Technology and Engineering International Journal of Recent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

KERALA SOLID WASTE MANAGEMENT PROJECT (KSWMP) with Financial Assistance from the World Bank
KERALA SOLID WASTE MANAGEMENT Public Disclosure Authorized PROJECT (KSWMP) INTRODUCTION AND STRATEGIC ENVIROMENTAL ASSESSMENT OF WASTE Public Disclosure Authorized MANAGEMENT SECTOR IN KERALA VOLUME I JUNE 2020 Public Disclosure Authorized Prepared by SUCHITWA MISSION Public Disclosure Authorized GOVERNMENT OF KERALA Contents 1 This is the STRATEGIC ENVIRONMENTAL ASSESSMENT OF WASTE MANAGEMENT SECTOR IN KERALA AND ENVIRONMENTAL AND SOCIAL MANAGEMENT FRAMEWORK for the KERALA SOLID WASTE MANAGEMENT PROJECT (KSWMP) with financial assistance from the World Bank. This is hereby disclosed for comments/suggestions of the public/stakeholders. Send your comments/suggestions to SUCHITWA MISSION, Swaraj Bhavan, Base Floor (-1), Nanthancodu, Kowdiar, Thiruvananthapuram-695003, Kerala, India or email: [email protected] Contents 2 Table of Contents CHAPTER 1. INTRODUCTION TO THE PROJECT .................................................. 1 1.1 Program Description ................................................................................. 1 1.1.1 Proposed Project Components ..................................................................... 1 1.1.2 Environmental Characteristics of the Project Location............................... 2 1.2 Need for an Environmental Management Framework ........................... 3 1.3 Overview of the Environmental Assessment and Framework ............. 3 1.3.1 Purpose of the SEA and ESMF ...................................................................... 3 1.3.2 The ESMF process ........................................................................................ -

IEEE Xplore文献资源介绍 IEEE Xplore科研检索演示 IEEE国际期刊会议投稿流程 IEEE相关资源推介 1
深度解密IEEE数据库: 科研检索与学术投稿 陈伟 iGroup公司IEEE产品培训主管 2016 培训重点 IEEE Xplore文献资源介绍 IEEE Xplore科研检索演示 IEEE国际期刊会议投稿流程 IEEE相关资源推介 1. 关于IEEE The Institute of Electrical & Electronics Engineers, 全球 最大的行业技术学会,成员遍布全球160多个国家和地区 ,会员超过40万人 IEEE带来的不仅仅只是技术文献 Our Global Reach 45 431,000+ Technical Societies and 160+ Members Councils Countries Our Technical Breadth 1,400+ 3,700,000+ 170 Annual Conferences Technical Documents Top-cited Periodicals 4 IEEE Societies IEEE Instrumentation and Measurement Society IEEE Aerospace and Electronic Systems Society IEEE Intelligent Transportation Systems Society IEEE Antennas and Propagation Society IEEE Magnetics Society IEEE Broadcast Technology Society IEEE Microwave Theory and Techniques Society IEEE Circuits and Systems Society IEEE Nuclear and Plasma Sciences Society IEEE Communications Society IEEE Oceanic Engineering Society IEEE Components, Packaging, and Manufacturing IEEE Photonics Society Technology Society IEEE Power Electronics Society IEEE Computational Intelligence Society IEEE Power and Energy Society IEEE Computer Society IEEE Product Safety Engineering Society IEEE Consumer Electronics Society IEEE Professional Communications Society IEEE Control Systems Society IEEE Reliability Society IEEE Dielectrics and Electrical Insulation Society IEEE Robotics and Automation Society IEEE Education Society IEEE Signal Processing Society IEEE Electron Devices Society IEEE Society on Social Implications of Technology IEEE Electromagnetic Compatibility Society IEEE Solid-State Circuits Society IEEE Engineering in Medicine -

