Forensic Analysis of the Windows Telemetry for Diagnostics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
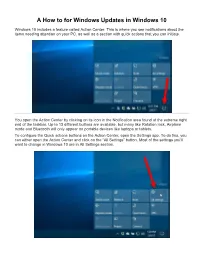
A How to for Windows Updates in Windows 10
A How to for Windows Updates in Windows 10 Windows 10 includes a feature called Action Center. This is where you see notifications about the items needing attention on your PC, as well as a section with quick actions that you can initiate. You open the Action Center by clicking on its icon in the Notification area found at the extreme right end of the taskbar. Up to 13 different buttons are available, but many like Rotation lock, Airplane mode and Bluetooth will only appear on portable devices like laptops or tablets. To configure the Quick actions buttons on the Action Center, open the Settings app. To do this, you can either open the Action Center and click on the “All Settings” button. Most of the settings you'll want to change in Windows 10 are in All Settings section. or you can open the Start menu and click the “Settings” button on the lower-left side of the menu. Windows settings is organized into various categories: System, Devices, Network & Internet, Personalization, Apps, Accounts, Time & language, Ease of Access, Privacy, and Update & security. You click on a category to view and change more settings for that category. Settings in Windows 10 – alternatively use Win () + I key combination. The Settings app from Windows 10 holds almost all the settings governing the way your computer or device works. The traditional way of getting to one setting or to another is to open the appropriate settings category and browse through it until you find what you’re looking for. The Setting app from Windows 10 is very well organized, a lot better than the old Control Panel used to be. -

APEX® Compounding System List of Microsoft Windows 10 Patches That Have Been Verified for Use with APEX
APEX® Compounding System List of Microsoft Windows 10 Patches That Have Been Verified For Use with APEX 2021-02 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4601318) 2021-02 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4601392) 2021-02 .NET Core 3.1.12 Security Update for x64 Client Security Update for Windows 10 Version 1607 for x64-based Systems (KB4535680) Security Update for SQL Server 2016 Service Pack 2 CU (KB4583461) Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (UP TO Version 1.331.666.0) 2020-12 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4593226) Update for Microsoft Defender Antivirus antimalware platform - KB4052623 (UP TO Version 4.18.2011.6) 2020-11 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4586830) Windows Malicious Software Removal Tool x64 -UP TO v5.86 (KB890830) Intel - Ports - 2011.0.7.0 2020-10 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4580346) 2020-10 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4580325) 2020-09 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4577015) 2020-09 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4576750) 2020-08 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4571694) 2020-07 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4565912) 2020-07 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4565511) 2020-06 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4561600) 2020-06 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4561616) 2020-06 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4562561) B. -

An Introduction to Windows Operating System
EINAR KROGH AN INTRODUCTION TO WINDOWS OPERATING SYSTEM Download free eBooks at bookboon.com 2 An Introduction to Windows Operating System 2nd edition © 2017 Einar Krogh & bookboon.com ISBN 978-87-403-1935-4 Peer review by Høgskolelektor Lars Vidar Magnusson, Høgskolen i Østfold Download free eBooks at bookboon.com 3 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS CONTENTS Introduction 9 1 About Windows history 10 1.1 MS-DOS 10 1.2 The first versions of Windows 11 1.3 Windows NT 12 1.4 Windows versions based on Windows NT 13 1.5 Windows Server 15 1.6 Control Questions 17 2 The tasks of an operating system 18 2.1 About the construction of computers 19 2.2 Central tasks for an operating system 20 2.3 Control Questions 22 �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� www.discovermitas.comMaersk.com/Mitas �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� Maersk.com/Mitas Month 16 I wwasas a construction Month 16 supervisorI wwasas in a construction the North Sea supervisor in advising and the North Sea Real work helpinghe foremen advising and IInternationalnternationaal opportunities ��reeree wworkoro placements solves Real work problems helpinghe foremen IInternationalnternationaal opportunities ��reeree wworkoro placements solves problems Download free eBooks at bookboon.com Click on the ad to read more 4 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS 3 Some concepts and terms of the Windows operating system 23 3.1 -

