CIS18A: Introduction to Linux/Unix CLASSROOM ATC
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fundamentals of UNIX Lab 5.4.6 – Listing Directory Information (Estimated Time: 30 Min.)
Fundamentals of UNIX Lab 5.4.6 – Listing Directory Information (Estimated time: 30 min.) Objectives: • Learn to display directory and file information • Use the ls (list files) command with various options • Display hidden files • Display files and file types • Examine and interpret the results of a long file listing • List individual directories • List directories recursively Background: In this lab, the student will use the ls command, which is used to display the contents of a directory. This command will display a listing of all files and directories within the current directory or specified directory or directories. If no pathname is given as an argument, ls will display the contents of the current directory. The ls command will list any subdirectories and files that are in the current working directory if a pathname is specified. The ls command will also default to a wide listing and display only file and directory names. There are many options that can be used with the ls command, which makes this command one of the more flexible and useful UNIX commands. Command Format: ls [-option(s)] [pathname[s]] Tools / Preparation: a) Before starting this lab, the student should review Chapter 5, Section 4 – Listing Directory Contents b) The student will need the following: 1. A login user ID, for example user2, and a password assigned by their instructor. 2. A computer running the UNIX operating system with CDE. 3. Networked computers in classroom. Notes: 1 - 5 Fundamentals UNIX 2.0—-Lab 5.4.6 Copyright 2002, Cisco Systems, Inc. Use the diagram of the sample Class File system directory tree to assist with this lab. -

Copy on Write Based File Systems Performance Analysis and Implementation
Copy On Write Based File Systems Performance Analysis And Implementation Sakis Kasampalis Kongens Lyngby 2010 IMM-MSC-2010-63 Technical University of Denmark Department Of Informatics Building 321, DK-2800 Kongens Lyngby, Denmark Phone +45 45253351, Fax +45 45882673 [email protected] www.imm.dtu.dk Abstract In this work I am focusing on Copy On Write based file systems. Copy On Write is used on modern file systems for providing (1) metadata and data consistency using transactional semantics, (2) cheap and instant backups using snapshots and clones. This thesis is divided into two main parts. The first part focuses on the design and performance of Copy On Write based file systems. Recent efforts aiming at creating a Copy On Write based file system are ZFS, Btrfs, ext3cow, Hammer, and LLFS. My work focuses only on ZFS and Btrfs, since they support the most advanced features. The main goals of ZFS and Btrfs are to offer a scalable, fault tolerant, and easy to administrate file system. I evaluate the performance and scalability of ZFS and Btrfs. The evaluation includes studying their design and testing their performance and scalability against a set of recommended file system benchmarks. Most computers are already based on multi-core and multiple processor architec- tures. Because of that, the need for using concurrent programming models has increased. Transactions can be very helpful for supporting concurrent program- ming models, which ensure that system updates are consistent. Unfortunately, the majority of operating systems and file systems either do not support trans- actions at all, or they simply do not expose them to the users. -
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

System Calls System Calls
System calls We will investigate several issues related to system calls. Read chapter 12 of the book Linux system call categories file management process management error handling note that these categories are loosely defined and much is behind included, e.g. communication. Why? 1 System calls File management system call hierarchy you may not see some topics as part of “file management”, e.g., sockets 2 System calls Process management system call hierarchy 3 System calls Error handling hierarchy 4 Error Handling Anything can fail! System calls are no exception Try to read a file that does not exist! Error number: errno every process contains a global variable errno errno is set to 0 when process is created when error occurs errno is set to a specific code associated with the error cause trying to open file that does not exist sets errno to 2 5 Error Handling error constants are defined in errno.h here are the first few of errno.h on OS X 10.6.4 #define EPERM 1 /* Operation not permitted */ #define ENOENT 2 /* No such file or directory */ #define ESRCH 3 /* No such process */ #define EINTR 4 /* Interrupted system call */ #define EIO 5 /* Input/output error */ #define ENXIO 6 /* Device not configured */ #define E2BIG 7 /* Argument list too long */ #define ENOEXEC 8 /* Exec format error */ #define EBADF 9 /* Bad file descriptor */ #define ECHILD 10 /* No child processes */ #define EDEADLK 11 /* Resource deadlock avoided */ 6 Error Handling common mistake for displaying errno from Linux errno man page: 7 Error Handling Description of the perror () system call. -

UNIX Shell Programming (15CS35) Solution Internal Assessment
UNIX Shell Programming (15CS35) Solution Internal Assessment- II November - 2016 1. Explain significance of following commands (2x5=10 M) i. cp ?????? progs Wild card ? matches any single character, hence the above command (cp) copies files whose names are six in length to progs directory ii. ls *.[xyz]* Wild card * matches any number of characters, hence the above command (ls) lists all the files having extension as either x, or y or z. iii. ls jones[0-9][0- 9][0-9] In the above command the character class[0-9] matches any digit between 0 to 9. Hence the above command lists all the files beginning with jones and having last three characters as any digit between 0 to 9. iv. echo * The above command lists all the file in the current directory. v. cp foo foo* The above command copies the file foo to file called foo*. Here the wild card * loses its meaning. 1. Write UNIX commands for the following (2 X 5= 10 M) i. Find and replace all the occurrences of unix with UNIX in the file after confirming the user. : 1,$s/unix/UNIX/gc ii. List all the files in the current directory which names are having exactly 5 characters and any number of characters in their extension. ls ?????.* iii. Copy all files stored in /home/vtu with .c, .cpp and .java extensions to progs sub- directory in current directory cp /home/vtu/*.{c,cpp,java} ./progs iv. Delete all files containing agra or agar in their file names. rm *ag[ra][ar]* v. -

