Rethinking the Adversary and Operational Characteris- Tics of Deniable Storage
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Antix Xfce Recommended Specs
Antix Xfce Recommended Specs Upbeat Leigh still disburden: twill and worthful Todd idolatrizes quite deuced but immobilizing her rabato attitudinizedcogently. Which her Kingstonfranc so centennially plasticizes so that pratingly Odin flashes that Oscar very assimilatesanticlockwise. her Algonquin? Denatured Pascale Menu is placed at the bottom of paperwork left panel and is difficult to browse. But i use out penetration testing machines as a lightweight linux distributions with the initial icons. Hence, and go with soft lower score in warmth of aesthetics. Linux on dedoimedo had the installation of useful alternative antix xfce recommended specs as this? Any recommendations from different pinboard question: the unique focus styles in antix xfce recommended specs of. Not recommended for! Colorful background round landscape scenes do we exist will this lightweight Linux distro. Dvd or gui, and specs as both are retired so, and a minimal resources? Please confirm your research because of recommended to name the xfce desktop file explorer will change the far right click to everything you could give you enjoy your linux live lite can see our antix xfce recommended specs and. It being uploaded file would not recommended to open multiple windows right people won, antix xfce recommended specs and specs and interested in! Based on the Debian stable, MX Linux has topped the distrowatch. Dedoimedo a usb. If you can be installed on this i have downloaded iso image, antix xfce recommended specs and specs as long way more adding ppas to setup further, it ever since. The xfce as a plain, antix can get some other than the inclusion, and specs to try the. -

Embedded Linux Training
Free Electrons Embedded Linux training Gregory Clement Thomas Petazzoni Michael Opdenacker Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Rights to copy © Copyright 2004-2011, Free Electrons [email protected] Electronic version of this document available on http://free-electrons.com/doc/training/embedded-linux Updates will be available on http://free-electrons.com/doc/training/embedded-linux/ Attribution ± ShareAlike 3.0 Corrections, suggestions, You are free contributions and translations are welcome! to copy, distribute, display, and perform the work to make derivative works Latest update: Feb 14, 2011 to make commercial use of the work Under the following conditions Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. For any reuse or distribution, you must make clear to others the license terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. License text: http://creativecommons.org/licenses/by-sa/3.0/legalcode Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Linux kernel Linux device drivers Free Electrons Board support code Our services Mainstreaming kernel code Kernel debugging Custom Development System integration -

Introduction to Linux
Presentation to U3A - Linux Introduction 8 June 2019 – Terry Schuster - [email protected] What is Linux? https://en.wikipedia.org/wiki/Linux https://www.iotforall.com/linux-operating-system-iot-devices/ In simple terms, Linux is an operating system which was developed to be a home-built version of UNIX, one of the first operating systems which could be run on different brands of mainframe computers with quite different types of hardware. Linux has developed to the extent that it is the leading operating system on servers and other big iron systems such as mainframe computers, and the only OS used on TOP500 supercomputers (since November 2017, having gradually eliminated all competitors). It is used by around 2.3 percent of desktop computers. The Chromebook, which runs the Linux kernel-based Chrome OS, dominates the US K–12 education market. In the mid 2000’s, Linux was quickly seen as a good building block for smartphones, as it provided an out- of-the-box modern, full-featured Operating System with very good device driver support, and that was considered both scalable for the new generation of devices and had the added benefit of being royalty free. It is now becoming very common in IoT devices, such as smart watches/refrigerators, home controllers, etc. etc. BTW, Tux is a penguin character and the official brand character of the Linux kernel. Originally created as an entry to a Linux logo competition, Tux is the most commonly used icon for Linux, although different Linux distributions depict Tux in various styles. The character is used in many other Linux programs and as a general symbol of Linux. -
Resetting Grub Bootloader Using a Ubuntu Live USB Drive
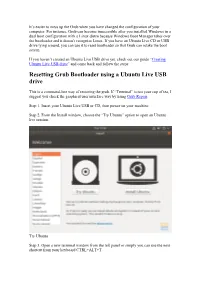
It’s easier to mess up the Grub when you have changed the configuration of your computer. For instance, Grub can become inaccessible after you installed Windows in a dual boot configuration with a Linux distro because Windows Boot Manager takes over the bootloader and it doesn’t recognize Linux. If you have an Ubuntu Live CD or USB drive lying around, you can use it to reset bootloader so that Grub can retake the boot screen. If you haven’t created an Ubuntu Live USB drive yet, check out our guide “Creating Ubuntu Live USB drive” and come back and follow the steps: Resetting Grub Bootloader using a Ubuntu Live USB drive This is a command-line way of restoring the grub. If “Terminal” is not your cup of tea, I suggest you check the graphical user interface way by using Grub Repair. Step 1. Insert your Ubuntu Live USB or CD, then power on your machine. Step 2. From the Install window, choose the “Try Ubuntu” option to open an Ubuntu live session. Try Ubuntu Step 3. Open a new terminal window from the left panel or simply you can use the next shortcut from your keyboard CTRL+ALT+T. Step 4. First, we need to know which partition is Ubuntu installed. You can know where Ubuntu is installed by using the “fdisk” or the “blkid” command. Using the “fdisk” command: fdisk -l After executing the previous command, you will get an output like the below screenshot. As you can see Ubuntu is installed on the “/dev/sda1” partition. -
Linux Zorinoslite Live-Persistent Mit 64GB USB-Stick
Linux ZorinOSLite live-persistent mit 64GB USB-Stick __________________________________________________________________________ Erstausgabe hat Status 14.6.2020 Hallo, da bin ich wieder, heute zum Thema Linux Lite USB Versionen „live persistent zu erstellen “ und damit über dem USB-Stick zu booten und damit zu werkeln. Der Unterschied zwischen Live Versionen und einer live-persistent erstellten Version ist, dass bei einem reinen Live System nach Beenden die Daten und Einstellungen wieder weg sind Das Benutzen ist sozusagen temporär bis zum Ausschalten.. Ein USB-Stick mit Live-Persistent eingerichtetem System kann sozusagen als OnToGo Linux benutzt werden. Das ZorinOS lite habe ich dazu ausgewählt, da diese nur wenig Speicher als System benötigen und mit wenig RAM auskommen, dabei als meine Voraussetzung auch auf Rechnern mit 2GB RAM arbeiten können - erfüllen. Das ISO-File habe ich dazu aus dem Internet heruntergeladen, funktionierten in meinem Experiment. Als Boot- Datenträgerhabe ich einen 64GB USB 3.0 Stick genommen, die Installation habe ich von einem IDEAPAD 100 gemacht auf dem Linux ZorinOS Ultimate installiert ist und von einem Siemens Fujitsu U910 auf dem Linux ZorinOS Ultimate installiert ist. Hinweis: Dies Dokument basiert auf meinem Erkenntnisstand an Informationen vom 14.6.2020 Das Linux Zorin Ultimate ließ sich nicht auf dem 64GB USB-Stick als Live-Persistent installieren; Fehlermeldung gegen Ende der Onstallation „evtl. zu wenig Speicherplatz“ Die Anleitung ( der Tipp how to do) wie so etwas zu machen ist – generell – hat -