Windows Server 2016 Security Guide
Windows Server Security Guide August 2017 © 2017 Microsoft Corporation. All rights reserved. The information in this document represents the current view of Microsoft on the content. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION ON THIS DOCUMENT Contents Windows Server 2016 Security Guide ............................................................. 3 Why is Windows Server 2016 security important? ............................................................................... 3 How does Windows Server 2016 help prevent and detect compromise? ........................................... 4 Additional resources ............................................................................................................................. 5 Build a secure foundation .............................................................................. 5 Stay current on Windows Server security updates ............................................................................... 5 Configure Windows Server security settings ........................................................................................ 6 The high-level process for obtaining and deploying the security baselines can be found in the Microsoft Security Compliance Toolkit 1.0. You can find out more about current Microsoft security guidance at Microsoft Security Guidance blog. .................................................................................... 7 Back up your information and systems ............................................................................................... -
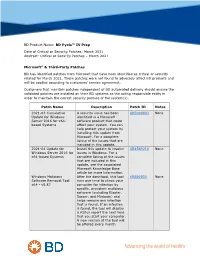
March 2021 Abstract: Critical Or Security Patches – March 2021
BD Product Name: BD Pyxis™ IV Prep Date of Critical or Security Patches: March 2021 Abstract: Critical or Security Patches – March 2021 Microsoft® & Third-Party Patches BD has identified patches from Microsoft that have been identified as critical or security related for March 2021. These patches were not found to adversely affect BD products and will be applied according to customers’ service agreement. Customers that maintain patches independent of BD automated delivery should ensure the validated patches are installed on their BD systems as the acting responsible entity in order to maintain the correct security posture of the system(s). Patch Name Description Patch ID Notes 2021-03 Cumulative A security issue has been KB5000803 None Update for Windows identified in a Microsoft Server 2016 for x64- software product that could based Systems affect your system. You can help protect your system by installing this update from Microsoft. For a complete listing of the issues that are included in this update, 2021-01 Update for Install this update to resolve KB4589210 None Windows Server 2016 for issues in Windows. For a x64-based Systems complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article for more information. Windows Malicious After the download, this tool KB890830 None Software Removal Tool runs one time to check your x64 - v5.87 computer for infection by specific, prevalent malicious software (including Blaster, Sasser, and Mydoom) and helps remove any infection that is found. If an infection is found, the tool will display a status report the next time that you start your computer. -

