Radius: a Remote Authentication Dial-In User Service
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

EAP-TLS Authentication with an NPS RADIUS Server
EAP-TLS Authentication with an NPS RADIUS Server 802.1X/EAP-TLS (Extensible Authentication Protocol-Transport Layer Security), defined in RFC 5216, provides secure authentication methods. Client devices (RADIUS supplicants) and a RADIUS authentication server verify each other's identity by validating the signature on the computer and server certificates that they send one another. This authentication method uses an infrastructure that includes a RADIUS authentication server that communicates with an external LDAP database. It also needs a mechanism for installing certificates on the server and all the supplicants, which you can do with a Windows NPS (Network Policy Server) using a GPO (Group Policy Object) to distribute computer certificates and an 802.1X SSID client configuration for wireless access. You can also employ the same infrastructure to authenticate users (also referred to as RADIUS supplicants) who submit user names and passwords to the authentication server. This document explains how to set up the following components to provide wireless client and user authentication through 802.1X/EAP-TLS: • (Aerohive) An 802.1X SSID that instructs APs (RADIUS authenticators) to forward authentication requests to an NPS RADIUS server • (Windows) An NPS RADIUS server that accepts authentication requests from the APs and EAP-TLS authentication requests from clients • (Windows) A GPO to deploy computer certificates and a wireless network configuration to clients • (Aerohive and Windows – optional) An Aerohive and NPS configuration in which different RADIUS attributes are returned based on authentication method (EAP-TLS or PEAP-MS-CHAPv2 in this example) assigning one user profile to clients authenticating by certificate and another to users authenticating by user name/password. -

Utility-Grade Core Network Services
WHITEPAPER Utility-Grade Core Network Services The infoblox appliance-based platform integrates distributes, and manages DNS, DHCP, IPAM, TFTP, NTP and more to drive networks and applications Executive Summary Networks and applications have become highly dependent on a collection of essential core network services that are not always “visible” or on the forefront of IT project lists. For example, virtually all applications, including web, e-mail, ERP, CRM, and Microsoft’s Active Directory require the Domain Name System (DNS) for their basic operation. Most IP-based devices, including laptops and desktops, require Dynamic Host Configuration Protocol (DHCP) to obtain an IP address. Newer devices such as IP phones, RFID readers, and cameras that are network-connected require file transfer services (via TFTP or HTTP) to receive configuration information and firmware updates. If core network services are compromised, networks and applications fail. These failures often manifest themselves as “network” or “application” issues but are often caused by failure of the underlying core network services themselves. A majority of enterprises still use an “ad-hoc” collection of disparate systems to deploy core network services and are, therefore, experiencing growing problems with availability, security, audit-ability, and real-time data integration that threaten current and future applications. For more than a decade, the focus of networking professionals has been on physical network architectures with high levels of redundancy and fault-tolerance. From the endpoint inward, enterprise networks are designed to provide high availability with device redundancy and multiple paths among users and data. One of the key components of these architectures has been the network appliance, purpose-built devices that are designed to perform a specific function such as routing, switching, or gateway applications. -

7750 SR OS System Management Guide
7750 SR OS System Management Guide Software Version: 7750 SR OS 10.0 R4 July 2012 Document Part Number: 93-0071-09-02 *93-0071-09-02* This document is protected by copyright. Except as specifically permitted herein, no portion of the provided information can be reproduced in any form, or by any means, without prior written permission from Alcatel-Lucent. Alcatel, Lucent, Alcatel-Lucent and the Alcatel-Lucent logo are trademarks of Alcatel-Lucent. All other trademarks are the property of their respective owners. The information presented is subject to change without notice. Alcatel-Lucent assumes no responsibility for inaccuracies contained herein. Copyright 2012 Alcatel-Lucent Alcatel-Lucent. All rights reserved. Table of Contents Preface. .13 Getting Started Alcatel-Lucent 7750 SR Router Configuration Process . .17 Security Authentication, Authorization, and Accounting . .20 Authentication . .21 Local Authentication . .22 RADIUS Authentication . .22 TACACS+ Authentication . .25 Authorization . .26 Local Authorization. .27 RADIUS Authorization . .27 TACACS+ Authorization. .27 Accounting. .28 RADIUS Accounting . .28 TACACS+ Accounting . .28 Security Controls . .30 When a Server Does Not Respond . .30 Access Request Flow . .31 CPU Protection . .32 CPU Protection Extensions ETH-CFM . .36 Vendor-Specific Attributes (VSAs) . .38 Other Security Features . .39 Secure Shell (SSH) . .39 Per Peer CPM Queuing. .41 Filters and Traffic Management. .42 TTL Security for BGP and LDP . .43 Exponential Login Backoff . .43 User Lockout . .45 Encryption . .46 802.1x Network Access Control . .46 TCP Enhanced Authentication Option. .46 Packet Formats . .48 Keychain. .49 Configuration Notes . .50 General . .50 Configuring Security with CLI . .51 Setting Up Security Attributes. .52 Configuring Authentication . .52 Configuring Authorization . -

