508 Test Report NIST Disk Imaging Tool Encase Forensic V8.05.00.182
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC
Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ Boot Disk User Guide Contents 1.0 Product Overview .......................................................................................................... -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

Multiboot Guide Booting Fedora and Other Operating Systems
Fedora 23 Multiboot Guide Booting Fedora and other operating systems. Fedora Documentation Project Copyright © 2013 Fedora Project Contributors. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries. All other trademarks are the property of their respective owners. -

Diskgenius User Guide (PDF)
www.diskgenius.com DiskGenius® User Guide The information in this document is subject to change without notice. This document is not warranted to be error free. Copyright © 2010-2021 Eassos Ltd. All Rights Reserved 1 / 236 www.diskgenius.com CONTENTS Introduction ................................................................................................................................. 6 Partition Management ............................................................................................................. 6 Create New Partition ........................................................................................................ 6 Active Partition (Mark Partition as Active) .............................................................. 10 Delete Partition ................................................................................................................ 12 Format Partition ............................................................................................................... 14 Hide Partition .................................................................................................................... 15 Modify Partition Parameters ........................................................................................ 17 Resize Partition ................................................................................................................. 20 Split Partition ..................................................................................................................... 23 Extend -

Lecture 7 Slides
✬ ✩ Computer Science CSCI 251 Systems and Networks Dr. Peter Walsh Department of Computer Science Vancouver Island University [email protected] ✫ 1: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ Virtualization Process • CPU virtualization Address Space • memory virtualization File • persistent storage virtualization ✫ 2: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ Formatting Low Level • sector creation • sector addressing using LBA (Logical Block Addressing) e.g., (cylinder 0, head 0, sector 1) = LBA 0, (cylinder 0, head 0, sector 2) = LBA 1 etc. • usually completed at time of manufacture Partitioning • each physical disk can be divided into partitions • a partition is a logical disk under OS control High Level • typically involves file system creation ✫ 3: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ IBM PC Basic I/O System (BIOS) BIOS • firmware executes on power-on startup • assumes disk data structure and boot-loader code starting at LBA 0 of bootable disk Legacy BIOS • LBA 0 contains MBR (Master Boot Record) • MBR contains the partition table • a partition entry contains a 32 bit start LBA field UEFI (Unified Extensible Firmware Interface) • GPT (GUID Partition Table) starts at LBA 0 • GPT contains the partition table • a partition entry contains a 64 bit start LBA field ✫ 4: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ IBM PC Basic I/O System (BIOS) cont. 3ΤΙςΕΞΜΡΚ7]ΩΞΙΘ &−37 9)∗− 4ΕςΞΜΞΜΣΡ 1&6 +48 4ΕςΞΜΞΜΣΡ 8ΕΦΠΙ 8ΕΦΠΙ &ΣΣΞ &ΣΣΞ 0ΣΕΗΙς 0ΣΕΗΙς −&14∋,ΕςΗ[ΕςΙ ✫ 5: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ IDE Devices Controller • typically can support 4 drives (2 ports) Old Naming Convention Device Name Port# Drive# /dev/hda 1 1 /dev/hdb 1 2 /dev/hdc 2 3 /dev/hdd 2 4 New Naming Convention Device Name Port# Drive# /dev/sda 1 1 /dev/sdb 1 2 /dev/sdc 2 3 /dev/sdd 2 4 ✫ 6: Computer Science CSCI 251 — Lecture 7 ✪ ✬ ✩ SATA Devices Controller • typically can support 2 - 6 drives (2 - 6 ports) Naming Convention Device Name Port# Drive# /dev/sda 1 1 /dev/sdb 2 2 ....... -
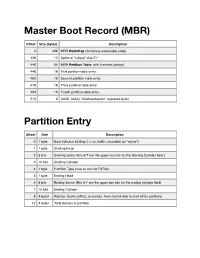
Master Boot Record (MBR)
Master Boot Record (MBR) Offset Size (bytes) Description 0 436 MBR Bootstrap (flat binary executable code) 436 10 Optional "unique" disk ID1 446 64 MBR Partition Table, with 4 entries (below) 446 16 First partition table entry 462 16 Second partition table entry 478 16 Third partition table entry 494 16 Fourth partition table entry 510 2 (0x55, 0xAA) "Valid bootsector" signature bytes Partition Entry Offset Size Description 0 1 byte Boot indicator bit flag: 0 = no, 0x80 = bootable (or "active") 1 1 byte Starting head 2 6 bits Starting sector (Bits 6-7 are the upper two bits for the Starting Cylinder field.) 3 10 bits Starting Cylinder 4 1 byte Partition Type (0xB or 0xC for FAT32). 5 1 byte Ending Head 6 6 bits Ending Sector (Bits 6-7 are the upper two bits for the ending cylinder field) 7 10 bits Ending Cylinder 8 4 bytes Relative Sector (offset, in sectors, from start of disk to start of the partition) 12 4 bytes Total Sectors in partition BIOS Parameter Block (BPB) Offset Size Meaning (bytes) (bytes) 0 3 The first three bytes EB XX 90 disassemble to JMP SHORT XX NOP. 3 8 OEM identifier. 11 2 The number of Bytes per sector (all numbers are in the little-endian format). 13 1 Number of sectors per cluster. 14 2 Number of reserved sectors. The boot record sectors are included in this value. 16 1 Number of File Allocation Tables (FAT's) on the storage media. Often 2. 17 2 Max # of directory entries (0 for FAT32 which stores directories in data region). -

