) 476 952 196 500 1,000 1,042 2,083 1,904 7,142 Ports: Line-rate 10/100/1000Base-T 192 384 132 336 672 630 1,260 — — Total 10/100/1000Base-T 192 384 288 630 1,260 630 1,260 — — Line-rate GbE (SFP) 192 384 132 336 672 350 700 — — Total GbE (SFP) 192 384 144 336 672 350 700 — — Line-rate 10 GbE 32 64 12 28 56 70 140 128 (QSFP+ breakout) 480 (10 GbE SFP+) Total 10 GbE 32 64 48 112 224 280 560 128 480 Line-rate 40 GbE — — — — — 14 28 32 (40 GbE QSFP+) 96 (40 GbE QSFP+) Total 40 GbE — — — — — 28 56 32 96 Line-rate 100 GbE — — — — — — — — 48 (Line rate 100 GbE) Line-rate OC-3c/OC-12c/OC-48c — — — 28 56 — — — — Power over Ethernet (IEEE 802.3af Class 3) 192 384 — — — — — — — Features: Modular FTOS Yes Yes Yes Yes Yes Yes Yes Yes Yes Industry-standard CLI (Console, Telnet, SSHv1/v2) Yes Yes Yes Yes Yes Yes Yes Yes Yes Max VLANs (Configured / Choices) 1K / 4K 1K / 4K 4K / 4K 4K / 4K 4K / 4K 4K / 4K 4K / 4K 4k / 4k 4k / 4k Max MAC Entries 256K 512K 192K 448K 896K 784K 1,568K 128K 1M Link Aggregation (Groups / Members) 128 / 8 128 / 8 255 / 16 255 / 16 255 / 16 32 / 64 or 255 / 8 32 / 64 or 255 / 8 128 / 8 256 / 64 Jumbo Frames (Bytes)