Harasimowicz Washington 025
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cloud Fonts in Microsoft Office
APRIL 2019 Guide to Cloud Fonts in Microsoft® Office 365® Cloud fonts are available to Office 365 subscribers on all platforms and devices. Documents that use cloud fonts will render correctly in Office 2019. Embed cloud fonts for use with older versions of Office. Reference article from Microsoft: Cloud fonts in Office DESIGN TO PRESENT Terberg Design, LLC Index MICROSOFT OFFICE CLOUD FONTS A B C D E Legend: Good choice for theme body fonts F G H I J Okay choice for theme body fonts Includes serif typefaces, K L M N O non-lining figures, and those missing italic and/or bold styles P R S T U Present with most older versions of Office, embedding not required V W Symbol fonts Language-specific fonts MICROSOFT OFFICE CLOUD FONTS Abadi NEW ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Abadi Extra Light ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Note: No italic or bold styles provided. Agency FB MICROSOFT OFFICE CLOUD FONTS ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Agency FB Bold ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Note: No italic style provided Algerian MICROSOFT OFFICE CLOUD FONTS ABCDEFGHIJKLMNOPQRSTUVWXYZ 01234567890 Note: Uppercase only. No other styles provided. Arial MICROSOFT OFFICE CLOUD FONTS ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Arial Italic ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Arial Bold ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 01234567890 Arial Bold Italic ABCDEFGHIJKLMNOPQRSTUVWXYZ -

IJRESS19-August2020
International Journal of Research in Economics and Social Sciences(IJRESS) Available online at: http://euroasiapub.org Vol. 10 Issue 8, August- 2020 ISSN(o): 2249-7382 | Impact Factor: 7.077 | (An open access scholarly, peer-reviewed, interdisciplinary, monthly, and fully refereed journal.) Importance of the number 0 and names for the number 0 in English Umarova Go’zalxon Teacher, Kokand State Pedagogical Institute, Uzbekistan Abdullayeva Marifatxon Teacher, Faculty of Preschool and Primary Education Annotatsiya: Maqolada 0 raqimining etimologiyasi, osiyodan yevropaga kirib kelishi, matematika va matematikadan boshqa fanlarga, yil jadvalida nol raqamining ahamiyati haqida fikr yuritiladi. Kalit so’zlar: ṣifr, matematik termin, kalkulyator, rim, arab raqamlari, elementar algebra Annotation: The article discusses the etymology of the number 0, its entry from Asia to Europe, the importance of the number zero in the table of the year, from mathematics and non-mathematics to other disciplines. Keywords: ṣifr, mathematical term, calculator, Roman, Arabic numerals, elementary algebra Аннотация: В статье обсуждается этимология числа 0, его проникновение из Азии в Европу, важность числа ноль в таблице года, от математики и нематематики до других дисциплин. Ключевые слова: ifr, математический термин, калькулятор, римские, арабские цифры, элементарная алгебра. The word zero came into the English language via French zéro from Italian zero, Italian contraction of Venetian zevero form of Italian zefiro via ṣafira or ṣifr.In pre-Islamic time the word ṣifr had the meaning "empty". Sifr evolved to mean zero when it was used to translate śūnya Sanskrit from India. The first known English use of zero was in 1598.[1]Depending on the context, there may be different words used for the number zero. -

