Azure Automation Microsoft Azure Essentials
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Second Edition Microsoft Azure Essentials
Fundamentals of Azure Second Edition Microsoft Azure Essentials Michael Collier Robin Shahan PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2016 by Michael Collier, Robin Shahan All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. ISBN: 978-1-5093-0296-3 Microsoft Press books are available through booksellers and distributors worldwide. If you need support related to this book, email Microsoft Press Support at [email protected]. Please tell us what you think of this book at http://aka.ms/tellpress. This book is provided “as-is” and expresses the author’s views and opinions. The views, opinions and information expressed in this book, including URL and other Internet website references, may change without notice. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. Microsoft and the trademarks listed at http://www.microsoft.com on the “Trademarks” webpage are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. Acquisitions Editor: Devon Musgrave Developmental Editor: Carol Dillingham Editorial Production: Cohesion Copyeditor: Ann Weaver Cover: Twist Creative • Seattle To my wife, Sonja, and sons, Aidan and Logan; I love you more than words can express. I could not have written this book without your immense support and patience. —Michael S. Collier I dedicate this book to the many people who helped make this the best book possible by reviewing, discussing, and sharing their technical wisdom. -

Introducing Windows Azure for IT Professionals
Introducing Windows ServerIntroducing Release 2012 R2 Preview Introducing Windows Azure For IT Professionals Mitch Tulloch with the Windows Azure Team PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2013 Microsoft Corporation All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2013949894 ISBN: 978-0-7356-8288-7 Microsoft Press books are available through booksellers and distributors worldwide. If you need support related to this book, email Microsoft Press Book Support at [email protected]. Please tell us what you think of this book at http://www.microsoft.com/learning/booksurvey. Microsoft and the trademarks listed at http://www.microsoft.com/about/legal/en/us/IntellectualProperty/ Trademarks/EN-US.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. The example companies, organizations, products, domain names, email addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, email address, logo, person, place, or event is intended or should be inferred. This book expresses the author’s views and opinions. The information contained in this book is provided without any express, statutory, or implied warranties. Neither the authors, Microsoft Corporation, nor -

Microsoft Azure Essentials Azure Machine Learning
Azure Machine Learning Microsoft Azure Essentials Jeff Barnes Visit us today at microsoftpressstore.com • Hundreds of titles available – Books, eBooks, and online resources from industry experts • Free U.S. shipping • eBooks in multiple formats – Read on your computer, tablet, mobile device, or e-reader • Print & eBook Best Value Packs • eBook Deal of the Week – Save up to 60% on featured titles • Newsletter and special offers – Be the first to hear about new releases, specials, and more • Register your book – Get additional benefits Hear about it first. Get the latest news from Microsoft Press sent to your inbox. • New and upcoming books • Special offers • Free eBooks • How-to articles Sign up today at MicrosoftPressStore.com/Newsletters Wait, there’s more... Find more great content and resources in the Microsoft Press Guided Tours app. The Microsoft Press Guided Tours app provides insightful tours by Microsoft Press authors of new and evolving Microsoft technologies. • Share text, code, illustrations, videos, and links with peers and friends • Create and manage highlights and notes • View resources and download code samples • Tag resources as favorites or to read later • Watch explanatory videos • Copy complete code listings and scripts Download from Windows Store PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2015 Microsoft Corporation. All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. ISBN: 978-0-7356-9817-8 Microsoft Press books are available through booksellers and distributors worldwide. -

NET Technology Guide for Business Applications // 1
.NET Technology Guide for Business Applications Professional Cesar de la Torre David Carmona Visit us today at microsoftpressstore.com • Hundreds of titles available – Books, eBooks, and online resources from industry experts • Free U.S. shipping • eBooks in multiple formats – Read on your computer, tablet, mobile device, or e-reader • Print & eBook Best Value Packs • eBook Deal of the Week – Save up to 60% on featured titles • Newsletter and special offers – Be the first to hear about new releases, specials, and more • Register your book – Get additional benefits Hear about it first. Get the latest news from Microsoft Press sent to your inbox. • New and upcoming books • Special offers • Free eBooks • How-to articles Sign up today at MicrosoftPressStore.com/Newsletters Wait, there’s more... Find more great content and resources in the Microsoft Press Guided Tours app. The Microsoft Press Guided Tours app provides insightful tours by Microsoft Press authors of new and evolving Microsoft technologies. • Share text, code, illustrations, videos, and links with peers and friends • Create and manage highlights and notes • View resources and download code samples • Tag resources as favorites or to read later • Watch explanatory videos • Copy complete code listings and scripts Download from Windows Store Free ebooks From technical overviews to drilldowns on special topics, get free ebooks from Microsoft Press at: www.microsoftvirtualacademy.com/ebooks Download your free ebooks in PDF, EPUB, and/or Mobi for Kindle formats. Look for other great resources at Microsoft Virtual Academy, where you can learn new skills and help advance your career with free Microsoft training delivered by experts. -