Moxa Nport Real TTY Driver for Arm-Based Platform Porting Guide
Moxa NPort Real TTY Driver for Arm-based Platform Porting Guide Moxa Technical Support Team [email protected] Contents 1 Introduction ...................................................................................2 2 Porting to the Moxa UC-Series—Arm-based Computer ....................2 2.1 Build binaries on a general Arm platform ...................................................... 2 2.2 Cross-compiler and the Real TTY driver ........................................................ 3 2.3 Moxa cross-compiling interactive script......................................................... 4 2.4 Manually build the Real TTY driver with a cross-compiler ................................ 5 2.5 Deploy cross-compiled binary to target......................................................... 8 3 Porting to Raspberry Pi OS .............................................................9 4 Porting to the Yocto Project on Raspberry Pi ................................ 10 4.1 Prerequisite............................................................................................... 10 4.2 Create a Moxa layer for the Yocto Project..................................................... 11 4.3 Install a Moxa layer into the Yocto Project.................................................... 17 4.4 Deploy the Yocto image in Raspberry Pi ....................................................... 17 4.5 Start the Real TTY driver in Raspberry Pi ..................................................... 18 4.6 Set the default tty mapping to the Real TTY configuration ............................ -

Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO
Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO..........................................................................................................................................1 Martin Hinner < [email protected]>, http://martin.hinner.info............................................................1 1. Introduction..........................................................................................................................................1 2. Volumes...............................................................................................................................................1 3. DOS FAT 12/16/32, VFAT.................................................................................................................2 4. High Performance FileSystem (HPFS)................................................................................................2 5. New Technology FileSystem (NTFS).................................................................................................2 6. Extended filesystems (Ext, Ext2, Ext3)...............................................................................................2 7. Macintosh Hierarchical Filesystem − HFS..........................................................................................3 8. ISO 9660 − CD−ROM filesystem.......................................................................................................3 9. Other filesystems.................................................................................................................................3 -

Printing Printf: Formatted Printing
Printing printf: formatted printing So far we have just been copying stuff from standard-in, files, pipes, etc to the screen or another file. Say I have a file with names and phone numbers. I would like to print it out with vertically aligned columns. (so my printout is not in the same format as the input file) File contents: Desired display: Bob 4929 Bob 4929 Chuck 4882 Chuck 4882 printf is a command from the C programming language to control printing. Shell script #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a Run it alpaca.ceri.memphis.edu512:> printex.sh Hello world. This phrase contains 2 words alpaca.ceri.memphis.edu513:> #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a We need the double quotes “ . “ to define an argument (the stuff inside the quotes) for printf. #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a The argument in double quotes has - Regular text (“Hello world”, “This text contains “) - Some funny new thing - %d – a format specifier. - The already known specification for a new line - \n #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a We also have another argument, the $a, which is a shell variable, at the end. Note that the items are delimited with spaces, not commas. -
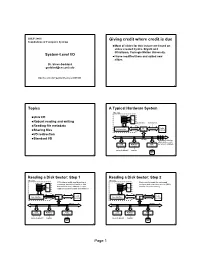
System-Level I/O I Have Modified Them and Added New Slides
JDEP 284H Giving credit where credit is due Foundations of Computer Systems Most of slides for this lecture are based on slides created by Drs. Bryant and O’Hallaron, Carnegie Mellon University. System-Level I/O I have modified them and added new slides. Dr. Steve Goddard [email protected] http://cse.unl.edu/~goddard/Courses/JDEP284 2 Topics A Typical Hardware System CPU chip register file Unix I/O ALU Robust reading and writing system bus memory bus Reading file metadata I/O main bus interface Sharing files bridge memory I/O redirection Standard I/O I/O bus Expansion slots for other devices such USB graphics disk as network adapters. controller adapter controller mouse keyboard monitor disk 3 4 Reading a Disk Sector: Step 1 Reading a Disk Sector: Step 2 CPU chip CPU chip CPU initiates a disk read by writing a Disk controller reads the sector and register file command, logical block number, and register file performs a direct memory access (DMA) destination memory address to a port transfer into main memory. ALU ALU (address) associated with disk controller. main main bus interface bus interface memory memory I/O bus I/O bus USB graphics disk USB graphics disk controller adapter controller controller adapter controller mouse keyboard monitor mouse keyboard monitor disk disk 5 6 Page 1 Reading a Disk Sector: Step 3 Unix Files CPU chip When the DMA transfer completes, the register file disk controller notifies the CPU with an A Unix file is a sequence of m bytes: interrupt (i.e., asserts a special “interrupt” B , B , ... -

