RADIUS and Freeradius
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security on SPWF04S Module
AN4963 Application note Security on SPWF04S module Introduction The SPWF04S seriesa of Wi-Fi modules feature security functions designed to preserve confidentiality, communication integrity and authentication during wireless communication and Internet connection, on at least two levels. The first level involves communication between peers as in access to a web server. The communication data must not be read by entities other than the client and the server; the client must ensure that the peer it communicates with is authentic. This feature is provided by the Transport Layer Security (TLS) protocol, which allows client and server applications to communication that is confidential and secure. The second level involves communication between the Wi-Fi device and the Access Point. Radio communication is very easy to intercept: an attacker just needs an antenna to read transmission packets. Encryption is a key instrument in ensuring that packets cannot be read by anything other than the two peers in communication. Security at the level of Wi-Fi network is provided by WPA2-PSK when dealing with personal networks, and WPA2-Enterprise when dealing with enterprise networks. For WPA2-PSK, setting up the module for the network is facilitated by Wi-Fi protected setup (WPS). Devices that support firmware updating via Wi-Fi or firmware over-the-air (FOTA) must be able to assess the authenticity of the firmware source and the integrity of the image file after it has been received. a SPWF04Sxxx Wi-Fi module, www.st.com/wifimodules. November 2017 DocID030067 Rev 2 1/62 www.st.com Contents AN4963 Contents 1 Transport layer security (TLS) protocol overview ....................... -
Wireless Authentication Using Radius Server
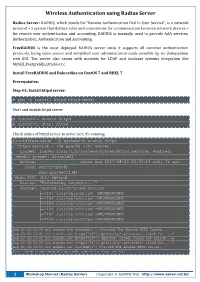
Wireless Authentication using Radius Server Radius Server: RADIUS, which stands for “Remote Authentication Dial In User Service”, is a network protocol – a system that defines rules and conventions for communication between network devices – for remote user authentication and accounting. RADIUS is normally used to provide AAA services; Authorization, Authentication and Accounting. FreeRADIUS is the most deployed RADIUS server since it supports all common authentication protocols, being open source and simplified user administration made possible by its dialupadmin web GUI. The server also comes with modules for LDAP and database systems integration like MySQL,PostgreSQL,Oracle e.t.c. Install FreeRADIUS and Daloradius on CentOS 7 and RHEL 7 Prerequisites: Step-01: Install httpd server: # yum -y install httpd httpd-devel Start and enable httpd server # systemctl enable httpd # systemctl start httpd Check status of httpd server to make sure it’s running [root@freeradius ~]# systemctl status httpd ● httpd.service - The Apache HTTP Server Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled) Active: active (running) since Sun 2017-08-20 02:33:03 EDT; 7s ago Docs: man:httpd(8) man:apachectl(8) Main PID: 7147 (httpd) Status: "Processing requests..." CGroup: /system.slice/httpd.service ├─7147 /usr/sbin/httpd -DFOREGROUND ├─7194 /usr/sbin/httpd -DFOREGROUND ├─7195 /usr/sbin/httpd -DFOREGROUND ├─7196 /usr/sbin/httpd -DFOREGROUND ├─7197 /usr/sbin/httpd -DFOREGROUND └─7199 /usr/sbin/httpd -DFOREGROUND Aug 20 02:33:00 ns1.mahedi.net systemd[1]: Starting The Apache HTTP Server... Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: AH00558: httpd: Could not reliab...e Aug 20 02:33:02 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:03 ns1.mahedi.net systemd[1]: Started The Apache HTTP Server. -

