Evaluation of Pitch Shift and Time Stretch Invariant Acoustic Fingerprint Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pitch Shifting with the Commercially Available Eventide Eclipse: Intended and Unintended Changes to the Speech Signal
JSLHR Research Note Pitch Shifting With the Commercially Available Eventide Eclipse: Intended and Unintended Changes to the Speech Signal Elizabeth S. Heller Murray,a Ashling A. Lupiani,a Katharine R. Kolin,a Roxanne K. Segina,a and Cara E. Steppa,b,c Purpose: This study details the intended and unintended 5.9% and 21.7% less than expected, based on the portion consequences of pitch shifting with the commercially of shift selected for measurement. The delay between input available Eventide Eclipse. and output signals was an average of 11.1 ms. Trials Method: Ten vocally healthy participants (M = 22.0 years; shifted +100 cents had a longer delay than trials shifted 6 cisgender females, 4 cisgender males) produced a sustained −100 or 0 cents. The first 2 formants (F1, F2) shifted in the /ɑ/, creating an input signal. This input signal was processed direction of the pitch shift, with F1 shifting 6.5% and F2 in near real time by the Eventide Eclipse to create an output shifting 6.0%. signal that was either not shifted (0 cents), shifted +100 cents, Conclusions: The Eventide Eclipse is an accurate pitch- or shifted −100 cents. Shifts occurred either throughout the shifting hardware that can be used to explore voice and entire vocalization or for a 200-ms period after vocal onset. vocal motor control. The pitch-shifting algorithm shifts all Results: Input signals were compared to output signals to frequencies, resulting in a subsequent change in F1 and F2 examine potential changes. Average pitch-shift magnitudes during pitch-shifted trials. Researchers using this device were within 1 cent of the intended pitch shift. -

3-D Audio Using Loudspeakers
3-D Audio Using Loudspeakers William G. Gardner B. S., Computer Science and Engineering, Massachusetts Institute of Technology, 1982 M. S., Media Arts and Sciences, Massachusetts Institute of Technology, 1992 Submitted to the Program in Media Arts and Sciences, School of Architecture and Planning in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy at the Massachusetts Institute of Technology September, 1997 © Massachusetts Institute of Technology, 1997. All Rights Reserved. Author Program in Media Arts and Sciences August 8, 1997 Certified by Barry L. Vercoe Professor of Media Arts and Sciences Massachusetts Institute of Technology Accepted by Stephen A. Benton Chair, Departmental Committee on Graduate Students Program in Media Arts and Sciences Massachusetts Institute of Technology 3-D Audio Using Loudspeakers William G. Gardner Submitted to the Program in Media Arts and Sciences, School of Architecture and Planning on August 8, 1997, in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy. Abstract 3-D audio systems, which can surround a listener with sounds at arbitrary locations, are an important part of immersive interfaces. A new approach is presented for implementing 3-D audio using a pair of conventional loudspeakers. The new idea is to use the tracked position of the listener’s head to optimize the acoustical presentation, and thus produce a much more realistic illusion over a larger listening area than existing loudspeaker 3-D audio systems. By using a remote head tracker, for instance based on computer vision, an immersive audio environment can be created without donning headphones or other equipment. -

Designing Empowering Vocal and Tangible Interaction
Designing Empowering Vocal and Tangible Interaction Anders-Petter Andersson Birgitta Cappelen Institute of Design Institute of Design AHO, Oslo AHO, Oslo Norway Norway [email protected] [email protected] ABSTRACT on observations in the research project RHYME for the last 2 Our voice and body are important parts of our self-experience, years and on work with families with children and adults with and our communication and relational possibilities. They severe disabilities prior to that. gradually become more important for Interaction Design due to Our approach is multidisciplinary and based on earlier studies increased development of tangible interaction and mobile of voice in resource-oriented Music and Health research and communication. In this paper we present and discuss our work the work on voice by music therapists. Further, more studies with voice and tangible interaction in our ongoing research and design methods in the fields of Tangible Interaction in project RHYME. The goal is to improve health for families, Interaction Design [10], voice recognition and generative sound adults and children with disabilities through use of synthesis in Computer Music [22, 31], and Interactive Music collaborative, musical, tangible media. We build on the use of [1] for interacting persons with layman expertise in everyday voice in Music Therapy and on a humanistic health approach. situations. Our challenge is to design vocal and tangible interactive media Our results point toward empowered participants, who that through use reduce isolation and passivity and increase interact with the vocal and tangible interactive designs [5]. empowerment for the users. We use sound recognition, Observations and interviews show increased communication generative sound synthesis, vibrations and cross-media abilities, social interaction and improved health [29]. -