Possibilities of Airframe Structures Cost Saving Through Reducing Number of Fasteners
Possibilities of airframe structures cost saving through reducing number of fasteners RŮŽEK Roman1,a, DOUBRAVA Radek1,b, KRUSE-STRACK Thomas2,c and KOERWIEN Thomas3,d 1Czech Aerospace Research Centre, Strength of Structure Department; Beranových 130, 199 05 Praha - Letňany, Czech Republic 2 Airbus Operations GmbH, Airframe Research & Technology, Kreetslag 10 21129 Hamburg Germany 3 Airbus Defence and Space GmbH, Materials & Processes, Rechliner Str., 85077 Manching, Germany [email protected], [email protected], [email protected], d [email protected] Keywords: Key, Word, Paper, Best conference, Contribution template (maximum of 5) Abstract. Reduction of numbers of mechanical fasteners together with bonding technology application can be one of the possibilities how to decrease costs of the structure. In the paper, results based on fatigue testing of novel design approaches for damage tolerant high load transfer (HLT) joints, as e.g. panel joints, are discussed for carbon fibre reinforced plastics (CFRP) adherents. Fatigue experimental results and numerical simulations of Wide Single Lap Shear (WSLS) specimen are presented for different configurations to proof the crack stopping behaviour of "state of the art" fasteners as reference crack arrestor concept. Introduction One of the main aims of designers is application of cost-effective strategies. The composite structures can lower costs of an airframe significantly, but there are some obstacles to adopt of advanced technologies like adhesive bonding or welding and prevent to use full strength capabilities of these technologies to real structures. Nowadays, there is no fully certified bonded technology applicable to full-scale airframe structure which comply airworthiness regulations from viewpoint of damage tolerance criteria. -

Abstract and Index and Web Discovery Services IEEE Partners
____________________________________________________________________________________________________________ Abstract and Index and Web Discovery Services IEEE Partners Introduction This document is intended to provide a general overview of the abstract and indexing services and web discovery services that take in IEEE content. While this report is intended to provide readers with information on IEEE content indexed and in what service, there are several things to keep in mind: Services identified in this report do not cover everything in IEEE’s Xplore Digital Library either because IEEE does not provide all content to these services, or because only certain content was selected by a partner. Some services add and delete titles regularly, or include only select articles, in order to maintain a database that is relevant to their audience. While IEEE may provide a data feed for a particular subscription package (noted in the tables below), partners are not required to index all content. Most partners update their products at varying intervals and many Abstract and Indexing Services do not include corrected or updated article information. As a result, and given that these services and our agreements with these partners can and do change, readers of this report are encouraged to contact Krista Thom, Publishing Relations Program Specialist at [email protected] with specific questions. Abstract & Indexing Services Abstract and indexing services maintain databases, often subject-specific, which users can search to find relevant content. The data included in these services may be peer-reviewed journals, books, reports, and other types of content. Unlike web scale discovery services, these services collect metadata (including abstracts) from publishers and other organizations into large repositories or indexes. -

Top 10 Male Indian Singers
Top 10 Male Indian Singers 001asd Don't agree with the list? Vote for an existing item you think should be ranked higher or if you are a logged in,add a new item for others to vote on or create your own version of this list. Share on facebookShare on twitterShare on emailShare on printShare on gmailShare on stumbleupon4 The Top Ten TheTopTens List Your List 1Sonu Nigam +40Son should be at number 1 +30I feels that I have goten all types of happiness when I listen the songs of sonu nigam. He is my idol and sometimes I think that he is second rafi thumbs upthumbs down +13Die-heart fan... He's the best! Love you Sonu, your an idol. thumbs upthumbs down More comments about Sonu Nigam 2Mohamed Rafi +30Rafi the greatest singer in the whole wide world without doubt. People in the west have seen many T.V. adverts with M. Rafi songs and that is incediable and mind blowing. +21He is the greatest singer ever born in the world. He had a unique voice quality, If God once again tries to create voice like Rafi he wont be able to recreate it because God creates unique things only once and that is Rafi sahab's voice. thumbs upthumbs down +17Rafi is the best, legend of legends can sing any type of song with east, he can surf from high to low with ease. Equally melodious voice, well balanced with right base and high range. His diction is fantastic, you may feel every word. Incomparable. More comments about Mohamed Rafi 3Kumar Sanu +14He holds a Guinness World Record for recording 28 songs in a single day Awards *. -

