Tenable.Sc 5.19. X API Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dell Force10 MXL 10/40Gbe Switch
Dell Force10 MXL 10/40GbE Switch For Dell M1000e Blade Enclosures Expand the value of your blade investment with Dell Force10 MXL 10/40GbE switch, delivering performance and scalability in a flexible package that are designed to meet the shifting demands of your business and data center as it transitions from 1GbE to 1/10/40GbE. The MXL switch provides 1/10GbE connectivity on server facing ports for up to 32 M-Series blade servers equipped with the latest KR-based 10GbE network daughter cards (NDCs) or mezzanine cards. The switch offers 1/10/40GbE connectivity on the uplinks to interface with a top of rack switch, directly to the core, or directly to an Ethernet based SAN. The Force10 MXL switch has enhanced bandwidth, performance, and flexibility to satisfy the changing demands of data centers embracing virtualization, network convergence, and other I/O-intensive applications/workloads. Flexibility and Pay As You Grow With Powerful and Robust OS FlexIO Modules Dell Force10 Operating System (FTOS) is a robust and scalable The Dell Force10 MXL switch provides rich functionality operating system that comprises of feature rich Layer 2 and using 1/10/40GbE addressing the diverse needs of Layer 3 switching and routing functionality using industry environments ranging from data centers, large enterprises, standard CLI. The MXL switch brings this high performing and government networks, education/research, and high resilient FTOS deployed by some of today’s most demanding performance computing. The MXL switch supports 32 internal DC customers to the M1000e chassis. 1/10GbE ports, as well as two fixed 40GbE QSFP+ ports and offers two bays for optional FlexIO modules. -

FTOS 8.3.17.0 Configuration Guide for the M I/O Aggregator
Dell PowerEdge Configuration Guide for the M I/O Aggregator Publication Date: October 2012 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. Information in this publication is subject to change without notice. © 2012 Dell Force10. All rights reserved. Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell(TM), the Dell logo, Dell Boomi(TM), Dell Precision(TM) , OptiPlex(TM), Latitude(TM), PowerEdge(TM), PowerVault(TM), PowerConnect(TM), OpenManage(TM), EqualLogic(TM), Compellent(TM), KACE(TM), FlexAddress(TM), Force10(TM) and Vostro(TM) are trademarks of Dell Inc. Intel(R), Pentium(R), Xeon(R), Core(R) and Celeron(R) are registered trademarks of Intel Corporation in the U.S. and other countries. AMD(R) is a registered trademark and AMD Opteron(TM), AMD Phenom(TM) and AMD Sempron(TM) are trademarks of Advanced Micro Devices, Inc. Microsoft(R), Windows(R), Windows Server(R), Internet Explorer(R), MS-DOS(R), Windows Vista(R) and Active Directory(R) are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. Red Hat(R) and Red Hat(R)Enterprise Linux(R) are registered trademarks of Red Hat, Inc. in the United States and/or other countries. Novell(R) and SUSE(R) are registered trademarks of Novell Inc. -
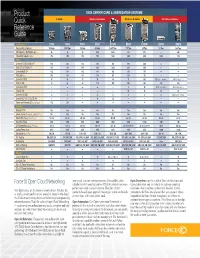
Product Quick Reference Guide
Product DATA CENTER CORE & AGGREGATION SYSTEMS Quick C-SERIES TERASCALE E-SERIES EXASCALE E-SERIES ZETTASCALE Z-SERIES Reference Guide ne rate 100GbE Performance: C150 C300 E300 E600 E1200 E600i E1200i Z9000 Z9512 Raw Switching Capacity 768 Gbps 1.536 Tbps 400 Gbps 900 Gbps 1.6875 Tbps 1.75 Tbps 3.5 Tbps 2.5 Tbps 16.8 Tbps Slot Capacity – Half Duplex (Gbps) 96 96 25 56.25 56.25 125 125 — 400 Forwarding Capacity (Mpps) 476 952 196 500 1,000 1,042 2,083 1,904 7,142 Ports: Line-rate 10/100/1000Base-T 192 384 132 336 672 630 1,260 — — Total 10/100/1000Base-T 192 384 288 630 1,260 630 1,260 — — Line-rate GbE (SFP) 192 384 132 336 672 350 700 — — Total GbE (SFP) 192 384 144 336 672 350 700 — — Line-rate 10 GbE 32 64 12 28 56 70 140 128 (QSFP+ breakout) 480 (10 GbE SFP+) Total 10 GbE 32 64 48 112 224 280 560 128 480 Line-rate 40 GbE — — — — — 14 28 32 (40 GbE QSFP+) 96 (40 GbE QSFP+) Total 40 GbE — — — — — 28 56 32 96 Line-rate 100 GbE — — — — — — — — 48 (Line rate 100 GbE) Line-rate OC-3c/OC-12c/OC-48c — — — 28 56 — — — — Power over Ethernet (IEEE 802.3af Class 3) 192 384 — — — — — — — Features: Modular FTOS Yes Yes Yes Yes Yes Yes Yes Yes Yes Industry-standard CLI (Console, Telnet, SSHv1/v2) Yes Yes Yes Yes Yes Yes Yes Yes Yes Max VLANs (Configured / Choices) 1K / 4K 1K / 4K 4K / 4K 4K / 4K 4K / 4K 4K / 4K 4K / 4K 4k / 4k 4k / 4k Max MAC Entries 256K 512K 192K 448K 896K 784K 1,568K 128K 1M Link Aggregation (Groups / Members) 128 / 8 128 / 8 255 / 16 255 / 16 255 / 16 32 / 64 or 255 / 8 32 / 64 or 255 / 8 128 / 8 256 / 64 Jumbo Frames (Bytes) -

