International Comparison of Bank Fraud Reimbursement: Customer Perceptions and Contractual Terms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

International Comparison of Bank Fraud
Journal of Cybersecurity, 3(2), 2017, 109–125 doi: 10.1093/cybsec/tyx011 Research paper Research paper International comparison of bank fraud reimbursement: customer perceptions and contractual terms Ingolf Becker,1,* Alice Hutchings,2 Ruba Abu-Salma,1 Ross Anderson,2 Nicholas Bohm,3 Steven J. Murdoch,1 M. Angela Sasse,1 and Gianluca Stringhini1 1Computer Science Department, University College London, Gower Street, London WC1E 6BT; 2 University of Cambridge Computer Laboratory, 15 JJ Thomson Avenue, CB3 0FD; 3Foundation for Information Policy Research *Corresponding author: E-mail: [email protected] Received 7 May 2017; accepted 17 November 2017 Abstract The study presented in this article investigated to what extent bank customers understand the terms and conditions (T&Cs) they have signed up to. If many customers are not able to understand T&Cs and the behaviours they are expected to comply with, they risk not being compensated when their accounts are breached. An expert analysis of 30 bank contracts across 25 countries found that most contract terms were too vague for customers to infer required behaviour. In some cases the rules vary for different products, meaning the advice can be contradictory at worst. While many banks allow customers to write Personal identification numbers (PINs) down (as long as they are disguised and not kept with the card), 20% of banks categorically forbid writing PINs down, and a handful stipulate that the customer have a unique PIN for each account. We tested our findings in a survey with 151 participants in Germany, the USA and UK. They mostly agree: only 35% fully understand the T&Cs, and 28% find important sections are unclear. -

Palestinian Forces
Center for Strategic and International Studies Arleigh A. Burke Chair in Strategy 1800 K Street, N.W. • Suite 400 • Washington, DC 20006 Phone: 1 (202) 775 -3270 • Fax : 1 (202) 457 -8746 Email: [email protected] Palestinian Forces Palestinian Authority and Militant Forces Anthony H. Cordesman Center for Strategic and International Studies [email protected] Rough Working Draft: Revised February 9, 2006 Copyright, Anthony H. Cordesman, all rights reserved. May not be reproduced, referenced, quote d, or excerpted without the written permission of the author. Cordesman: Palestinian Forces 2/9/06 Page 2 ROUGH WORKING DRAFT: REVISED FEBRUARY 9, 2006 ................................ ................................ ............ 1 THE MILITARY FORCES OF PALESTINE ................................ ................................ ................................ .......... 2 THE OSLO ACCORDS AND THE NEW ISRAELI -PALESTINIAN WAR ................................ ................................ .............. 3 THE DEATH OF ARAFAT AND THE VICTORY OF HAMAS : REDEFINING PALESTINIAN POLITICS AND THE ARAB - ISRAELI MILITARY BALANCE ................................ ................................ ................................ ................................ .... 4 THE CHANGING STRUCTURE OF PALESTINIAN AUTHORITY FORC ES ................................ ................................ .......... 5 Palestinian Authority Forces During the Peace Process ................................ ................................ ..................... 6 The -

