Design of a Dual Stack DNS Server with Dynamic Updates
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ROBRA – the Snake Robot
International Journal of Computer Science Trends and Technology (IJCST) – Volume 7 Issue 3, May - Jun 2019 RESEARCH ARTICLE OPEN ACCESS ROBRA – The Snake Robot James M.V, Nandukrishna S, Noyal Jose, Ebin Biju Department of Computer Science and Engineering Toc H Institute of Science & Technology, Ernakulam Kerala – India ABSTRACT Robra - A snake-like robot which, provides the locomotion of a real snake. The shape and size of the robot depends on application. Robra can avoid obstacles by receiving signals from sensors and move with flexibility on terrain surfaces. Multiple joints increases its degree of freedom. It can quickly explore and navigate foreign environments and detect potential dangers for direct human involvement. Robra uses PIR() to detect presence of humans in an environment like civilians trapped in collapsed buildings during natural disasters. It can move through crevices and uneven surfaces. It detects obstacles by using Ultrasonic range movement sensors. This provides noncontact distance between the obstacles to detect and avoid collision with them. Electro chemical sensors are used for detection of poisonous gases. Robra has an onboard camera which records and send the video data in real time via WiFi. Robra has microphones for the survivors to communicate and inform their status incase of rescue aid. Thus Robra covers wide real time applications like surveillance, rescue aid etc. Keywords:- Robra, Snake, act have a wingspan almost 10 feet, giving it an ape-like I. INTRODUCTION appearance. In the past two decades it is estimated that disasters are Momaro - This robot has been specifically designed by the responsible for about 3 million deaths worldwide, 800million team NimbRo Rescue from the University of Bonn in people adversely affected. -

Table of Content
TABLE OF CONTENT 1. What is Joomla………………………………………………………………. 2 2. Download and Install Joomla………………………………………………. 3 2.1 Pre-installation Check………………………………………………….... 3 2.2 Configuration …………………………………………………………… 4 3. Creating Content……………………………………………………………....9 3.1 Create a Category…………………………………………………………9 3.2 Create Article………………………………………………………………10 4. Modules……………………………………………………………………….. 12 5. How to Show Position for Template?....................................................... 14 6. Menu……………………………………………………………………………16 6.1 How to Create Menu?.........................................................................16 7. User……………………………………………………………………………. 18 7.1 Users Groups…………………………………………………………….. 18 7.2 Add New User……………………………………………………………..19 1 1. What is Joomla? Joomla is a free system for creating websites. It is an open source project, which, like most open source projects, is constantly in motion. It has been extremely successful for seven years now and is popular with millions of users worldwide. The word Joomla is a derivative of the word Joomla from the African language Swahili and means "all together". The project Joomla is the result of a heated discussion between the Mambo Foundation, which was founded in August 2005, and its then-development team. Joomla is a development of the successful system Mambo. Joomla is used all over the world for simple homepages and for complex corporate websites as well. It is easy to install, easy to manage and very reliable. The Joomla team has organized and reorganized itself throughout the last seven years to better meet the user demands. 2 2. Download and Install Joomla “Where and what to download?” “How to install?” In order to install Joomla! on your local computer, it is necessary to set up your "own internet", for which you'll need a browser, a web server, a PHP environment and as well a Joomla supported database system. -