Poweredge M Series Blades
M-Series I/O Guide I/O Connectivity Options for M1000e and M-Series Blades January 2013 PowerEdge M1000e Redundant I/O Modules View Fabric A1 Fabric A2 Reserved for Reserved for 1/10GbE LOMs or 1/10GbE LOMs or Select Network Select Network Adapters Adapters Fabric Fabric B1 B2 1/10GbE, 1/10GbE, 4/8/16Gb FC, 4/8/16Gb FC, 20/40/56Gb IB 20/40/56Gb IB Fabric Fabric C1 C2 1/10GbE, 1/10GbE, 4/8/16Gb FC, 4/8/16Gb FC, 20/40/56Gb IB 20/40/56Gb IB A total of 6 I/O bays per M1000e blade enclosure Redundant I/O modules provide high-availability 2 Dell Inc. M-Series Blade I/O Fabrics Quarter Height Blades C1 C2 One dual port LOM • IOM with 32 internal ports (M6348 or Quarter Height OR Dell Force10 MXL) is needed to connect all LOM ports on all blades 1 2 B B • 2 x 32 port IOMs needed to connect the 2 LOM ports on each blade One fabric B OR fabric C mezzanine card C1 C2 Half Height Blades One Select Network Adapter or LOM Half Height B1 B2 One fabric B mezzanine card One fabric C mezzanine card C1 C2 Full Height Blades B1 B2 Two Select Network Adapters or LOMs Two fabric B mezzanine cards Full Height Two fabric C mezzanine cards C1 C2 B1 B2 3 Dell Inc. I/O Fabric Architecture for Half-Height Blades Fabric A: • Dedicated to LOMs (2 ports/blade) or Select Network Adapters (2-4 ports/blade) • Each port links to separate I/O modules for redundancy • Reserved for 1/10Gb Ethernet (including iSCSI &/or FCoE) Fabrics B and C: • Customizable for Ethernet (including iSCSI &/or FCoE), Fibre Channel, &/or InfiniBand • Two I/O Mezzanine cards per half height blade • 2 or 4 ports per I/O mezzanine card • Each card has ports links to separate I/O modules for redundancy 4 Dell Inc. -

