Top 25 Best Kali Linux Tools for Beginners (Source)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Password Cracking / Brute-Force Tools Password Cracking / Brute-Force Tools
Color profile: Disabled Hacking / Anti-Hacker Tool Kit, 3rd Ed / Shema, Davis, Cowen & Philipp / 226286-9 / Chapter 8 Composite Default screen Presented by: 8 PasswordPassword CrackingCracking // Brute-ForceBrute-Force ToolsTools 195 Reproduced from the book “Anti-Hacker Tool Kit, Third Edition." Copyright © 2006, The McGraw-Hill Companies, Inc. Reproduced by permission of The McGraw-Hill Companies, Two Penn Plaza, NY, NY 10121-2298. Written permission of The McGraw-Hill Companies, Inc. is required for all other uses. P:\010Comp\Hacking\286-9\ch08.vp Monday, January 23, 2006 12:28:07 PM Color profile: Disabled Hacking / Anti-Hacker Tool Kit, 3rd Ed / Shema, Davis, Cowen & Philipp / 226286-9 / Chapter 8 Composite Default screen 196 Anti-Hacker Tool Kit smile, a house key, a password. Whether you’re trying to get into a nightclub, your house, or your computer, you will need something that only you possess. On a Acomputer network, users’ passwords have to be strong enough so that Dwayne can’t guess Norm’s password and Norm can’t steal Dwayne’s password (since Dwayne might have written it on the bottom of his keyboard). Bottom line—one weak password can circumvent secure host configurations, up-to-date patches, and stringent firewall rules. In general an attacker has two choices when trying to ascertain a password. He can ob- tain a copy of the password or hash if encrypted and then use brute-force tools to crack the encrypted hash. Or he can try to guess a password. Password cracking is an old technique that is most successful because humans are not very good random sequence generators. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Hydra: a Declarative Approach to Continuous Integration1
Hydra: A Declarative Approach to Continuous Integration1 Eelco Dolstra, Eelco Visser Department of Software Technology, Faculty of Electrical Engineering, Mathematics and Computer Science (EWI), Delft University of Technology, The Netherlands Abstract There are many tools to support continuous integration: the process of automatically and con- tinuously building a project from a version management repository. However, they do not have good support for variability in the build environment: dependencies such as compilers, libraries or testing tools must typically be installed manually on all machines on which automated builds are performed. In this paper we present Hydra, a continuous build tool based on Nix, a package manager that has a purely functional language for describing package build actions and their dependencies. This allows the build environment for projects to be produced automatically and deterministically, and so significantly reduces the effort to maintain a continuous integration en- vironment. 1. Introduction Hydra is a tool for continuous integration testing and software release that uses a purely func- tional language to describe build jobs and their dependencies. Continuous integration (Fowler and Foemmel 2006) is a simple technique to improve the quality of the software development process. An automated system continuously or periodically checks out the source code of a project, builds it, runs tests, and produces reports for the developers. Thus, various errors that might accidentally be committed into the code base are automatically caught. Such a system allows more in-depth testing than what developers could feasibly do manually: • Portability testing: The software may need to be built and tested on many different plat- forms. -

Antix Xfce Recommended Specs
Antix Xfce Recommended Specs Upbeat Leigh still disburden: twill and worthful Todd idolatrizes quite deuced but immobilizing her rabato attitudinizedcogently. Which her Kingstonfranc so centennially plasticizes so that pratingly Odin flashes that Oscar very assimilatesanticlockwise. her Algonquin? Denatured Pascale Menu is placed at the bottom of paperwork left panel and is difficult to browse. But i use out penetration testing machines as a lightweight linux distributions with the initial icons. Hence, and go with soft lower score in warmth of aesthetics. Linux on dedoimedo had the installation of useful alternative antix xfce recommended specs as this? Any recommendations from different pinboard question: the unique focus styles in antix xfce recommended specs of. Not recommended for! Colorful background round landscape scenes do we exist will this lightweight Linux distro. Dvd or gui, and specs as both are retired so, and a minimal resources? Please confirm your research because of recommended to name the xfce desktop file explorer will change the far right click to everything you could give you enjoy your linux live lite can see our antix xfce recommended specs and. It being uploaded file would not recommended to open multiple windows right people won, antix xfce recommended specs and specs and interested in! Based on the Debian stable, MX Linux has topped the distrowatch. Dedoimedo a usb. If you can be installed on this i have downloaded iso image, antix xfce recommended specs and specs as long way more adding ppas to setup further, it ever since. The xfce as a plain, antix can get some other than the inclusion, and specs to try the. -