Security on SPWF04S Module
AN4963 Application note Security on SPWF04S module Introduction The SPWF04S seriesa of Wi-Fi modules feature security functions designed to preserve confidentiality, communication integrity and authentication during wireless communication and Internet connection, on at least two levels. The first level involves communication between peers as in access to a web server. The communication data must not be read by entities other than the client and the server; the client must ensure that the peer it communicates with is authentic. This feature is provided by the Transport Layer Security (TLS) protocol, which allows client and server applications to communication that is confidential and secure. The second level involves communication between the Wi-Fi device and the Access Point. Radio communication is very easy to intercept: an attacker just needs an antenna to read transmission packets. Encryption is a key instrument in ensuring that packets cannot be read by anything other than the two peers in communication. Security at the level of Wi-Fi network is provided by WPA2-PSK when dealing with personal networks, and WPA2-Enterprise when dealing with enterprise networks. For WPA2-PSK, setting up the module for the network is facilitated by Wi-Fi protected setup (WPS). Devices that support firmware updating via Wi-Fi or firmware over-the-air (FOTA) must be able to assess the authenticity of the firmware source and the integrity of the image file after it has been received. a SPWF04Sxxx Wi-Fi module, www.st.com/wifimodules. November 2017 DocID030067 Rev 2 1/62 www.st.com Contents AN4963 Contents 1 Transport layer security (TLS) protocol overview ....................... -
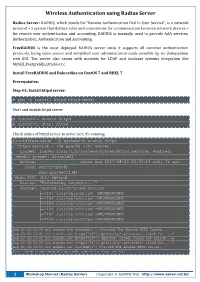
Wireless Authentication Using Radius Server
Wireless Authentication using Radius Server Radius Server: RADIUS, which stands for “Remote Authentication Dial In User Service”, is a network protocol – a system that defines rules and conventions for communication between network devices – for remote user authentication and accounting. RADIUS is normally used to provide AAA services; Authorization, Authentication and Accounting. FreeRADIUS is the most deployed RADIUS server since it supports all common authentication protocols, being open source and simplified user administration made possible by its dialupadmin web GUI. The server also comes with modules for LDAP and database systems integration like MySQL,PostgreSQL,Oracle e.t.c. Install FreeRADIUS and Daloradius on CentOS 7 and RHEL 7 Prerequisites: Step-01: Install httpd server: # yum -y install httpd httpd-devel Start and enable httpd server # systemctl enable httpd # systemctl start httpd Check status of httpd server to make sure it’s running [root@freeradius ~]# systemctl status httpd ● httpd.service - The Apache HTTP Server Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled) Active: active (running) since Sun 2017-08-20 02:33:03 EDT; 7s ago Docs: man:httpd(8) man:apachectl(8) Main PID: 7147 (httpd) Status: "Processing requests..." CGroup: /system.slice/httpd.service ├─7147 /usr/sbin/httpd -DFOREGROUND ├─7194 /usr/sbin/httpd -DFOREGROUND ├─7195 /usr/sbin/httpd -DFOREGROUND ├─7196 /usr/sbin/httpd -DFOREGROUND ├─7197 /usr/sbin/httpd -DFOREGROUND └─7199 /usr/sbin/httpd -DFOREGROUND Aug 20 02:33:00 ns1.mahedi.net systemd[1]: Starting The Apache HTTP Server... Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: AH00558: httpd: Could not reliab...e Aug 20 02:33:02 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:03 ns1.mahedi.net systemd[1]: Started The Apache HTTP Server. -

Table of Contents
Table of Contents Introduction . 3 IT Strategic Plan Synopsis . 4 IT Organization . 6 Our Mission . 7 Our Vision . 7 Enterprise IT Technical Roadmap . 8 Year One — 2012 . 8 Year Two — 2013 . 11 Year Three — 2014 . 14 Technology Timeline . 17 SRNS Leadership Team . 20 SRNS-IT Leadership . 21 Partner CIOs . 22 Information Technology Strategic Background . 23 2012 IT Focus Areas . 24 DOE 2012 Strategic Plan . 25 NNSA 2012 Strategic Plan . 25 DOE Strategic Plan Alignment to IT Focus Areas . 26 NNSA Strategic Plan Alignment to IT Focus Areas . 27 enterprise•SRS 2012 Strategic Plan . 28 e•SRS Strategic Plan Alignment to IT Focus Areas . 29 Attachment A — Accelerating SRS Missions and Reducing Infrastructure through Innovative Computing and Communications . 30 Current Status of 2009 IT Strategic Initiatives . 31 Attachment B — Recent Accomplishments . 34 2012–2014 SRNS Information Technology Strategic Plan Introduction Information Technology’s (IT) objective is to provide our customers with services and solutions that facilitate their day-to-day operations, helping each customer to be successful in meeting their business goals and objectives. Further, it is our intent to meet this objective with services and solutions that adhere to industry standards and best practices, delivered by our staff of talented and skilled people who are attuned to our customers’ businesses and needs and who strive to deliver exceptional services. The goal of this strategic plan is to put forward a roadmap for the next three years (2012-2014) that assists us in identifying the technologies and solutions needed to better support the strategic direction of the Savannah River Site (SRS). -

Cost Effective RADIUS Authentication for Wireless Clients
Database Systems Journal vol. I, no. 2/2010 27 Cost Effective RADIUS Authentication for Wireless Clients Alexandru ENACEANU Faculty of Computer Science, Romanian-American University, Bucharest, Romania [email protected] Gabriel GARAIS Faculty of Computer Science, Romanian-American University, Bucharest, Romania Network administrators need to keep administrative user information for each network device, but network devices usually support only limited functions for user management. WLAN security is a modern problem that needs to be solved and it requires a lot of overhead especially when applied to corporate wireless networks. Administrators can set up a RADIUS server that uses an external database server to handle authentication, authorization, and accounting for network security issues. Keywords: RADIUS, WLAN, Wireless Authentication, Wireless Access Control totally inadequate for a corporate wireless or Introduction Corporate wireless a campus network. That is because a 1 networks are in general the primary corporate wireless network has a lot of source of hacking into the corporate access points to reconfigure for changing the systems. The risks to users of wireless access key or adding a new MAC address to technology have increased lately, as the the allowed clients list. service has become more popular. There WLAN security can be significantly were relatively few dangers when wireless strengthened by using 802.1X to control technology was first introduced. Crackers access point access and deliver dynamic had not yet had time to latch on to the new keys to authenticated users. Authentication technology and wireless was not commonly Servers based on the RADIUS protocol play found in the work place. -

