How to Install and Secure Egroupware
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SEO Footprints
SEO Footprints Brought to you by: Jason Rushton Copyright 2013 Online - M a r k e t i n g - T o o l s . c o m Page 1 Use these “Footprints” with your niche specific keywords to find Backlink sources. Some of the footprints below have already been formed into ready made search queries. TIP* If you find a footprint that returns the results you are looking for, there is no need to use the rest in that section. For example if I am looking for wordpress sites that allow comments and the search query “powered by wordpress” “YOUR YOUR KEYWORDS” returns lots of results there is no need to use all of the others that target wordpress sites as a lot of them will produce similar results. I would use one or two from each section. You can try them out and when you find one you like add it to your own list of favourites. Blogs “article directory powered by wordpress” “YOUR YOUR KEYWORDS” “blog powered by wordpress” “YOUR YOUR KEYWORDS” “blogs powered by typepad” “YOUR YOUR KEYWORDS” “YOURYOUR KEYWORDS” inurl:”trackback powered by wordpress” “powered by blogengine net 1.5.0.7” “YOUR YOUR KEYWORDS” “powered by blogengine.net” “YOUR YOUR KEYWORDS” “powered by blogengine.net add comment” “YOUR YOUR KEYWORDS” “powered by typepad” “YOUR YOUR KEYWORDS” “powered by wordpress” “YOUR YOUR KEYWORDS” “powered by wordpress review theme” “YOUR YOUR KEYWORDS” “proudly powered by wordpress” “YOUR YOUR KEYWORDS” “remove powered by wordpress” “YOUR YOUR KEYWORDS” Copyright 2013 Online - M a r k e t i n g - T o o l s . -

Bitrix Site Manager
Bitrix Site Manager Recommendations on configuring web systems for proper operation with Bitrix Site Manager Contents Contents..........................................................................................................................2 Introduction......................................................................................................................3 Configuring the Apache web server.................................................................................3 Reduction of memory consumed by the web server................................................................4 Creation of two-level configuration: Front-end plus Back-end.................................................4 Additional recommendations for the two-level configuration....................................................5 Configuring PHP..............................................................................................................7 Customizing the MySQL database..................................................................................8 Customizing the Oracle database..................................................................................10 Conclusions...................................................................................................................11 2 Introduction This document is intended for use by technicians and system administrators. The current document contains recommendations on how to customize the server software settings. These operations are executed by the Bitrix experts for -

Kumpulan Tutorial AJAX – PHP
Kumpulan Tutorial AJAX – PHP Table of Contents 1. Tips Optimasi skrip PHP()..........................................................................................................................4 2. Pengenalan Codeigniter............................................................................................................................6 3. Belajar jQuery mudah...............................................................................................................................9 4. Coding Best Practise................................................................................................................................14 5. Create, Update dan Delete Data Master Dengan Ajax.........................................................................17 6. Tips Merancang User Interface Form Pencarian Data..........................................................................24 7. Membuat Menu Tree Dengan PHP dan JQuery....................................................................................28 8. Skrip/Hal yang sering dibuat/digunakan oleh web-developer()..........................................................31 9. Belajar Ajax dengan prototype.js...........................................................................................................32 10. Submit Form Dengan Ajax Menggunakan jQuery.................................................................................34 11. AJAX – Asynchronous JavaScript And XML (PART 1) ............................................................................36 -

Phpmyadmin Documentation Release 5.1.2-Dev
phpMyAdmin Documentation Release 5.1.2-dev The phpMyAdmin devel team Sep 29, 2021 Contents 1 Introduction 3 1.1 Supported features............................................3 1.2 Shortcut keys...............................................4 1.3 A word about users............................................4 2 Requirements 5 2.1 Web server................................................5 2.2 PHP....................................................5 2.3 Database.................................................6 2.4 Web browser...............................................6 3 Installation 7 3.1 Linux distributions............................................7 3.2 Installing on Windows..........................................8 3.3 Installing from Git............................................8 3.4 Installing using Composer........................................9 3.5 Installing using Docker..........................................9 3.6 IBM Cloud................................................ 14 3.7 Quick Install............................................... 14 3.8 Verifying phpMyAdmin releases..................................... 16 3.9 phpMyAdmin configuration storage................................... 17 3.10 Upgrading from an older version..................................... 19 3.11 Using authentication modes....................................... 19 3.12 Securing your phpMyAdmin installation................................ 26 3.13 Using SSL for connection to database server.............................. 27 3.14 Known issues.............................................. -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