What's New in Windows 10
Contents What's new in Windows 10 What's new in Windows 10, version 1903 What's new in Windows 10, version 1809 What's new in Windows 10, version 1803 What's new in Windows 10, version 1709 What's new in Windows 10, version 1703 What's new in Windows 10, version 1607 What's new in Windows 10, versions 1507 and 1511 What's new in Windows 10 5/21/2019 • 2 minutes to read • Edit Online Windows 10 provides IT professionals with advanced protection against modern security threats and comprehensive management and control over devices and apps, as well as flexible deployment, update, and support options. Learn about new features in Windows 10 for IT professionals, such as Windows Information Protection, Windows Hello, Device Guard, and more. In this section What's new in Windows 10, version 1903 What's new in Windows 10, version 1809 What's new in Windows 10, version 1803 What's new in Windows 10, version 1709 What's new in Windows 10, version 1703 What's new in Windows 10, version 1607 What's new in Windows 10, versions 1507 and 1511 Learn more Windows 10 release information Windows 10 update history Windows 10 content from Microsoft Ignite Compare Windows 10 Editions See also Windows 10 Enterprise LTSC Edit an existing topic using the Edit link What's new in Windows 10, version 1903 IT Pro content 6/18/2019 • 10 minutes to read • Edit Online Applies to Windows 10, version 1903 This article lists new and updated features and content that are of interest to IT Pros for Windows 10 version 1903, also known as the Windows 10 May 2019 Update. -
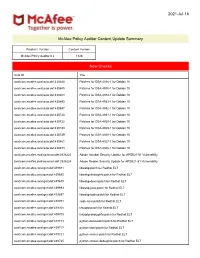
Mcafee Policy Auditor Content Update V1326
2021-Jul-16 McAfee Policy Auditor Content Update Summary Product / Version Content Version McAfee Policy Auditor 6.x 1326 New Checks Oval ID Title oval:com.mcafee.oval.auto:def:430640 Patches for DSA-4936-1 for Debian 10 oval:com.mcafee.oval.auto:def:430680 Patches for DSA-4935-1 for Debian 10 oval:com.mcafee.oval.auto:def:430683 Patches for DSA-4934-1 for Debian 10 oval:com.mcafee.oval.auto:def:430693 Patches for DSA-4933-1 for Debian 10 oval:com.mcafee.oval.auto:def:430697 Patches for DSA-4932-1 for Debian 10 oval:com.mcafee.oval.auto:def:430720 Patches for DSA-4931-1 for Debian 10 oval:com.mcafee.oval.auto:def:430732 Patches for DSA-4930-1 for Debian 10 oval:com.mcafee.oval.auto:def:430733 Patches for DSA-4929-1 for Debian 10 oval:com.mcafee.oval.auto:def:430739 Patches for DSA-4928-1 for Debian 10 oval:com.mcafee.oval.auto:def:430861 Patches for DSA-4927-1 for Debian 10 oval:com.mcafee.oval.auto:def:430873 Patches for DSA-4926-1 for Debian 10 oval:com.mcafee.oval.common:def:2938223 Adobe Acrobat Security Update for APSB21-51 Vulnerability oval:com.mcafee.oval.common:def:2938224 Adobe Reader Security Update for APSB21-51 Vulnerability oval:com.mcafee.oval.gen:def:439681 libwebp patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439685 libwebp-debuginfo patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439689 libwebp-devel patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439693 libwebp-java patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439697 libwebp-tools patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439701 ceph-iscsi patch -

Rules of the Road for Safe Patching
Rules of the road for safe patching Monthly security patches ship on the second Tuesday of each month (Patch Tuesday). For all versions of Windows, defer them for at least 15 days. That should give Microsoft time to identify and fix any significant oopses. The exception is the rare urgent threat — in which case, we'll tell you to install an update sooner than later. (Check out our AskWoody.com posts on the days following Patch Tuesday.) Another exception: Security patches may also contain nonsecurity fixes. In some cases, you might want to install a security update sooner when it includes a feature fix you really need. Microsoft also sends out preview updates, typically on the third Tuesday of each month. They are completely optional, and we recommend skipping them. We will list them in the next Patch Watch column following their release because Microsoft typically doesn't label them as previews (bad dog!). Updates can be deferred on Window 10 Pro and above. If you're running Win10 Home, we recommend upgrading to Pro. Ensure that Windows 7's patch-update setting are set to download or check for updates, but don't automatically install them. It's your best defense against problematic patches. Other rules Never install hardware drivers -- unless you get them from the computer's manufacturer Never install an update to a newer version of .NET. Let your applications set the .NET versions they need If you are offered .NET 4.8, skip it. For business, I recommend being on 1903 at this time and deferring 1909 Version 2004 Sheet updated: 7/14/2020 >>>> Should be installed as of June 30, 2020 for business patchers Known issues page: https://docs.microsoft.com/en-us/windows/release-information/status-windows- Notes: 1) Test on your network, install as you see fit. -

WINDOWS 10 UPDATES Past, Present & Future
WINDOWS 10 UPDATES Past, Present & Future � Windows as a Service Prior to Windows 10, Microsoft released new versions of Windows every few years. This traditional deployment schedule imposed a training burden on users because the feature revisions were often significant. That schedule also meant waiting long periods without new features — a scenario that doesn’t work in today’s rapidly changing world, a world in which new security, management, and deployment capabilities are necessary to address challenges. Windows as a service will deliver smaller feature updates two times per year, around March and September, to help address these issues. DEFINITIONS •Feature updates will be released twice per year, around March and September. As the name suggests, these will add new features to Windows 10, delivered in bite-sized chunks compared to the previous practice of Windows releases every 3-5 years. •Quality updates are released monthly, delivering both security and non-security fixes. These are cumulative, so installing the latest quality update is sufficient to get all the available fixes for a specific Windows 10 feature update. •Insider Preview builds are made available during the development of the features that will be shipped in the next feature update, enabling organizations to validate new features as well as compatibility with existing apps and infrastructure, providing feedback to Microsoft on any issues encountered. Device Compatibility Device compatibility in Windows 10 is also very strong; new hardware is not needed for Windows 10 as any device capable of running Windows 7 or later can run Windows 10. In fact, the minimum hardware requirements to run Windows 10 are the same as those required for Windows 7. -

