Kerberized Identity-Based Encryption and the Interoperability of Space-Based Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Submarine Cables
SUBMARINE CABLES The business of constructing and then maintaining DLA Piper is one of the largest global law firms in and selling capacity over submarine fibreoptic cables the world. We have a particular focus on this sector is fascinating, and is absolutely fundamental to and are very familiar with its specific idiosyncrasies modern day communications. The sector has its own and requirements. Whether it’s negotiating a new unique challenges due to the extraordinarily rapid consortium agreement, arranging finance, undertaking pace of development in transmission technologies pre-investment due diligence, advising on taxation as well as the timescales and levels of investment matters, dealing with regulatory matters, purchasing required to build new systems. infrastructure or capacity (on a lease or “IRU” basis) or advising on the effects of insolvency we have sector-specific experience which we don’t think can be matched by any other law firm in the world. UNRIVALLED SECTOR EXPERTISE ■ Advising Main One in connection with the extension of their existing West African cable system to other Offering outstanding legal support to the industry requires countries in the region. a complex mix of international law, financing, tax, regulatory, property and commercial expertise. It requires ■ Advising Broadband Infraco, one of the principal a thorough understanding of the sector in all its aspects, investors in the (consortium) West Africa Cable and it requires experience going back many years. System (WACS) in relation to its investment in WACS. The bulk of the work was to help them sell a significant Our unrivalled international network matches perfectly percentage of their entitlement under the consortium’s the international nature of the business, and allows the construction and maintenance agreement (the firm to provide timely and relevant advice to submarine “C&MA”) to another African telecoms operator. -

Saex 16.2 Sarex 07.2 – Sarex 16.2 AUMA NORM Actuator (Without Controls)
Multi-turn actuators SAEx 07.2 – SAEx 16.2 SAREx 07.2 – SAREx 16.2 AUMA NORM actuator (without controls) Operation instructions Assembly, operation, commissioning SAEx 07.2 – SAEx 16.2 / SAREx 07.2 – SAREx 16.2 Table of contents Read operation instructions first. ● Observe safety instructions. ● These operation instructions are part of the product. ● Retain operation instructions during product life. ● Pass on instructions to any subsequent user or owner of the product. Purpose of the document: This document contains information for installation, commissioning, operation and maintenance staff. It is intended to support device installation and commissioning. Table of contents Page 1. Safety instructions................................................................................................................. 5 1.1. Basic information on safety 5 1.2. Range of application 5 1.3. Warnings and notes 6 1.4. References and symbols 7 2. Identification........................................................................................................................... 8 2.1. Name plate 8 2.2. Short description 10 3. Transport, storage and packaging........................................................................................ 11 3.1. Transport 11 3.2. Storage 11 3.3. Packaging 11 4. Assembly................................................................................................................................ 12 4.1. Mounting position 12 4.2. Handwheel fitting 12 4.3. Multi-turn actuator: mount to valve/gearbox 12 4.3.1. Output drive types B, B1 – B4 and E 12 4.3.1.1. Multi-turn actuator (with output drive types B1 – B4 or E): mount to valve/gearbox 13 4.3.2. Output drive type A 13 4.3.2.1. Stem nut: finish machining 14 4.3.2.2. Multi-turn actuator (with output drive type A): mount to valve 15 4.4. Accessories for assembly 16 4.4.1. Stem protection tube for rising valve stem 16 5. -