Cost Effective RADIUS Authentication for Wireless Clients
Database Systems Journal vol. I, no. 2/2010 27 Cost Effective RADIUS Authentication for Wireless Clients Alexandru ENACEANU Faculty of Computer Science, Romanian-American University, Bucharest, Romania [email protected] Gabriel GARAIS Faculty of Computer Science, Romanian-American University, Bucharest, Romania Network administrators need to keep administrative user information for each network device, but network devices usually support only limited functions for user management. WLAN security is a modern problem that needs to be solved and it requires a lot of overhead especially when applied to corporate wireless networks. Administrators can set up a RADIUS server that uses an external database server to handle authentication, authorization, and accounting for network security issues. Keywords: RADIUS, WLAN, Wireless Authentication, Wireless Access Control totally inadequate for a corporate wireless or Introduction Corporate wireless a campus network. That is because a 1 networks are in general the primary corporate wireless network has a lot of source of hacking into the corporate access points to reconfigure for changing the systems. The risks to users of wireless access key or adding a new MAC address to technology have increased lately, as the the allowed clients list. service has become more popular. There WLAN security can be significantly were relatively few dangers when wireless strengthened by using 802.1X to control technology was first introduced. Crackers access point access and deliver dynamic had not yet had time to latch on to the new keys to authenticated users. Authentication technology and wireless was not commonly Servers based on the RADIUS protocol play found in the work place. -

Experiences with BOWL: Managing an Outdoor Wifi Network (Or How to Keep Both Internet Users and Researchers Happy?) T
Experiences with BOWL: Managing an Outdoor WiFi Network (or How to Keep Both Internet Users and Researchers Happy?) T. Fischer, T. Huhn,¨ R. Kuck, R. Merz, J. Schulz-Zander, C. Sengul TU Berlin/Deutsche Telekom Laboratories {thorsten,thomas,rkuck,julius,cigdem}@net.t-labs.tu-berlin.de,[email protected] Abstract The Berlin Open Wireless Lab (BOWL) project at Technische Universitat¨ Berlin (TUB) maintains an out- door WiFi network which is used both for Internet ac- cess and as a testbed for wireless research. From the very beginning of the BOWL project, we experienced several development and operations challenges to keep Internet users and researchers happy. Development chal- lenges included allowing multiple researchers with very different requirements to run experiments in the network while maintaining reliable Internet access. On the oper- ations side, one of the recent issues we faced was au- thentication of users from different domains, which re- quired us to integrate with various external authentica- tion services. In this paper, we present our experience Figure 1: Coverage of the BOWL network on the TU- in handling these challenges on both development and Berlin campus. operations sides and the lessons we learned. Keywords: WiFi, configuration management, authenti- a variety of other networks and infrastructures which are cation, research, DevOps, infrastructure, testbed not controlled by the BOWL project, adding to the in- 1 Introduction herent complexity of running a production network. In this paper, we focus on two of our many challenges that Wireless testbeds are invaluable for researchers to test we have experienced in the last year while moving from their solutions under real system and network condi- a prototype to a more stable infrastructure. -

FREERADIUS TECHNICAL GUIDE CHAPTER 1 - INTRODUCTION WHAT IS FREERADIUS? Chapter 1 - Introduction
THE FREERADIUS TECHNICAL GUIDE CHAPTER 1 - INTRODUCTION WHAT IS FREERADIUS? Chapter 1 - Introduction This chapter describes: • What is RADIUS? • What is FreeRADIUS? • FreeRADIUS benefits • FreeRADIUS case studies 1.0 What is RADIUS? RADIUS, which stands for “Remote Authentication Dial In User Service”, is a network protocol - a system that defines rules and conventions for communication between network devices - for remote user authentication and accounting. Commonly used by Internet Service Providers (ISPs), cellular network providers, and corporate and educational networks, the RADIUS protocol serves three primary functions: • Authenticates users or devices before allowing them access to a network • Authorizes those users or devices for specific network services • Accounts for and tracks the usage of those services For a detailed look at how RADIUS performs these functions, see section 2.2, “The RADIUS Session Process”, on page 11. 1.0.1 History In 1991, Merit Network, a non-profit internet provider, required a creative way to manage dial-in access to various Points-Of-Presence (POPs) across its network. In response to this need, RADIUS was created by Livingston Enterprises. At the time RADIUS was created, network access systems were distributed across a wide area and were run by multiple independent organizations. Central administrators wanted to prevent problems with security and scalability, and thus did not want to distribute user names and passwords; instead, they wanted the remote access servers to contact a central server to authorize access to the requested system or service. In response to contact from the remote access server, the central server would return a “success” or “failure” message, and the remote machines would be in charge of enforcing this response for each end user. -