Extensible Authentication Protocol (EAP) and IEEE 802.1X: Tutorial and Empirical Experience
CHEN LAYOUT 11/17/05 11:57 AM Page 52 Extensible Authentication Protocol (EAP) and IEEE 802.1x: Tutorial and Empirical Experience JYH-CHENG CHEN AND YU-PING WANG, NATIONAL TSING HUA UNIVERSITY Abstract oped WIRE1x to support various versions of MS Windows. As This article presents the technical details of the Extensible the name suggests, WIRE1x is an open-source implementa- Authentication Protocol (EAP) and IEEE 802.1x by using tion of IEEE 802.1x client (supplicant)1 developed by the WIRE1x, an open-source implementation of IEEE 802.1x Wireless Internet Research & Engineering (WIRE) Laborato- client (supplicant) and various EAP-based authentication ry.2 Both source code and executable code of WIRE1x can be mechanisms. By using a real implementation, 802.1x and EAP downloaded freely from http://wire.cs.nthu.edu.tw/wire1x/. should be easily understood. Essentially, 802.1x provides a framework for port-based access control. It can work with various authentication mecha- nisms to authenticate and authorize users. The Extensible Introduction Authentication Protocol (EAP, IETF RFC 2284) is a protocol Wireless local area networks (WLANs) have become increas- commonly used in 802.1x to authenticate users. Currently, ingly more prevalent in recent years. The IEEE 802.11 stan- WIRE1x provides various authentication mechanisms, includ- dard is one of the most widely adopted standards for ing EAP Message Digest 5 (EAP-MD5, IETF RFC 1321), broadband wireless Internet access. However, security consid- EAP Transport Layer Security (EAP-TLS, IETF RFC 2716), erations with regard to wireless environments are more com- EAP Tunneled TLS (EAP-TTLS) [5], and Protected Extensi- plicated than those in wired environments. -

Aerohive Configuration Guide: RADIUS Authentication | 2
Aerohive Configuration Guide RADIUS Authentication Aerohive Configuration Guide: RADIUS Authentication | 2 Copyright © 2012 Aerohive Networks, Inc. All rights reserved Aerohive Networks, Inc. 330 Gibraltar Drive Sunnyvale, CA 94089 P/N 330068-03, Rev. A To learn more about Aerohive products visit www.aerohive.com/techdocs Aerohive Networks, Inc. Aerohive Configuration Guide: RADIUS Authentication | 3 Contents Contents ...................................................................................................................................................................................................................... 3 IEEE 802.1X Primer................................................................................................................................................................................................... 4 Example 1: Single Site Authentication .................................................................................................................................................................... 6 Step 1: Configuring the Network Policy ..............................................................................................................................................................7 Step 2: Configuring the Interface and User Access .........................................................................................................................................7 Step 3: Uploading the Configuration and Certificates .................................................................................................................................... -

Kerberos: an Authentication Service for Computer Networks by Clifford Neuman and Theodore Ts’O
Kerberos: An Authentication Service for Computer Networks by Clifford Neuman and Theodore Ts’o Presented by: Smitha Sundareswaran Chi Tsong Su Introduction z Kerberos: An authentication protocol based on cryptography z Designed at MIT under project Athena z Variation of Needham Schroeder protocol - Difference: Kerberos assumes all systems on the network to be synchronized z Similar function as its mythological namesake: “guards” the access to network protocols Contribution z Defines ideas of authentication, Integrity, confidentiality and Authorization z Working of Kerberos z Limitations z Utilities z How to obtain and use Kerberos z Other methods to improve security Why Kerberos? z Foils threats due to eavesdropping z More convenient than password based authentication { Allows user to avoid “authentication by assertion” z Authentication based on cryptography: attacker can’t impersonate a valid user How Kerberos Works z Distributed authentication service using a series of encrypted messages {Password doesn’t pass through the network z Timestamps to reduce the number of messages needed for authentication z “Ticket granting Service” for subsequent authentication Kerberos Authentication and Encryption zAuthentication proves that a client is running on behalf of a particular user zUses encryption key for authentication {Encryption key = Password zEncryption implemented using DES {Checksum included in message checksum and encryption provide integrity & confidentiality The Kerberos Ticket z Initially, client and Server don’t share an encryption -