STT700 Smartline Temperature Transmitter User's Manual
STT700 SmartLine Temperature Transmitter User’s Manual 34-TT-25-17 Revision 6 November 2020 Honeywell Process Solutions Copyrights, Notices and Trademarks © Copyright 2020 by Honeywell, Inc. Revision 6, November 2020 While the information in this document is presented in good faith and believed to be accurate, Honeywell disclaims any implied warranties of merchantability and fitness for a particular purpose and makes no express warranties except as may be stated in the written agreement with and for its customers. In no event is Honeywell liable to anyone for any indirect, special, or consequential damages. The information and specifications in this document are subject to change without notice. Honeywell, TDC 3000, SFC, SmartLine, PlantScape, Experion PKS, and TotalPlant are registered trademarks of Honeywell International Inc. Other brand or product names are trademarks of their respective owners. Honeywell Process Solutions 1250 W Sam Houston Pkwy S Houston, TX 77042 Revision 6 STT700 Temperature Transmitter User’s Manual Page ii About This Manual This manual is a detailed how to reference for installing, piping, wiring, configuring, starting up, operating, maintaining, calibrating, and servicing Honeywell’s family of STT700 temperature transmitters. Users who have a Honeywell STT700 SmartLine Temperature Transmitter configured for HART protocol or Honeywell’s Digitally Enhanced (DE) are referred to the STT700 SmartLine Series HART/DE Option User’s Manual, document number 34-TT-25-18. The configuration of your transmitter depends on the mode of operation and the options selected for it with respect to operating controls, displays and mechanical installation. This manual provides detailed procedures to assist first-time users, and it further includes keystroke summaries, where appropriate, as quick reference or refreshers for experienced personnel. -

INFORME DE BANDA ANCHA EN CANARIAS 2014 · Ecanarias 2015 BANDA ANCHAEN OBSERVATORIO CANARIODE CANARIAS 2014 (Edición 2015) INFORME DE
INFORME DE INFORME DE BANDA ANCHA EN CANARIAS 2014 · eCANARIAS 2015 BANDA ANCHA EN CANARIAS 2014 (edición 2015) OBSERVATORIO CANARIO DE INFORME DE BANDA ANCHA EN CANARIAS 2014 (edición 2015) OBSERVATORIO CANARIO DE LAS TELECOMUNICACIONES Y DE LA SOCIEDAD DE LA INFORMACIÓN Edita: OBSERVATORIO CANARIO DE LAS TELECOMUNICACIONES Y DE LA SOCIEDAD DE LA INFORMACIÓN AGENCIA CANARIA DE INVESTIGACIÓN, INNOVACIÓN Y SOCIEDAD DE LA INFORMACIÓN Avenida de Buenos Aires, 5 Edificio Tres de Mayo, 2ª planta 38071 Santa Cruz de Tenerife C/ León y Castillo, nº 200 Edificio Servicios Múltiples III, 6ª planta 35071 Las Palmas de Gran Canaria Febrero de 2016 www.octsi.es Esta obra está distribuida bajo una Licencia Reconocimiento - No comercial – Sin obras derivadas 3.0 España de Creative Commons, disponible en: http://creativecommons.org/ licenses/by-nc-nd/3.0/es/ (resumen) y http://creativecommons.org/licenses/by-nc-nd/3.0/ es/legalcode.es (texto completo). Se permite la copia, distribución y comunicación pública de la obra siempre que se reconoz- ca a sus autores, se realice sin fines comerciales o lucrativos, y no se altere, transforme o genere una obra derivada a partir de ella. Diseño y maquetación: DAUTE DISEÑO, S.L. ÍNDICE I. INTRODUCCIÓN 7 II. RESUMEN EJECUTIVO 9 III. CONTEXTO 13 1. Desarrollo de la banda ancha 13 2. Situación del sector de las telecomunicaciones 22 3. Velocidad de la banda ancha 24 4. Penetración de la banda ancha 27 5. El mercado de la banda ancha 29 5.1. El mercado de fibra oscura de España 33 5.2. Situación competitiva por centrales en España 34 6. -

2013 Submarine Cable Market Industry Report
submarine telecoms INDUSTRY REPORT 2013 Authored by Submarine Cable Industry Report Issue 2 March 2013 Copyright © 2013 by Submarine Telecoms Forum, Inc. All rights reserved. No part of this book may be used or reproduced by any means, graphic, electronic, or mechanical, including photocopying, recording, taping or by any information storage retrieval system without the written permission of the publisher except in the case of brief quotations embodied in critical articles and reviews. Submarine Telecoms Forum, Inc. 21495 Ridgetop Circle Suite 201 Sterling, Virginia 20166 USA www.subtelforum.com ISSN: pending 2 Disclaimer: While every care is taken in preparation of this publication, the publishers cannot be held responsible for the accuracy of the information herein, or any errors which may occur in advertising or editorial content, or any consequence arising from any errors or omissions, and the editor reserves the right to edit any advertising or editorial material submitted for publication. If you have a suggestion, please let us know by emailing [email protected]. 3 Table of Contents 1. Foreword 10 2. Introduction 11 3. Executive Summary 13 4. Worldwide Market Analysis and Outlook 18 4.1 Overview of Historical System Investment 20 4.2 2008 – 2012 Systems in Review 20 4.3 Systems Investment in 2013 and Beyond 21 5. Supplier Analysis 25 5.1 System Suppliers 25 5.2 Upgrade Suppliers 26 6. Ownership Analysis 28 6.1 Financing of Current Submarine Systems 28 7. Regional Market Analysis and Capacity Outlook 31 7.1 Transatlantic -