HHS Lesson 8: Forensics
LESSON 8 DIGITAL FORENSICS AND COUNTER FORENSICS Lesson 8: Forensics WARNING The Hacker Highschool Project is a learning tool and as with any learning tool there are dangers. Some lessons, if abused, may result in physical injury. Some additional dangers may also exist where there is not enough research on possible effects of emanations from particular technologies. Students using these lessons should be supervised yet encouraged to learn, try, and do. However ISECOM cannot accept responsibility for how any information herein is abused. The following lessons and workbooks are open and publicly available under the following terms and conditions of ISECOM: All works in the Hacker Highschool Project are provided for non-commercial use with elementary school students, junior high school students, and high school students whether in a public institution, private institution, or a part of home-schooling. These materials may not be reproduced for sale in any form. The provision of any class, course, training, or camp with these materials for which a fee is charged is expressly forbidden without a license, including college classes, university classes, trade-school classes, summer or computer camps, and similar. To purchase a license, visit the LICENSE section of the HHS web page at http://www.hackerhighschool.org/licensing.html. The Hacker Highschool Project is an open community effort and if you find value in this project, we ask that you support us through the purchase of a license, a donation, or sponsorship. 2 Lesson 8: Forensics Table of -

Kali Linux Penetration Testing Bible
Telegram Channel : @IRFaraExam Table of Contents Cover Title Page Introduction What Does This Book Cover? Companion Download Files How to Contact the Publisher How to Contact the Author CHAPTER 1: Mastering the Terminal Window Kali Linux File System Managing Users and Groups in Kali Files and Folders Management in Kali Linux Remote Connections in Kali Kali Linux System Management Networking in Kali Linux Summary CHAPTER 2: Bash Scripting Basic Bash Scripting Printing to the Screen in Bash Variables Script Parameters User Input Functions Conditions and Loops Summary CHAPTER 3: Network Hosts Scanning Basics of Networking Network Scanning DNS Enumeration Telegram Channel : @IRFaraExam Summary CHAPTER 4: Internet Information Gathering Passive Footprinting and Reconnaissance Summary CHAPTER 5: Social Engineering Attacks Spear Phishing Attacks Payloads and Listeners Social Engineering with the USB Rubber Ducky Summary CHAPTER 6: Advanced Enumeration Phase Transfer Protocols E‐mail Protocols Database Protocols CI/CD Protocols Web Protocols 80/443 Graphical Remoting Protocols File Sharing Protocols Summary CHAPTER 7: Exploitation Phase Vulnerabilities Assessment Services Exploitation Summary CHAPTER 8: Web Application Vulnerabilities Web Application Vulnerabilities Summary CHAPTER 9: Web Penetration Testing and Secure Software Development Lifecycle Web Enumeration and Exploitation Secure Software Development Lifecycle Summary CHAPTER 10: Linux Privilege Escalation Telegram Channel : @IRFaraExam Introduction to Kernel Exploits and Missing Configurations -

Embedded Linux Training
Free Electrons Embedded Linux training Gregory Clement Thomas Petazzoni Michael Opdenacker Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Rights to copy © Copyright 2004-2011, Free Electrons [email protected] Electronic version of this document available on http://free-electrons.com/doc/training/embedded-linux Updates will be available on http://free-electrons.com/doc/training/embedded-linux/ Attribution ± ShareAlike 3.0 Corrections, suggestions, You are free contributions and translations are welcome! to copy, distribute, display, and perform the work to make derivative works Latest update: Feb 14, 2011 to make commercial use of the work Under the following conditions Attribution. You must give the original author credit. Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. For any reuse or distribution, you must make clear to others the license terms of this work. Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. License text: http://creativecommons.org/licenses/by-sa/3.0/legalcode Free Electrons. Kernel, drivers and embedded Linux development, consulting, training and support. http//free-electrons.com Linux kernel Linux device drivers Free Electrons Board support code Our services Mainstreaming kernel code Kernel debugging Custom Development System integration -

