Arc-Length Compression
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Polar Coordinates, Arc Length and the Lemniscate Curve
Ursinus College Digital Commons @ Ursinus College Transforming Instruction in Undergraduate Calculus Mathematics via Primary Historical Sources (TRIUMPHS) Summer 2018 Gaussian Guesswork: Polar Coordinates, Arc Length and the Lemniscate Curve Janet Heine Barnett Colorado State University-Pueblo, [email protected] Follow this and additional works at: https://digitalcommons.ursinus.edu/triumphs_calculus Click here to let us know how access to this document benefits ou.y Recommended Citation Barnett, Janet Heine, "Gaussian Guesswork: Polar Coordinates, Arc Length and the Lemniscate Curve" (2018). Calculus. 3. https://digitalcommons.ursinus.edu/triumphs_calculus/3 This Course Materials is brought to you for free and open access by the Transforming Instruction in Undergraduate Mathematics via Primary Historical Sources (TRIUMPHS) at Digital Commons @ Ursinus College. It has been accepted for inclusion in Calculus by an authorized administrator of Digital Commons @ Ursinus College. For more information, please contact [email protected]. Gaussian Guesswork: Polar Coordinates, Arc Length and the Lemniscate Curve Janet Heine Barnett∗ October 26, 2020 Just prior to his 19th birthday, the mathematical genius Carl Freidrich Gauss (1777{1855) began a \mathematical diary" in which he recorded his mathematical discoveries for nearly 20 years. Among these discoveries is the existence of a beautiful relationship between three particular numbers: • the ratio of the circumference of a circle to its diameter, or π; Z 1 dx • a specific value of a certain (elliptic1) integral, which Gauss denoted2 by $ = 2 p ; and 4 0 1 − x p p • a number called \the arithmetic-geometric mean" of 1 and 2, which he denoted as M( 2; 1). Like many of his discoveries, Gauss uncovered this particular relationship through a combination of the use of analogy and the examination of computational data, a practice that historian Adrian Rice called \Gaussian Guesswork" in his Math Horizons article subtitled \Why 1:19814023473559220744 ::: is such a beautiful number" [Rice, November 2009]. -
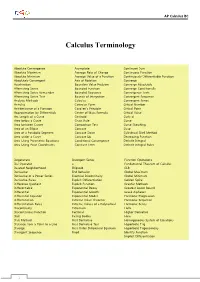
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

NOTES Reconsidering Leibniz's Analytic Solution of the Catenary
NOTES Reconsidering Leibniz's Analytic Solution of the Catenary Problem: The Letter to Rudolph von Bodenhausen of August 1691 Mike Raugh January 23, 2017 Leibniz published his solution of the catenary problem as a classical ruler-and-compass con- struction in the June 1691 issue of Acta Eruditorum, without comment about the analysis used to derive it.1 However, in a private letter to Rudolph Christian von Bodenhausen later in the same year he explained his analysis.2 Here I take up Leibniz's argument at a crucial point in the letter to show that a simple observation leads easily and much more quickly to the solution than the path followed by Leibniz. The argument up to the crucial point affords a showcase in the techniques of Leibniz's calculus, so I take advantage of the opportunity to discuss it in the Appendix. Leibniz begins by deriving a differential equation for the catenary, which in our modern orientation of an x − y coordinate system would be written as, dy n Z p = (n = dx2 + dy2); (1) dx a where (x; z) represents cartesian coordinates for a point on the catenary, n is the arc length from that point to the lowest point, the fraction on the left is a ratio of differentials, and a is a constant representing unity used throughout the derivation to maintain homogeneity.3 The equation characterizes the catenary, but to solve it n must be eliminated. 1Leibniz, Gottfried Wilhelm, \De linea in quam flexile se pondere curvat" in Die Mathematischen Zeitschriftenartikel, Chap 15, pp 115{124, (German translation and comments by Hess und Babin), Georg Olms Verlag, 2011. -

The Arc Length of a Random Lemniscate
The arc length of a random lemniscate Erik Lundberg, Florida Atlantic University joint work with Koushik Ramachandran [email protected] SEAM 2017 Random lemniscates Topic of my talk last year at SEAM: Random rational lemniscates on the sphere. Topic of my talk today: Random polynomial lemniscates in the plane. Polynomial lemniscates: three guises I Complex Analysis: pre-image of unit circle under polynomial map jp(z)j = 1 I Potential Theory: level set of logarithmic potential log jp(z)j = 0 I Algebraic Geometry: special real-algebraic curve p(x + iy)p(x + iy) − 1 = 0 Polynomial lemniscates: three guises I Complex Analysis: pre-image of unit circle under polynomial map jp(z)j = 1 I Potential Theory: level set of logarithmic potential log jp(z)j = 0 I Algebraic Geometry: special real-algebraic curve p(x + iy)p(x + iy) − 1 = 0 Polynomial lemniscates: three guises I Complex Analysis: pre-image of unit circle under polynomial map jp(z)j = 1 I Potential Theory: level set of logarithmic potential log jp(z)j = 0 I Algebraic Geometry: special real-algebraic curve p(x + iy)p(x + iy) − 1 = 0 Prevalence of lemniscates I Approximation theory: Hilbert's lemniscate theorem I Conformal mapping: Bell representation of n-connected domains I Holomorphic dynamics: Mandelbrot and Julia lemniscates I Numerical analysis: Arnoldi lemniscates I 2-D shapes: proper lemniscates and conformal welding I Harmonic mapping: critical sets of complex harmonic polynomials I Gravitational lensing: critical sets of lensing maps Prevalence of lemniscates I Approximation theory: -