Siaran Media Radiozayan (BM) FINAL 2OCT
SIARAN MEDIA RADIO ‘ZAYAN’ SAJI SEGMEN GAYA HIDUP MUSLIM MODEN KONTEMPORARI Dengarkan Mawi, Raqib, Lin Ariffin, Anas dan Falyq sebagai pengemudi utama Zayan menerusi strim di zayan.my dan gelombang radio bermula 2 Oktober! KUALA LUMPUR, 2 Oktober – Masih lagi mengekalkan prestasi sebagai rangkaian radio nombor satu Malaysia, Astro Radio terus memperkukuhkan jenama-jenama radio di bawah naungannya dengan menyediakan pelbagai kandungan menarik yang menepati citarasa para pendengar di Malaysia. Terus utuh menjadi pilihan hati rakyat Malaysia, Astro Radio menubuhkan sebuah lagi jenama baharu radio yang diberi nama Zayan. Diumumkan pada 21 September 2017 lalu bersempena Majlis Kesyukuran anjuran Astro Radio, Zayan bakal beroperasi pada 2 Oktober 2017 bersama lima (5) orang penyampai radio yang terdiri daripada selebriti terkenal tanah air seperti bekas juara Akademi Fantasia (AF) musim ke-3 Mawi , bekas penyanyi kumpulan nasyid, Anas , penyanyi lagu ketuhanan Raqib, Falyq dan pengacara rancangan Bismillahdduha (Astro Oasis), Lin Ariffin. Menurut Pengurus Kandungan Zayan, Wan Syahrul Amry bin Wan Mansor, “Zayan menyediakan pelbagai kandungan yang merangkumi fesyen, teknologi, hiburan dan gaya hidup terkini berlandaskan gaya hidup Muslim moden kontemporari. Gelombang baharu ini tertumpu kepada golongan pelajar-pelajar dan dewasa bekerjaya serta pendengar muda alaf baru yang sentiasa aktif menerokai dunia dan berkongsi pengalaman mereka. Membawa maksud ‘keindahan’, pengisian baharu ini merupakan stesen berbahasa Malaysia keempat (4) di bawah naungan Astro Radio yang dilancarkan pada 2 Oktober.” Tambah Wan Syahrul Amry, “Stesen ini turut menawarkan alternatif yang lebih baik untuk para pendengar khususnya golongan Muslim moden kontemporari, yang mementingkan pengisian positif dalam mendasari dan memenuhi kehidupan seharian mereka. Kami menampilkan barisan personaliti radio yang bertenaga, kreatif, trendy, peramah, ceria dan mempunyai prinsip hidup yang tinggi. -
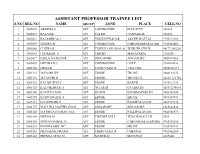
Assistant Professor Trainee List
ASSISTANT PROFESSOR TRAINEE LIST S.NO REG.NO NAME GROUP ZONE PLACE CELL.NO 1 5005002 ABARNA.S APT COIMBATORE POLLACHI 288830 2 5005027 BALAJI.K APT SALEM NAMAKKAL 252624 3 5005031 BALAMBIGA.J APT VIRUDHUNAGAR ARUPPUKOTTAI 9790311169 4 5005059 CHITRA .R APT COIMBATORE CHENNIAMPALAYAM 9942602460 5 5005060 CHITRA.R APT THIRUVANNAMALAI THIRUPPATHUR 04177 243224 6 5005061 CHOKKAR .N APT TRICHY MANAPARAI 2260206 7 5005077 EZHLILNATHAN.R APT SINGAPORE SINGAPORE 9443079960 8 5005085 GEETHA.K.J. APT COIMBATORE OOTY 9942028536 9 5005100 HEMA.K APT THIRUVALLUR VELLORE 99940 63717 10 5005111 JAYASRI .KP APT ERODE ERODE 9442122278 11 5005116 JEYANTHI.D APT ERODE ERODE DT. 04285-221702 12 5005123 KALIMUTHU.V APT ERODE KARUR 9994311315 13 5005125 KALVIKARASI .S APT GUJARAT GUJARATH 0265-3298695 14 5005140 KAVITHA.M.M. APT HOSUR DHARMAPURI-DT. 9486358784 15 5005155 KUPPUSWAMI .A APT ERODE ERODE 9843269931 16 5005161 LOGESWARI.S APT ERODE PALLIPALAYAM 9487927370 17 5005177 MALLIKA MATHIVANAN APT SINGAPORE SINGAPORE 6565643834 18 5005188 MATHIVATHANAN .M.K APT ERODE PALLIPALAYAM. 9842988871 19 5005190 MEENA.M APT TIRUNELVELI THACHANALLUR 5655 20 5005196 MOHANAMBAL .G APT ERODE CHENNIMALAI-ERODE 9965360200 21 5005239 PONNUSAMY .VC APT ERODE ERODE 9965769357 22 5005242 PRAVEENKUMAR.R APT THIRUVALLUR CHENNAI 9962062264 23 5005245 PREMALATHA.M APT MADURAI MADURAI 2629604 24 5005254 RAJALAKSHMI.N APT SALEM NAMAKKAL 9442156240 25 5005280 RUPA.T APT THIRUVANNAMALAI THIRUVANNAMALAI 7845443323 26 5005285 SANGILIKALAI .M.V APT DINDIGUL BODI 283105 27 5005286 SANKAR -