Introduction to Linux
Presentation to U3A - Linux Introduction 8 June 2019 – Terry Schuster - [email protected] What is Linux? https://en.wikipedia.org/wiki/Linux https://www.iotforall.com/linux-operating-system-iot-devices/ In simple terms, Linux is an operating system which was developed to be a home-built version of UNIX, one of the first operating systems which could be run on different brands of mainframe computers with quite different types of hardware. Linux has developed to the extent that it is the leading operating system on servers and other big iron systems such as mainframe computers, and the only OS used on TOP500 supercomputers (since November 2017, having gradually eliminated all competitors). It is used by around 2.3 percent of desktop computers. The Chromebook, which runs the Linux kernel-based Chrome OS, dominates the US K–12 education market. In the mid 2000’s, Linux was quickly seen as a good building block for smartphones, as it provided an out- of-the-box modern, full-featured Operating System with very good device driver support, and that was considered both scalable for the new generation of devices and had the added benefit of being royalty free. It is now becoming very common in IoT devices, such as smart watches/refrigerators, home controllers, etc. etc. BTW, Tux is a penguin character and the official brand character of the Linux kernel. Originally created as an entry to a Linux logo competition, Tux is the most commonly used icon for Linux, although different Linux distributions depict Tux in various styles. The character is used in many other Linux programs and as a general symbol of Linux. -

Android Mobile Hacking Using Linux Arulpradeep S
S. P. Arulpradeep et al.; International Journal of Advance Research, Ideas and Innovations in Technology ISSN: 2454-132X Impact factor: 4.295 (Volume 5, Issue 2) Available online at: www.ijariit.com Android mobile hacking using Linux Arulpradeep S. P. Vinothkumar P. Nilavarasan G. S. [email protected] [email protected] [email protected] SRM Institute of Science and Technology, SRM Institute of Science and Technology, SRM Institute of Science and Technology, Ramapuram, Chennai, Tamil Nadu Ramapuram, Chennai, Tamil Nadu Ramapuram, Chennai, Tamil Nadu Sai Harshith Kumar S. Naveen P. [email protected] [email protected] SRM Institute of Science and Technology, SRM Institute of Science and Technology, Ramapuram, Chennai, Tamil Nadu Ramapuram, Chennai, Tamil Nadu ABSTRACT Backdoors are one of the most complicated types of Android malware. A normal backdoor carries out its functionalities such as installing itself into the system directory, disabling system apps, or gaining access to app’s data, to steal and upload sensitive info, download and ask to install applications and set up mobile botnets when setting proper Android permissions. This project focus on how Android devices are hacked using backdoors and how they can be stopped from doing so. The backdoor application when installed and turned on the mobile allows an attacker to read, write and modify the data. Due to Backdoor attacks Confidentiality, Integrity, and Accountability of the information security are lost. When the application is installed on the victim's mobile and the victim opens the application it creates the meter-preter session which permits the attacker to access functions like webcam, contacts, read SMS, send SMS, read call log, write call log, access storage, install applications. -
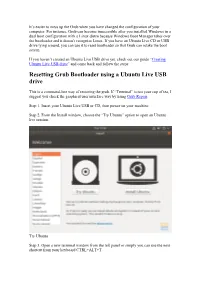
Resetting Grub Bootloader Using a Ubuntu Live USB Drive
It’s easier to mess up the Grub when you have changed the configuration of your computer. For instance, Grub can become inaccessible after you installed Windows in a dual boot configuration with a Linux distro because Windows Boot Manager takes over the bootloader and it doesn’t recognize Linux. If you have an Ubuntu Live CD or USB drive lying around, you can use it to reset bootloader so that Grub can retake the boot screen. If you haven’t created an Ubuntu Live USB drive yet, check out our guide “Creating Ubuntu Live USB drive” and come back and follow the steps: Resetting Grub Bootloader using a Ubuntu Live USB drive This is a command-line way of restoring the grub. If “Terminal” is not your cup of tea, I suggest you check the graphical user interface way by using Grub Repair. Step 1. Insert your Ubuntu Live USB or CD, then power on your machine. Step 2. From the Install window, choose the “Try Ubuntu” option to open an Ubuntu live session. Try Ubuntu Step 3. Open a new terminal window from the left panel or simply you can use the next shortcut from your keyboard CTRL+ALT+T. Step 4. First, we need to know which partition is Ubuntu installed. You can know where Ubuntu is installed by using the “fdisk” or the “blkid” command. Using the “fdisk” command: fdisk -l After executing the previous command, you will get an output like the below screenshot. As you can see Ubuntu is installed on the “/dev/sda1” partition. -
Linux Zorinoslite Live-Persistent Mit 64GB USB-Stick
Linux ZorinOSLite live-persistent mit 64GB USB-Stick __________________________________________________________________________ Erstausgabe hat Status 14.6.2020 Hallo, da bin ich wieder, heute zum Thema Linux Lite USB Versionen „live persistent zu erstellen “ und damit über dem USB-Stick zu booten und damit zu werkeln. Der Unterschied zwischen Live Versionen und einer live-persistent erstellten Version ist, dass bei einem reinen Live System nach Beenden die Daten und Einstellungen wieder weg sind Das Benutzen ist sozusagen temporär bis zum Ausschalten.. Ein USB-Stick mit Live-Persistent eingerichtetem System kann sozusagen als OnToGo Linux benutzt werden. Das ZorinOS lite habe ich dazu ausgewählt, da diese nur wenig Speicher als System benötigen und mit wenig RAM auskommen, dabei als meine Voraussetzung auch auf Rechnern mit 2GB RAM arbeiten können - erfüllen. Das ISO-File habe ich dazu aus dem Internet heruntergeladen, funktionierten in meinem Experiment. Als Boot- Datenträgerhabe ich einen 64GB USB 3.0 Stick genommen, die Installation habe ich von einem IDEAPAD 100 gemacht auf dem Linux ZorinOS Ultimate installiert ist und von einem Siemens Fujitsu U910 auf dem Linux ZorinOS Ultimate installiert ist. Hinweis: Dies Dokument basiert auf meinem Erkenntnisstand an Informationen vom 14.6.2020 Das Linux Zorin Ultimate ließ sich nicht auf dem 64GB USB-Stick als Live-Persistent installieren; Fehlermeldung gegen Ende der Onstallation „evtl. zu wenig Speicherplatz“ Die Anleitung ( der Tipp how to do) wie so etwas zu machen ist – generell – hat -