Discrete and Smooth Curves Differential Geometry for Computer Science (Spring 2013), Stanford University Due Monday, April 15, in Class
Homework 1: Discrete and Smooth Curves Differential Geometry for Computer Science (Spring 2013), Stanford University Due Monday, April 15, in class This is the first homework assignment for CS 468. We will have assignments approximately every two weeks. Check the course website for assignment materials and the late policy. Although you may discuss problems with your peers in CS 468, your homework is expected to be your own work. Problem 1 (20 points). Consider the parametrized curve g(s) := a cos(s/L), a sin(s/L), bs/L for s 2 R, where the numbers a, b, L 2 R satisfy a2 + b2 = L2. (a) Show that the parameter s is the arc-length and find an expression for the length of g for s 2 [0, L]. (b) Determine the geodesic curvature vector, geodesic curvature, torsion, normal, and binormal of g. (c) Determine the osculating plane of g. (d) Show that the lines containing the normal N(s) and passing through g(s) meet the z-axis under a constant angle equal to p/2. (e) Show that the tangent lines to g make a constant angle with the z-axis. Problem 2 (10 points). Let g : I ! R3 be a curve parametrized by arc length. Show that the torsion of g is given by ... hg˙ (s) × g¨(s), g(s)i ( ) = − t s 2 jkg(s)j where × is the vector cross product. Problem 3 (20 points). Let g : I ! R3 be a curve and let g˜ : I ! R3 be the reparametrization of g defined by g˜ := g ◦ f where f : I ! I is a diffeomorphism. -

Superellipse (Lamé Curve)
6 Superellipse (Lamé curve) 6.1 Equations of a superellipse A superellipse (horizontally long) is expressed as follows. Implicit Equation x n y n + = 10<b a , n > 0 (1.1) a b Explicit Equation 1 n x n y = b 1 - 0<b a , n > 0 (1.1') a When a =3, b=2 , the superellipses for n = 9.9 , 2, 1 and 2/3 are drawn as follows. Fig1 These are called an ellipse when n= 2, are called a diamond when n = 1, and are called an asteroid when n = 2/3. These are known well. parametric representation of an ellipse In order to ask for the area and the arc length of a super-ellipse, it is necessary to calculus the equations. However, it is difficult for (1.1) and (1.1'). Then, in order to make these easy, parametric representation of (1.1) is often used. As far as the 1st quadrant, (1.1) is as follows . xn yn 0xa + = 1 a n b n 0yb Let us compare this with the following trigonometric equation. sin 2 + cos 2 = 1 Then, we obtain xn yn = sin 2 , = cos 2 a n b n i.e. - 1 - 2 2 x = a sin n ,y = bcos n The variable and the domain are changed as follows. x: 0a : 0/2 By this representation, the area and the arc length of a superellipse can be calculated clockwise from the y-axis. cf. If we represent this as usual as follows, 2 2 x = a cos n ,y = bsin n the area and the arc length of a superellipse can be calculated counterclockwise from the x-axis. -

Arc Length and Curvature
Arc Length and Curvature For a ‘smooth’ parametric curve: xftygt= (), ==() and zht() for atb≤≤ OR for a ‘smooth’ vector function: rijk()tftgtht= ()++ () () for atb≤≤ the arc length of the curve for the t values atb≤ ≤ is defined as the integral b 222 ('())('())('())f tgthtdt++ ∫ a b For vector functions, the integrand can be simplified this way: r'(tdt ) ∫a Ex) Find the arc length along the curve rjk()tt= (cos())33+ (sin()) t for 0/2≤ t ≤π . Unit Tangent and Unit Normal Vectors r'(t ) Unit Tangent Vector Æ T()t = r'(t ) T'(t ) Unit Normal Vector Æ N()t = (can be a lengthy calculation) T'(t ) The unit normal vector is designed to be perpendicular to the unit tangent vector AND it points ‘into the turn’ along a vector curve’s path. 2 Ex) For the vector function rij()tt=++− (2 3) (5 t ), find T()t and N()t . (this blank page was NOT a mistake ... we’ll need it) Ex) Graph the vector function rij()tt= (2++− 3) (5 t2 ) and its unit tangent and unit normal vectors at t = 1. Curvature Curvature, denoted by the Greek letter ‘ κ ’ (kappa) measures the rate at which the ‘tilt’ of the unit tangent vector is changing with respect to the arc length. The derivation of the curvature formula is a rather lengthy one, so I will leave it out. Curvature for a vector function r()t rr'(tt )× ''( ) Æ κ= r'(t ) 3 Curvature for a scalar function yfx= () fx''( ) Æ κ= (This numerator represents absolute value, not vector magnitude.) (1+ (fx '( ))23/2 ) YOU WILL BE GIVEN THESE FORMULAS ON THE TEST!! NO NEED TO MEMORIZE!! One visualization of curvature comes from using osculating circles. -

