An Adjustable RDH Method for AMBTC-Compressed Images Using Unilateral Pixel Value Modification Strategy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Protection and Transmission of Chinese Nanyin by Prof
Protection and Transmission of Chinese Nanyin by Prof. Wang, Yaohua Fujian Normal University, China Intangible cultural heritage is the memory of human historical culture, the root of human culture, the ‘energic origin’ of the spirit of human culture and the footstone for the construction of modern human civilization. Ever since China joined the Convention for the Safeguarding of the Intangible Cultural Heritage in 2004, it has done a lot not only on cognition but also on action to contribute to the protection and transmission of intangible cultural heritage. Please allow me to expatiate these on the case of Chinese nanyin(南音, southern music). I. The precious multi-values of nanyin decide the necessity of protection and transmission for Chinese nanyin. Nanyin, also known as “nanqu” (南曲), “nanyue” (南乐), “nanguan” (南管), “xianguan” (弦管), is one of the oldest music genres with strong local characteristics. As major musical genre, it prevails in the south of Fujian – both in the cities and countryside of Quanzhou, Xiamen, Zhangzhou – and is also quite popular in Taiwan, Hongkong, Macao and the countries of Southeast Asia inhabited by Chinese immigrants from South Fujian. The music of nanyin is also found in various Fujian local operas such as Liyuan Opera (梨园戏), Gaojia Opera (高甲戏), line-leading puppet show (提线木偶戏), Dacheng Opera (打城戏) and the like, forming an essential part of their vocal melodies and instrumental music. As the intangible cultural heritage, nanyin has such values as follows. I.I. Academic value and historical value Nanyin enjoys a reputation as “a living fossil of the ancient music”, as we can trace its relevance to and inheritance of Chinese ancient music in terms of their musical phenomena and features of musical form. -

Demarcation of the Hourly Communication Area: a Case Study of Xiamen-Zhangzhou-Quanzhou Metropolitan Area, China Yue-E ZENG1,A
2016 Joint International Conference on Service Science, Management and Engineering (SSME 2016) and International Conference on Information Science and Technology (IST 2016) ISBN: 978-1-60595-379-3 Demarcation of the Hourly Communication Area: A Case Study of Xiamen-Zhangzhou-Quanzhou Metropolitan Area, China Yue-E ZENG 1,a , Shi-Dai WU2,b,* 1College of Resource and Environmental Science, Quanzhou Normal University, Quanzhou, China 2College of Geographical Sciences, Fujian Normal University, Fuzhou, China [email protected], [email protected] *Corresponding author Keywords: Hourly Communication Area, Traffic Waiting Time, Xiamen-Zhangzhou-Quanzhou. Abstract. With the advance of urban integration in China, the hourly communication area has attracted significant attention during the development of urban agglomerations. Using ArcGIS 10.1, this study uses the data on traffic networks and data from surveys conducted in Xiamen- Zhangzhou-Quanzhou Metropolitan Area, Fujian Province, in 2014 to demarcate the theoretical HCAs by applying the convex hull method, and establishes the actual HCAs according to the traffic waiting time. The analysis shows that the extent of the theoretical HCAs of XZQ is beyond the scope of the cities’ domains, with areas of 15473.3 km 2, 16356.7 km 2 and 19276.9 km 2, respectively. Furthermore, this paper shows that the traffic waiting time in XZQ ranges from 31 to 61 min, resulting in the reductions in the actual HCAs of 91.7%, 82.9% and 83.9%, compared to the theoretical HCAs. There are only a few areas of intersection between neighbouring cities. Policies should not only pay more attention to the intra-urban public transit systems but also build adequate public transit terminals to facilitate passenger transfers, such as new metro or light rail systems. -