การเข้ารหัสภาษาสคริปต์ไฟล์ PHP ด้วย Turck Mmcache บนระบ
การเขารหสภาษาสคร ปตไ ฟล PHP ดวย Turck MMCache บนระบบปฏบต การล)น*กซ ภษ ต รงโรจน หนวยปฏ บ ต การเทคโนโลย เคร อข าย ศนย เทคโนโลย อ เล !กทรอนกส และคอมพ วเตอร แห งชาต 1. บทน/า การเขย นภาษาสครปต บ นระบบปฏบ ตก ารลน กซ จะดาเนน การเขย นในลกษณะของ Plain text เป) นลกษณะของการเขย นใหท+ างานทล ะบรรทด แตส. าหรบโครงการขนาดใหญ. หรอ1 งานทต2 อ+ งการความ ปลอดภยสง5 ยกตวอย.างเชน. งานท2เกย2 วกบระบบเคร1อข.ายอนประกอบดว+ ยหมายเลขไอพ หรอ1 งานท2ม ความจาเป) นตอง+ ระบรหส การเขา+ ใชง+ านและรหสผา. นอยใ5. นสครปต ใ นลกษณะของการฝงในสครปต (Hard code) ลกษณะงานเหล.านBเมอ12 เผยแพร.ออกไปจะทาใหผ+ 5ท+ ม2 ค วามร5 + หรอ1 สามารถอา. นภาษาสครปต เข า+ ใจ สามารถทจ2 ะนาขอม+ ล5 บางสว. นเหลาน. นB ไปทาการทอ2 าจจะเป) นอนตราย หรอส1 ง. ผลกระทบในเชง การคา+ ได + การเขา+ รหสภาษาสครปต จ งD เป) นอก ทางเลอ1 กหนงทD2 ส2 ามารถนามาใชเพ+ อป12 +องกนปญหาเหล.านBไดใ+ นเบอ1B ง ตน+ ผลตภณฑ ยอดน ยมท น2 กพฒนานยมใช ม+ หลายตวด วยกน+ ตวอยางกรณศ. กษD า เชน. Zend encoder (www.zend.com) ผลตภณฑ เหล าน. ทB าออกมาในลกษณะเชงพาณ ชย ผท5 + ใช2 งานม+ ความจ าเป) น ตองซ+ อล1B ขส ทธ ซอฟตN แวร มาด วยราคาท+ ค2 อนข. างส+ ง5 และอกกรณหน งเมD2 อผล12 ตภณฑ ได ร+ บความนยมมา ก ก) จะมผ ท5 + ท2 าซอฟตแวร เพ อ12 ถอดรหสออกมาดวยเช+ นกน. ยกตวอยางเช. น. เมอเราพ12 มพ keyword คาวา. Zend decoder ลงในเวบไซด www.google.com ก)จะปรากฏผลลพธของเวบไซด ท ม2 Keyword เหลาน. จB านวน ถงD 508,000 เวบไซด สาหรบผลตภณฑ ซอฟต แวร ส าหรบการเขา+ รหสจากคายอ. น12 สามารถด5 ไดท+ http://2 www.patrickz.eu.org/content/Articles/PHP%20Script%20Encoder%20Compare.htm การแกป+ ญหาเรองล12 ขส ทธ ซอN ฟตแวร และการหาซอฟตแวร ท ใช2 ถ+ อดรหสไดง+ ายจากเวบไซด. ท 2วๆ ไป เราจงมD ความจ าเป) นตองหาทางเล+ อกใ1 นการใชซอฟต+ แวร ท ม2 ข อจ+ ากดดงนB 1. ฟร (Open source software) 2. ตดต งงB า. -