Windows 10 Minimum Hardware Requirements
Windows 10 Minimum Hardware Requirements December 2019 © 2019 Microsoft. All rights reserved. Windows 10 Minimum Hardware Requirements Copyright This document is provided "as-is." Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. © 2019 Microsoft. All rights reserved. Please refer to Microsoft Trademarks for a list of trademarked products. Portions of this software may be based on NCSA Mosaic. NCSA Mosaic was developed by the National Center for Supercomputing Applications at the University of Illinois at Urbana-Champaign. Distributed under a licensing agreement with Spyglass, Inc. May contain security software licensed from RSA Data Security, Inc. UPnP™ is a certification mark of the UPnP™ Implementers Corporation. Bluetooth® is a trademark owned by Bluetooth SIG, Inc., USA and licensed to Microsoft Corporation. Intel is a registered trademark of Intel Corporation. Itanium is a registered trademark of Intel Corporation. All other trademarks are property of their respective owners. © 2019 Microsoft. All rights reserved. ii Windows 10 Minimum Hardware Requirements Contents Change history ................................................................................................... -

Windows Embedded Operating System Add-Ons and Security Updates
Windows Embedded operating system add- ons and security updates Release Notes Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2019 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. 2019 - 12 Rev. A04 Contents 1 Overview..................................................................................................................................... 8 2 Support matrix.............................................................................................................................9 3 CAD MAP VDI enhancement version 3.0.6.0 add-on for Windows 10 IoT-based thin clients................ 11 Release summary.................................................................................................................................................................. 11 Priority and recommendations.......................................................................................................................................11 Compatibility......................................................................................................................................................................... -

Installing and Upgrading Client Systems
L e s s o n Installing and Upgrading Client Systems 1 Objective Domain Matrix Objective Domain Objective Technology Skill Description Domain Number Understanding Windows Identify Windows 2.1 Systems operating system editions Understand 2.4 operating system architecture Understanding Understand 2.3 Installation Types installation types Identify upgrade 2.2 paths COPYRIGHTED MATERIAL c01.indd 10/07/2019 Page 1 Key Terms AppLocker kernel mode Assigned Access 8.1 laptop BitLocker Lite Touch Installation (LTI) BranchCache LoadState.exe Business Store Long-Term Servicing Branch clean installation Private catalog Client Hyper-V Remote Desktop cloud RemoteApp command-line interface (CLI) ScanState.exe Continuum smartphone Cortana tablet Credential Guard text user interface (TUI) Current Branch for Business upgrade installation desktop PC User Experience control and lockdown device driver user interface (UI) Device Guard user mode DirectAccess User State Migration Tool (USMT) Encrypting File System (EFS) UsmtUtils.exe Enterprise Mode Internet Explorer virtual desktops (EMIE) Windows 10 graphical user interface (GUI) Windows 10 Education Group Policy management Windows 10 Enterprise hardware interrupts (IRQ) Windows 10 Home High Touch Installation (HTI) Windows 10 Media Creation tool hybrid computer Windows 10 Pro joining to a domain Windows Deployment Services c01.indd 10/07/2019 Page 2 Understanding Windows Systems 3 Windows Hello Windows Update for Business Windows Spotlight x64 Windows To Go x86 Windows Update Zero Touch Installation (ZTI) Lesson 1 Case You work as an IT technician for Interstate Snacks, Inc., a mid-market food service and vending company. Management has decided to standardize on Windows 10 Pro and has asked your IT group to evaluate all existing computers to determine if they can support the operating system.