Participants: (In Order of the Surname)
Participants 31 Participants: (in order of the surname) Yansong Bai yyyòòòttt: Jilin University, Changchun. E-mail: [email protected] Jianhai Bao ïïï°°°: Central South University, Changsha. E-mail: [email protected] Chuanzhong Chen •••DDD¨¨¨: Hainan Normal University, Haikou. E-mail: [email protected] Dayue Chen •••ŒŒŒ: Peking University, Beijing. E-mail: [email protected] Haotian Chen •••hhhUUU: Jilin University, Changchun. E-mail: [email protected] Longyu Chen •••999ˆˆˆ: Peking University, Beijing. E-mail: [email protected] Man Chen •••ùùù: Capital Normal University, Beijing. E-mail: [email protected] Mu-Fa Chen •••777{{{: Beijing Normal University, Beijing. E-mail: [email protected] Shukai Chen •••ÓÓÓppp: Beijing Normal University, Beijing. E-mail: [email protected] Xia Chen •••ggg: Jilin University, Changchun; University of Tennessee, USA. E-mail: [email protected] Xin Chen •••lll: Shanghai Jiao Tong University, Shanghai. E-mail: [email protected] Xue Chen •••ÆÆÆ: Capital Normal University, Beijing. E-mail: [email protected] Zengjing Chen •••OOO¹¹¹: Shandong University, Jinan. E-mail: [email protected] 32 Participants Huihui Cheng §§§¦¦¦¦¦¦: North China University of Water Resources and Electric Power, Zhengzhou E-mail: [email protected] Lan Cheng §§§===: Central South University, Changsha. E-mail: [email protected] Zhiwen Cheng §§§“““>>>: Beijing Normal University, Beijing. E-mail: [email protected] Michael Choi éééRRRZZZ: The Chinese University of Hong Kong, Shenzhen. E-mail: [email protected] Bowen Deng """ÆÆÆ©©©: Jilin University, Changchun. E-mail: [email protected] Changsong Deng """ttt: Wuhan University, Wuhan. E-mail: [email protected] Xue Ding ¶¶¶ÈÈÈ: Jilin University, Changchun. -

The 8Th International Conference on Numerical Optimization and Numerical Linear Algebra
The 8th International Conference on Numerical Optimization and Numerical Linear Algebra November 7-11, 2011 Xiamen, Fujian, China http://lsec.cc.ac.cn/~icnonla The 8th International Conference on Numerical Optimization and Numerical Linear Algebra November 7-11, 2011 Xiamen, Fujian, China http://lsec.cc.ac.cn/~icnonla ——————————————————— Information for Participants Sponsors Committees Conference Schedule Abstracts List of Participants Sightseeing Information Information for Participants Conference Hotel and Conference Venue Hotel: Peony Wanpeng Hotel f.û+U, Address: No.17-19, Huyuan Road, Siming District, Xiamen f½g²«m©´ 17-19 Ò Venue: Conference Room No. 1, Science & Art Center, Xia- men University fÆƲâ¥%Ҭƿ Address: No. 422, Siming South Road, Siming District, Xiamen f½g²«g²H´ 422 Ò Arrival By air: The distance between Xiamen International Airport and the conference hotel is about 14.2 km. It will cost you about 40 RMB (6.5 USD c.a.) to take a taxi. For the invited speakers, you will be picked up at the airport, if you have sent your arrival information to the organizing committee. By train: There is about 3.8 km from Xiamen railway station to the conference hotel. The taxi fare is about 12 RMB (2 USD c.a.). i Xiamen North railway station is 30.3 km away from the conference hotel. Participants who arrive there are suggested to take an inter- city high speed train to Xiamen railway station first (22 min., 9 RMB). On-site Registration On-site registration will take place at the lobby of Peony Wanpeng Hotel on November 6 from 9:00 to 21:00. -

University of Leeds Chinese Accepted Institution List 2021
University of Leeds Chinese accepted Institution List 2021 This list applies to courses in: All Engineering and Computing courses School of Mathematics School of Education School of Politics and International Studies School of Sociology and Social Policy GPA Requirements 2:1 = 75-85% 2:2 = 70-80% Please visit https://courses.leeds.ac.uk to find out which courses require a 2:1 and a 2:2. Please note: This document is to be used as a guide only. Final decisions will be made by the University of Leeds admissions teams. -