Pitch-Shifting Algorithm Design and Applications in Music
DEGREE PROJECT IN ELECTRICAL ENGINEERING, SECOND CYCLE, 30 CREDITS STOCKHOLM, SWEDEN 2019 Pitch-shifting algorithm design and applications in music THÉO ROYER KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE ii Abstract Pitch-shifting lowers or increases the pitch of an audio recording. This technique has been used in recording studios since the 1960s, many Beatles tracks being produced using analog pitch-shifting effects. With the advent of the first digital pitch-shifting hardware in the 1970s, this technique became essential in music production. Nowa- days, it is massively used in popular music for pitch correction or other creative pur- poses. With the improvement of mixing and mastering processes, the recent focus in the audio industry has been placed on the high quality of pitch-shifting tools. As a consequence, current state-of-the-art literature algorithms are often outperformed by the best commercial algorithms. Unfortunately, these commercial algorithms are ”black boxes” which are very complicated to reverse engineer. In this master thesis, state-of-the-art pitch-shifting techniques found in the liter- ature are evaluated, attaching great importance to audio quality on musical signals. Time domain and frequency domain methods are studied and tested on a wide range of audio signals. Two offline implementations of the most promising algorithms are proposed with novel features. Pitch Synchronous Overlap and Add (PSOLA), a sim- ple time domain algorithm, is used to create pitch-shifting, formant-shifting, pitch correction and chorus effects on voice and monophonic signals. Phase vocoder, a more complex frequency domain algorithm, is combined with high quality spec- tral envelope estimation and harmonic-percussive separation to design a polyvalent pitch-shifting and formant-shifting algorithm. -
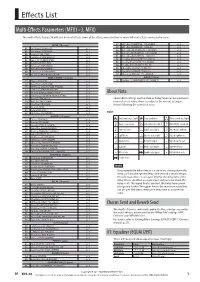
Effects List
Effects List Multi-Effects Parameters (MFX1–3, MFX) The multi-effects feature 78 different kinds of effects. Some of the effects consist of two or more different effects connected in series. 67 p. 8 FILTER (10 types) OD->Flg (OVERDRIVE"FLANGER) 68 OD->Dly (OVERDRIVE DELAY) p. 8 01 Equalizer (EQUALIZER) p. 1 " 69 Dist->Cho (DISTORTION CHORUS) p. 8 02 Spectrum (SPECTRUM) p. 2 " 70 Dist->Flg (DISTORTION FLANGER) p. 8 03 Isolator (ISOLATOR) p. 2 " 71 p. 8 04 Low Boost (LOW BOOST) p. 2 Dist->Dly (DISTORTION"DELAY) 05 Super Flt (SUPER FILTER) p. 2 72 Eh->Cho (ENHANCER"CHORUS) p. 8 06 Step Flt (STEP FILTER) p. 2 73 Eh->Flg (ENHANCER"FLANGER) p. 8 07 Enhancer (ENHANCER) p. 2 74 Eh->Dly (ENHANCER"DELAY) p. 8 08 AutoWah (AUTO WAH) p. 2 75 Cho->Dly (CHORUS"DELAY) p. 9 09 Humanizer (HUMANIZER) p. 2 76 Flg->Dly (FLANGER"DELAY) p. 9 10 Sp Sim (SPEAKER SIMULATOR) p. 2 77 Cho->Flg (CHORUS"FLANGER) p. 9 MODULATION (12 types) PIANO (1 type) 11 Phaser (PHASER) p. 3 78 SymReso (SYMPATHETIC RESONANCE) p. 9 12 Step Ph (STEP PHASER) p. 3 13 MltPhaser (MULTI STAGE PHASER) p. 3 14 InfPhaser (INFINITE PHASER) p. 3 15 Ring Mod (RING MODULATOR) p. 3 About Note 16 Step Ring (STEP RING MODULATOR) p. 3 17 Tremolo (TREMOLO) p. 3 Some effect settings (such as Rate or Delay Time) can be specified in 18 Auto Pan (AUTO PAN) p. 3 terms of a note value. The note value for the current setting is 19 Step Pan (STEP PAN) p. -