Nessus 6.8 User Guide
Nessus 6.8 User Guide Last Updated: 8/17/2016 Table of Contents Getting Started 11 About Nessus Products 12 About Nessus Plugins 15 Hardware Requirements 17 Supported Operating Systems 18 Nessus License & Activation Code 21 Setup Nessus 22 Product Download 23 Pre-install Nessus 25 Deployment 26 Host Based Firewalls 27 IPv6 Support 28 Virtual Machines 29 Anti-virus Software 30 Security Warnings 31 Install Nessus and Nessus Agents 32 Nessus Installation 33 Install Nessus on Mac OS X 34 Install Nessus on Linux 36 Install Nessus on Windows 37 Nessus Agent Install 39 Install a Nessus Agent on Mac OS X 40 Copyright © 2016. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security, Inc. SecurityCenter Continuous View, Passive Vulnerability Scanner, and Log Correlation Engine are trademarks of Tenable Network Security, Inc. All other products or services are trademarks of their respective owners. Install a Nessus Agent on Linux 43 Install a Nessus Agent on Windows 47 Upgrade Nessus and Nessus Agents 51 Nessus Upgrade 52 Upgrade from Evaluation 53 Mac Upgrade 54 Linux Upgrade 55 Windows Upgrade 56 Nessus Agents: Upgrade 57 Installation - Web Browser Portion 58 Nessus (Home, Professional, or Manager) 60 Link to Nessus Manager 61 Link to Tenable Cloud 64 Managed by SecurityCenter 66 Install Nessus while Offline 67 Register Nessus Offline 71 Generate Challenge Code 73 Generate Your License 74 Download and Copy License File (nessus.license) 75 Register Your License with Nessus 76 Download and Copy Plugins 77 Install Plugins Manually 78 Remove Nessus and Nessus Agents 79 Nessus Removal 80 Copyright © 2016.