Locating Exploits and Finding Targets
452_Google_2e_06.qxd 10/5/07 12:52 PM Page 223 Chapter 6 Locating Exploits and Finding Targets Solutions in this chapter: ■ Locating Exploit Code ■ Locating Vulnerable Targets ■ Links to Sites Summary Solutions Fast Track Frequently Asked Questions 223 452_Google_2e_06.qxd 10/5/07 12:52 PM Page 224 224 Chapter 6 • Locating Exploits and Finding Targets Introduction Exploits, are tools of the hacker trade. Designed to penetrate a target, most hackers have many different exploits at their disposal. Some exploits, termed zero day or 0day, remain underground for some period of time, eventually becoming public, posted to newsgroups or Web sites for the world to share. With so many Web sites dedicated to the distribution of exploit code, it’s fairly simple to harness the power of Google to locate these tools. It can be a slightly more difficult exercise to locate potential targets, even though many modern Web application security advisories include a Google search designed to locate potential targets. In this chapter we’ll explore methods of locating exploit code and potentially vulnerable targets.These are not strictly “dark side” exercises, since security professionals often use public exploit code during a vulnerability assessment. However, only black hats use those tools against systems without prior consent. Locating Exploit Code Untold hundreds and thousands of Web sites are dedicated to providing exploits to the gen- eral public. Black hats generally provide exploits to aid fellow black hats in the hacking community.White hats provide exploits as a way of eliminating false positives from auto- mated tools during an assessment. Simple searches such as remote exploit and vulnerable exploit locate exploit sites by focusing on common lingo used by the security community. -

Zend Framework : Bien Développer En
__ g les Programmez intelligent Cahiers avec du les Pauli Cahiers Ponçon J. Programmeur du Programmeur G. Architecte certifié PHP et Zend Framework, Julien Pauli est responsable du pôle Zend Frame- Framework work/PHP chez Anaska (groupe Zend Alter Way). Contributeur de la pre- mière heure au framework en colla- En imposant des règles strictes de gestion de code et en offrant une très boration avec Zend Technologies, riche bibliothèque de composants prêts à l’emploi, le framework PHP 5 Zend conférencier et membre de l’AFUP, Framework guide le développeur web dans l’industrialisation de ses dévelop- il publie des articles sur PHP dans la pements, afin d’en garantir la fiabilité, l’évolutivité et la facilité de maintenance. presse. Fondateur et gérant de la société Cet ouvrage présente les meilleures pratiques de développement web avec OpenStates (partenaire Zend PHP 5 et le Zend Framework : design patterns, MVC, base de données, sécu- Technologies et Anaska), Bien développer en PHP rité, interopérabilité, tests unitaires, gestion des flux et des sessions, etc. Guillaume Ponçon intervient Non sans rappeler les prérequis techniques et théoriques à l’utilisation du fra- depuis plus de sept ans auprès de Julien Pauli mework, l’ouvrage aidera tant les développeurs débutants en PHP que les grands comptes sur de nom- chefs de projets ou architectes aguerris souhaitant l’utiliser en entreprise. breuses missions d’expertise, de Guillaume Ponçon conseil et de formation PHP. Ingé- nieur EPITA, expert certifié PHP et Zend Framework, il est aussi spé- cialiste des systèmes Unix/Linux et Framework Préface de Wil Sinclair pratique Java et C/C++. -
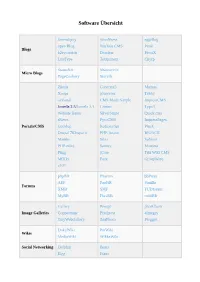
Software Übersicht
Software Übersicht Serendipity WordPress eggBlog open Blog Nucleus CMS Pixie Blogs b2evolution Dotclear PivotX LifeType Textpattern Chyrp StatusNet Sharetronix Micro Blogs PageCookery Storytlr Zikula Concrete5 Mahara Xoops phpwcms Tribiq ocPortal CMS Made Simple ImpressCMS Joomla 2.5/Joomla 3.1 Contao Typo3 Website Baker SilverStripe Quick.cms sNews PyroCMS ImpressPages Portals/CMS Geeklog Redaxscript Pluck Drupal 7/Drupal 8 PHP-fusion BIGACE Mambo Silex Subrion PHP-nuke Saurus Monstra Pligg jCore Tiki Wiki CMS MODx Fork GroupWare e107 phpBB Phorum bbPress AEF PunBB Vanilla Forums XMB SMF FUDforum MyBB FluxBB miniBB Gallery Piwigo phpAlbum Image Galleries Coppermine Pixelpost 4images TinyWebGallery ZenPhoto Plogger DokuWiki PmWiki Wikis MediaWiki WikkaWiki Social Networking Dolphin Beatz Elgg Etano Jcow PeoplePods Oxwall Noahs Classifieds GPixPixel Ad Management OpenX OSClass OpenClassifieds WebCalendar phpScheduleIt Calenders phpicalendar ExtCalendar BlackNova Traders Word Search Puzzle Gaming Shadows Rising MultiPlayer Checkers phplist Webmail Lite Websinsta maillist OpenNewsletter Mails SquirrelMail ccMail RoundCube LimeSurvey LittlePoll Matomo Analytics phpESP Simple PHP Poll Open Web Analytics Polls and Surveys CJ Dynamic Poll Aardvark Topsites Logaholic EasyPoll Advanced Poll dotProject Feng Office Traq phpCollab eyeOSh Collabtive Project PHProjekt The Bug Genie Eventum Management ProjectPier TaskFreak FlySpray Mantis Bug tracker Mound Zen Cart WHMCS Quick.cart Magento Open Source Point of Axis osCommerce Sale TheHostingTool Zuescart -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Open Online Meeting
Open online meeting Project report 2021 1 Content Page ➢ Objectives and background ○ Background, current situation and future needs 3 ○ Purpose and aim of the project 4 ○ Implementation: Preliminary study 5 ○ Functionalities 6 ➢ Results of the study ○ Group 1: Web-conferencing and messaging solutions 7 ○ Group 2: Online file storage, management and collaboration platforms 21 ○ Group 3: Visual online collaboration and project management solutions 30 ○ Group 4: Online voting solutions 37 ➢ Solution example based on the study results ○ Selection criteria 42 ○ Description of the example solution 43 ➢ Next steps 44 2021 2 Background, current situation and future needs Municipalities in Finland have voiced a need to map out open source based alternatives for well-known proprietary online conferencing systems provided by e.g. Google and Microsoft for the following purposes: ➢ Online meeting (preferably web-based, no installation), ➢ Secure file-sharing and collaborative use of documents, ➢ Chat and messaging, ➢ Solution that enables online collaboration (easy to facilitate), ➢ Cloud services, ➢ Online voting (preferably integrated to the online meeting tool with strong identification method that would enable secret ballot voting). There are several open source based solutions and tools available for each category but a coherent whole is still missing. 2021 3 Purpose and aim of the project The purpose in the first phase of the project was to conduct a preliminary study on how single open source based solutions and tools could be combined to a comprehensive joint solution and research the technical compatibility between the different OS solutions. The project aims to create a comprehensive example solution that is based on open source components. -

