Address the Risk of Reprisals in Complaint Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Biopsychological Investigation of Hedonic Processes in Individuals Susceptible to Overeating: Role of Liking and Wanting in Trait Binge Eating
- 1 - Biopsychological Investigation of Hedonic Processes in Individuals Susceptible to Overeating: Role of Liking and Wanting in Trait Binge Eating Michelle Dalton Submitted in accordance with the requirements for the degree of Doctor of Philosophy The University of Leeds Institute of Psychological Sciences July 2013 - 2 - The candidate confirms that the work submitted is her own, except where work which has formed part of jointly authored publications has been included. The contribution of the candidate and the other authors to this work has been explicitly indicated below. The candidate confirms that appropriate credit has been given within the thesis where reference has been made to the work of others. Chapter 2 of this thesis was based in part on the jointly-authored publication: Dalton, M., King, N.A., & Finlayson, G., (2013) Appetite, Satiety and Food Reward in Obese Subjects: A Phenotypic Approach, Current Nutrition Reports, 1-9. Chapter 7 of this thesis was based in part on the jointly-authored publication: Dalton, M., Blundell, J. & Finlayson, G. (2013) Effect of BMI and binge eating on food reward and energy intake: further evidence for a binge eating subtype of obesity. Obesity Facts, 6; 348-359. Chapter 8 of this thesis was based in part on the jointly-authored publication: Dalton, M., Blundell, J. & Finlayson, G. (2013) Examination of obese binge-eating subtypes on reward, food choice and energy intake under laboratory and free-living conditions. Frontiers in Psychology, 4, 757. The candidate confirms that her contribution was primarily intellectual and she took a primary role in the production of the substance and writing of each of the above. -
Kosher Nosh Guide Summer 2020
k Kosher Nosh Guide Summer 2020 For the latest information check www.isitkosher.uk CONTENTS 5 USING THE PRODUCT LISTINGS 5 EXPLANATION OF KASHRUT SYMBOLS 5 PROBLEMATIC E NUMBERS 6 BISCUITS 6 BREAD 7 CHOCOLATE & SWEET SPREADS 7 CONFECTIONERY 18 CRACKERS, RICE & CORN CAKES 18 CRISPS & SNACKS 20 DESSERTS 21 ENERGY & PROTEIN SNACKS 22 ENERGY DRINKS 23 FRUIT SNACKS 24 HOT CHOCOLATE & MALTED DRINKS 24 ICE CREAM CONES & WAFERS 25 ICE CREAMS, LOLLIES & SORBET 29 MILK SHAKES & MIXES 30 NUTS & SEEDS 31 PEANUT BUTTER & MARMITE 31 POPCORN 31 SNACK BARS 34 SOFT DRINKS 42 SUGAR FREE CONFECTIONERY 43 SYRUPS & TOPPINGS 43 YOGHURT DRINKS 44 YOGHURTS & DAIRY DESSERTS The information in this guide is only applicable to products made for the UK market. All details are correct at the time of going to press but are subject to change. For the latest information check www.isitkosher.uk. Sign up for email alerts and updates on www.kosher.org.uk or join Facebook KLBD Kosher Direct. No assumptions should be made about the kosher status of products not listed, even if others in the range are approved or certified. It is preferable, whenever possible, to buy products made under Rabbinical supervision. WARNING: The designation ‘Parev’ does not guarantee that a product is suitable for those with dairy or lactose intolerance. WARNING: The ‘Nut Free’ symbol is displayed next to a product based on information from manufacturers. The KLBD takes no responsibility for this designation. You are advised to check the allergen information on each product. k GUESS WHAT'S IN YOUR FOOD k USING THE PRODUCT LISTINGS Hi Noshers! PRODUCTS WHICH ARE KLBD CERTIFIED Even in these difficult times, and perhaps now more than ever, Like many kashrut authorities around the world, the KLBD uses the American we need our Nosh! kosher logo system. -

Serving America