11.1 Circumference and Arc Length
11.1 Circumference and Arc Length EEssentialssential QQuestionuestion How can you fi nd the length of a circular arc? Finding the Length of a Circular Arc Work with a partner. Find the length of each red circular arc. a. entire circle b. one-fourth of a circle y y 5 5 C 3 3 1 A 1 A B −5 −3 −1 1 3 5 x −5 −3 −1 1 3 5 x −3 −3 −5 −5 c. one-third of a circle d. fi ve-eighths of a circle y y C 4 4 2 2 A B A B −4 −2 2 4 x −4 −2 2 4 x − − 2 C 2 −4 −4 Using Arc Length Work with a partner. The rider is attempting to stop with the front tire of the motorcycle in the painted rectangular box for a skills test. The front tire makes exactly one-half additional revolution before stopping. LOOKING FOR The diameter of the tire is 25 inches. Is the REGULARITY front tire still in contact with the IN REPEATED painted box? Explain. REASONING To be profi cient in math, you need to notice if 3 ft calculations are repeated and look both for general methods and for shortcuts. CCommunicateommunicate YourYour AnswerAnswer 3. How can you fi nd the length of a circular arc? 4. A motorcycle tire has a diameter of 24 inches. Approximately how many inches does the motorcycle travel when its front tire makes three-fourths of a revolution? Section 11.1 Circumference and Arc Length 593 hhs_geo_pe_1101.indds_geo_pe_1101.indd 593593 11/19/15/19/15 33:10:10 PMPM 11.1 Lesson WWhathat YYouou WWillill LLearnearn Use the formula for circumference. -

Notes Sec 8.1 Arc Length
Section 8.1 MATH 1152Q Arc Length Notes Arc Length Suppose that a curve C is defined by the equation yfx= ( ), where f is continuous and axb££. We obtain a polygonal approximation to C by dividing the interval [ab, ] into n subintervals with endpoints x0 , x1 , , xn and equal width Dx . If yfxii= ( ), then the point Pi (xyii, ) lies on C and the polygon with vertices P0 , P1 , , Pn is an approximation to C . The length L of C is approximately the length of this polygon and the approximation gets better as we let n increase. Therefore, we define the length L of the curve C with equation yfx= ( ), axb££, as the limit of the lengths of these inscribed polygons (provided the limit exists). n L = lim PPii-1 n®¥ å i=1 The definition of arc length given above is not very convenient for computational purposes, but we can derive an integral formula for L in the case where f has a continuous derivative. Such a function f is called smooth because a small change in x produces a small change in fx'( ). If we let Dyyyiii=--1, then 22 PPii-1 =(xxii---11) +( yy ii-) 22 =(Dxy) +(Di ) éù2 2 æöDyi =(Dx) êú1+ç÷ ëûêúèøDx 2 æöDyi =+1 ç÷ ×Dx èøDx By applying the Mean Value Theorem to f on the interval [xxii-1, ], we find that there is a * number xi between xi-1 and xi such that * fx( ii) - fx( --11) = f'( x iii)( x- x) Page 1 of 3 Thus we have 2 æöDyi PPii-1 =+1 ç÷ ×Dx èøDx 2 =+1'éùfx* ×D x ëû( i ) Therefore, n L = lim PPii-1 n®¥ å i=1 n 2 * =+lim 1éùfx ' i ×D x n®¥ å ëû( ) i=1 b 2 =+1'éùfx( ) dx òa ëû 2 The integral exists because the integrand 1'+ ëûéùfx( ) is continuous. -