Microsoft Acquires Massive, Inc
S T A N F O R D U N I V E R S I T Y! 2 0 0 7 - 3 5 3 - 1! W W W . C A S E W I K I . O R G! R e v . M a y 2 9 , 2 0 0 7 MICROSOFT ACQUIRES MASSIVE, INC. May 4th, 2006 T A B L E O F C O N T E N T S 1. Introduction 2. Industry Overview 2.1. The Advertising Opportunity Within Video Games 2.2. Market Size and Demographics 2.3. Video Games and Advertising 2.4. Market Dynamics 3. Massive, Inc. ! Company Background 3.1. Founding of Massive 3.2. The Financing of Massive 3.3. Product Launch / Technology 3.4. The Massive / Microsoft Deal 4. Microsoft, Inc. within the Video Game Industry 4.1. Role as a Game Publisher / Developer 4.2. Acquisitions 4.3. Role as an Electronic Advertising Network 4.4. Statements Regarding the Acquisition of Massive, Inc. 5. Exhibits 5.1. Table of Exhibits 6. References ! 2 0 0 7 - 3 5 3 - 1! M i c r o s o f t A c q u i s i t i o n o f M a s s i v e , I n c .! I N T R O D U C T I O N In May 2007, Microsoft Corporation was a company in transition. Despite decades of dominance in its core markets of operating systems and desktop productivity software, Mi! crosoft was under tremendous pressure to create strongholds in new market spaces. -

MOS 2016 Study Guide for Microsoft Outlook
MOS 2016 Study Guide for Microsoft Outlook Joan E. Lambert Microsoft Office Specialist Exam 77-731 MOS 2016 Study Guide for Microsoft Outlook Editor-in-Chief Greg Wiegand Published with the authorization of Microsoft Corporation by: Pearson Education, Inc. Senior Acquisitions Editor Laura Norman Copyright © 2017 by Pearson Education, Inc. Senior Production Editor All rights reserved. Printed in the United States of America. This publication is pro- Tracey Croom tected by copyright, and permission must be obtained from the publisher prior to any prohibited reproduction, storage in a retrieval system, or transmission in any Editorial Production form or by any means, electronic, mechanical, photocopying, recording, or like- Online Training Solutions, Inc. wise. For information regarding permissions, request forms, and the appropriate (OTSI) contacts within the Pearson Education Global Rights & Permissions Department, please visit http://www.pearsoned.com/permissions. No patent liability is assumed Series Project Editor with respect to the use of the information contained herein. Although every pre- Kathy Krause (OTSI) caution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions. Nor is any liability assumed for Copy Editor/Proofreader damages resulting from the use of the information contained herein. Jaime Odell (OTSI) ISBN-13: 978-0-7356-9938-0 Indexer ISBN-10: 0-7356-9938-0 Susie Carr (OTSI) Library of Congress Control Number: 2016953082 Editorial Assistant Cindy J. Teeters First Printing November 2016 Interior Designer/Compositor Microsoft and the trademarks listed at http://www.microsoft.com on the Joan Lambert (OTSI) “Trademarks” webpage are trademarks of the Microsoft group of companies. -