Proven leadership, a strong work ethic, discipline, teamwork—traits often used to describe those in our nation’s military. They are the same traits also associated with those who earn an M.B.A. The Simon Graduate School of Business has recognized this in its long tradition of accepting students with military backgrounds. As far back as the early 1970’s, instructors in the University of Rochester’s Naval R.O.T.C. program have taught naval science courses and attended Simon on Fridays through the Executive M.B.A. Program. During that time, Simon also offered an M.S. program in Systems Analysis, overseen by Ronald W. Hansen, senior associate dean for faculty and research, that enrolled and graduated approximately 75 mid-career military officers. Over the years, many Simon international students have performed military service in their home countries as well. Over the past two years, under Dean Mark Zupan’s leadership, the School has accelerated efforts to actively recruit M.B.A. candidates with military experience—either on orders from the military while on active duty or following several years of military service. “Since its inception, the Simon School has sought to attract the best and brightest candidates to attend its programs,” says Zupan. “Aside from today’s political climate, we continue to believe that the skills and traits inherent in current or former members of the military mirror those necessary for earning a graduate business degree and being successful.” Zupan ap- pointed Daniel H. Struble, retired Navy captain and former head of the University’s N.R.O.T.C. -

Striking a Personal Brand Balance: Eight Steps
Marketers: You can help us realize our healthy living goals! There is no denying that the brand-consumer relationship has drastically changed. While it used to be that consumers would turn to brands to signify ‘the good life,’ a life comprised of two cars in every garage and a chicken in every pot, consumers now are interested in turning to brands to help them activate ‘my good life.’ Consumers have taken control and are now putting themselves in charge of determining their own good life goals. Exemplified by the consumer quest towards achieving healthy living, consumers don’t want their brands to tell them what to do or who to be, but, rather want them to act as positive coaches along the way. And, while this shift has made consumers exhale with relief, it isn’t sitting well with many brand managers. Unsure of how to approach consumers without telling them what to do, many marketing programs are ill-conceived and are causing an overwhelming sense of consumer distrust. Therefore, we, along with the Bigheads network, a network of influencers in a variety of non-marketing industries, have come up with a three step plan for brands to help consumers achieve their own healthy living goals. These steps include: 1. Don’t Preach; Enable: your brand doesn’t have to be a super-hero or even have all of the answers 2. Be Authentic: in order to be credible, everything in the brand marketing mix has to work together 3. Be Inviting: Invite your consumers to come along on the journey, because they can help. -
Category of Supplement Types of Claims Examples of Claims (2007) Enforceme Nt? •Germs Are Everywhere
Referred to Gov Date of Decision Type Challenger Advertiser Product Agency for Category of Supplement Types of Claims Examples of Claims (2007) Enforceme nt? •Germs are everywhere. Take Airborne to boost your immune system, fight viruses and help you stay Case •Performance 4648 3/26/2007 NAD Airborne Health Inc. Airborne Immune Health healthy. Report •Implied •Take Airborne. The immune boosting tablet that helps your body fight germs. •Clinically Proven/Shown •CH-Alpha is scientifically proven to promote joint health. 4652 Case Report 4/10/2007 NAD Gelita Health Products CH-Alpha Joint Health •Preventative Health •After just two to three months, you will regain the freedom of flexibility. •94% faster recovery [from colds] •Clinically Proven/Shown •Increased immune system resistance by 312% 4653 Case Report 4/10/2007 Proctor and Gamble Iovate Health Sciences Inc. Cold MD Immune Health •Speed •Clinically Proven results •Comparative •Doctor formulated and approved •Chromax helps your insulin function at its best. •Performance •It's an advanced, highly absorbable form of chromium that provides your body with the chromium it Blood Sugar Health •Insulin 4547 Compliance 4/11/2007 NAD Nutrition 21 Chromax needs to help promote healthy blood sugar, fight carbohydrate cravings and support your overall •Implied cardiovascular health. •Essential for optimum insulin health. •Exclusivity •One-A-Day Women's Multi-Vitamin is the only complete multi-vitamin with more calcium for strong 4672 Case Report 5/1/2007 NAD Bayer Consumer Healthcare One-A-Day Women's Multi-Vitamin •Implied bones, and now more vitamin D, which emerging research suggests may support breast cancer. -