Django-Freeradius Documentation Release 0.1
django-freeradius Documentation Release 0.1 Fiorella De Luca Sep 10, 2020 Contents: 1 Setup 3 1.1 Create a virtual environment.......................................3 1.2 Install required system packages.....................................3 1.3 Install stable version from pypi.....................................3 1.4 Install development version.......................................4 1.5 Setup (integrate in an existing django project)..............................4 1.6 Migrating an existing freeradius database................................5 1.7 Installing for development........................................5 1.8 Troubleshooting.............................................6 1.9 Automating management commands..................................6 2 Available settings 9 2.1 DJANGO_FREERADIUS_EDITABLE_ACCOUNTING ........................9 2.2 DJANGO_FREERADIUS_EDITABLE_POSTAUTH ..........................9 2.3 DJANGO_FREERADIUS_GROUPCHECK_ADMIN ...........................9 2.4 DJANGO_FREERADIUS_GROUPREPLY_ADMIN ...........................9 2.5 DJANGO_FREERADIUS_USERGROUP_ADMIN ............................ 10 2.6 DJANGO_FREERADIUS_DEFAULT_SECRET_FORMAT ....................... 10 2.7 DJANGO_FREERADIUS_DISABLED_SECRET_FORMATS ..................... 10 2.8 DJANGO_FREERADIUS_RADCHECK_SECRET_VALIDATORS ................... 10 2.9 DJANGO_FREERADIUS_BATCH_DEFAULT_PASSWORD_LENGTH ................ 11 2.10 DJANGO_FREERADIUS_BATCH_DELETE_EXPIRED ........................ 11 2.11 DJANGO_FREERADIUS_BATCH_PDF_TEMPLATE ......................... 11 2.12 DJANGO_FREERADIUS_API_TOKEN -

Building, Installing, and Configuring a RADIUS Server George Mays, CCNA, A+, Network+, Security+, CTT+, I-Net+
Expert Reference Series of White Papers Building, Installing, and Configuring a RADIUS Server 1-800-COURSES www.globalknowledge.com Building, Installing, and Configuring a RADIUS Server George Mays, CCNA, A+, Network+, Security+, CTT+, I-Net+ Introduction I work often with a variety of networking devices from different manufacturers. In many cases the equipment is simply being evaluated, configured for demonstration purposes, or incorporated into a lab for classroom use. RADIUS is supported by a lot of these gadgets but I have never found a handy-dandy inexpensive and easy to use RADIUS server. Well, let’s build one. RADIUS is an acronym for Remote Authentication Dial-In User Services. It is an AAA tool intended to be useful in instances where the user would like to centralize management of authentication, authorization, and accounting functions (hence the AAA). Authentication, or proving that users are who they claim to be, is the primary reason that most people are driven to want a RADIUS server. But the authorization (limiting what a user is allowed to do once they have been authenticated) and accounting (logging and billing functions) will be of interest to some people, too. Where I most often like to demonstrate the use of RADIUS is in the configuration of Ethernet switches and IEEE 802.11 access points. For switches, RADIUS is most often used in conjunction with IEEE 802.1x port-based network access controls, which can in turn be used to control the identity of users who are allowed access to specific ports. For access points the same mechanism is actually in play, but it is used to limit who can associate with the wireless network. -