The Arab-Israeli Conflict and Civil Litigation Against Terrorism
SCHUPACK IN FINAL 9/8/2010 11:38:51 AM THE ARAB-ISRAELI CONFLICT AND CIVIL LITIGATION AGAINST TERRORISM ADAM N. SCHUPACK† ABSTRACT The Arab-Israeli conflict has been a testing ground for the involvement of U.S. courts in foreign conflicts and for the concept of civil litigation against terrorists. Plaintiffs on both sides of the dispute have sought to recover damages in U.S. courts, embroiling the courts in one of the world’s most contentious political disputes. Plaintiffs bringing claims against the Palestine Liberation Organization, the Palestinian Authority, material supporters of terrorism, and the Islamic Republic of Iran have been aided by congressional statutes passed precisely to enhance their ability to bring such lawsuits, whereas plaintiffs bringing suit against Israel or Israeli leaders have not had the benefit of such laws. Although the courts have sought to give effect to the congressional authorization embodied in these statutes, they have faced the resistance—at times half-hearted—of the executive branch, which regards such legislative and judicial involvement as an intrusion on its foreign policy prerogatives. Though these lawsuits have been subject to criticism and have not fully achieved the goals attributed to them, U.S. courts have largely acted within the authority given them by Congress and the executive branch in hearing the suits, and there is at least some evidence that such lawsuits constitute an effective tool in the fight against terrorism. INTRODUCTION Alisa Flatow, a twenty-year-old Brandeis University student studying in Israel, was killed on April 9, 1995, when Palestinian Copyright © 2010 Adam N. -
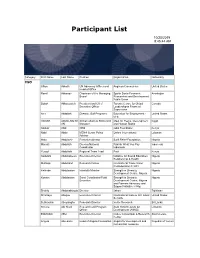
Participant List
Participant List 10/20/2019 8:45:44 AM Category First Name Last Name Position Organization Nationality CSO Jillian Abballe UN Advocacy Officer and Anglican Communion United States Head of Office Ramil Abbasov Chariman of the Managing Spektr Socio-Economic Azerbaijan Board Researches and Development Public Union Babak Abbaszadeh President and Chief Toronto Centre for Global Canada Executive Officer Leadership in Financial Supervision Amr Abdallah Director, Gulf Programs Educaiton for Employment - United States EFE HAGAR ABDELRAHM African affairs & SDGs Unit Maat for Peace, Development Egypt AN Manager and Human Rights Abukar Abdi CEO Juba Foundation Kenya Nabil Abdo MENA Senior Policy Oxfam International Lebanon Advisor Mala Abdulaziz Executive director Swift Relief Foundation Nigeria Maryati Abdullah Director/National Publish What You Pay Indonesia Coordinator Indonesia Yussuf Abdullahi Regional Team Lead Pact Kenya Abdulahi Abdulraheem Executive Director Initiative for Sound Education Nigeria Relationship & Health Muttaqa Abdulra'uf Research Fellow International Trade Union Nigeria Confederation (ITUC) Kehinde Abdulsalam Interfaith Minister Strength in Diversity Nigeria Development Centre, Nigeria Kassim Abdulsalam Zonal Coordinator/Field Strength in Diversity Nigeria Executive Development Centre, Nigeria and Farmers Advocacy and Support Initiative in Nig Shahlo Abdunabizoda Director Jahon Tajikistan Shontaye Abegaz Executive Director International Insitute for Human United States Security Subhashini Abeysinghe Research Director Verite -

Monthly Banking Statistics
Monthly Banking Statistics March 2018 (released 30 April 2018) Copyright © Australian Prudential Regulation Authority (APRA) This work is licensed under the Creative Commons Attribution 3.0 Australia Licence (CCBY 3.0). This licence allows you to copy, distribute and adapt this work, provided you attribute the work and do not suggest that APRA endorses you or your work. To view a full copy of the terms of this licence, visit: http://creativecommons.org/licenses/by/3.0/au/ Disclaimer While APRA endeavours to ensure the quality of this Publication, APRA does not accept any responsibility for the accuracy, completeness or currency of the material included in this Publication, and will not be liable for any loss or damage arising out of any use of, or reliance on, this Publication. Forthcoming issues This publication will be released on the APRA website by close of business on the last business day (within NSW) of every month. The data to be released will be for the previous calendar month. Notation Amounts are expressed in millions of Australian dollars. Both the Australian-dollar denominated transactions and the Australian-dollar equivalent of foreign-currency denominated transactions are included. The symbol ‘—‘ indicates a value of zero. Values less than half a million dollars are rounded to '0'. Explanatory notes A set of explanatory notes is provided at the end of the publication to assist the reader in understanding the source and definitions of the data. In particular, these notes help explain differences between the data presented and information publicly released by banks in their financial statements and profit announcements. -