Typotheque Elementar
Typotheque type specimen & OpenType feature specification. Please read before using the fonts. OpenType font family supporting Latin based European Elementar Std languages, with extensive typographic features. AB — Western European (1252 Latin 1) — Central European (1250 Latin 2) — Baltic (1257) — Turkish (1254) Designed by Gustavo Ferreira, 2002-2011 OpenType features in Elementar hiztvsgfq What is OpenType? OpenType is a cross-platform font format developed by Adobe and Microsoft. It has a potential to provide advanced typographic features such as multilingual character sets, ligatures, small capitals, various numeral styles, and contextual substitutions. OpenType, as the new industry standard, supports Unicode, which enables the fonts to contain a large number of characters. While PostScript fonts are a technically limited to a maximum of only 256 characters, OpenType fonts can have more than 65,000 glyphs. This means that a user does not need to have separate fonts for Western, Central European, Baltic, Cyrillic or Greek languages, but could have one single file which supports all these encodings. OpenType fonts work in all applications, however only some applications take advantage of the advanced OpenType features. Other applications will only use the first 256 characters. For more about OpenType information go to www.typotheque. com/opentype © 2011, Typotheque.com. For information purposes only. complete character set © 2011, Typotheque.com. For information purposes only. © 2011, Typotheque.com. For information purposes only. © 2011, Typotheque.com. For information purposes only. About the Font Elementar is a parametric font system designed to bring more typographic flexibility to digital screens. Elementar embraces and explores the unique properties of digital media: the pixel, the coarse resolution grid, and the dimension of time. -

Amazon Fulfillment Web Service Developer Guide Version 1.1 Amazon Fulfillment Web Service Developer Guide
Amazon Fulfillment Web Service Developer Guide Version 1.1 Amazon Fulfillment Web Service Developer Guide Amazon Fulfillment Web Service: Developer Guide Copyright © 2010 Amazon Web Services LLC or its affiliates. All rights reserved. Amazon Fulfillment Web Service Developer Guide Table of Contents Welcome ............................................................................................................................................................. 1 What©s New ........................................................................................................................................................ 4 Introduction to Amazon FWS ............................................................................................................................. 6 Programming Guide ........................................................................................................................................... 9 About Requests and Responses ............................................................................................................ 9 SOAP Requests ............................................................................................................................ 9 Query Requests .......................................................................................................................... 11 Request Authentication ............................................................................................................... 12 What Is Authentication? .................................................................................................... -

Proposal to Represent the Slashed Zero Variant of Empty
L2/15-268 Title: Proposal to Represent the Slashed Zero Variant of Empty Set Source: Barbara Beeton (American Mathematical Society), Asmus Freytag (ASMUS, Inc.), Laurențiu Iancu and Murray Sargent III (Microsoft Corporation) Status: Individual contribution Action: For consideration by the Unicode Technical Committee Date: 2015-10-30 Abstract As of Unicode Version 8.0, the symbol for empty set is encoded as the character U+2205 EMPTY SET, with no standardized variation sequences. In scientific publications, the symbol is typeset in one of three var- iant forms, chosen by notational style: a slashed circle, ∅, a slashed wide oval in the shape a letter, ∅, or a slashed narrow oval in the shape of a digit zero, . The slashed circle and the slashed zero forms are the most widely used, and correspond to the LaTeX commands \varnothing and \emptyset, respectively. Having one Unicode representation to map to, fonts that provide glyphs for more than one form of the symbol typically implement a stylistic variant or a mapping to a PUA code point. However, the wide- spread use of the slashed zero variant and its mapping to the main LaTeX command for the symbol, \emptyset, make it a candidate for a dedicated means to distinctly represent it in Unicode. This document evaluates three approaches for representing in Unicode the slashed zero variant of the empty set symbol and proposes a solution based on a variation sequence. Additional related characters resulting from the investigation and needed to complete the solution are also proposed for encoding. 1. The empty set symbol 1.1. Historical references The introduction of the modern symbol for the empty set is attributed to André Weil of the Nicholas Bourbaki group. -
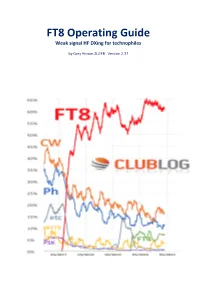
FT8 Operating Guide V2
FT8 Operating Guide Weak signal HF DXing for technophiles by Gary Hinson ZL2iFB Version 2.37 Note: this document is occasionally updated. The definitive latest English version is maintained at https://www.g4ifb.com/FT8_Hinson_tips_for_HF_DXers.pdf Please use and share that URL or the shortcut bit.ly/FT8OP to stay current. Any archived copies, translations and extracts lurking elsewhere on the Web are not under my control and are probably out of date … but it’s possible they are even better than this version! FT8 Operating Guide FT8 Operating Guide By Gary Hinson ZL2iFB 1 Introduction and purpose of this document ............................................................................... 2 2 START HERE ............................................................................................................................... 3 3 Important: accurate timing ........................................................................................................ 5 4 Important: transmit levels ......................................................................................................... 8 5 Important: receive levels ......................................................................................................... 11 6 Other software settings ........................................................................................................... 14 7 How to respond to a CQ, or call a specific station ..................................................................... 17 8 How to call CQ ........................................................................................................................ -