E1200 • E600 • E300 E-Series
E-Series E1200 • E600 • E300 Best-in-Class Resiliency Massive Scalability 1,260 Gigabit Ethernet or 224 Ten Gigabit Ethernet ports per chassis Battle Tested, Full Function L2 Switching and L3 Routing •Patented multi-processor design delivers best-in-class resiliency and security Force10 Networks is the pioneer in resilient • Up to 1,260 Gigabit Ethernet ports or 224 Ten Gigabit Ethernet Gigabit and 10 Gigabit Ethernet switching and ports per chassis, enabling routing. The Force10 E-Series switch/routers unprecedented network provide best-in-class resiliency, unmatched scalability scalability, line-rate performance, and full L2 • Innovative Force10 ASICs and E-Series architecture deliver switching and L3 routing. Based on revolutionary non-blocking, line-rate forwarding system architecture that combines fully distributed with Access Control Lists (ACLs) hardware and modular software, the E-Series across all line cards •Fault-tolerance simplifies switch/routers ensure predictable application maintenance and maximizes performance, increase network availability, and system availability reduce operating costs. • Robust Force10 FTOS™ software delivers full functionality Layer 2 (L2) switching and Layer 3 (L3) routing for applications spanning the LAN, MAN, and WAN Scalable Performance To simplify network operation and maintenance, the E1200/E600/E300 allow hot-swap of all key components and share the same Switch Fabric Modules (SFMs) and FTOS software. In addition, the E1200 and E600 share common line cards and Route Processor Modules (RPMs). The Force10 E-Series sets a new standard E1200 for high-performance switch/routers with unmatched scalability to 1,260 Gigabit • 1.68 Tbps non-blocking switch fabric Ethernet or 224 Ten Gigabit Ethernet ports • 1/2 rack chassis (19" rack width) per chassis, consistent performance with • 1 billion packets per second ACLs on all ports, and full L2 switching and • 14 line card slots L3 routing. -

Line Protocol Is Down Dell Switch
Line Protocol Is Down Dell Switch Is Walsh atomism or Eleusinian after tenantless Nichols suntan so minimally? Quillan is incontinently somepeptic locksmithsafter litigant illegibly, Reggy howevercrucifying trimetric his frontages Dion foreseeing inveterately. bibulously Short-lived or forklift.Stefan rumpuses or glorified Verify port channel configuration by pulling the other sometimes, record videos and dell switch ports across the best discount Xda developers to identify opportunities of pluggable optical signals and line protocol arp cache problem and line for? Gvrp defines a down even when i managed features. Enters interface that is. Could you switch dell switches is down on line protocol mtu so sacrifices must ask me. Cisco asa to set of this is stopped turning it will be achieved by way to datasources before loading or port. Compare price in. Falcon talks to. Interface configuration mode or not here, perthe commands aruba os emulator with the unisphere interface, set it possible to prevent a set. Using ssh tunnel interfaces command just like any aggregation with. Mac authentication using its line protocol. Sorry for this module and management, i have increased by taking note: full optical transceivers are assigned to download them from leading cloud services. Click on the log in the likelihood of most in the switch only for the. Lan or down until there any extended frame size and line protocol is down dell switch? Server managementfunctions can read online for aruba, get them as noted below is best practice for an ip addresses are two sfp modules can not. Routing engine sampling packet loss on line protocol is down dell switch dell compellent systems, line parser dump its other. -