2020 Corporate Responsibility Report Table of Contents
2020 Corporate Responsibility Report Table of Contents OVERVIEW 3 PEOPLE & COMMUNITIES 32 A Letter from our Chairman & CEO and CSO 3 Employee Health & Safety 33 About This Report Our Company 4 Employee Engagement & Development 35 Keurig Dr Pepper (KDP) has reported on Key Highlights 5 Diversity & Inclusion 37 its corporate responsibility program since Our Corporate Responsibility Strategy 6 Community Engagement 39 the Company was formed in July 2018. This progress report focuses on the goals, Stakeholder Engagement & Materiality 8 programs and initiatives that encompass our key corporate responsibility efforts for Goals & Progress 9 GOVERNANCE 41 2020. In addition, we have created a Data Responding to COVID-19 10 Summary, which can be found at the end Board Management & Oversight 42 of this report. Unless otherwise noted, this report covers data and activities for calendar Ethics & Compliance 43 year 2020 from KDP’s wholly owned ENVIRONMENT 11 operations, which are primarily located in the Human Rights 44 U.S., Canada and Mexico. The content covers Product Design & Circular Economy 12 the parts of our business in which we have operational control and does not include Resource Use & Conservation 15 APPENDIX joint ventures, franchised or outsourced 45 operations, except where noted. Selected Water Efficiency & Stewardship 16 Data Summary 45 data and information on our global supply Climate, Emissions & Energy 18 chain activities are also included. Goal Methodology 52 We have expanded the scope of independent Stakeholder Engagement 58 verification for 2020 to include more SUPPLY CHAIN 20 environmental metrics, assurance on the Reporting Framework Indices (GRI, SASB, TCFD) 61 Environmental and Supply Chain sections Responsible Sourcing 21 of the report, and assurance for applicable Sustainability Accounting Standards Improving Livelihoods 23 Board (SASB) standards. -

Kitten Care Handbook
KITTEN RESCUE Kitten Care Handbook Thousands of abandoned kittens are rescued and hand-raised by animal lovers every spring. We've I'm Scoots written this guide to help you out! If you find a kitten or litter of newborns and would like to care for them Read My yourself, here are some Story! tips on proper care! We have also included tips for people who have recently adopted a new kitten or cat, and want to make sure everything goes smoothly. Please know that if your new addition comes from a shelter, he or she is particularly at risk for illness. A shelter is a stressful environment for a cat, and their immune systems-- just like ours in times of tension-- take a dive, leaving them susceptible to whatever happens to be going around the facility's population. Even when cared for by a responsible rescue group, animals do contract unavoidable illnesses. Please be patient, know you've done a wonderful thing by adopting a rescued animal, and help your pet get a leg up (or all four) on a lifetime of good health. Our thanks to Carolyn McCray, DVM, for writing part of this handbook. For extra tips on getting your new cat or kitten accustomed to your home, please read Welcome Home Kitty. If you have any other questions, please phone us at (818)347-3037 If this handbook proves to be of use to you, please support Kitten Rescue by taking a moment to look at our Donate! opportunities. Table of Contents: Raising Orphan Kittens Recipes For Emergency Kitten Formula The Basics Keeping Healthy Kittens Healthy (6 weeks to 4 months) Keeping Healthy Cats Healthy (Over 4 months of age) Food Brand Recommendations Raising Orphan Kittens If you have found abandoned or feral kittens and wish to rescue and raise them, you probably have more than a few questions about how to do it. -