Security on SPWF04S Module
AN4963 Application note Security on SPWF04S module Introduction The SPWF04S seriesa of Wi-Fi modules feature security functions designed to preserve confidentiality, communication integrity and authentication during wireless communication and Internet connection, on at least two levels. The first level involves communication between peers as in access to a web server. The communication data must not be read by entities other than the client and the server; the client must ensure that the peer it communicates with is authentic. This feature is provided by the Transport Layer Security (TLS) protocol, which allows client and server applications to communication that is confidential and secure. The second level involves communication between the Wi-Fi device and the Access Point. Radio communication is very easy to intercept: an attacker just needs an antenna to read transmission packets. Encryption is a key instrument in ensuring that packets cannot be read by anything other than the two peers in communication. Security at the level of Wi-Fi network is provided by WPA2-PSK when dealing with personal networks, and WPA2-Enterprise when dealing with enterprise networks. For WPA2-PSK, setting up the module for the network is facilitated by Wi-Fi protected setup (WPS). Devices that support firmware updating via Wi-Fi or firmware over-the-air (FOTA) must be able to assess the authenticity of the firmware source and the integrity of the image file after it has been received. a SPWF04Sxxx Wi-Fi module, www.st.com/wifimodules. November 2017 DocID030067 Rev 2 1/62 www.st.com Contents AN4963 Contents 1 Transport layer security (TLS) protocol overview ....................... -
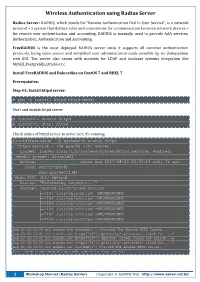
Wireless Authentication Using Radius Server
Wireless Authentication using Radius Server Radius Server: RADIUS, which stands for “Remote Authentication Dial In User Service”, is a network protocol – a system that defines rules and conventions for communication between network devices – for remote user authentication and accounting. RADIUS is normally used to provide AAA services; Authorization, Authentication and Accounting. FreeRADIUS is the most deployed RADIUS server since it supports all common authentication protocols, being open source and simplified user administration made possible by its dialupadmin web GUI. The server also comes with modules for LDAP and database systems integration like MySQL,PostgreSQL,Oracle e.t.c. Install FreeRADIUS and Daloradius on CentOS 7 and RHEL 7 Prerequisites: Step-01: Install httpd server: # yum -y install httpd httpd-devel Start and enable httpd server # systemctl enable httpd # systemctl start httpd Check status of httpd server to make sure it’s running [root@freeradius ~]# systemctl status httpd ● httpd.service - The Apache HTTP Server Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled) Active: active (running) since Sun 2017-08-20 02:33:03 EDT; 7s ago Docs: man:httpd(8) man:apachectl(8) Main PID: 7147 (httpd) Status: "Processing requests..." CGroup: /system.slice/httpd.service ├─7147 /usr/sbin/httpd -DFOREGROUND ├─7194 /usr/sbin/httpd -DFOREGROUND ├─7195 /usr/sbin/httpd -DFOREGROUND ├─7196 /usr/sbin/httpd -DFOREGROUND ├─7197 /usr/sbin/httpd -DFOREGROUND └─7199 /usr/sbin/httpd -DFOREGROUND Aug 20 02:33:00 ns1.mahedi.net systemd[1]: Starting The Apache HTTP Server... Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:01 ns1.mahedi.net httpd[7147]: AH00558: httpd: Could not reliab...e Aug 20 02:33:02 ns1.mahedi.net httpd[7147]: gethostby*.getanswer: asked for ..." Aug 20 02:33:03 ns1.mahedi.net systemd[1]: Started The Apache HTTP Server. -

Authentication, Authorization and Accounting (AAA) Protocols
Authentication, Authorization and Accounting (AAA) Protocols Agententechnologien in der Telekommunikation Sommersemester 2009 Babak Shafieian [email protected] A O T Agententechnologien in betrieblichen Anwendungen 10.06.2009 und der Telekommunikation Overview A O T Agententechnologien in der Telekommunikation - 2 TU Berlin Motivation (Why AAA?) Ö Telecommunications services are a global market worth over US$ 1.5 trillion in revenue. Home Entertainment Voice over IP (VoIP) Multimedia Conference Messaging/ Presence A O T Agententechnologien in der Telekommunikation - 3 TU Berlin Authentication (Who is [email protected]) Ö Authentication is the process of verifying user’s identity using credentials like username, password or certificates. Ö After the successful match of user’s authentication credentials with the credentials stored in the database of the service provider, the user is granted access to the network, otherwise the access is denied. A O T Agententechnologien in der Telekommunikation - 4 TU Berlin Authorization Ö Is the process of enforcing policies. It determines what types or qualities of network resources or specific services the user is permitted. Ö By using the access policy defined for a specific user, the service provider grants or rejects the access requests from the user. Ö Access policy could be applied on a per user or group basis. A O T Agententechnologien in der Telekommunikation - 5 TU Berlin Accounting Ö Is the process of keeping track of what the user is doing. Ö It includes: Amount of the time spent in the network (duration of session) Number of packets(or bytes) transmitted during a session. The accessed services during a session. -