Chinese Journal of Atherosclerosis
CHINESE JOURNAL OF ARTERIOSCLEROSIS Volume 18, Number 7, July 26,2010 CONTENTS EXPERIMENTAL RESEARCH 1. Elevated Expression of Urotensin Ⅱ and Its Receptor in Vascular Calcification of Rats.ZHANG Yong-Gang, ZHANG Xu-Sheng, WEI Rui-Hong, WU Li-Biao, CHEN Xin-Sheng, LI Jun,and XU Xi-Zhen. CHINESE JOURNAL OF ARTERIOSCLEROSIS. 2010;18(17): 505 2. Effect of 2,3,5,4-Tetrahydroxystilbene Glucoside on the Expression of NF-κB and TNFα in Human Umbilical Vein Endothelial Cell Injured by H2O2. LONG Shi-Yin, CUI Hui-Hui, ZHANG Cai-Pin,QIAO Xin-Hui, Tian Ying, TIAN Ru-fang, TONG Li ,and HUANG Liang-Zhu. CHINESE JOURNAL OF ARTERIOSCLEROSIS. 2010;18(17): 510 3. Effect of Endothein 1 and BQ 123 on Adenosine Triphosphatase Activity and mRNA Expression in Aortic Smooth Muscle Cells from Spontanously Hypertensive Rats.YANG Zheng, SHANG Qian-Hui, WU Qin,and QIU Min. CHINESE JOURNAL OF ARTERIOSCLEROSIS. 2010;18(17): 514 4. Effect of Propolis on Reverse Cholesterol Transport in Mice in Vivo. SI Yan-Hong, YU Yang, WANG Xin-Nong, SANG Hui, WANG Shao-Yan, WANG Jia-Fu, QIN Shu-Cun . CHINESE JOURNAL OF ARTERIOSCLEROSIS. 2010;18(17): 519 5. Apoptosis of Human Umbilical Vein Endothelial Cells Induced by Fluctuated Hyperglycemia Is Associatedwith Adiponectin Receptor1. ZHAO Hong-Yu, YI Tong-Ning,and ZHANG Jin. CHINESE JOURNAL OF ARTERIOSCLEROSIS. 2010;18(17): 523 6. Gambogic Acid Inhibits Cell Proliferation via Suppressing Epithelial Growth Factor Receptor Tyrosine Phosphorylation in Rat Aortic Smooth Muscle Cell.LIU Yong, LIN Mei, LI Wen, HE Yan-Zheng, SHI Sen, ZENG Hong,and WANG Shen-Ming CHINESE JOURNAL OF ARTERIOSCLEROSIS. -