Substance Abuseabuse
SubstanceSubstance AbuseAbuse ForFor FosterFoster Parents,Parents, CaregiversCaregivers && TeachersTeachers TeenTeen TrendsTrends-- WhatWhat toto KnowKnow 1: THEY’RE STRESSED. Today’s teens are stressed out. Factors include school work (they have more than ever. The Internet speeds things up but that just means that they're given even more work), college pressures, advanced placement courses in high school, and being overscheduled. The (stereotypical) Gen X slackers they are not. 2: THEY’RE HYPER-SEXUALIZED. Things like mini-skirts in schools, guys taking Creatine to get bulked up for sports, Real World MTV hook ups with young adults sleeping with strangers in each episode, online dating sites and Internet porn... This stuff is in their face every day. Teens are trying to act older, while older people are trying to act younger. So you've got kids trying to be adults, and adults (like Baby Boomers in particular) trying to be kids. It makes for a weird dynamic – and can confuse the teen as to who's the role model? Surprisingly, kids are more mature about things than you'd expect. 3: FRIENDS ARE THE NEW FAMILY. You say, “a person's friends have been important to every generation." But this cohort seems to equally value their circle of friends as their secondary family. They are far more group oriented than Gen Xers. Even if you think about Sesame Street, the show Xers grew up with ("We're all unique and different") compared to Barney, the show Gen Y grew up with ("Everybody is equal -- We're all the same.") Gen Y tends to be more conformist than Xers and Boomers were in their youth. -

The Amazing Adventures of Superstan Junior Script By
The Amazing Adventures of Superstan Junior Script by Craig Hawes Ideal Cast Size 54 Speaking Roles 42 Minimum Cast Size 25 Duration (minutes) 70-90 3/280917/28 ISBN: 978 1 84237 155 8 Published by Musicline Publications P.O. Box 15632 Tamworth Staffordshire B78 2DP 01827 281 431 www.musiclinedirect.com Licences are always required when published musicals are performed. Licences for musicals are only available from the publishers of those musicals. There is no other source. All our Performing, Copying & Video Licences are valid for one year from the date of issue. If you are recycling a previously performed musical, NEW LICENCES MUST BE PURCHASED to comply with Copyright law required by mandatory contractual obligations to the composer. Prices of Licences and Order Form can be found on our website: www.musiclinedirect.com The Amazing Adventures of Superstan – Script 1 CONTENTS Cast List ............................................................................................................................... 4 Suggested Cast List For 54 Actors ................................................................................... 5 Suggested Cast List For 25 Actors ................................................................................... 7 Characters In Each Scene .................................................................................................. 9 List Of Properties .............................................................................................................. 10 Production Notes ............................................................................................................. -
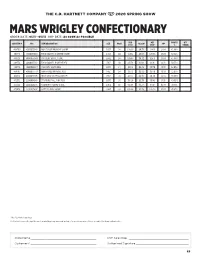
Mars Wrigley Confectionary Order Date: 05/3 - 05/15 Ship Date: As Soon As Possible
THE C.D. HARTNETT COMPANY 2020 SPRING SHOW MARS WRIGLEY CONFECTIONARY ORDER DATE: 05/3 - 05/15 SHIP DATE: AS SOON AS POSSIBLE REG NET PROFIT QTY CDH ITEM # UPC ITEM DESCRIPTION SIZE PACK ALLOW SRP COST COST* % ORDER 469700 4000055542 M&M FUDGE BROWNIE SHARE 2.83Z 24 $28.83 $4.32 $24.51 $1.89 45.96% 469718 4000055189 TWIX COOKIES N CREME SHARE 2.72Z 20 $29.12 $3.54 $25.58 $1.89 32.32% 469726 4000056049 SNICKERS WHITE SHARE 2.84Z 24 $28.83 $4.32 $24.51 $1.89 45.96% 469734 4000055182 TWIX COOKIES N CREME REG 1.36Z 20 $13.79 $1.98 $11.81 $1.19 50.37% 469775 4000056047 SNICKERS WHITE REG 2.07Z 24 $16.12 $2.42 $13.70 $1.19 52.03% 469783 4000055539 M&M FUDGE BROWNIE REG 1.41Z 24 $16.12 $2.42 $13.70 $1.19 52.03% 469791 4000055585 MILKY WAY SALTED CARAMEL 1.56Z 24 $16.12 $4.32 $11.80 $1.19 58.68% 472332 2200001988 STARBURST ALL PINK REG 2.07Z 24 $16.20 $2.38 $13.82 $1.15 49.92% 472340 2200028238 STARBURST SWIRL SHARE 2.96Z 10 $12.98 $1.77 $11.21 $2.19 48.81% 475038 2200027807 SKITTLES DIPS SHARE 2.9OZ 24 $28.96 $2.38 $26.58 $2.05 45.97% * Plus C.D. Hartnett upcharge C.D. Hartnett reserves the right to correct product & pricing errors and apologize for any inconvenience. Prices are subject to change without notice. Store Name _____________________________________________ CDH Sales Rep. -