Libertine's Xetex-Documentation
Manual for L L with XƎTEX Advantages of XeTex over classic LaTex, examples of configuration Deutse Version ebenfalls erhältli. P H P Libertine Open Fonts Projekt http://linuxlibertine.sf.net Berlin, den 21. MÄarz 2009 Inhaltsverzeichnis 1 Advantages of XeTex 3 2 Commands 3 3 Choosing OpenType-features 4 3.1 Leers: ..................................... 4 3.2 Numbers/Figures: ............................... 4 3.3 Ligatures: .................................... 4 4 Links 4 5 Appendix 5 2 1 Advantages of XeTex ² Full Unicode-support. You can enter all Unicode-Glyphs directly into the source code. ² Simple usability of TrueType- and OTF-Fonts ² Full OpenType-support: { automatic substitution of standard activated OpenType-features, i.e. ligatures su as ff, fi, , , fl,ffi, ffl,, , … { shiing from Stylistic Sets, i.e. old style figures, proportional figures, ÄÖÜ as trema-leers, substitution of german ß with ss { true GPOS-kerning 2 Commands e XeTex-interpreter is being invocated via xelatex instead of latex or pdflatex, example: xelatex Document.tex e output is a PDF-file, ergo analog to our example as Dokument.pdf Because the interpreter needs to know wi fonts to use and because XeTex needs some special paages, the document heading looks a lile bit different from usual. Following commands should be entered into the heading: \usepackage{xunicode} \usepackage{fontspec} \usepackage{xltxtra} In contrast, the definition of the input encoding (inputenc) is obsolete, because XeTex consi- ders UTF-8. Some examples found in the internet begin with following META-information: %!TEX TS-program = xetex %!TEX encoding = UTF-8 Unicode though this doesn’t seem to be obligatory. ere are different possibilities to tell XeTex, whi fonts to use locally or globally. -