802.1X for Home Users and Guest Networks
Author Stefan Neuhuber Submission Institut of Networks and Security Thesis Supervisor Univ.-Prof. Priv.-Doz. DI Dr. René Mayrhofer February, 2017 802.1x for home users and guest networks Master’s Thesis to confer the academic degree of Diplom-Ingenieur in the Master’s Program Computer Science JOHANNES KEPLER UNIVERSITY LINZ Altenbergerstraße 69 4040 Linz, Österreich www.jku.at DVR 0093696 Contents 1. Introduction ....................................... 1 1.1. Motivation . 1 1.2. Threat Model and security concerns . 2 1.3. Structure . 2 2. State of the art ..................................... 3 3. Employed Technologies and Tools ........................... 8 3.1. OpenWrt . 8 3.1.1. Architecture . 9 3.1.2. Build System . 9 3.1.3. Flash Memory Layout . 10 3.1.4. The Unified Configuration Interface (UCI) System . 13 3.2. Port-Based Authentication - 802.1x . 15 3.2.1. Primary Components . 17 3.2.2. Authentication Process . 19 3.2.2.1. Communication between Supplicant and Authenticator (802.1x) . 20 3.2.2.2. Communication between Authenticator and Authentication Server (RADIUS) . 22 3.2.2.3. Communication between Supplicant and Authentication Server (EAP-Method) . 23 3.3. EAPoL/EAPoW Protocol . 24 3.3.1. Packet Structure . 25 Version . 25 Type..................................... 25 Length . 26 Packet Body . 26 3.4. Extensible Authentication Protocol (EAP) . 26 3.4.1. Packet Structure . 27 Code..................................... 28 Identifier . 28 Length . 29 I Data . 29 3.4.2. Packet Types . 29 EAP-Request/Response . 29 EAP-Success/Failure . 30 3.4.3. EAP-Methods . 30 3.4.3.1. Packet Structure . 31 Type ................................. 31 Data . 31 3.4.3.2. -

CHAPTER 6 - EAP AUTHENTICATION the PROCESS Chapter 6 - EAP Authentication
THE FREERADIUS IMPLEMENTATION GUIDE CHAPTER 6 - EAP AUTHENTICATION THE PROCESS Chapter 6 - EAP Authentication This chapter describes using Extensible Authentication Protocol with FreeRADIUS. The following topics are discussed in this chapter: • EAP Overview • Types/Methods • Testing with eapol_test • TLS based EAP methods • Certificates 6.0 EAP Overview EAP stands for Extensible Authentication Protocol. The extensible portion of the EAP acronym describes the intended use of the protocol: EAP is a simple wrapper that can transport other authentication methods. These other methods are independent of the encapsulating EAP layer and are independent of each other. EAP provides only for authentication. There is no way to transport authorization data in EAP (as opposed to RADIUS, which can send authorization data); therefore, only success and failure can be transported in EAP - other information such as IP address assignments and session timeouts cannot be transported in this manner. The protocol originally started out in PPP, where it was intended to replace the use of PAP and CHAP. Since then, it has gained wider use in wired and wireless network authentication, especially with 802.1X When used in conjunction with RADIUS, EAP requires the following participants (the names used here are taken from the IEEE 802.1X standard): • Supplicant The supplicant is the machine that requests network access to a Local Area Network (LAN). It contains the credentials used for authentication, and it is one end of the EAP exchange. • Authenticator The authenticator is the Access Point or switch that controls access to the LAN. It allows or denies network access based on the status returned by EAP. -

Radius: a Remote Authentication Dial-In User Service
InSight: RIVIER ACADEMIC JOURNAL, VOLUME 5, NUMBER 2, FALL 2009 RADIUS: A REMOTE AUTHENTICATION DIAL-IN USER SERVICE Daniel Szilagyi*, Arti Sood** and Tejinder Singh§ M.S. in Computer Science Program, Rivier College Abstract This paper provides an overview of RADIUS deployment in the network. It also introduces the various protocols, such as EAP, that is used to implement this service, and PAP, CHAP, MSCHAP, EAP-TLS, EAP-TTLS, EAP- LEAP, EAP-FAST, EAP-FAST that provide authentication mechanisms. These protocols are not discussed in detail but only to present the idea of workflow as to how the RADIUS works in conjunction with them. The role of RADIUS is outlined in point-to-point and VPN connection. Also the 802.1x framework and RADIUS are described briefly. The various AAA protocols are discussed briefly along with DIAMETER, an enhanced version of the RADIUS protocol. This paper is intended for readers with Computer Science or Information Technology background. 1. Overview With growing numbers of remote users like telecommuters using wireless laptops, PDA(s) trying to access the network, Remote Authentication Dial-In User Service (RADIUS) is widely used. RADIUS, a distributed service, provides centralized management of user access control and security. RADIUS manages and secures the Wireless Local Area Network (WLAN), remote Virtual Private Network (VPN), and wired access. RADIUS is available as a standalone service like Internet Authentication Service (IAS), Access Control Server (ACS) etc. It may also be embedded in the network devices such as routers, switches etc. Users are authenticated by the RADIUS server against a central database which stores profile data such as passwords, type of access, etc. -