Brazil, the Internet and the Digital Bill of Rights Reviewing the State of Brazilian Internet Governance
STRATEGIC IGARAPÉ INSTITUTE PAPER a think and do tank 25 APRIL 2017 Brazil, the Internet and the Digital Bill of Rights Reviewing the State of Brazilian Internet Governance Daniel Arnaudo Brazil, the Internet and the Digital Bill of Rights - Reviewing the State of Brazilian Internet Governance Table of Contents List of Abbreviations 1 Abstract 2 Introduction and Key Findings 3 A Brief History of the MCI 5 Understanding Internet Governance through the Marco Civil 7 Freedom of Expression, Privacy and Human Rights 8 Democratic and Collaborative Governance 15 Universality, Diversity, Innovation 17 Network Neutrality 23 Infrastructure Update 25 Security, Functionality and Stability 30 Brazilian Internet Governance on the Global Stage 35 Conclusion 36 Annex: Key Articles in the Marco Civil da Internet 39 References 43 IGARAPÉ INSTITUTE | STRATEGIC PAPER 25 | APRIL 2017 List of Abbreviations MCI - Marco Civil da Internet [Internet Bill of ABIN - Agência Brasileira de Inteligência Nacional Rights] [Brazilian National Intelligence Agency] NSA - National Security Agency ANATEL - Agência Nacional de Telecomunicações [National Telecommunications PL/PLS - Proposed Law/Proposed Senate Law Agency] PNBL - Plano Nacional da Banda Larga [National ASN - Autonomous System Number Broadband Plan] BRICS - Brazil, Russia, India, China and South RIR - Regional Internet Registry Africa TLD - Top Level Domain CDCiber - Center for Cybernetic Defense WCIT - World Conference on International CGI - Comitê Gestor da Internet [Internet Steering Telecommunications Committee] -
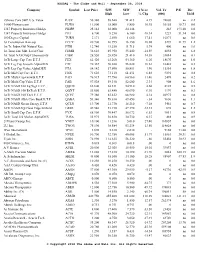
Ishares Core S&P U.S. Value 1-800-Flowers.Com 1347 Property
NASDAQ - The Globe and Mail - September 28, 2018 Company Symbol Last Price 52W 52W 1 Year Vol. Yr P/E Div. High Low % Chg (000) Yield iShares Core S&P U.S. Value IUSV 56.380 58.640 51.413 4.19 74603 na 2.2 1-800-Flowers.com FLWS 11.800 15.000 8.850 10.95 36155 18.73 0.0 1347 Property Insurance Holdgs PIHPP 25.142 28.000 24.148 - 263 193.40 8.0 1347 Property Insurance Holdgs PIH 6.700 8.250 6.100 -18.14 1221 51.54 0.0 180 Degree Capital TURN 2.171 2.500 1.660 17.41 16071 na 0.0 1st Constitution Bancorp FCCY 20.700 26.995 16.150 10.08 3239 21.79 1.2 1st Tr. Indxx Gbl Natural Res. FTRI 12.740 13.250 11.715 3.74 400 na 3.6 1st Trust Em. Mkt. Local Curr. FEMB 36.610 45.950 35.440 -14.59 4858 na 6.8 1st Trust NASDAQ Cybersecurity CIBR 28.520 28.920 21.410 14.58 35014 na 0.1 1stTr Large Cap Core E.T.F. FEX 62.420 63.260 54.360 6.20 18670 na 1.0 1stTr Lrg Cap Growth AlphaDEX FTC 70.367 70.880 56.820 10.61 10422 na 0.3 1stTr Lrg Cap Value AlphaDEX FTA 54.142 57.690 50.851 1.90 15316 na 1.8 1stTr Mid Cap Core E.T.F. FNX 71.620 73.110 61.431 6.48 9091 na 0.8 1stTr Multi Cap Growth E.T.F. -