Banking Automation Bulletin | Media Pack 2021
Banking Automation BULLETIN Media Pack 2021 Reaching and staying in touch with your commercial targets is more important than ever Curated news, opinions and intelligence on Editorial overview banking and cash automation, self-service and digital banking, cards and payments since 1979 Banking Automation Bulletin is a subscription newsletter Independent and authoritative insights from focused on key issues in banking and cash automation, industry experts, including proprietary global self-service and digital banking, cards and payments. research by RBR The Bulletin is published monthly by RBR and draws 4,000 named subscribers of digital and printed extensively on the firm’s proprietary industry research. editions with total, monthly readership of 12,000 The Bulletin is valued by its readership for providing independent and insightful news, opinions and 88% of readership are senior decision makers information on issues of core interest. representing more than 1,000 banks across 106 countries worldwide Regular topics covered by the Bulletin include: Strong social media presence through focused LinkedIn discussion group with 8,500+ members • Artificial intelligence and machine learning and Twitter @RBRLondon • Biometric authentication 12 issues per year with bonus distribution at key • Blockchain and cryptocurrency industry events around the world • Branch and digital transformation Unique opportunity to reach high-quality • Cash usage and automation readership via impactful adverts and advertorials • Deposit automation and recycling • Digital banking and payments Who should advertise? • Financial inclusion and accessibility • Fintech innovation Banking Automation Bulletin is a unique and powerful • IP video and behavioural analytics advertising medium for organisations providing • Logical, cyber and physical bank security solutions to retail banks. -

Bank of England List of Banks- August 2020
LIST OF BANKS AS COMPILED BY THE BANK OF ENGLAND AS AT 1st August 2020 (Amendments to the List of Banks since 30th June 2020 can be found below) Banks incorporated in the United Kingdom ABC International Bank Plc DB UK Bank Limited Access Bank UK Limited, The ADIB (UK) Ltd EFG Private Bank Limited Ahli United Bank (UK) PLC Europe Arab Bank plc AIB Group (UK) Plc Al Rayan Bank PLC FBN Bank (UK) Ltd Aldermore Bank Plc FCE Bank Plc Alliance Trust Savings Limited FCMB Bank (UK) Limited Allica Bank Ltd Alpha Bank London Limited Gatehouse Bank Plc Arbuthnot Latham & Co Limited Ghana International Bank Plc Atom Bank PLC GH Bank Limited Axis Bank UK Limited Goldman Sachs International Bank Guaranty Trust Bank (UK) Limited Bank and Clients PLC Gulf International Bank (UK) Limited Bank Leumi (UK) plc Bank Mandiri (Europe) Limited Habib Bank Zurich Plc Bank Of Baroda (UK) Limited Hampden & Co Plc Bank of Beirut (UK) Ltd Hampshire Trust Bank Plc Bank of Ceylon (UK) Ltd Handelsbanken PLC Bank of China (UK) Ltd Havin Bank Ltd Bank of Ireland (UK) Plc HBL Bank UK Limited Bank of London and The Middle East plc HSBC Bank Plc Bank of New York Mellon (International) Limited, The HSBC Private Bank (UK) Limited Bank of Scotland plc HSBC Trust Company (UK) Ltd Bank of the Philippine Islands (Europe) PLC HSBC UK Bank Plc Bank Saderat Plc Bank Sepah International Plc ICBC (London) plc Barclays Bank Plc ICBC Standard Bank Plc Barclays Bank UK PLC ICICI Bank UK Plc BFC Bank Limited Investec Bank PLC Bira Bank Limited Itau BBA International PLC BMCE Bank International plc British Arab Commercial Bank Plc JN Bank UK Ltd Brown Shipley & Co Limited J.P. -

Supporting Growth and Development in the Australian Community
Supporting Growth and Development in the Australian Community. Annual Report 2015 Arab Bank Australia Limited and its controlled entities Chairman’s Report Mr Geoffrey C E Wild AM In 2016 we reach our thirty year milestone of providing exceptional relationship banking to the Australian community in our key focus areas of Western Sydney and Metropolitan Melbourne. We are proud to be a member of a well regarded global group and remain true to our heritage, well capitalised and highly liquid. We consistently give back to the communities we serve and are welcoming the opportunity to partner with our existing and future customers as they maximise the opportunities from federal and state government investment in our key geographical areas. The encouraging growth in the portfolio in 2015 and the high quality of our lending book are supporting the continuous improvement in our fi nancial performance. We are proud of the gender and ethnic diversity of our team members. Collectively we have 49.6% male to 50.4% female team members with a good proportion of female representation across all tiers of the organisation. I would like thank everyone at Arab Bank Australia for their continued efforts and our loyal and growing customer base for their continued support. Geoffrey C E Wild AM Chairman 2 Arab Bank Australia Limited and its controlled entities Managing Director’s Report Mr Joseph Rizk OAM This year we are celebrating over 30 years of providing Arab Bank Australia Limited exceptional service to our customers in Australia. Over this Business Overview time we are proud to have built and maintained a strong affi nity with our community and the areas in which they Business Development choose to work and live. -