7360 Freeradius Category: Experimental September 2014 ISSN: 2070-1721
Internet Engineering Task Force (IETF) A. DeKok Request for Comments: 7360 FreeRADIUS Category: Experimental September 2014 ISSN: 2070-1721 Datagram Transport Layer Security (DTLS) as a Transport Layer for RADIUS Abstract The RADIUS protocol defined in RFC 2865 has limited support for authentication and encryption of RADIUS packets. The protocol transports data in the clear, although some parts of the packets can have obfuscated content. Packets may be replayed verbatim by an attacker, and client-server authentication is based on fixed shared secrets. This document specifies how the Datagram Transport Layer Security (DTLS) protocol may be used as a fix for these problems. It also describes how implementations of this proposal can coexist with current RADIUS systems. Status of This Memo This document is not an Internet Standards Track specification; it is published for examination, experimental implementation, and evaluation. This document defines an Experimental Protocol for the Internet community. This document is a product of the Internet Engineering Task Force (IETF). It represents the consensus of the IETF community. It has received public review and has been approved for publication by the Internet Engineering Steering Group (IESG). Not all documents approved by the IESG are a candidate for any level of Internet Standard; see Section 2 of RFC 5741. Information about the current status of this document, any errata, and how to provide feedback on it may be obtained at http://www.rfc-editor.org/info/rfc7360. DeKok Experimental [Page 1] RFC 7360 DTLS as a Transport Layer for RADIUS September 2014 Copyright Notice Copyright (c) 2014 IETF Trust and the persons identified as the document authors. -

Application Note 582911
AN12661 EdgeLockTM SE05x for Wi-Fi Credential Protection Rev. 1.2 — 7 December 2020 Application note 582911 Document information Information Content Keywords EdgeLock SE05x, Wi-Fi credentials, WPA-EAP-TLS Abstract This application note describes how to leverage EdgeLock SE05x for Wi-Fi credential protection. It explains how to run a demo setup that showcases the use of EdgeLock SE05x ease of use configuration to authenticate devices to a Wi-Fi network based on WPA-EAP-TLS protocol. NXP Semiconductors AN12661 EdgeLockTM SE05x for Wi-Fi Credential Protection Revision history Revision history Revision Date Description number 1.0 2020-05-14 First version. 1.1 2020-06-12 ssscli compilation instructions updated 1.2 2020-12-07 Updated to the latest template and fixed broken URLs AN12661 All information provided in this document is subject to legal disclaimers. © NXP B.V. 2020. All rights reserved. Application note Rev. 1.2 — 7 December 2020 582911 2 / 17 NXP Semiconductors AN12661 EdgeLockTM SE05x for Wi-Fi Credential Protection 1 Abbreviations Table 1. Abbreviations Acronym Description WSN Wireless Sensor Network AP Access Point CA Certificate Authority RADIUS Remote Authentication Dial-In User Service PCR Platform Configuration Registers OEM Original Equipment Manufacturer ECC Elliptic-Curve Cryptography MCU Micro Controller Unit PMK Pairwise Master Key PTK Pairwise Transient Key PBKDF Password-Based Key Derivation Function PSK Pre-Shared Key EAP Extensible Authentication Protocol TLS Transport Layer Security SSL Secure Sockets Layer AN12661 All information provided in this document is subject to legal disclaimers. © NXP B.V. 2020. All rights reserved. Application note Rev. 1.2 — 7 December 2020 582911 3 / 17 NXP Semiconductors AN12661 EdgeLockTM SE05x for Wi-Fi Credential Protection 2 EdgeLock SE05x for Wi-Fi credential protection Today’s networks include a wide range of wireless devices, from computers and phones to IP cameras, smart TVs and connected appliances.