MS-100BT Effects List
Effect Types and Parameters © 2012 ZOOM CORPORATION Copying or reproduction of this document in whole or in part without permission is prohibited. Effect Types and Parameters Parameter Parameter range Effect type Effect explanation Flanger This is a jet sound like an ADA Flanger. Knob1 Knob2 Knob3 Depth 0–100 Rate 0–50 Reso -10–10 Page01 Sets the depth of the modulation. Sets the speed of the modulation. Adjusts the intensity of the modulation resonance. PreD 0–50 Mix 0–100 Level 0–150 Page02 Adjusts the amount of effected sound Sets pre-delay time of effect sound. Adjusts the output level. that is mixed with the original sound. Effect screen Parameter explanation Tempo synchronization possible icon Effect Types and Parameters [DYN/FLTR] Comp This compressor in the style of the MXR Dyna Comp. Knob1 Knob2 Knob3 Sense 0–10 Tone 0–10 Level 0–150 Page01 Adjusts the compressor sensitivity. Adjusts the tone. Adjusts the output level. ATTCK Slow, Fast Page02 Sets compressor attack speed to Fast or Slow. RackComp This compressor allows more detailed adjustment than Comp. Knob1 Knob2 Knob3 THRSH 0–50 Ratio 1–10 Level 0–150 Page01 Sets the level that activates the Adjusts the compression ratio. Adjusts the output level. compressor. ATTCK 1–10 Page02 Adjusts the compressor attack rate. M Comp This compressor provides a more natural sound. Knob1 Knob2 Knob3 THRSH 0–50 Ratio 1–10 Level 0–150 Page01 Sets the level that activates the Adjusts the compression ratio. Adjusts the output level. compressor. ATTCK 1–10 Page02 Adjusts the compressor attack rate. -

Timbretron:Awavenet(Cyclegan(Cqt(Audio))) Pipeline for Musical Timbre Transfer
Published as a conference paper at ICLR 2019 TIMBRETRON:AWAVENET(CYCLEGAN(CQT(AUDIO))) PIPELINE FOR MUSICAL TIMBRE TRANSFER Sicong Huang1;2, Qiyang Li1;2, Cem Anil1;2, Xuchan Bao1;2, Sageev Oore2;3, Roger B. Grosse1;2 University of Toronto1, Vector Institute2, Dalhousie University3 ABSTRACT In this work, we address the problem of musical timbre transfer, where the goal is to manipulate the timbre of a sound sample from one instrument to match another instrument while preserving other musical content, such as pitch, rhythm, and loudness. In principle, one could apply image-based style transfer techniques to a time-frequency representation of an audio signal, but this depends on having a representation that allows independent manipulation of timbre as well as high- quality waveform generation. We introduce TimbreTron, a method for musical timbre transfer which applies “image” domain style transfer to a time-frequency representation of the audio signal, and then produces a high-quality waveform using a conditional WaveNet synthesizer. We show that the Constant Q Transform (CQT) representation is particularly well-suited to convolutional architectures due to its approximate pitch equivariance. Based on human perceptual evaluations, we confirmed that TimbreTron recognizably transferred the timbre while otherwise preserving the musical content, for both monophonic and polyphonic samples. We made an accompanying demo video 1 which we strongly encourage you to watch before reading the paper. 1 INTRODUCTION Timbre is a perceptual characteristic that distinguishes one musical instrument from another playing the same note with the same intensity and duration. Modeling timbre is very hard, and it has been referred to as “the psychoacoustician’s multidimensional waste-basket category for everything that cannot be labeled pitch or loudness”2. -