PTC Academy Pioneering Technologies Keith Shaw
Keith Russell Shaw EMEA September 2019 Confidential – © 2018 Equinix Inc. Equinix.com 1 § A submarine cable is a cable laid on the sea bed between land- based stations to carry telecommunication signals across stretches Global of the ocean and sea. § As of early 2019, there are approximately 428* submarine cables in Connectivity service around the world. * The total number of cables is constantly changing as new cables enter service and older cable are decommissioned. Confidential – © 2018 Equinix Inc. Equinix.com 2 Summary of current SubSea Cable landscape from the various Suppliers viewpoints Confidential – © 2018 Equinix Inc. Equinix.com 3 Introduction to Open Cables • Outlining key considerations when designing or purchasing a new submarine cable, open or otherwise • It is intended to help ensure the network is upgradeable day 1, or in the future, to best leverage the significant investment made • The benefits of open cables have become generally accepted • within the submarine cable industry. Confidential – © 2018 Equinix Inc. Equinix.com 4 Introduction to Open Cables – Technologies – Breaking the mould Business benefits are: • Freedom to choose best-in-breed vendors with the decision based purely on their wet plant performance • Freedom to choose a best-in-breed Submarine Line Terminal Equipment (SLTE) at a later date, taking full advantage of: Faster innovation cycles Trends toward Point-of-Presence (POP-to-POP) and DC Interconnection Traffic patterns, away from (CLS-to-CLS), are more fitting Submarine upgrade vendors with strong -

Submarine Telecoms INDUSTRY REPORT 2012
submarine telecoms INDUSTRY REPORT 2012 1 Submarine Cable Industry Report Issue 1 July 2012 Copyright © 2012 by Submarine Telecoms Forum, Inc. All rights reserved. No part of this book may be used or reproduced by any means, graphic, electronic, or mechanical, including photocopying, recording, taping or by any information storage retrieval system without the written permission of the publisher except in the case of brief quotations embodied in critical articles and reviews. Submarine Telecoms Forum, Inc. 21495 Ridgetop Circle Suite 201 Sterling, Virginia 20166 USA www.subtelforum.com ISSN: applied for 2 Disclaimer: While every care is taken in preparation of this publication, the publishers cannot be held responsible for the accuracy of the information herein, or any errors which may occur in advertising or editorial content, or any consequence arising from any errors or omissions, and the editor reserves the right to edit any advertising or editorial material submitted for publication. If you have a suggestion, please let us know by emailing [email protected]. 3 Table of Contents 1.0 Introduction 13 2.0 Worldwide Market Analysis and Outlook 14 2.1 Connecting the Unconnected 14 2.2 Overview of Historical System Investment 15 2.3 2008 to 2012 Systems in Review 16 2.4 Systems Investment Beyond 2012 17 2.5 Decommissioning 18 3.0 Supplier Analysis 20 3.1 System Suppliers 20 3.2 Upgrade Suppliers 20 4.0 Ownership Analysis 23 4.1 Financing of Current Submarine Systems 23 4.2 Financing of Proposed Submarine Systems 23 5.0 Recent -

ELECTRIC ACTUATORS for the Automation of Valves in the Oil and Gas Industry ABOUT THIS BROCHURE
ELECTRIC ACTUATORS for the automation of valves in the oil and gas industry ABOUT THIS BROCHURE This brochure intends to describe functions and possible applications for electric actuators, actuator controls and gearboxes. The document provides an introduction into the topic, an overview on products and founded explanations regarding design and function of electric AUMA actuators. On the rear pages of this brochure, you will find a a chapter with detailed technical data for swift product selection. For device selection, further information can be obtained from our separate specific data sheets. It will be our pleasure to assist you and provide any further details that might be needed. The latest information on AUMA products can be found on the Internet at www.auma. com. All documents, including dimensional drawings, wiring diagrams, technical and electrical data sheets, as well as inspection certificates are available on the Internet in digital form. 2 Who are AUMA? About this brochure 2 AUMA - the specialist for electric actuators 4 Basic information Applications 6 Worldwide use 8 What is an electric actuator? 10 SAEx multi-turn actuators and SQEx part-turn actuators 12 Automation solutions for any valve type 14 Service conditions 16 Basic actuator functions 20 Controls concepts 22 Operation and clarity Integration within the DCS - AMExC and ACExC actuators controls 24 Clearly structured operation 26 Reliability, service life, maintenance - with test engineering features 28 AUMA CDT for ACExC controls - easy commissioning 30 AUMA CDT -