Annex Mainland University Study Subsidy Scheme Number Of
Annex Mainland University Study Subsidy Scheme Number of Recipients of Subsidies with a Breakdown by Institutions in the 2020/21 Academic Year (as at July 31, 2021) Number of Number of Recipients of Recipients “Means-tested of “Non- Mainland Institution Subsidy” means- Full-rate Half-rate tested subsidy subsidy Subsidy” Shanghai University 0 0 1 Shanghai University of Traditional 18 5 8 Chinese Medicine Shanghai International Studies University 7 0 14 Shanghai Jiao Tong University 2 1 6 Shanghai Normal University 2 4 0 Shanghai University of Finance and 2 0 4 Economics Shanghai University of Sport 1 1 0 Shandong University 33 6 7 Shandong University of 2 0 0 Traditional Chinese Medicine Sun Yat-sen University 158 49 68 Central Academy of Fine Arts 2 1 3 Central Conservatory of Music 1 1 0 Central University of Finance and 1 1 5 Economics The Central Academy of Drama 1 0 1 Central South University 4 0 4 Zhongnan University of Economics and 10 4 2 Law Renmin University of China 3 0 2 China University of Geosciences 1 0 0 (Wuhan) China University of Political Science and 28 9 27 Law China Conservatory of Music 0 1 0 Number of Number of Recipients of Recipients “Means-tested of “Non- Mainland Institution Subsidy” means- Full-rate Half-rate tested subsidy subsidy Subsidy” Communication University of China 3 4 6 Tianjin University 4 0 4 Tianjin University of Traditional Chinese 0 0 1 Medicine Tianjin Foreign Studies 0 0 1 University Peking University 14 5 28 Beijing University of Chinese Medicine 73 25 53 Beijing University of Chemical 0 1 -

Millet Arrived in the South China Coast Around 5,500 Years Ago
EGU21-8311, updated on 27 Sep 2021 https://doi.org/10.5194/egusphere-egu21-8311 EGU General Assembly 2021 © Author(s) 2021. This work is distributed under the Creative Commons Attribution 4.0 License. Millet arrived in the South China Coast around 5,500 years ago Jinqi Dai1,2,3, Xipeng Cai4, Jianhui Jin1,2,3, Wei Ge5, Yunming Huang6, Wei Wu7,8, Taoqin Xia4, Fusheng Li4, and Xinxin Zuo1,2,3 1Key Laboratory for Humid Subtropical Eco-geographical Processes of the Ministry of Education, Fujian Normal University, Fuzhou, China 2School of Geographical Sciences, Fujian Normal University, Fuzhou, China 3Center for Environmental Archaeology in Southeast China, Fujian Normal University, Pingtan, China 4Fuzhou Municipal Institute of Archaeology, Fuzhou, China 5School of Humanities, Xiamen University, Xiamen, China 6School of Humanities, Minjiang University, Fuzhou, China 7College of Architecture and Urban Planning, Fujian University of Technology, Fuzhou, China 8Tanshishan Site Museum, Fuzhou, China Crop dispersal has long been recognised as an important topic in agricultural archaeology and food globalisation. One of most pressing questions facing archaeologists is determining when and where millet arrived in the South China Coast. Our study focused on the millet phytoliths remains from three Neolithic sites in southeast coastal Fujian. Multiple dating methods, including charred carbon dating, phytolith carbon dating, and optically stimulated luminescence were used to construct the chronologies of the sites. The dating results showed that BTS was initially occupied at approximately 5,500 cal a BP. The millet phytoliths recovered in this study are likely the earliest millet remains found in Fujian, suggesting that millet arrived in the South China Coast at least 5,500 years ago. -
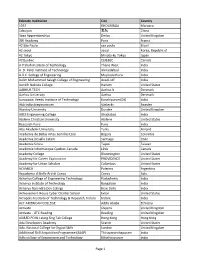
List AWS Educate Institutions
Educate Institution City Country 1337 KHOURIBGA Morocco 1daoyun 无锡 China 3aaa Apprenticeships Derby United Kingdom 3W Academy Paris France 42 São Paulo sao paulo Brazil 42 seoul seoul Korea, Republic of 42 Tokyo Minato-ku Tokyo Japan 42Quebec QUEBEC Canada A P Shah Institute of Technology Thane West India A. D. Patel Institute of Technology Ahmedabad India A.V.C. College of Engineering Mayiladuthurai India Aalim Muhammed Salegh College of Engineering Avadi-IAF India Aaniiih Nakoda College Harlem United States AARHUS TECH Aarhus N Denmark Aarhus University Aarhus Denmark Aarupadai Veedu Institute of Technology Kanchipuram(Dt) India Abb Industrigymansium Västerås Sweden Abertay University Dundee United Kingdom ABES Engineering College Ghaziabad India Abilene Christian University Abilene United States Research Pune Pune India Abo Akademi University Turku Finland Academia de Bellas Artes Semillas Ltda Bogota Colombia Academia Desafio Latam Santiago Chile Academia Sinica Taipei Taiwan Academie Informatique Quebec-Canada Lévis Canada Academy College Bloomington United States Academy for Career Exploration PROVIDENCE United States Academy for Urban Scholars Columbus United States ACAMICA Palermo Argentina Accademia di Belle Arti di Cuneo Cuneo Italy Achariya College of Engineering Technology Puducherry India Acharya Institute of Technology Bangalore India Acharya Narendra Dev College New Delhi India Achievement House Cyber Charter School Exton United States Acropolis Institute of Technology & Research, Indore Indore India ACT AMERICAN COLLEGE -