Audio Plug-Ins Guide Version 9.0 Legal Notices This Guide Is Copyrighted ©2010 by Avid Technology, Inc., (Hereafter “Avid”), with All Rights Reserved
Audio Plug-Ins Guide Version 9.0 Legal Notices This guide is copyrighted ©2010 by Avid Technology, Inc., (hereafter “Avid”), with all rights reserved. Under copyright laws, this guide may not be duplicated in whole or in part without the written consent of Avid. 003, 96 I/O, 96i I/O, 192 Digital I/O, 192 I/O, 888|24 I/O, 882|20 I/O, 1622 I/O, 24-Bit ADAT Bridge I/O, AudioSuite, Avid, Avid DNA, Avid Mojo, Avid Unity, Avid Unity ISIS, Avid Xpress, AVoption, Axiom, Beat Detective, Bomb Factory, Bruno, C|24, Command|8, Control|24, D-Command, D-Control, D-Fi, D-fx, D-Show, D-Verb, DAE, Digi 002, DigiBase, DigiDelivery, Digidesign, Digidesign Audio Engine, Digidesign Intelligent Noise Reduction, Digidesign TDM Bus, DigiDrive, DigiRack, DigiTest, DigiTranslator, DINR, DV Toolkit, EditPack, Eleven, EUCON, HD Core, HD Process, Hybrid, Impact, Interplay, LoFi, M-Audio, MachineControl, Maxim, Mbox, MediaComposer, MIDI I/O, MIX, MultiShell, Nitris, OMF, OMF Interchange, PRE, ProControl, Pro Tools M-Powered, Pro Tools, Pro Tools|HD, Pro Tools LE, QuickPunch, Recti-Fi, Reel Tape, Reso, Reverb One, ReVibe, RTAS, Sibelius, Smack!, SoundReplacer, Sound Designer II, Strike, Structure, SYNC HD, SYNC I/O, Synchronic, TL Aggro, TL AutoPan, TL Drum Rehab, TL Everyphase, TL Fauxlder, TL In Tune, TL MasterMeter, TL Metro, TL Space, TL Utilities, Transfuser, Trillium Lane Labs, Vari-Fi, Velvet, X-Form, and XMON are trademarks or registered trademarks of Avid Technology, Inc. Xpand! is Registered in the U.S. Patent and Trademark Office. All other trademarks are the property of their respective owners. -

Universal and Non-Universal Features of Musical Pitch Perception Revealed by Singing
Article Universal and Non-universal Features of Musical Pitch Perception Revealed by Singing Highlights Authors d Pitch perception was probed cross-culturally with sung Nori Jacoby, Eduardo A. Undurraga, reproduction of tone sequences Malinda J. McPherson, Joaquı´n Valdes, Toma´ s Ossando´ n, d Mental scaling of pitch was approximately logarithmic for US Josh H. McDermott and Amazonian listeners Correspondence d Pitch perception deteriorated similarly in both groups for very high-frequency tones [email protected] (N.J.), [email protected] (J.H.M.) d Sung correlates of octave equivalence varied across cultures and musical expertise In Brief Jacoby et al. use sung reproduction of tones to explore pitch perception cross- culturally. US and native Amazonian listeners exhibit deterioration of pitch at high frequencies and logarithmic mental scaling of pitch. However, sung correlates of octave equivalence are undetectable in Amazonians, suggesting effects of culture-specific experience. Jacoby et al., 2019, Current Biology 29, 3229–3243 October 7, 2019 ª 2019 Elsevier Ltd. https://doi.org/10.1016/j.cub.2019.08.020 Current Biology Article Universal and Non-universal Features of Musical Pitch Perception Revealed by Singing Nori Jacoby,1,2,9,* Eduardo A. Undurraga,3,4 Malinda J. McPherson,5,6 Joaquı´n Valdes, 7 Toma´ s Ossando´ n,7 and Josh H. McDermott5,6,8,* 1Computational Auditory Perception Group, Max Planck Institute for Empirical Aesthetics, Frankfurt 60322, Germany 2The Center for Science and Society, Columbia University, New York, NY 10027, -

Music Technology Grade 6
MUSIC TECHNOLOGY GRADE 6 THE EWING PUBLIC SCHOOLS 2099 Pennington Road Ewing, NJ 08618 Revision Date: February 25, 2019__ Michael Nitti Written by: Music Teachers Superintendent In accordance with The Ewing Public Schools’ Policy 2230, Course Guides, this curriculum has been reviewed and found to be in compliance with all policies and all affirmative action criteria. Table of Contents Page Preface 3 21st Century Life and Careers 4 Scope of Essential Learning: Unit 1: Introduction to Music Technology (9 Class Sessions) 5 Unit 2: Acoustics: The Science of Sound (5 Class Sessions) 9 Unit 3: Sound Engineering (12 Class Sessions) 13 Unit 4: The Technology of Music (9 Class Sessions) 16 Unit 5: Final Project Creation (10 Class Sessions) 20 Sample 21st Century, Career, & Technology Integration 23 Preface The purpose of all music courses in The Ewing Public Schools is to develop comprehensive musicianship with a focus on musical literacy. As music educators, we believe all students are musical by nature and have a tremendous potential to learn and enjoy music. While research shows that music helps students to develop higher-order skills and increases desire to learn, our driving goal is to help students become more enlightened and truly alive through a balanced, comprehensive and sequential program of study. The Middle School General Music program allows students to transfer prior knowledge and skills and to explore and develop their musicianship through various units of study. The Music Technology class is a semester-long course offered to 6th graders, every other day for 41 minutes. 3 21st Century Life and Careers In today's global economy, students need to be lifelong learners who have the knowledge and skills to adapt to an evolving workplace and world. -