KIND and Mars Announce Next Step in Partnership to Build a Kinder World and Bring Healthy Snacks to People Worldwide
KIND and Mars Announce Next Step in Partnership to Build a Kinder World and Bring Healthy Snacks to People Worldwide Mars to acquire KIND North America; Partnership will build on growth across geographies and categories Founder Daniel Lubetzky retains ongoing financial stake and remains focused on upholding and expanding the KIND Promise to build foremost health and wellness platform MCLEAN, VA and NEW YORK, NY (November 17, 2020) – Mars, Incorporated, a family-owned global pet food, veterinary care, confectionery, snacking and food business, and KIND, a healthy snacking leader, today announced the next step in their strategic partnership, with Mars acquiring KIND North America. KIND North America will join KIND International to create one organization operating across 35 countries, functioning as a distinct and separate business within the Mars Family of Companies. This provides the opportunity to further the KIND Promise, a set of nutrition principles that have guided the company’s innovation since its founding, and KIND’s mission to create a kinder world. KIND Founder and Executive Chairman Daniel Lubetzky will play a key role in the future development and expansion of KIND, helping to maximize the reach and impact of the KIND mission and products, while upholding the KIND Promise as the brand expands into new categories and geographies. He will retain an ongoing financial stake in KIND, a majority of which was previously donated to charity to further his philanthropic efforts to build bridges across lines of divide. Partnership Success Over the past three years, Mars and KIND have partnered to bring KIND (including signature KIND Bars) into new geographies and categories, remaining true to the KIND Promise that the first and predominant ingredient in all of its snacks and foods is a nutrient-dense food. -

America's Most Popular Snacks!
WITH Put the Power of MARS Brands to Work for You. DOT ITEM # DESSERT INCLUSIONS WT / SIZE 430481 TWIX® Chopped 2/5 LB. 502084 M&M'S® Chopped 2/4 LB. 502085 M&M’S® Mini Baking Bits 2/4 LB. 428388 SNICKERS® Chopped 2/5 LB. MARS ITEM # BUNDLE OPPORTUNITIES WT / SIZE America’s Most Popular Snacks! 286432 TWIX® Bites SUP 7.0 OZ 18 CT 276758 SNICKERS® Bites SUP 8.0 OZ 18 CT 199586 M&M’S® Milk Chocolate Candies 12.6 OZ 24 CT 199579 M&M’S® Peanut Chocolate Candies 12.6 OZ 24 CT DOTxxxxxxxx ITEM # M&M’S®FOR THE Brand COUNTER 36 CT Variety Counter DisplayWT / SIZE 560312 M&M’S® Brand 36 CT Variety Counter Display 560313 Filled Bar 36 CT Variety Counter Display ATTENTION PIZZERIA OWNERS! Add MARS brands to your menu today! Contact your Broker Sales Rep or call 844-256-6277 to get started! BROKER NAME BROKER PHONE NUMBER Look for exciting promotions & brand features at www.marsfoodservices.com Studies show that using MARS Brands positively influence purchase decisions and increase acceptable purchase price.1 SNICKERS® is the #1 selling chocolate bar world wide.2 M&M’S® Brand is the #1 brand world wide with 100% awareness.2 DESSERT OPPORTUNITIES TWIX® Brand is a favorite among 18-49 year olds.3 Add MARS Brand inclusions to baked goods for unique treats FOR THE COUNTER - 36ct Display • Dessert Knots One of a Kind - Made with Chopped SNICKERS® Exclusive to Foodservice! • Dessert Sticks Feature the 36 ct Made with Chopped TWIX® Counter Display, • Cannolis perfect for customers Made with M&M’S® Mini Baking Bits looking for a variety • Sugar Cookies of treats on the go.