Typotheque Halte Font Family
Typotheque type specimen & OpenType feature specification. Please read before using the fonts. OpenType font family supporting Latin based languages with their own small caps, with extensive typographic features. 01 Halte OpenType features in Halte ewjduhiz tvnsgfq Designed by Hrvoje Živčić, 2018 What is OpenType? OpenType is a cross-platform font format developed by Adobe and Microsoft. It has a potential to provide advanced typographic features such as multilingual character sets, ligatures, small capitals, various numeral styles, and contextual substitutions. OpenType, as the new industry standard, supports Unicode, which enables the fonts to contain a large number of characters. While PostScript fonts are a technically limited to a maximum of only 256 characters, OpenType fonts can have more than 65,000 glyphs. This means that a user does not need to have separate fonts for Western, Central European, Baltic, Cyrillic or Greek languages, but could have one single file which supports all these encodings. OpenType fonts work in all applications, however only some applications take advantage of the advanced OpenType features. Other applications will only use the first 256 characters. © 2018, Typotheque.com. For information purposes only. character set ABCDEFGHIJKLMNOPQRSTUVWXYZ ([0123456789]) ÁÀÂÄÃÅĂĀĄÇĆČĈĊĎĐÉÈÊËĔĚĖĒẼĘĞĜĢĠĦĤÍIÌÎÏĬĪĮĨĴJ ĶĹĻĿŁÑŃŇŅṆNŊÓÒÔÖÕŎŐŌØǾPŔŘŖŚŞŠŜṢȘŦŤȚÚÙÛÜŬŰŪŲŮŨǓẂŴẄẀŸŶȲỲÝŹŽŻZÞÐÆǼǢŒ abcdefghijklmnopqrstuvwxyz ([0123456789]) áàâäãåăāąçćčĉċďđéèêëĕěėēẽęğĝģġħĥíıìîïĭīįĩĵjķĺļŀłñńňņṇnŋ óòôöõŏőōøǿpŕřŗśşšŝṣșŧťțúùûüŭűūųůũǔẃŵẅẁÿŷȳỳýźžżzþðæǽǣœ -
L2/17-294: Proposal to Add Standardized Variation Sequence For
L2/17-294 Universal Multiple-Octet Coded Character Set International Organization for Standardization Doc Type: Working Group Document Title: Proposal to add standardized variation sequence for U+FF10 FULLWIDTH DIGIT ZERO Author: Ken Lunde (Adobe Systems Incorporated) Status: Corporate Full Member Contribution Action: For consideration by the UTC Date: 2017-08-14 References: L2/15-268 Background Discussions of document L2/15-268 resulted in a small number of standardized variation sequences to be added in Unicode Version 9.0, including the following one that is directly relevant to this particular proposal: 0030 FE00; short diagonal stroke form; # DIGIT ZERO The Adobe-Japan1-6 glyph set, which is used as the basis for hundreds, and possibly thousands, of OpenType Japanese fonts, includes several “slashed zero” glyphs, three of which correspond to <U+0030,U+FE00>. The glyphs are CIDs 230 (proportional upright), 632 (half-width), and 9673 (proportional italic), all of which are uni- fied with U+0030 DIGIT ZERO.* Also included in this glyph set is a full-width version at CID+8228 that is a vari- ant of the glyph that maps from U+FF10 FULLWIDTH DIGIT ZERO. The table below shows the corresponding “slashed zero” glyphs from the Kozuka, Meiryo, Hiragino, and Heisei typeface families: Typeface Family Proportional Proportional Italic Half-Width Full-Width Kozuka Mincho 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ Kozuka Gothic 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ Meiryo 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ Hiragino Mincho 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ Hiragino Kaku Gothic 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ Heisei Mincho 0⌍⌌ 0⌍⌌ n/a 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ Heisei Kaku Gothic 0⌍⌌ 0⌍⌌ n/a 0⌍⌌ 0⌍⌌ 0⌍ ⌌0⌍ ⌌ * Also included in this glyph set are pre-rotated versions of these three glyphs at CIDs 8949 (CID+230), 9081 (CID+632), and 13189 (CID+9673) that are referenced by the effectively-deprecated OpenType 'vrt2' GSUB feature. -

Bankjet 2500 Programmer's Guide
Programmer’s Guide PN: 100-08072 Rev D Feb-2008 Change Log BANKjet® 2500 Programmer’s Guide Change Log Rev 1 Initial Draft Aug 2007 Rev 2 Second Draft Aug 2007 Rev 2 Added Wide Slip Zone commands. Updated statistics tables. Rev 3 Added Enhanced Page Mode Oct 2007 Rev A Initial Release Nov 2007 Rev B Dec 2007 Clarified the enter boot load instructions. Added reference to secondary boot loader document Rev C Jan 2008 Added a section on enhanced POR.INI options. Added a section on error indications Removed references to paper low. (The Bankjet 2500 does not support paper low) Changed the print zone from 2.83 to 2.67 inches. Rev D Added Hard error blink Error Chart Reformatted document. Removed sections. Page ii 100-08072 Rev D Feb-08 Programmer’s Guide BANKjet® 2500 General Information Feb-08 100-08072 Rev D Page iii Change Log BANKjet® 2500 Programmer’s Guide ® BANKjet 2500 Disclaimer © 2007 Transact Technologies, Inc. All rights reserved. NOTICE TO ALL PERSONS RECEIVING THIS DOCUMENT: The information in this document is subject to change without notice. No part of this document may be reproduced, stored or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of Transact Technologies, Inc. ("Transact"). This document is the property of and contains information that is both confidential and proprietary to Transact. Recipient shall not disclose any portion of this document to any third party. TRANSACT DOES NOT ASSUME ANY LIABILITY FOR DAMAGES INCURRED, DIRECTLY OR INDIRECTLY, FROM ANY ERRORS, OMISSIONS OR DISCREPANCIES IN THE INFORMATION CONTAINED IN THIS DOCUMENT. -