Tectips: Hidden FDISK(32) Options
WHITE PAPER TecTips: Hidden FDISK(32) Options Guide Previously Undocumented Options of the FDISK Utility Released Under Microsoft Windows95™ OSR2 or Later Abstract 2 Document Conventions 2 Read This First 3 Best-Case Scenario 3 Windows Startup Disk 3 How to apply these options 3 FDISK(32) Options 4 Informational Options 4 Behavioral Options 5 Functional Options 6 February, 2000 Content ©1999 StorageSoft Corporation, all rights reserved Authored by Doug Hassell, In-house Technical Writer StorageSoft White Paper page 2 FDISK(32) Command Line Options Abstract Anyone that remembers setting-up Windows 3.x or the first Win95 release surely knows of the text-based utility, fdisk.exe. Some of those may even be aware of the few, documented switches, such as /status, /x or even the commonly referenced /mbr. Even fewer would be aware of the large table of undocumented command-line options - including automated creation, reboot behavior, and other modifiers - which we will divulge in this document. Note that all options given here are not fully tested, nor are they guaranteed to work in all scenarios, all commands referenced apply to the contemporary release of Win95 (OSR2 - version “B” - or later, including Win98 and the up-and-coming Millennium™ edition). For our recommendation on how to use these swtiches, please refer to the “Read This First” section. Document Conventions In this document are certain references that deserve special recognition. This is done through special text- formatting conventions, described here… v Words and phrases of particular importance will stand-out. Each occurrence of this style will generally indicate a critical condition or pitfall that deserves specific attention. -