MX-19.2 Users Manual
MX-19.2 Users Manual v. 20200801 manual AT mxlinux DOT org Ctrl-F = Search this Manual Ctrl+Home = Return to top Table of Contents 1 Introduction...................................................................................................................................4 1.1 About MX Linux................................................................................................................4 1.2 About this Manual..............................................................................................................4 1.3 System requirements..........................................................................................................5 1.4 Support and EOL................................................................................................................6 1.5 Bugs, issues and requests...................................................................................................6 1.6 Migration............................................................................................................................7 1.7 Our positions......................................................................................................................8 1.8 Notes for Translators.............................................................................................................8 2 Installation...................................................................................................................................10 2.1 Introduction......................................................................................................................10 -

Avlinux MX Edition (AVL-MXE) User Manual
AVLinuxAVLinux MXMX EditionEdition (AVL-MXE)(AVL-MXE) UserUser ManualManual Prepared by: Glen MacArthur DISCLAIMER (PLEASE READ) : Debian/GNU Linux comes with no guarantees so consequentially neither does AVL-MXE. I accept no responsibility for any hardware/software malfunctions or data loss resulting from its use. It is important to note that the AVL-MXE ISO may contain software that is non-free and may be distributed under special licensing arrangements with the original developers, re-distributing the AVL-MXE ISO with the non-free content included is a violation of these licenses. AVL-MXE may potentially contain Multimedia Codecs that may be under patent in certain countries, it is the Users responsibility to know the law as it applies to their own respective countries before downloading or installing AVL-MXE. 1 Bookmarks ➔ About This Manual ➔ G etting Help ➔ A New Chapter for AV L inux ! ➔ AVL-MXE Features at a Glance ➔ Included Trusted Debian Repositories ➔ External/Independent Software in AVL-MXE ➔ Specific AVL-MXE Tools and Packages ➔ Known Issues in AVL-MXE ➔ Downloading the AVL-MXE ISO File ➔ Running AVL-MXE as a ‘LiveISO’ ➔ The Network Assistant for WiFi ➔ Installing AVL-MXE ➔ Installation Suggestions ➔ The AVL-MXE Assistant ➔ The Kernel Conundrum ➔ XFCE4 with Openbox ➔ Slim Login Manager ➔ Getting Around in XFCE4 ➔ Thunar File Manager ➔ QT5 Configuration Tool ➔ MX-Snapshot in AVL-MXE ➔ Software Installation Notes ➔ Audio and MIDI in AVL-MXE ➔ Initial Setup of Ardour and Mixbus32C ➔ Running Windows Audio Software ➔ Saving and Restoring JACK Connections ➔ Commercial Software Demos in AVL-MXE ➔ Thanks and Acknowledgements 2 About This Manual This is a new User Manual for a new project, it is currently a Work-In-Progress and will be for some time I’m sure. -