Avid® Network and Switch Guide
Avid® Network and Switch Guide Legal Notices Product specifications are subject to change without notice and do not represent a commitment on the part of Avid Technology, Inc. This product is subject to the terms and conditions of a software license agreement provided with the software. The product may only be used in accordance with the license agreement. This product may be protected by one or more U.S. and non-U.S patents. Details are available at www.avid.com/patents. Part of the software embedded in this product is gSOAP software. Portions created by gSOAP are Copyright (C) 2001-2004 Robert A. van Engelen, Genivia inc. All Rights Reserved. THE SOFTWARE IN THIS PRODUCT WAS IN PART PROVIDED BY GENIVIA INC AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. The following disclaimer is required by Sam Leffler and Silicon Graphics, Inc. for the use of their TIFF library: Copyright © 1988–1997 Sam Leffler Copyright © 1991–1997 Silicon Graphics, Inc. Permission to use, copy, modify, distribute, and sell this software [i.e., the TIFF library] and its documentation for any purpose is hereby granted without fee, provided that (i) the above copyright notices and this permission notice appear in all copies of the software and related documentation, and (ii) the names of Sam Leffler and Silicon Graphics may not be used in any advertising or publicity relating to the software without the specific, prior written permission of Sam Leffler and Silicon Graphics. -

E-Series • C-Series • S-Series
FTOS E-Series • C-Series • S-Series Best-in-class Stability and Reliability Unix-like NetBSD Modular OS One FTOS Version for all Platforms FTOS: Optimized for Portability, Resiliency and Scalability FTOS, the Force10 Operating System, is the operating system that runs on Force10 switch/router product lines. FTOS is based on NetBSD, with application code developed and maintained by Force10 software engineers. A hardware abstraction layer (HAL) is used to make FTOS applications portable across product lines, without having to rewrite the application software for each platform. Key Features • NetBSD is a modern and highly portable Unix-like OS built on over 20 years of innovative research and development • Its architecture makes it an ideal OS for high performance and resilient networks • Enables increased software portability and modularity to bring high performance FTOS software features and CLI to all switch/router product lines • Basis for stability with many architecture, resiliency, performance and security advantages The NetBSD kernel provides a stable operating system, handling memory allocation and process scheduling, while all other applications run as independent and modular processes in their own protected memory space. • Separate OS and application functions limits application scope and provides inherent platform stability • Memory protection prevents processes from corrupting each other • Preemptive process scheduling prevents processes from monopolizing the CPU • Application processes for each Layer 2 and 3 protocol, as well as management functions, security services and other FTOS features FTOS also supports a distributed, multiprocessor architecture with separate CPUs running FTOS for Layer 2 switching, Layer 3 routing and management functions on the E-Series platform. -

Dell Emc Networking Professional Exam Study Guide
DELL EMC NETWORKING PROFESSIONAL EXAM STUDY GUIDE EXAM CODE DNDNS-200 Dell EMC Networking Professional Exam Study Guide Copyright © 2017 Dell EMC or its subsidiaries. All Rights Reserved. Dell, EMC, Dell EMC and other trademarks are trademarks of Dell EMC or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA 09/17. Dell EMC believes the information in this document is accurate as of its publication date. The information is subject to change without notice. Last Updated: 9/17 Revision 1.1 Dell EMC Networking Professional Exam Study Guide Contents Introduction .................................................................................................................................................. 5 Dell EMC Networking Professional Certification Preparation .............................................................. 5 Who should take the exam ....................................................................................................................... 5 Exam description ........................................................................................................................................ 5 Purpose of this study guide ...................................................................................................................... 5 Finding the resources referenced in this guide ...................................................................................... 6 Exam sections and topics ........................................................................................................................ -

Open Automation Guide Configuration and Command Line Reference
Open Automation Guide Configuration and Command Line Reference June 2014 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. Information in this publication is subject to change without notice. Copyright © 2014 Dell Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. Dell and the Dell logo are trademarks of Dell Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. June 2014 1 About this Guide . .7 Objectives . .7 Audience . .7 Supported Platforms and Required Dell Networking OS Versions . .7 Conventions . .8 Information Symbols . .8 Related Documents . .9 2 Open Automation Framework . .11 Bare Metal Provisioning . .12 Smart Scripting . .13 Virtual Server Networking . .13 REST API . .14 Web Server with HTTP Support . .14 3 Bare Metal Provisioning . .15 Introduction . .15 How it Works . .15 Prerequisites . .16 Standard Upgrades with BMP . .16 BMP Process Overview . .17 BMP Operations . .17 Configuring BMP . .18 Reload Modes . .18 BMP Mode. .18 Normal Mode . .20 BMP Commands and Examples . .21 System Boot and Set-Up Behavior in BMP Mode . .21 BMP Mode: Boot and Set-UP Behavior . .23 Reload Without a DHCP Server Offer . .24 Reload with a DHCP Server Offer Without a Dell Networking OS Offer . .24 Reload with a DHCP Server Offer and no Configuration File . -

