Filename/Filepath Limits © 2020 Dave Leippe Via
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Configuring UNIX-Specific Settings: Creating Symbolic Links : Snap
Configuring UNIX-specific settings: Creating symbolic links Snap Creator Framework NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/snap-creator- framework/installation/task_creating_symbolic_links_for_domino_plug_in_on_linux_and_solaris_hosts.ht ml on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Configuring UNIX-specific settings: Creating symbolic links . 1 Creating symbolic links for the Domino plug-in on Linux and Solaris hosts. 1 Creating symbolic links for the Domino plug-in on AIX hosts. 2 Configuring UNIX-specific settings: Creating symbolic links If you are going to install the Snap Creator Agent on a UNIX operating system (AIX, Linux, and Solaris), for the IBM Domino plug-in to work properly, three symbolic links (symlinks) must be created to link to Domino’s shared object files. Installation procedures vary slightly depending on the operating system. Refer to the appropriate procedure for your operating system. Domino does not support the HP-UX operating system. Creating symbolic links for the Domino plug-in on Linux and Solaris hosts You need to perform this procedure if you want to create symbolic links for the Domino plug-in on Linux and Solaris hosts. You should not copy and paste commands directly from this document; errors (such as incorrectly transferred characters caused by line breaks and hard returns) might result. Copy and paste the commands into a text editor, verify the commands, and then enter them in the CLI console. The paths provided in the following steps refer to the 32-bit systems; 64-bit systems must create simlinks to /usr/lib64 instead of /usr/lib. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

Powershell Integration with Vmware View 5.0
PowerShell Integration with VMware® View™ 5.0 TECHNICAL WHITE PAPER PowerShell Integration with VMware View 5.0 Table of Contents Introduction . 3 VMware View. 3 Windows PowerShell . 3 Architecture . 4 Cmdlet dll. 4 Communication with Broker . 4 VMware View PowerCLI Integration . 5 VMware View PowerCLI Prerequisites . 5 Using VMware View PowerCLI . 5 VMware View PowerCLI cmdlets . 6 vSphere PowerCLI Integration . 7 Examples of VMware View PowerCLI and VMware vSphere PowerCLI Integration . 7 Passing VMs from Get-VM to VMware View PowerCLI cmdlets . 7 Registering a vCenter Server . .. 7 Using Other VMware vSphere Objects . 7 Advanced Usage . 7 Integrating VMware View PowerCLI into Your Own Scripts . 8 Scheduling PowerShell Scripts . 8 Workflow with VMware View PowerCLI and VMware vSphere PowerCLI . 9 Sample Scripts . 10 Add or Remove Datastores in Automatic Pools . 10 Add or Remove Virtual Machines . 11 Inventory Path Manipulation . 15 Poll Pool Usage . 16 Basic Troubleshooting . 18 About the Authors . 18 TECHNICAL WHITE PAPER / 2 PowerShell Integration with VMware View 5.0 Introduction VMware View VMware® View™ is a best-in-class enterprise desktop virtualization platform. VMware View separates the personal desktop environment from the physical system by moving desktops to a datacenter, where users can access them using a client-server computing model. VMware View delivers a rich set of features required for any enterprise deployment by providing a robust platform for hosting virtual desktops from VMware vSphere™. Windows PowerShell Windows PowerShell is Microsoft’s command line shell and scripting language. PowerShell is built on the Microsoft .NET Framework and helps in system administration. By providing full access to COM (Component Object Model) and WMI (Windows Management Instrumentation), PowerShell enables administrators to perform administrative tasks on both local and remote Windows systems. -