Communications of the Tex Users Group 2013 U.S.A
“The Internet is completely decent- ralized,” Mr. Rimovsky said. [anonymous] International Herald Tribune (14 September 1998) COMMUNICATIONS OF THE TEX USERS GROUP EDITOR BARBARA BEETON VOLUME 34, NUMBER 2 • 2013 PORTLAND • OREGON • U.S.A. 110 TUGboat, Volume 34 (2013), No. 2 TUGboat editorial information Suggestions and proposals for TUGboat articles are This regular issue (Vol. 34, No. 2) is the second gratefully accepted. Please submit contributions by elec- issue of the 2013 volume year. tronic mail to [email protected]. TUGboat is distributed as a benefit of member- Effective with the 2005 volume year, submission of ship to all current TUG members. It is also available a new manuscript implies permission to publish the ar- TUGboat to non-members in printed form through the TUG store ticle, if accepted, on the web site, as well as (http://tug.org/store), and online at the TUGboat in print. Thus, the physical address you provide in the web site, http://tug.org/TUGboat. Online publication manuscript will also be available online. If you have any to non-members is delayed up to one year after print reservations about posting online, please notify the edi- publication, to give members the benefit of early access. tors at the time of submission and we will be happy to Submissions to TUGboat are reviewed by volun- make special arrangements. teers and checked by the Editor before publication. How- TUGboat editorial board ever, the authors are still assumed to be the experts. Barbara Beeton, Editor-in-Chief Questions regarding content or accuracy should there- Karl Berry, Production Manager fore be directed to the authors, with an information copy Boris Veytsman, Associate Editor, Book Reviews to the Editor. -

Font Technology Opentype
FONT TECHNOLOGY OPENTYPE Information Brochure | 2011 URW++ DESIGN & DEVELOPMENT GMBH Poppenbütteler Bogen 36 22399 Hamburg | Germany TEL +49 (0)40 60605 0 FAX +49 (0)40 60605 111 [email protected] | www.urwpp.de ©2011 URW++ DESIGN & DEVELOPMENT GMBH A INTRODUCTION ++ | A | B1 | B2 | B3 | B4 | C | D | E 1.1 Introduction to OpenType OpenType is a cross-platform font format developed by Adobe and Microsoft. URW++ offers its complete typeface library of Latin fonts in OpenType format. This document focuses primarily on OpenType font technology covering character sets for Western and Eastern Europe. Standard Ligatures European Scripts Discretionary Ligatures Ordinals Middle Eastern Scripts Contextual Ligatures South Asian Scripts Historical Ligatures East Asian Scripts Ancient Scripts Symbols & Punctuation Ligatures Language Support Stylistic Alternates Contextual Alternates Randomize Historical Forms Alternate Annotation Forms Swashes OPENTYPE Alternates Contextual Swashes Capitals & Swashes Small Capitals Petite Capitals Capital Spacing Case Titling Capitals Sensitive Small Capitals from Capitals Forms Figures Petite Capitals from Capitals Variants Tabular Lining Orna- Proportional Oldstyle ments Cross Platform Proportional Lining Supersript Compatibility Tabular Oldstyle Subscript Fractions As illustrated in the above graphic, the OpenType font format has many benefits. Not only the cross-platform compatibility makes OpenType the most advanced font format up to date, but especially its ability to support widely expanded character sets and layout features, in turn providing richer linguistic support and advanced typographic control. 02 | 15 ©2011 URW++ DESIGN & DEVELOPMENT GMBH A INTRODUCTION ++ | A | B1 | B2 | B3 | B4 | C | D | E 2.1 Cross Platform Compatibility The OpenType font format uses only a single font file for the outline and the metric data and can be installed on both Mac OSX and Windows systems, ensuring total compatibility among all electronic documents.