An Empirical Study on Context Awareness Integrated Mobile Assisted Instruction and the Factors
OPEN ACCESS EURASIA Journal of Mathematics Science and Technology Education ISSN: 1305-8223 (online) 1305-8215 (print) 2017 13(6):1737-1747 DOI 10.12973/eurasia.2017.00695a An Empirical Study on Context Awareness Integrated Mobile Assisted Instruction and the Factors Qiujin Zheng Fujian Agriculture and Forestry University, CHINA Ting Chen Fujian Agriculture and Forestry University, CHINA Deyi Kong Fujian Jiangxia University, CHINA Received 19 January 2016 ▪ Revised 26 August 2016 ▪ Accepted 21 January 2017 ABSTRACT Education is now an indicator of national modernization that countries in the world intend to promote the national quality and cultivate talents for national development through education. Especially, when human societies get into the 21st century, global societies, politics, economy, and culture are facing major changes. With the development of technology, the advance of the Internet, and the popularity of mobile devices, learning outside the classroom is no longer a problem and learning combined with authentic contexts becomes easier. When mobile devices are developed to connect to the network, it starts the mobile learning stage and ubiquitous learning becomes the easily accessible reality. Having Fujian Agriculture and Forestry University, Fujian Normal University, and Fujian Huaqiao University as the research objects, total 348 students of two classes each from the three universities are selected as the research objects in this study. The research results conclude 1.significantly positive correlations between context awareness and self- efficacy, 2.remarkably positive correlations between self-efficacy and learning motivation, and 3.notably positive correlations between context awareness and learning motivation. According to the research results, suggestions are proposed in this study, expecting to assist in the development of education. -