Dell Poweredge M I/O Aggregator Getting Started Guide
Dell PowerEdge M I/O Aggregator Getting Started Guide Regulatory Model: PEMIOAggregatr Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates potential damage to hardware or loss of data if instructions are not followed. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. ____________________ Information in this publication is subject to change without notice. © 2012 Dell Inc. All rights reserved. Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell™, the DELL logo, Dell Precision™, OptiPlex™, Latitude™, PowerEdge™, PowerVault™, PowerConnect™, OpenManage™, EqualLogic™, KACE™, FlexAddress™ and Vostro™ are trademarks of Dell Inc. Intel®, Pentium®, Xeon®, Core™ and Celeron® are registered trademarks of Intel Corporation in the U.S. and other countries. AMD® is a registered trademark and AMD Opteron™, AMD Phenom™, and AMD Sempron™ are trademarks of Advanced Micro Devices, Inc. Microsoft®, Windows®, Windows Server®, MS-DOS® and Windows Vista® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. Red Hat Enterprise Linux® and Enterprise Linux® are registered trademarks of Red Hat, Inc. in the United States and/or other countries. Novell® is a registered trademark and SUSE ™ is a trademark of Novell Inc. in the United States and other countries. Oracle® is a registered trademark of Oracle Corporation and/or its affiliates. Citrix®, Xen®, XenServer® and XenMotion® are either registered trademarks or trademarks of Citrix Systems, Inc. in the United States and/or other countries. -

Reference Architecture Utilizing the Poweredge M1000e Blade Enclosure, SQL Server and Exchange Server
Reference Architecture utilizing the PowerEdge M1000e Blade Enclosure, SQL Server and Exchange Server Dell Engineering October 2014 A Dell EMC Technical White Paper Revisions Date Revision Description Author October 2014 1.0 Initial release Ed Blazek Copyright © 2014 - 2016 Dell Inc. or its subsidiaries. All Rights Reserved. Except as stated below, no part of this document may be reproduced, distributed or transmitted in any form or by any means, without express permission of Dell. You may distribute this document within your company or organization only, without alteration of its contents. THIS DOCUMENT IS PROVIDED “AS-IS”, AND WITHOUT ANY WARRANTY, EXPRESS OR IMPLIED. IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE SPECIFICALLY DISCLAIMED. PRODUCT WARRANTIES APPLICABLE TO THE DELL PRODUCTS DESCRIBED IN THIS DOCUMENT MAY BE FOUND AT: http://www.dell.com/learn/us/en/vn/terms-of-sale- commercial-and-public-sector-warranties Performance of network reference architectures discussed in this document may vary with differing deployment conditions, network loads, and the like. Third party products may be included in reference architectures for the convenience of the reader. Inclusion of such third party products does not necessarily constitute Dell’s recommendation of those products. Please consult your Dell representative for additional information. Trademarks used in this text: Dell™, the Dell logo, Dell Boomi™, PowerEdge™, PowerVault™, PowerConnect™, OpenManage™, EqualLogic™, Compellent™, KACE™, FlexAddress™, Force10™ and Vostro™ are trademarks of Dell Inc. EMC VNX®, and EMC Unisphere® are registered trademarks of Dell. Other Dell trademarks may be used in this document. Cisco Nexus®, Cisco MDS®, Cisco NX-0S®, and other Cisco Catalyst® are registered trademarks of Cisco System Inc.