LUO-THESIS.Pdf (3.607Mb)
BUILDING A DISTRIBUTED TRUST MODEL OF RESTFUL WEB SERVICES FOR MOBILE DEVICES A Thesis Submitted to the College of Graduate Studies and Research In Partial Fulfillment of the Requirements For the Degree of Master of Science In the Department of Computer Science University of Saskatchewan Saskatoon By Min Luo Copyright Min Luo, September, 2012. All rights reserved. PERMISSION TO USE In presenting this thesis in partial fulfilment of the requirements for a Postgraduate degree from the University of Saskatchewan, I agree that the Libraries of this University may make it freely available for inspection. I further agree that permission for copying of this thesis in any manner, in whole or in part, for scholarly purposes may be granted by the professor or professors who supervised my thesis work or, in their absence, by the Head of the Department or the Dean of the College in which my thesis work was done. It is understood that any copying or publication or use of this thesis or parts thereof for financial gain shall not be allowed without my written permission. It is also understood that due recognition shall be given to me and to the University of Saskatchewan in any scholarly use which may be made of any material in my thesis. Requests for permission to copy or to make other use of material in this thesis in whole or part should be addressed to: Head of the Department of Computer Science 176 Thorvaldson Building 110 Science Place University of Saskatchewan Saskatoon, Saskatchewan (S7N 5C9) ACKNOWLEDGMENTS First of all I would like to thank my supervisor, Dr. -

Experiences with BOWL: Managing an Outdoor Wifi Network (Or How to Keep Both Internet Users and Researchers Happy?) T
Experiences with BOWL: Managing an Outdoor WiFi Network (or How to Keep Both Internet Users and Researchers Happy?) T. Fischer, T. Huhn,¨ R. Kuck, R. Merz, J. Schulz-Zander, C. Sengul TU Berlin/Deutsche Telekom Laboratories {thorsten,thomas,rkuck,julius,cigdem}@net.t-labs.tu-berlin.de,[email protected] Abstract The Berlin Open Wireless Lab (BOWL) project at Technische Universitat¨ Berlin (TUB) maintains an out- door WiFi network which is used both for Internet ac- cess and as a testbed for wireless research. From the very beginning of the BOWL project, we experienced several development and operations challenges to keep Internet users and researchers happy. Development chal- lenges included allowing multiple researchers with very different requirements to run experiments in the network while maintaining reliable Internet access. On the oper- ations side, one of the recent issues we faced was au- thentication of users from different domains, which re- quired us to integrate with various external authentica- tion services. In this paper, we present our experience Figure 1: Coverage of the BOWL network on the TU- in handling these challenges on both development and Berlin campus. operations sides and the lessons we learned. Keywords: WiFi, configuration management, authenti- a variety of other networks and infrastructures which are cation, research, DevOps, infrastructure, testbed not controlled by the BOWL project, adding to the in- 1 Introduction herent complexity of running a production network. In this paper, we focus on two of our many challenges that Wireless testbeds are invaluable for researchers to test we have experienced in the last year while moving from their solutions under real system and network condi- a prototype to a more stable infrastructure. -

Demetri Kambanis
801 N. Fairfax Ave., #312 Los Angeles, CA 90046 917-294-8987 [email protected] Demetri Kambanis Technical Director with 12+ years of agency experience leading large-scale technology projects for Fortune 500 companies. I combine strong technology design/strategy skills with the operational experience running development teams for projects involving a full solution stack. I have expertise in the full software development lifecycle, proficiency in the agile methodology and deep project management skills, having provided the effective planning and implementation that led to numerous successful project launches. I help streamline technology processes and tools that drive efficiencies and ensure quality and project profitability. I have several years of hands-on development expertise in numerous client-side and server-side technologies, including work with content management systems. Strengths include: ! Technical analysis and design, server architecture, solution definition, product evaluation, integration with existing systems ! Day-to-day team operational management, resourcing, staffing and outsourcing ! Hands-on development with front-end and back-end technologies, including work with content management systems ! Strong experience in server and network design and architecture, ensuring performance, availability and security ! Technology project planning and scoping, scheduling, budgeting and estimating ! Strong experience in agile development, test-driven and behavior-driven development ! Relationship with technology partners, vendors -