Handbook for Foreign Students
Handbook for Foreign Students Overseas Education College of Fuzhou University Fuzhou·China Catalog Message from the President ··························1 Location of FZU ··························2 Map of New Campus ··························5 Introduction of Fuzhou ·························7 Introduction of Fuzhou University ····················10 Rules of Conduct ························12 Campus Life ························13 Scholarships ·························13 Tuitions and Fees ························14 A Glimpse of the Dormitory ························15 Dormitory notice ························16 Enrollment Requirements and Application Procedures ··17 Special Safety Notice ·····················18 Residence Permit Application for Freshmen ···········19 Q & A ························21 Message from the President Dear Students, First, I would like to express my warm welcome to all of you! Fuzhou University (FZU) is located at the foot of Qishan Mountain beside Wulong River. With beautiful scenery and fresh air, you may feel she has only spring in one year. Moreover, towering mountains and gurgling rivers reveal a beautiful and glorious history. FZU has gathered the respect of teachers, national academicians, scholars, as well as national and provincial famous tutors. Lectures, debates and discussions create a stimulating learning environment. Our world-class resources will be your most valuable assets towards growth and success. FZU places great importance on international campus construction. The colorful and diverse campus cultural activities will provide you a fulfilling extracurricular life. Welcome to FZU. Wish you a great success here! 1 Location of FZU By Airplane It is one-hour-and-a-half drive from the university to Fuzhou Changle International Airport. There are direct flights from Fuzhou to main cities in China as well as international flights to Hong Kong, and other cities. You can get to Changle Airport by taxi,or by bus. -
1 Please Read These Instructions Carefully
PLEASE READ THESE INSTRUCTIONS CAREFULLY. MISTAKES IN YOUR CSC APPLICATION COULD LEAD TO YOUR APPLICATION BEING REJECTED. Visit http://studyinchina.csc.edu.cn/#/login to CREATE AN ACCOUNT. • The online application works best with Firefox or Internet Explorer (11.0). Menu selection functions may not work with other browsers. • The online application is only available in Chinese and English. 1 • Please read this page carefully before clicking on the “Application online” tab to start your application. 2 • The Program Category is Type B. • The Agency No. matches the university you will be attending. See Appendix A for a list of the Chinese university agency numbers. • Use the + by each section to expand on that section of the form. 3 • Fill out your personal information accurately. o Make sure to have a valid passport at the time of your application. o Use the name and date of birth that are on your passport. Use the name on your passport for all correspondences with the CLIC office or Chinese institutions. o List Canadian as your Nationality, even if you have dual citizenship. Only Canadian citizens are eligible for CLIC support. o Enter the mailing address for where you want your admission documents to be sent under Permanent Address. Leave Current Address blank. Contact your home or host university coordinator to find out when you will receive your admission documents. Contact information for you home university CLIC liaison can be found here: http://clicstudyinchina.com/contact-us/ 4 • Fill out your Education and Employment History accurately. o For Highest Education enter your current degree studies. -

Building Bridges Between Oregon and Fujian: Twenty Years of the Horner Exchange
Portland State University PDXScholar Library Faculty Publications and Presentations University Library 4-21-2017 Building Bridges Between Oregon and Fujian: Twenty Years of the Horner Exchange Richard Sapon-White Oregon State University Veronica Vichit-Vadakan Oregon College of Oriental Medicine Jian Wang Portland State University Follow this and additional works at: https://pdxscholar.library.pdx.edu/ulib_fac Part of the Library and Information Science Commons Let us know how access to this document benefits ou.y Citation Details Sapon-White, R., Vichit-Vadakan, V., and Wang, J. (April 2017). Building Bridges Between Oregon and Fujian: Twenty Years of the Horner Exchange. Presented at the Oregon Library Association Conference. This Presentation is brought to you for free and open access. It has been accepted for inclusion in Library Faculty Publications and Presentations by an authorized administrator of PDXScholar. Please contact us if we can make this document more accessible: [email protected]. Building Bridges Between Oregon and Fujian: Twenty Years of the Horner Exchange Presented by Richard Sapon-White Veronica Vichit-Vadakan Jian Wang Oregon Library Association Conference April 21, 2017 Presentation Overview • Introductions •Background on the Horner Exchange • 2016 Exchange •Libraries •Conversation •Sightseeing •Food! • Current Collaborations • Reflections on the Exchange • The Future of the Horner Exchange Introductions Background on the Horner Exchange Fujian Province • Olympian, 1932, 1936 • Orphanage director, mining company bookkeeper, ordained minister, conscientious objector • Married Marian Johnsen in Bremerton, Washington, 1946 • Postwar Japan • Education reforms • “Jack and Betty” books • Acting governor of Palau (1950) • Author of several books including: The Japanese and the Americans and On Both Sides of the Pacific Dr.