Arab Bank Investor Relations Presentation March 2021
Arab Bank Group Investor Presentation March 2021 1 Arab Bank Group – Table of contents 3 Introduction 7 Group Strategy and Business Model 12 Financial Performance 16 Governance and Sustainability 18 Financial Statements, Ratings 2 Arab Bank Group Vision Trusted banking partner for the MENA region, with the capital strength to deliver long term value to our customers and shareholders Our Identity Pioneer in the MENA banking industry with deep regional knowledge developed over 90 years Largest regional platform with global footprint - over 600 branches in 28 countries Our business is corporate & consumer banking and trade finance Our reputation is one of competence, trustworthiness and resilience Committed to the region and the founding principle – economic development of the Arab World Strengths Solid & consistent Growth Agenda Driving Efficiency performance • Strong operating performance • Largest Arab banking network • Leverage regional and global & high quality earnings • Large and diversified customer network • Robust and high quality deposit base • Implement digitisation strategy capitalization • Leading product offering • Fintech Investments • High liquidity levels delivered through digital • Robust compliance and risk channels management 3 Rich legacy of expansion and consistent performance Algeria Bahrain Syria Lebanon Europe Morocco USA Employees Egypt Turkey Switzerland Far East Saudi Arabia UAE Sudan 10,000+ Countries 1930 1940 1950 1960 1970 1980 1990 2000 28 UK Palestine Qatar Yemen Australia Jordan Tunisia Branches Oman 600+ The largest private bank international network serving the MENA region Subsidiaries Europe Arab Bank (100% Arab Bank Australia (100%) Major Associates Islamic Int’l AB - Jordan (100%) Arab National Bank-KSA (40%) Arab National Leasing Co. (100%) Oman Arab Bank (49%) * AB Invest – Jordan (100%) Arab Tunisian Bank (64%) Al Nisr Al Arabi Ins. -