Web-Base Orientation to Living and Studying in Kokkola, Finland
Yewon Temitayo Gbetoyon WEB-BASE ORIENTATION TO LIVING AND STUDYING IN KOKKOLA, FINLAND. Bachelor's thesis CENTRIA UNIVERSITY OF APPLIED SCIENCES Degree Programme in Information Technology December, 2012. Abstract CENTRIA UNIVERSITY Date Author OF APPLIED SCIENCES DECEMBER 2012 YEWON TEMITAYO GBETOYON Degree Programme Information Technology Name of thesis WEB-BASE ORIENTATION TO LIVING AND STUDYING IN KOKKOLA, FINLAND Instructor Pages GRZEGORY SZEWCYK [65] Supervisor ARTUR HLOBAZ The aim of this thesis was to create a website that gives general knowledge prospective foreign applicants (full time students and exchange students) applying to Centria University of Applied Sciences, Kokkola to study. The website entails up-to-date information in the area of description of the university, requirements for applying, entrance examination abroad, visa application requirements for non-EU Students. Joomla! 1.5 and XAMMP were the two software employed for designing the website. The rudiments and functionalities that came with Joomla and XAMMP made it possible to build a complete website. However, a number of challenges were encountered while creating a suitable template and employing the right modules for the intended purposes of the website. These problems were resolved with the help of the Joomla forum and supports that Joomla user can get from free from the Joomla website (www.forum .joomla.org). Moreso, for the creation of a full website, Joomla may be required as a good option for designing a website because every year the developers of Joomla add new features that make website designing more comprehensible. Therefore, for the purpose of this thesis, a website designed with Joomla that gives rise to the creation of many web pages and the results of the website is presented in the framework. -

Arcnews Summer 2014 Newsletter
ArcNews Esri | Summer 2014 | Vol. 36, No. 2 White House Climate Data Initiative Advances on Many Fronts Coastal flooding. Sea level rise. Drought. The Obama administration says The ArcGIS Platform in 2014 it wants to help communities better prepare for climate change effects like People today expect to access the information they need, collaborate with others, and produce these by using scientific data, technology, and technical know-how from the results at any time, on any device, from wherever they are. The line between the work people do public and private sectors. inside and outside their offices is blurring; analysis and decision making are taking place whenever Esri is joining Microsoft and several other tech companies to provide tech- and wherever they need to occur. In anticipation of these growing trends, Esri has evolved ArcGIS nology and expertise for the White House’s Climate Data Initiative. into a location platform that gives people in any organization the ability to discover, use, make, and “The notion is to create and share knowledge to make communities more share maps from any device, anywhere, at any time. resilient,” said Esri president Jack Dangermond. continued on page 4 ArcGIS Already Supports GeoPackage Esri Leads in Supporting OGC Standards “Esri continues to add support for many open and interoperable data sources,” says Keith Ryden, Esri software development team member, who led Esri’s work on GeoPackage and worked on the Open Geospatial Consortium, Inc. (OGC), standard. “Adding GeoPackage support was a natural progres- sion to our previous support of OGC WMS, WMTS, WFS, WCS, and OGC KML. -

FREERADIUS TECHNICAL GUIDE CHAPTER 1 - INTRODUCTION WHAT IS FREERADIUS? Chapter 1 - Introduction
THE FREERADIUS TECHNICAL GUIDE CHAPTER 1 - INTRODUCTION WHAT IS FREERADIUS? Chapter 1 - Introduction This chapter describes: • What is RADIUS? • What is FreeRADIUS? • FreeRADIUS benefits • FreeRADIUS case studies 1.0 What is RADIUS? RADIUS, which stands for “Remote Authentication Dial In User Service”, is a network protocol - a system that defines rules and conventions for communication between network devices - for remote user authentication and accounting. Commonly used by Internet Service Providers (ISPs), cellular network providers, and corporate and educational networks, the RADIUS protocol serves three primary functions: • Authenticates users or devices before allowing them access to a network • Authorizes those users or devices for specific network services • Accounts for and tracks the usage of those services For a detailed look at how RADIUS performs these functions, see section 2.2, “The RADIUS Session Process”, on page 11. 1.0.1 History In 1991, Merit Network, a non-profit internet provider, required a creative way to manage dial-in access to various Points-Of-Presence (POPs) across its network. In response to this need, RADIUS was created by Livingston Enterprises. At the time RADIUS was created, network access systems were distributed across a wide area and were run by multiple independent organizations. Central administrators wanted to prevent problems with security and scalability, and thus did not want to distribute user names and passwords; instead, they wanted the remote access servers to contact a central server to authorize access to the requested system or service. In response to contact from the remote access server, the central server would return a “success” or “failure” message, and the remote machines would be in charge of enforcing this response for each end user.