A Polyphonic Pitch Tracking Embedded System for Rapid Instrument Augmentation
A polyphonic pitch tracking embedded system for rapid instrument augmentation Rodrigo Schramm Federico Visi Department of Music Institute of Systematic Musicology Universidade Federal do Rio Universität Hamburg / Grande do Sul / Brazil Germany [email protected] [email protected] André Brasil Marcelo Johann Department of Music Institute of Informatics Universidade Federal do Rio Universidade Federal do Rio Grande do Sul / Brazil Grande do Sul / Brazil [email protected] [email protected] ABSTRACT (e.g. instrument shape, modes of interaction, aesthetic, This paper presents a system for easily augmenting poly- etc.) while others are extended. The augmentation may phonic pitched instruments. The entire system is designed focus on the interaction between the performer and the in- to run on a low-cost embedded computer, suitable for live strument, on how sound is generated, or both. performance and easy to customise for different use cases. Many hardware devices such as tiny computers, micro- The core of the system implements real-time spectrum fac- controllers, and a variety of sensors and transducers have torisation, decomposing polyphonic audio input signals into become more accessible. In addition, plenty of software music note activations. New instruments can be easily added and source libraries to process and generate sounds [12] are to the system with the help of custom spectral template freely available. All these resources create a powerful toolset dictionaries. Instrument augmentation is achieved by re- for building DMIs. placing or mixing the instrument's original sounds with a Instrument makers can manipulate audio with the aid of large variety of synthetic or sampled sounds, which follow many digital signal processing algorithms and libraries [15, the polyphonic pitch activations. -

Timbre-Induced Pitch Deviations of Musical Sounds
journal of interdisciplinary music studies spring 2007, volume 1, issue 1, art. #071102, pp. 33-50 Timbre-Induced Pitch Deviations of Musical Sounds Müzik Seslerinde Tını Kaynaklı Ses Perdesi Sapmaları Allan Vurma1 and Jaan Ross2 1Estonian Academy of Music and Theatre 2University of Tartu and Estonian Academy of Music and Theatre Abstract. This article deals with timbre- Özet. Bu makale müzisyenlerin günlük ça- induced pitch deviations and their magnitude lıma ortamlarına benzer biçimde tasarlanmı in environments designed to resemble those ortamlarda tını kaynaklı ses perdesi sapma- that performing musicians encounter in their larını ve bu sapmaların büyüklüklerini konu daily practice. Two experiments were con- alır. ki deney gerçekletirilmitir. Birinci de- ducted. In the first experiment classically neyde klasik eitim almı arkıcılar kendi trained singers matched the pitch of synthe- seslerini sentezlenmi piyano ve obua ses- sized sounds of the piano and oboe. The fun- lerinin ses perdeleriyle eletirmitir. Vokal damental frequency of vocal sounds was on seslerin temel frekansları çalgı seslerinin temel average 7 to 13 cents lower than the funda- frekanslarından ortalama 7-13 cent daha mental frequency of the instrumental sounds. altında gözlenmitir. Bu fark piano tınısıyla The difference was more pronounced in the yapılan deneyde daha belirgin çıkmıtır. kinci case of the piano timbre. In the second ex- deneyde katılımcılar birinci deneydeki tek bir periment, participants compared sounds pro- arkıcının ses perdesi eleme görevinde üret- duced by a single performer from the pitch- tii sesleri sentezlenmi piano ve obua sesleri matching task of the first experiment to syn- ile karılatırmıtır. Katılımcıların, çalgı ses- thesized piano and oboe sounds.