Palestinian Terrorist Organizations Use the Arab Bank to Channel
SSppeecciiiaalll IIInnfffoorrrmmaatttiiioonn JJJuulllyy 220000044 BBuulllllleetttiiinnn Intelligence and Terrorism Information Center at the Center for Special Studies (C.S.S.) PPallessttiiniiaan TTeerrroorisstt Orggaanizzattionss Ussee TThee Arraab BBannk ttoo Channneel MMoonneey iintoo TTeerrroorismm Introduction The Arab Bank is a private banking institution with head offices in Jordan. It is one of the largest banks in the Arab world and has many branches in the Palestinian Authority (PA)- administered territories. It is the preferred channel of many Palestinian terrorist organizations, particularly Hamas and the Palestinian Islamic Jihad, for the transfer of money from external sources into the PA-administered territories. Documents captured by the Israeli army clearly illustrate the bank’s important role as a the Palestinian terrorist organization conduit for the transfer of funds to the infrastructure supporting their activities (payments to the families of terrorists who die while perpetrating attacks, and to terrorists who are wounded, imprisoned or wanted by the Israeli police). In addition, funds move through the bank to finance their military activities and civilian infrastructure (da’wah). It is reasonable to assume that members of the bank’s directorate, and certainly officials of the Palestinian Authority and its security services, are aware of the services the bank provides to the terrorist organizations; despite that, they have never taken effective steps to stop them. 2 Background The Arab Bank is one of the largest financial institutions in the Arab world. It has 190 branches in 28 countries and operates in every Arab country (including 87 branches in Jordan, 15 in the PA-administered territories, 12 in Lebanon, 11 in Morocco, 9 in Yemen, 8 in Oman, 8 in the United Arab Emirates, 7 in Egypt, 5 in Bahrain, 4 in Qatar and 3 in Algeria). -
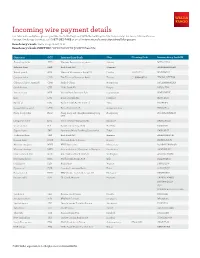
Incoming Wire Payment Details for International Wires, Please Provide the Initiating Bank with the Routing Instructions Below
Incoming wire payment details For international wires, please provide the initiating bank with the routing instructions below. For more information on Foreign Exchange Services, call 1-877-593-2468 or email [email protected]. Beneficiary’s bank: Wells Fargo Bank, N.A. Beneficiary’s bank SWIFT BIC: WFBIUS6WFFX (SWIFT Field 57a) Currency CCY Intermediary Bank City Clearing Code Intermediary Swift ID Australian dollar AUD Westpac Banking Corporation Sydney WPACAU2S Bahraini dinar BHD Arab Bank PLC Manama ARABBHBMMAN British pound GBP National Westminster Bank PLC London SC600004 NWBKGB2L Candian dollar CAD The Toronoto Dominion Bank Toronto CC000400732 TDOMCATTTOR Chinese offshore renminbi CNH Bank of China Hong Kong BKCHHKHHXXX Czech koruna CZK HSBC Bank PLC Prague MIDLCZPP Danish krone DKK Nordea Bank Danmark A/S Copenhagen NDEADKKK Euro EUR Deutsche Bank AG Frankfurt DEUTDEFF Fiji dollar FJD Bank of South Pacific Limited Suva BOSPFJFJ Guatemalan quetzal GTQ Banco Industrial SA Guatemala City INDLGTGC Hong Kong dollar HKD Hong Kong and Shanghai Banking Corp Hong Kong HSBCHKHHHKH LTD Hungarian forint HUF Unicredit Bank Hungary ZRT Budapest BACXHUHB Israeli shekel ILS Bank Leumi le Israel B.M. Tel-Aviv LUMIILIT Japanese yen JPY Sumitomo Mitsui Banking Corporation Tokyo SMBCJPJT Jordanian dinar JOD Arab Bank PLC Amman ARABJOAXTRF Kuwaiti dinar KWD National Bank of Kuwait Kuwait NBOKKWKW Mexican new peso MXN BBVA Bancomer Mexico City BCMRMXMMCOR Moroccan dirham MAD Societe Generale Marocaine de Banques Casablanca SGMBMAMC -

Arab Bank Group Annual Report 2012 T AB
Arab Bank Group Annual Report 2012 t AB CHAIRMAN’S MESSAGE 4 l E O CEO’S Message 6 Board Of Directors’ REport f CON - MAIN BUSINESS ACtIVItIES Of ARAB BANK 10 - Geographical Coverage 14 - Branches & StAff Distribution According tO Governorates 15 t EN - Addresses Of Arab Bank Branches and Offices Abroad 16 t - TotAl EMplOyees Of Arab Bank Group 20 S - CApItAl Investment Of Arab Bank 21 - Subsidiaries & Sister Company 22 - DetailEd INformation on the Bank’S Subsidiaries & Sister Company 34 - MEMBERS Of tHE BOARd Of dIRECtORS 39 - SENIOR EXECUtIVES 49 - NUMBER Of SHARES OWNEd By MAJOR SHAREHOLDERS AS At 31 dECEMBER 2012 & 2011 65 - CompEtItiveness and Market Share 66 - PatentS & Government Protection 68 - Major SUppliers and ClientS 69 - Government or INternational OrganizAtions RegulAtions 70 - Arab Bank OrganizAtion Chart / Head Office 71 - NUMBER Of StAFF ANd ACAdEMIC QUAlIfCAtIONS 72 - Training Courses vs. Trainees in Jordan & Arab Areas in 2012 MAtrix 74 - RISK MANAGEMENt 76 - AccomplishmentS 2012 87 - Financial IMpact Of Non-Recurring Operations 91 2 t AB - Time Series DatA for Major Financial INdicators (2008 – 2012) 92 l - Financial Performance 93 E O - FUtURE OUTLOOK ANd PLANS fOR 2013 102 f - EXternal AUdItors’ Compensation in jordan and abroad 105 CON - Number Of Arab Bank Shares Owned By Members Of the Board 106 - Number Of Arab Bank Shares Owned By Senior Executives 108 t - Number Of Arab Bank Shares Owned By the RElAtives Of the Board Members 110 EN - Number Of Arab Bank Shares Owned By the RElAtives Of the Senior Executives