Africa Bandwidth Supply
The Future of African Bandwidth Markets African International Capacity Demand, Supply and Economics in an Era of Bandwidth Abundance REPORT SUMMARY, TABLE OF CONTENTS & SAMPLE PAGES May 2017 Report Summary: The Future of African Bandwidth Markets The African International Capacity Market Has Entered a New Era An Unprecedented View into African International Capacity Markets and Models The African international capacity market has entered a new era , a new phase that The most comprehensive independent report available on African international comes after a period of dynamic growth between 2010 and 2015, and follows a capacity markets and part of Xalam Analytics’ “Future of the African Internet Series”, miserable decade of bandwidth scarcity between 2000 and 2010. The Future of African Bandwidth Markets provides an unprecedented view into African international capacity demand, supply, key players, pricing and evolving business Things are different in 2017. Today’s African international capacity market is facing a models. seminal challenge to its economic structure, a paradoxical predicament at a time when Internet traffic is booming across the continent. The dynamics behind these changes and It explores key questions such as the size of demand, the impact of capacity oversupply, their implications for market players and investors are at the heart of The Future of the economic viability of proposed cable systems (SACS, SAIL, Liquid Sea, etc.), the African Bandwidth Markets report. future of African pure play capacity models, the impact of new wholesale capacity disruptors such as Angola Cables and Djibouti Telecom, how much lower international There is much to assess. Our research says Africa’s international capacity demand capacity price points can go, the impact of IXPs, which players will control African profile looks excellent. -
Big Stores Hold Off Reopening As States Ease Restrictions
P2JW116000-7-A00100-17FFFF5178F Reopening theU.S. EconomyEvenif ThePandemic Endures REVIEW Flowers to Power WSJ Yo ur Garden THE WALL STREETJOURNAL WEEKEND OFF DUTY ******* SATURDAY/SUNDAY,APRIL 25 -26, 2020 ~VOL. CCLXXV NO.97 WSJ.com HHHH $5.00 AT&T What’s News Chief to Retireat World-Wide TheEnd he FDAsaid two ma- Tlaria drugstouted by Trump and some doctorsfor Of June use against the coronavirus arelinked to heart problems and should only be used on Stankey to take reins hospitalized patientsoras part of clinical trials. A1 from Stephenson just Health experts and the as new streaming maker of Lysol issued warn- ingsafter Trump speculated service set to launch about using disinfectants inside the body,comments BY DREW FITZGERALD that he later walked back. A6 AT&T Inc. Chief Executive TheU.S.death toll from JOURNAL Randall Stephenson said he the coronavirus surpassed would step aside at the end of 50,000 as some states be- REET ST June, handing leadership of one ganreopening partsoftheir LL of the world’slargest media economies.Trump signed WA and telecommunications com- stimulus legislation. A5 THE panies to alongtime deputy R Esper told Navy officials FO amid the coronavirus pandemic. that he wasn’t ready to sign N Companyveteran John TO off on arecommendation Stankey will succeed Mr. Ste- MEL to reinstatethe USS Theo- A phenson, whoturned 60 this DR doreRoosevelt’scaptain. A3 AU week.Mr. Stephenson has A barber worked with a client in Decatur, Ga., on Friday, after the state permitted many businesses to reopen. spent most of his 13 years as Trump indicated he plans chairman and CEO piecing to- to use acoronavirus-relief gether a modern media busi- lawasleveragetoforce the ness by scooping up DirecTV Postal Servicetoraise rates Big Stores Hold Off Reopening and then Time Warner,remak- forpackagedelivery.