Regional Contest Cookbook
Regional Contest Cookbook About ACM ICPC Mission: ACM International Collegiate Programming Contest (ICPC) provides college students with opportunities to interact with students from other universities and to sharpen and demonstrate their problem-solving, programming, and teamwork skills. The contest provides a platform for ACM, industry, and academia to encourage and focus public attention on the next generation of computing professionals as they pursue excellence. About the Contest The ACM International Collegiate Programming Contest (ICPC) traces its roots to a competition held at Texas A&M in 1970 hosted by the Alpha Chapter of the UPE Computer Science Honor Society. The idea quickly gained popularity within the United States and Canada as an innovative initiative to challenge the top students in the emerging field of computer science. The contest evolved into a multi-tier competition with the first Finals held at the ACM Computer Science Conference in 1977. Operating under the auspices of ACM and headquartered at Baylor University since 1989, the contest has expanded into a global network of universities hosting regional competitions that advance teams to the ACM-ICPC World Finals. Since IBM became sponsor in 1997, the contest has increased by a factor of eight. Participation has grown to involve several tens of thousands of the finest students and faculty in computing disciplines at 1,821 universities from 83 countries on six continents. The contest fosters creativity, teamwork, and innovation in building new software programs, and enables students to test their ability to perform under pressure. Quite simply, it is the oldest, largest, and most prestigious programming contest in the world. -

IFLA Journal Volume 46 Number 3 October 2020
IFLA Volume 46 Number 3 October 2020 IFLA Contents Articles Designing a mentoring program for faculty librarians 197 Erla P. Heyns and Judith M. Nixon Transformational and transactional leadership and knowledge sharing in Nigerian university libraries 207 C. I. Ugwu, O. B. Onyancha and M. Fombard Knowledge management and innovation: Two explicit intentions pursued by Spanish university libraries 224 Ana R. Pacios National and international trends in library and information science research: A comparative review of the literature 234 Mallikarjun Dora and H. Anil Kumar Taxonomy design methodologies: Emergent research for knowledge management domains 250 Virginia M. Tucker The effect of information literacy instruction on lifelong learning readiness 259 Leili Seifi, Maryam Habibi and Mohsen Ayati Semantic modeling for education of library and information sciences in Iran, based on Soft Systems Methodology 271 Amir Hessam Radfar, Fatima Fahimnia, Mohammad Reza Esmaeili and Moluk al-Sadat Beheshti Abstracts 290 Aims and Scope IFLA Journal is an international journal publishing peer reviewed articles on library and information services and the social, political and economic issues that impact access to information through libraries. The Journal publishes research, case studies and essays that reflect the broad spectrum of the profession internationally. To submit an article to IFLA Journal please visit: journals.sagepub.com/home/ifl IFLA Journal Official Journal of the International Federation of Library Associations and Institutions ISSN 0340-0352 [print] 1745-2651 [online] Published 4 times a year in March, June, October and December Editor Steve Witt, University of Illinois at Urbana-Champaign, 321 Main Library, MC – 522 1408 W. Gregory Drive, Urbana, IL, USA. -