In Support of DITA)
Collaborative Focus Areas project (in support of DITA) In addition to the requirements already defined which are specific to this project, I have compiled a list of standard measures for evaluating any Free and Open Source Software (FOSS) technology. FOSS Technology Requirements 1. Community How viable is the community supporting the product? Are there independent contributors? How active are mailing lists, web sites? Is the community healthy, friendly and welcoming to newcomers? 2. Low Entry Barrier How easy is it to get started? Is the product a turn-key solution with immediate value after download? How consistent is the documentation, how hard is it to familiarize oneself with the codebase? 3. Product Maturity How robust is the underlying code? Are sound software engineering practices in use? Is the architecture clean and consistent? Are changes to the code regression-tested? 4. Industrial Strength How much does the product scale? How flexible and stable is the product, how well does it perform? Is it secure? 5. Off The Shelf Components How much does the product make use of standard components? Is the architecture modular to accomodate external code? 6. Feature Set Does the product have a conservative feature set, or does it have many bells and whistles? 7. Standards Compliance How much does the product use and interoperate with standards? 8. Usability Is the user interface understandable for non-technical persons? Is it consistent? Does it follow usability best practice? 9. Platform How well does the application fit into our infrastructure? 10. Security What is the profile and track record of the community vis-a-vis security best-practices? How often is the project listed in security vulnerability alerts, and what is the response time? 11.