PUF Based Authentication Protocol for Iot
S S symmetry Article PUF Based Authentication Protocol for IoT An Braeken Vrije Universiteit Brussel, Pleinlaan 2, 1050 Brussel, Belgium; [email protected]; Tel.: +32-468-104-767 Received: 11 July 2018; Accepted: 11 August 2018; Published: 20 August 2018 Abstract: Key agreement between two constrained Internet of Things (IoT) devices that have not met each other is an essential feature to provide in order to establish trust among its users. Physical Unclonable Functions (PUFs) on a device represent a low cost primitive exploiting the unique random patterns in the device and have been already applied in a multitude of applications for secure key generation and key agreement in order to avoid an attacker to take over the identity of a tampered device, whose key material has been extracted. This paper shows that the key agreement scheme of a recently proposed PUF based protocol, presented by Chatterjee et al., for Internet of Things (IoT) is vulnerable for man-in-the-middle, impersonation, and replay attacks in the Yao–Dolev security model. We propose an alternative scheme, which is able to solve these issues and can provide in addition a more efficient key agreement and subsequently a communication phase between two IoT devices connected to the same authentication server. The scheme also offers identity based authentication and repudiation, when only using elliptic curve multiplications and additions, instead of the compute intensive pairing operations. Keywords: physical unclonable function; authentication; elliptic curve cryptography; internet of things 1. Introduction Internet of Things (IoT) is experiencing worldwide growth. Not only classical computing and communication devices are connected, but also a whole range of other gadgets that are used in our daily life, such as thermostats, light switches, door locks, refrigerators, etc. -

Recommendation for EAP Methods
Archived NIST Technical Series Publication The attached publication has been archived (withdrawn), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Archived Publication Series/Number: NIST Special Publication 800-120 Title: Recommendation for EAP Methods Used in Wireless Network Access Authentication Publication Date(s): September 2009 Withdrawal Date: October 19, 2018 Withdrawal Note: This publication is out of date. Refer to relevant standards from the Internet Engineering Task Force (IETF), http://www.ietf.org/ . Superseding Publication(s) The attached publication has been superseded by the following publication(s): Series/Number: Title: Author(s): Publication Date(s): URL/DOI: Additional Information (if applicable) Contact: Computer Security Division (Information Technology Laboratory) Latest revision of the attached publication: Related information: https://csrc.nist.gov https://csrc.nist.gov/publications/detail/sp/800-120/archive/2009-09-17 Withdrawal N/A announcement (link): Date updated: October 19, 2018 NIST Special Publication 800-120 Recommendation for EAP Methods Used in Wireless Network Access Authentication Katrin Hoeper and Lily Chen Computer Security Division Information Technology Laboratory C O M P U T E R S E C U R I T Y September 2009 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Patrick Gallagher, Deputy Director Abstract This Recommendation specifies security requirements for authentication methods with key establishment supported by the Extensible Authentication Protocol (EAP) defined in IETF RFC 3748 for wireless access authentications to federal networks. KEY WORDS: EAP methods, authentication, key establishment. SP 800-120: Recommendation for EAP Methods Used in Wireless Network Access Authentication Acknowledgments The authors, Katrin Hoeper and Lily Chen, wish to thank their colleagues who reviewed drafts of this document and contributed to its technical content. -

Operations T. Dahm Internet-Draft A. Ota Intended Status: Informational Google Inc Expires: July 30, 2020 D
Operations T. Dahm Internet-Draft A. Ota Intended status: Informational Google Inc Expires: July 30, 2020 D. Medway Gash Cisco Systems, Inc. D. Carrel vIPtela, Inc. L. Grant January 27, 2020 The TACACS+ Protocol draft-ietf-opsawg-tacacs-17 Abstract This document describes the Terminal Access Controller Access-Control System Plus (TACACS+) protocol which is widely deployed today to provide Device Administration for routers, network access servers and other networked computing devices via one or more centralized servers. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at https://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on July 30, 2020. Copyright Notice Copyright (c) 2020 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust's Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents Dahm, et al. Expires July 30, 2020 [Page 1] Internet-Draft The TACACS+ Protocol January 2020 carefully, as they describe your rights and restrictions with respect to this document.