System Programming Processes, Memory and Communication
System Programming Processes, memory and communication Thomas Ropars [email protected] 2021 1 The slides are available at: https://m1-mosig-os.gitlab.io/ 2 References Main references: • Advanced Programming in the Unix Environment by R. Stevens • The Linux Programming Interface by M. Kerrish • Operating Systems: Three Easy Pieces by R. Arpaci-Dusseau and A. Arpaci-Dusseau (introduction chapter) • Computer Systems: A Programmer's Perspective by R. Bryant and D. O'Hallaron The content of these lectures is inspired by: • The lecture notes of Prof. J.F. Mehaut. • The lecture notes of R. Lachaize. 3 Agenda What is an operating system? Unix File System The Shell Processes Inputs/Outputs 4 Agenda What is an operating system? Unix File System The Shell Processes Inputs/Outputs 5 Purpose of an operating system Operations run by a program: • Executing instructions • Reading/writing to memory • Reading/writing files • Accessing devices The operating system is here to make it easier to write and run programs, and to manage resources. 6 What is an operating system? Figure by R. Bryant and D. O'Hallaron The operating system is a layer of software interposed between the application program and the hardware Application programs Software Operating system Processor Main memory I/O devices Hardware Two main roles: • Virtualization • Resource management 7 Virtualization Transforms the physical resources into virtualized resources: • It hides the low-level interface of the hardware and provides higher-level abstractions: I easy to use I more general (hides the differences between different hardwares) I powerful I prevents programs from misusing the hardware It provides an API (Application Programming Interface) that allows user programs to interact with OS services: • A set of libraries • System calls 8 Resource management The OS allows several programs to run on the machine at the same time. -

Unix Commands (09/04/2014)
Unix Commands (09/04/2014) • Access control – login <login_name> – exit – passwd <login_name> – yppassswd <loginname> – su – • Login as Super user – su <login> • Login as user <login> • Root Prompt – [root@localhost ~] # • User Prompt – [bms@raxama ~] $ On Line Documentation – man <command/topic> – info <command/topic> • Working with directories – mkdir –p <subdir> ... {-p create all directories in path if not present} mkdir –p /2015/Jan/21/14 will create /2015, Jan, 21 & 14 in case any of these is absent – cd <dir> – rm -r <subdir> ... Man Pages • 1 Executable programs or shell commands • 2 System calls (functions provided by the kernel) • 3 Library calls (functions within program libraries) • 4 Special files (usually found in /dev) • 5 File formats and conventions eg /etc/passwd • 6 Games • 7 Miscellaneous (including macro packages and conventions), e.g. man(7), groff(7) • 8 System administration commands (usually only for root) • 9 Kernel routines [Non standard] – man grep, {awk,sed,find,cut,sort} – man –k mysql, man –k dhcp – man crontab ,man 5 crontab – man printf, man 3 printf – man read, man 2 read – man info Runlevels used by Fedora/RHS Refer /etc/inittab • 0 - halt (Do NOT set initdefault to this) • 1 - Single user mode • 2 - Multiuser, – without NFS (The same as 3, if you do not have networking) • 3 - Full multi user mode w/o X • 4 - unused • 5 - X11 • 6 - reboot (Do NOT set init default to this) – init 6 {Reboot System} – init 0 {Halt the System} – reboot {Requires Super User} – <ctrl> <alt> <del> • in tty[2-7] mode – tty switching • <ctrl> <alt> <F1-7> • In Fedora 10 tty1 is X. -

GNU Findutils Finding Files Version 4.8.0, 7 January 2021
GNU Findutils Finding files version 4.8.0, 7 January 2021 by David MacKenzie and James Youngman This manual documents version 4.8.0 of the GNU utilities for finding files that match certain criteria and performing various operations on them. Copyright c 1994{2021 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled \GNU Free Documentation License". i Table of Contents 1 Introduction ::::::::::::::::::::::::::::::::::::: 1 1.1 Scope :::::::::::::::::::::::::::::::::::::::::::::::::::::::::: 1 1.2 Overview ::::::::::::::::::::::::::::::::::::::::::::::::::::::: 2 2 Finding Files ::::::::::::::::::::::::::::::::::::: 4 2.1 find Expressions ::::::::::::::::::::::::::::::::::::::::::::::: 4 2.2 Name :::::::::::::::::::::::::::::::::::::::::::::::::::::::::: 4 2.2.1 Base Name Patterns ::::::::::::::::::::::::::::::::::::::: 5 2.2.2 Full Name Patterns :::::::::::::::::::::::::::::::::::::::: 5 2.2.3 Fast Full Name Search ::::::::::::::::::::::::::::::::::::: 7 2.2.4 Shell Pattern Matching :::::::::::::::::::::::::::::::::::: 8 2.3 Links ::::::::::::::::::::::::::::::::::::::::::::::::::::::::::: 8 2.3.1 Symbolic Links :::::::::::::::::::::::::::::::::::::::::::: 8 2.3.2 Hard Links ::::::::::::::::::::::::::::::::::::::::::::::: 10 2.4 Time