13.3 Arc Length
13.3 Arc Length Review: curve in space: rt f t i g t j h t k Tangent vector: r'(t0 ) f ' t i g ' t j h ' t k Tangent line at t t0: s r( t 0) s r '( t 0 ) Velocity: v(t ) r '( t ) speed = | v ( t ) | Acceleration a(t ) v '( t ) r ''( t ) 1 Projectile motion: r(t ) gt2 j v t r initial velocity vr , initial position 2 00 00 g 32ft gravitational constant sec2 Initial speed |v0 | , initial height h, launching angle : 1 2 r(t ) v00cos t , h v sin t gt 2 Recall the length of a curve in the plane: b curve as a graph y f x: length from t a to t b 1 [f '(x)]2 dx a b curve in parametric form : x f t and y g t : length [f '(t)]22 [ g '(t)] dt a A curve in 3-space : r t f t, g t , h t b Length or Arc Length [f '(t)]2 [ g '(t)] 2 [ h '(t)] 2 dt a b Length |r '(t ) | dt a Example 1: A line from a to b : r()()tt a b a , 0t 1 1 1 length rt dt b a dt b a = distance from a to b 0 0 Example 2: 2 2 2 Compute the length (circumference) of circle: ()()x x00 y y r parametric description: x x00 rcos( t ), y y rsin( t ) 0 t 2 2 2 2 length = rt dt r2sin 2 ( t ) r 2 cos 2 ( t ) dt rdt2 r 0 0 0 Problem : A drunken bee travels along the path r(tt ) cos(2 ),sin(2 t), t for 10 seconds. -

2.3. Arc Length, Parametric Curves 2.3.1. Parametric Curves. a Parametric Curve Can Be Thought of As the Trajectory of a Point T
2.3. ARC LENGTH, PARAMETRIC CURVES 57 2.3. Arc Length, Parametric Curves 2.3.1. Parametric Curves. A parametric curve can be thought of as the trajectory of a point that moves trough the plane with coor- dinates (x, y) = (f(t), g(t)), where f(t) and g(t) are functions of the parameter t. For each value of t we get a point of the curve. Example: A parametric equation for a circle of radius 1 and center (0, 0) is: x = cos t, y = sin t . The equations x = f(t), y = g(t) are called parametric equations. Given a parametric curve, sometimes we can eliminate t and obtain an equivalent non-parametric equation for the same curve. For instance t can be eliminated from x = cos t, y = sin t by using the trigonometric relation cos2 t + sin2 t = 1, which yields the (non-parametric) equation for a circle of radius 1 and center (0, 0): x2 + y2 = 1 . Example: Find a non-parametric equation for the following para- metric curve: x = t2 2t, y = t + 1 . − Answer: We eliminate t by isolating it from the second equation: t = (y 1) , − and plugging it in the first equation: x = (y 1)2 2(y 1) . − − − i.e.: x = y2 4y + 3 , − which is a parabola with horizontal axis. 2.3.2. Arc Length. Here we describe how to find the length of a smooth arc. A smooth arc is the graph of a continuous function whose derivative is also continuous (so it does not have corner points). -

Differential Geometry Motivation
(Discrete) Differential Geometry Motivation • Understand the structure of the surface – Properties: smoothness, “curviness”, important directions • How to modify the surface to change these properties • What properties are preserved for different modifications • The math behind the scenes for many geometry processing applications 2 Motivation • Smoothness ➡ Mesh smoothing • Curvature ➡ Adaptive simplification ➡ Parameterization 3 Motivation • Triangle shape ➡ Remeshing • Principal directions ➡ Quad remeshing 4 Differential Geometry • M.P. do Carmo: Differential Geometry of Curves and Surfaces, Prentice Hall, 1976 Leonard Euler (1707 - 1783) Carl Friedrich Gauss (1777 - 1855) 5 Parametric Curves “velocity” of particle on trajectory 6 Parametric Curves A Simple Example α1(t)() = (a cos(t), a s(sin(t)) t t ∈ [0,2π] a α2(t) = (a cos(2t), a sin(2t)) t ∈ [0,π] 7 Parametric Curves A Simple Example α'(t) α(t))( = (cos(t), s in (t)) t α'(t) = (-sin(t), cos(t)) α'(t) - direction of movement ⏐α'(t)⏐ - speed of movement 8 Parametric Curves A Simple Example α2'(t) α1'(t) α (t)() = (cos(t), sin (t)) t 1 α2(t) = (cos(2t), sin(2t)) Same direction, different speed 9 Length of a Curve • Let and 10 Length of a Curve • Chord length Euclidean norm 11 Length of a Curve • Chord length • Arc length 12 Examples y(t) x(t) • Straight line – x(t)=() = (t,t), t∈[0,∞) – x(t) = (2t,2t), t∈[0,∞) – x(t) = (t2,t2), t∈[0,∞) x(t) • Circle y(t) – x(t) = (cos(t),sin(t)), t∈[0,2π) x(t) x(t) 13 Examples α(t) = (a cos(t), a sin(t)), t ∈ [0,2π] α'(t) = (-a sin(t), a cos(t)) Many