Michael James Halvorson
Michael James Halvorson [email protected] https://www.plu.edu/business-economic-history-program/ (206) 327-5992 CURRENT POSITIONS Benson Family Chair in Business and Economic History, Pacific Lutheran University, Tacoma, WA, 98447 Professor of History, Department of History, Pacific Lutheran University, Tacoma, Washington, 98447 Innovation Studies Program Chair, Division of Interdisciplinary Studies, Pacific Lutheran University, Tacoma, WA, 98447 EDUCATION Ph. D. History, University of Washington, Seattle, Washington, 2001. Program focus was Early Modern Europe, with supporting fields in Early Medieval, Late Medieval, and Tudor/Stuart England. Dissertation: Theology, Ritual, and Confessionalization: The Making and Meaning of Lutheran Baptism in Reformation Germany, 1520-1618. This 400-page dissertation used Lutheran baptism as a vehicle for assessing the religious, political, and cultural values of German Lutherans during the Protestant Reformation. M.A. History, University of Washington, Seattle, Washington, 1996. Program featured coursework and study in the Late-Medieval, Renaissance, and Reformation fields. Language study and reading exams in Medieval Latin and German. B.A. Computer Science, Pacific Lutheran University, Tacoma, Washington, 1985. Program emphasized software development, mathematics, and writing. Minor in History. Core requirements satisfied through interdisciplinary Integrated Studies program (Core II). Leadership Seminar, Pacific Lutheran University, 2010-2011. A year-long (for credit) course for mid-level managers -

Microsoft SQL Server 2008 Reporting Services Step by Step Ebook
● ● ● ● ● ● ● ● ● ● ● How to access your CD files The print edition of this book includes a CD. To access the CD files, go to http://aka.ms/626478/files, and look for the Downloads tab. Note: Use a desktop web browser, as files may not be accessible from all ereader devices. Questions? Please contact: [email protected] Microsoft Press PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2009 by Stacia Misner All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2008940501 Printed and bound in the United States of America. 1 2 3 4 5 6 7 8 9 QWT 4 3 2 1 0 9 Distributed in Canada by H.B. Fenn and Company Ltd. A CIP catalogue record for this book is available from the British Library. Microsoft Press books are available through booksellers and distributors worldwide. For further infor mation about international editions, contact your local Microsoft Corporation office or contact Microsoft Press International directly at fax (425) 936-7329. Visit our Web site at www.microsoft.com/mspress. Send comments to [email protected]. Microsoft, Microsoft Press, Access, Active Directory, ActiveX, Excel, IntelliSense, Internet Explorer, MS, PerformancePoint, SharePoint, SQL Server, Visual Basic, Visual C#, Visual Studio, Windows, Windows Server, and Windows Vista are either registered trademarks or trademarks of the Microsoft group of companies. Other product and company names mentioned herein may be the trademarks of their respective owners. -

Microsoft Corporation
A Progressive Digital Media business COMPANY PROFILE Microsoft Corporation REFERENCE CODE: 8ABE78BB-0732-4ACA-A41D-3012EBB1334D PUBLICATION DATE: 25 Jul 2017 www.marketline.com COPYRIGHT MARKETLINE. THIS CONTENT IS A LICENSED PRODUCT AND IS NOT TO BE PHOTOCOPIED OR DISTRIBUTED Microsoft Corporation TABLE OF CONTENTS TABLE OF CONTENTS Company Overview ........................................................................................................3 Key Facts.........................................................................................................................3 Business Description .....................................................................................................4 History .............................................................................................................................5 Key Employees .............................................................................................................26 Key Employee Biographies .........................................................................................28 Major Products & Services ..........................................................................................35 SWOT Analysis .............................................................................................................36 Top Competitors ...........................................................................................................44 Company View ..............................................................................................................45 -