Partition.Pdf
Linux Partition HOWTO Anthony Lissot Revision History Revision 3.5 26 Dec 2005 reorganized document page ordering. added page on setting up swap space. added page of partition labels. updated max swap size values in section 4. added instructions on making ext2/3 file systems. broken links identified by Richard Calmbach are fixed. created an XML version. Revision 3.4.4 08 March 2004 synchronized SGML version with HTML version. Updated lilo placement and swap size discussion. Revision 3.3 04 April 2003 synchronized SGML and HTML versions Revision 3.3 10 July 2001 Corrected Section 6, calculation of cylinder numbers Revision 3.2 1 September 2000 Dan Scott provides sgml conversion 2 Oct. 2000. Rewrote Introduction. Rewrote discussion on device names in Logical Devices. Reorganized Partition Types. Edited Partition Requirements. Added Recovering a deleted partition table. Revision 3.1 12 June 2000 Corrected swap size limitation in Partition Requirements, updated various links in Introduction, added submitted example in How to Partition with fdisk, added file system discussion in Partition Requirements. Revision 3.0 1 May 2000 First revision by Anthony Lissot based on Linux Partition HOWTO by Kristian Koehntopp. Revision 2.4 3 November 1997 Last revision by Kristian Koehntopp. This Linux Mini−HOWTO teaches you how to plan and create partitions on IDE and SCSI hard drives. It discusses partitioning terminology and considers size and location issues. Use of the fdisk partitioning utility for creating and recovering of partition tables is covered. The most recent version of this document is here. The Turkish translation is here. Linux Partition HOWTO Table of Contents 1. -

File Allocation Table - Wikipedia, the Free Encyclopedia Page 1 of 22
File Allocation Table - Wikipedia, the free encyclopedia Page 1 of 22 File Allocation Table From Wikipedia, the free encyclopedia File Allocation Table (FAT) is a file system developed by Microsoft for MS-DOS and is the primary file system for consumer versions of Microsoft Windows up to and including Windows Me. FAT as it applies to flexible/floppy and optical disc cartridges (FAT12 and FAT16 without long filename support) has been standardized as ECMA-107 and ISO/IEC 9293. The file system is partially patented. The FAT file system is relatively uncomplicated, and is supported by virtually all existing operating systems for personal computers. This ubiquity makes it an ideal format for floppy disks and solid-state memory cards, and a convenient way of sharing data between disparate operating systems installed on the same computer (a dual boot environment). The most common implementations have a serious drawback in that when files are deleted and new files written to the media, directory fragments tend to become scattered over the entire disk, making reading and writing a slow process. Defragmentation is one solution to this, but is often a lengthy process in itself and has to be performed regularly to keep the FAT file system clean. Defragmentation should not be performed on solid-state memory cards since they wear down eventually. Contents 1 History 1.1 FAT12 1.2 Directories 1.3 Initial FAT16 1.4 Extended partition and logical drives 1.5 Final FAT16 1.6 Long File Names (VFAT, LFNs) 1.7 FAT32 1.8 Fragmentation 1.9 Third party -

FAT32 File Structure Prof
FAT32 File Structure Prof. James L. Frankel Harvard University Version of 9:45 PM 24-Mar-2021 Copyright © 2021 James L. Frankel. All rights reserved. FAT32 Source Documentation • The reference document you should use is the Microsoft Extensible Firmware Initiative FAT32 File System Specification • On class web site under The NXP/Freescale ARM -> microSDHC Card • It is available on the class web site at https://cscie92.dce.harvard.edu/spring2021/Microsoft%20Extensible%20Firmware%20Initiative%20FAT32%2 0File%20System%20Specification,%20Version%201.03,%2020001206.pdf under Online Papers Used in Class • Important correction to this document concerns the DIR_CrtTimeTenth field in the FAT 32 Byte Directory Entry Structure • The name and description of this field is incorrect • Instead of DIR_CrtTimeTenth, we will use the name DIR_CrtTimeHundth • Here is the correct description of this field (to update the text on page 23): • Hundredths of a second time at file creation time. This field contains a count of hundredths of a second. Because the seconds portion of the DIR_CrtTime field denotes a creation time with a granularity of 2 seconds, this field contains a number of hundredths of a second (0 to 199, inclusively) that denotes a number of seconds from 0 to 1.99, inclusively, that may increment the number of seconds in addition to supplying the number of hundredths of a second. • There is also a typo on page 25 where a field is referred to as DIR_CrtTimeMil (which does not exist), and, as corrected here, should be DIR_CrtTimeHundth 2 SD Documentation • Documentation for the SD controller in the K70 • K70 Sub-Family Reference Manual, Rev.