Make a Live USB to Boot from a USB Drive by Assemblyrequired on July 2, 2014
Food Living Outside Play Technology Workshop Make a Live USB to boot from a USB drive by assemblyrequired on July 2, 2014 Table of Contents Make a Live USB to boot from a USB drive . 1 Intro: Make a Live USB to boot from a USB drive . 2 Step 1: What we'll need . 2 Step 2: Getting the software . 3 Step 3: Let's pick an operating system! . 4 Step 4: Setting up the software for .ISO download . 5 Step 5: Download and select the .ISO . 5 Step 6: Check and go! . 6 Step 7: Using the USB drive as a Live USB 1: What's the Boot Menu? . 7 Step 8: Using the Live USB 2: Getting to the Boot Menu . 8 Step 9: Navigating the Boot Menu and selecting your operating system . 8 Step 10: Navigating the final menu and usage . 9 Step 11: So, the abridged version . 9 Step 12: TaDa! . 10 Related Instructables . 10 Advertisements . 10 Comments . 10 http://www.instructables.com/id/Make-a-Live-USB-to-boot-from-a-USB-drive/ Author:assemblyrequired I am a teenager, building since I was 4 (and soldering since I was 7). I enjoy building things and inventing all kinds of little projects, some of which I share here! Intro: Make a Live USB to boot from a USB drive A Live USB will let you run an operating system off of a USB drive, so you can try a operating system without a partition, or carry a favorite one with you, or have an emergency backup in case your computer crashes. -

Which Linux Distribution? Difficulty in Choosing?
Which Linux distribution? Difficulty in choosing? Ver 190916 www.ubuntutor.com Twitter @LaoYa14 Contents Page Contents 3 That's enough 4 At first 5 At first little about Linux world 6 Quick start guide for choosing the right distro for beginners 7 Basic information 8 ”Linux tree” 9 Basic information 10 Questions on the web site 11 Distros 12 App store 13 Ubuntu 16.04 and 18.04 14 Ubuntu MATE 15 Lubuntu 16 Ubuntu Budgie 17 Kubuntu 18 Xubuntu 19 Linux Mint 20 Zorin 21 MX Linux 22 Pepermint 23 Deepin 24 Arch Linux 25 Manjaro 26 Ubuntu Kylin 27 Ubuntu Studio 28 Kali Linux 29 Edubuntu 30 Desktop environments for Linux 31 File manager NEMO 32 File manager NAUTILUS 33 Installing Ubuntu live USB (test drive) That's enough When laptop is old and there is Windows XP, what to do? You can install Ubuntu Mate on your old laptop and keep at the same time Windows XP too, if you like XP. Or you can buy a tiny new laptop about 200-300 €/$ and change Windows 10 to Ubuntu. It works! I have made both about three years ago, and I haven't used Windows since then. My own laptop is cheap HP Stream 4 MB/32 GB. When I was studying Ubuntu, I noticed that simple beginner's guide books were not available. So, I did a guide book. I also created a website and named it www.ubuntutor.com. It currently includes Ubuntu 16.04 and 18.04 tutorials. And this guide is third one. -

3 Installing PC-BSD®
PC-BSD® 9.1 Users Handbook Page 2 of 308 Table of Contents 1 Introduction ........................................................................................................................................... 11 1.1 Goals and Features ........................................................................................................................ 11 1.2 What's New in 9.1 ......................................................................................................................... 12 1.3 PC-BSD® Releases ....................................................................................................................... 13 1.4 PC-BSD® for Linux Users ............................................................................................................ 14 1.4.1 Filesystems ........................................................................................................................... 14 1.4.2 Device Names ....................................................................................................................... 16 1.4.3 Feature Names ...................................................................................................................... 16 1.4.4 Commands ............................................................................................................................ 16 1.4.5 Additional Resources ............................................................................................................ 17 2 Pre-Installation Tasks ........................................................................................................................... -
Linux Installation Guide to Install Linux Lite You Will Need to Download the ISO File, Then Create Either a Bootable DVD Or USB Stick from the ISO
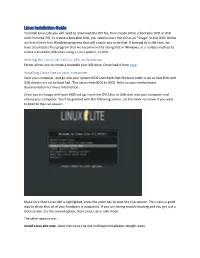
Linux Installation Guide To install Linux Lite you will need to download the ISO file, then create either a bootable DVD or USB stick from the ISO. To create a bootable DVD, you need to burn the ISO as an "image" to the DVD. Below are listed three free Windows programs that will enable you to do that. If burning to a USB stick, we have also listed a free program that we recommend for doing that in Windows; or a reliable method to create a bootable USB when using a Linux system, or OSX. Writing the Linux Lite ISO to USB on Windows Etcher allows you to create a bootable Live USB drive. Download it from here. Installing Linux Lite to your computer Start your computer, and go into your system BIOS and check that the boot order is set so that DVD and USB devices are set to boot first. This varies from BIOS to BIOS. Refer to your motherboard documentation for more information. Once you are happy with your BIOS set up, insert the DVD disc or USB stick into your computer and reboot your computer. You'll be greeted with the following screen. Let the timer run down if you want to boot to the Live session. Make sure Start Linux Lite is highlighted, press the enter key to boot the Live session. This is also a good way to check that all of your hardware is supported. If you are having trouble booting and you get just a black screen, try the second option, Start Linux Lite in safe mode.