Gail Fialkov , Et Al. V. Microsoft Corporation, Et Al. 13-CV-02039
Case 2:13-cv-02039-RSM Document 52 Filed 01/24/14 Page 1 of 41 1 THE HONORABLE RICARDO S. MARTINEZ 2 3 4 5 6 7 8 UNITED STATES DISTRICT COURT 9 WESTERN DISTRICT OF WASHINGTON 10 AT SEATTLE 11 GAIL FIALKOV, Individually and on Behalf No. 2:13-cv-02039-RSM 12 of All Others Similarly Situated, CLASS ACTION 13 Plaintiff, CONSOLIDATED COMPLAINT FOR 14 vs. VIOLATIONS OF THE FEDERAL SECURITIES LAWS 15 MICROSOFT CORPORATION, et al., 16 Defendants. 17 DEMAND FOR JURY TRIAL 18 19 20 21 22 23 24 25 26 907786_1 CONSOLIDATED COMPLAINT FOR Robbins Geller Rudman & Dowd LLP II VIOLATIONS OF THE FEDERAL SECURITIES 655 West Broadway, Suite 1900, San Diego, CA 92101 Telephone: 619/231-1058 • Fax: 619/231-7423 LAWS (2:13-cv-02039-RSM) Case 2:13-cv-02039-RSM Document 52 Filed 01/24/14 Page 2 of 41 1 Lead Plaintiffs, the Seafarers Pension Plan, the Seafarers Officers and Employees Pension 2 Plan, the United Industrial Workers Pension Plan, the MCS Supplementary Pension Plan and the 3 Oklahoma Firefighters Pension and Retirement System (“Lead Plaintiffs”), on behalf of themselves 4 and all other persons similarly situated, allege the following based upon personal knowledge as to 5 themselves and their own acts, and information and belief as to all other matters, based upon, inter 6 alia, the investigation conducted by and through their attorneys. 7 NATURE OF THE ACTION 8 1. This is a federal securities class action brought against Microsoft Corporation 9 (“Microsoft” or the “Company”) and three of its senior officers for violations of the Securities 10 Exchange Act of 1934 (the “1934 Act”). -
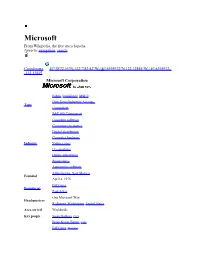
Microsoft from Wikipedia, the Free Encyclopedia Jump To: Navigation, Search
Microsoft From Wikipedia, the free encyclopedia Jump to: navigation, search Coordinates: 47°38′22.55″N 122°7′42.42″W / 47.6395972°N 122.12845°W / 47.6395972; -122.12845 Microsoft Corporation Public (NASDAQ: MSFT) Dow Jones Industrial Average Type Component S&P 500 Component Computer software Consumer electronics Digital distribution Computer hardware Industry Video games IT consulting Online advertising Retail stores Automotive software Albuquerque, New Mexico Founded April 4, 1975 Bill Gates Founder(s) Paul Allen One Microsoft Way Headquarters Redmond, Washington, United States Area served Worldwide Key people Steve Ballmer (CEO) Brian Kevin Turner (COO) Bill Gates (Chairman) Ray Ozzie (CSA) Craig Mundie (CRSO) Products See products listing Services See services listing Revenue $62.484 billion (2010) Operating income $24.098 billion (2010) Profit $18.760 billion (2010) Total assets $86.113 billion (2010) Total equity $46.175 billion (2010) Employees 89,000 (2010) Subsidiaries List of acquisitions Website microsoft.com Microsoft Corporation is an American public multinational corporation headquartered in Redmond, Washington, USA that develops, manufactures, licenses, and supports a wide range of products and services predominantly related to computing through its various product divisions. Established on April 4, 1975 to develop and sell BASIC interpreters for the Altair 8800, Microsoft rose to dominate the home computer operating system (OS) market with MS-DOS in the mid-1980s, followed by the Microsoft Windows line of OSes. Microsoft would also come to dominate the office suite market with Microsoft Office. The company has diversified in recent years into the video game industry with the Xbox and its successor, the Xbox 360 as well as into the consumer electronics market with Zune and the Windows Phone OS. -

Windows 10 Step by Step
spine = .8739” The quick way to learn Windows 10 Step by Windows 10 This is learning made easy. Get more done quickly Step with Windows 10. Jump in wherever you need answers—brisk lessons and colorful screenshots IN FULL COLOR! show you exactly what to do, step by step. Windows 10 • Discover fun and functional Windows 10 features! • Work with the new, improved Start menu and Start screen • Learn about different sign-in methods • Put the Cortana personal assistant to work for you • Manage your online reading list and annotate articles with the new browser, Microsoft Edge • Help safeguard your computer, your information, and your privacy • Manage connections to networks, devices, and storage resources Step Colorful screenshots by Step Download your Step by Step practice files at: Helpful tips and http://aka.ms/Windows10SBS/files pointers Lambert Lambert Easy numbered steps MicrosoftPressStore.com ISBN 978-0-7356-9795-9 U.S.A. $29.99 29999 Canada $36.99 [Recommended] Joan Lambert 9 780735 697959 Windows/Windows 10 Steve Lambert PRACTICE FILES Celebrating over 30 years! 9780735697959_Win10_SBS.indd 1 9/24/2015 7:29:34 AM Windows 10 Step by Step Joan Lambert Steve Lambert Win10SBS.indb 1 10/5/2015 6:33:24 PM PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2015 by Joan Lambert All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2014952811 ISBN: 978-0-7356-9795-9 Printed and bound in the United States of America.