Nautical Education for Offshore Cxtractivc
Lso-B-7i-ooz NAUTICALEDUCATION FOR OFFSHORE CXTRACTIVC INDUSTRIES RV G-H.HOFFMANN WITH FREDTOWNSEND AND WARREN NORVILLE 5' GRAHT PUI3I.ICATIOHHO. LSU-II-77-OL C6NTCRfOR WETLAND RESOURCES ~ LOUISIANA STATC UNIVf RSIEY ~ BATON ROUCIC, LOUISIANA 7000 NAUTICAL EDUCATION FOR THE V~M$pQog767 QoM G. H. Ho f fmann with Fred Townsend and Warren Norville LOUISIANA STATE UNIVERSITY CENTER FOR WETLAND RESOURCES BATON ROUGE, LA 70803 Sea Grant Publication No. LSU-8-77-001 September 1977 This work is a result of research sponsored jointly by the Terrebonne Parish School Board and the Louisiana Sea Grant Program, a part of the National Sea Grant Program maintained by the National Oceanic and Atmospheric Administration of the U.S. Department of Commerce. CONTENTS List of Figures List of Tables Vi Acknowledgments Beginnings of the Oil Industry 1 2 The Offshore Revolution Drilling a Wildcat Well The Petr omar ine Fleet 46 6 4.1 Tankers 4.2 Seagoing Tank Barges and Tugs ll 4.3 Inland Tank Barges and Towboats 13 4.4 Inland Drilling Barges 16 4.5 Offshore Drilling Tenders 16 4.6 Submersible Drilling Vessels 17 4.7 3ack-up DrilIing Barges 18 4.8 Semi-Submersible Drilling Vessels 19 4.9 Drill Ships 20 4.10 Crewboats 27 4.11 Supply vessels 28 4.12 Tugs 30 4.13 Derrick Barges 31 4.I4 Pipelaying Barges 31 4.15 Air Cushion Vehicles ACV! 37 Producing Oil and Gas 37 Design Procedures 44 6.1 Owner Requirements 44 6.2 Design Drawings and Specifications 45 6.3 Regulatory Agencies 49 6.4 Design Calculations 54 6.5 The Measurements of a Ship 60 6.6 Free Surface 68 6.7 Model Testing 69 Construction Procedure 70 7.1 Estimating 70 7.2 Working Plans 72 7.3 Production 74 7.4 Inspection 76 7.5 Trials and Tests 78 Delivery 80 Stability and Trim 82 9.1 Stability 82 9.2 Transverse Metacenter 86 9.3 Calculating GM 87 9.4 KM and KG 88 9. -

A TRIBUTE in LOVING MEMORY Irina Diana Tarabac
A TRIBUTE IN LOVING MEMORY Irina Diana Tarabac (1970-2007) Irina Diana Tarabac dedicated her life to learning, teaching, and science – the field of her choice being linguistics. Among many brilliant scholars and scientists in the Linguistics Department at Stony Brook University, Irina stood out for many a reasons. Unfortunately, Irina left us too early in October 2007. After arriving to study at Stony Brook at 2002, Irina became an active member of the linguistic community in the metropolitan area of New York. She frequently attended seminars in the Linguistics Departments of NYU and the CUNY Graduate Center. Irina was dedicated to life-long learning, and she set extremely high standards for herself, her own research and her teaching responsibilities. She taught a morphology seminar in Bucharest and served as a TA for classes on many different topics at Stony Brook, including syntax, morphology, language philosophy, phonology, typology, and Semitic languages. She was a wonderful teacher and was very concerned about her students. Her dedication to linguistics didn’t leave her much time to pursue her hobbies, but whenever Irina found some time off, she enjoyed listening to symphonic music, reading good literature, visiting museums, and spending time with her friends. Irina earned a Master’s degree in Bucharest, Romania in 1996 and had studied and conducted research in the Netherlands between 1997 and 1999. Irina conducted research on well-known languages such as Dutch, Romanian, and Modern Greek as well as less-known languages such as Rapanui and Burushaki. Irina’s passing is a great loss to her family, her friends and the field of linguistics.