Where Do You Want to Go Today? Escalating
Where Do You Want to Go Today? ∗ Escalating Privileges by Pathname Manipulation Suresh Chari Shai Halevi Wietse Venema IBM T.J. Watson Research Center, Hawthorne, New York, USA Abstract 1. Introduction We analyze filename-based privilege escalation attacks, In this work we take another look at the problem of where an attacker creates filesystem links, thereby “trick- privilege escalation via manipulation of filesystem names. ing” a victim program into opening unintended files. Historically, attention has focused on attacks against priv- We develop primitives for a POSIX environment, provid- ileged processes that open files in directories that are ing assurance that files in “safe directories” (such as writable by an attacker. One classical example is email /etc/passwd) cannot be opened by looking up a file by delivery in the UNIX environment (e.g., [9]). Here, an “unsafe pathname” (such as a pathname that resolves the mail-delivery directory (e.g., /var/mail) is often through a symbolic link in a world-writable directory). In group or world writable. An adversarial user may use today's UNIX systems, solutions to this problem are typ- its write permission to create a hard link or symlink at ically built into (some) applications and use application- /var/mail/root that resolves to /etc/passwd. A specific knowledge about (un)safety of certain directories. simple-minded mail-delivery program that appends mail to In contrast, we seek solutions that can be implemented in the file /var/mail/root can have disastrous implica- the filesystem itself (or a library on top of it), thus providing tions for system security. -

Converting ASCII Files
Converting Data from ASCII to SPSS System Files Some data files, especially older ones, will not be available as SPSS system files, but instead will be provided with a fixed-format ASCII (American Standard Code for Information Interchange) file and an SPSS syntax file. Once you have downloaded your files and, if necessary, unzipped them: • Start SPSS and open the syntax file (the one with the “.sps” extension). • Find the “FILE HANDLE” command and replace “data-filename” with the path to your data file (the one ending in “.txt”). For example, if you download ICPSR Study 4131 (ABC News Pennsylvania Poll, Sept. 2004) in a directory on your “C” drive called “Temp,” the path created will be "C:\Temp\5268001\ICPSR_04131\DS0001_ABC_News_Pennsylvania_Poll,_Sept ember_2004__\04131-0001-Data.txt." (This is admittedly pretty unwieldy, and it might be a good idea to move and rename the file before proceeding). The FILE HANDLE: FILE HANDLE DATA / NAME="data-filename" LRECL=225. would become: FILE HANDLE DATA / NAME="C:\Temp\5268001\ICPSR_04131\DS0001_ABC_News_Pennsylvania_P oll,_September_2004__\04131-0001-Data.txt " LRECL=225. • Find the “SAVE OUTFILE” command (probably the last one in the file), and replace “spss-filename.sav” with the name and path of the SPSS system file you wish to create. If the command is preceded by an asterisk, remove the asterisk. For example, SAVE OUTFILE="spss-filename.sav". would become: SAVE OUTFILE="C:\Temp\5268001\ICPSR_04131\DS0001_ABC_News_Pennsylvania _Poll,_September_2004__\04131-0001-Data.sav". From the menu bar, click on “Run” and “All.” If no "SAVE OUTFILE" command exits, create one from scratch. -

An Incremental Path Towards a Safer OS Kernel
An Incremental Path Towards a Safer OS Kernel Jialin Li Samantha Miller Danyang Zhuo University of Washington University of Washington Duke University Ang Chen Jon Howell Thomas Anderson Rice University VMware Research University of Washington LoC Abstract Incremental Progress Tens of Linux Safe Linux Linux has become the de-facto operating system of our age, Millions FreeBSD but its vulnerabilities are a constant threat to service availabil- Hundreds of Singularity ity, user privacy, and data integrity. While one might scrap Thousands Biscuit Linux and start over, the cost of that would be prohibitive due Theseus Thousands RedLeaf seL4 to Linux’s ubiquitous deployment. In this paper, we propose Hyperkernel Safety an alternative, incremental route to a safer Linux through No Type Ownership Functional proper modularization and gradual replacement module by Guarantees Safety Safety Verification module. We lay out the research challenges and potential Figure 1: Our vision and the current state of systems. solutions for this route, and discuss the open questions ahead. security vulnerabilities are reported each year, and lifetime CCS Concepts analysis suggests that the new code added this year has intro- duced tens of thousands of more bugs. ! • Software and its engineering Software verification; While operating systems are far from the only source of se- ! • Computer systems organization Reliability. curity vulnerabilities, it is hard to envision building trustwor- Keywords thy computer systems without addressing operating system correctness. kernel safety, verified systems, reliable systems One attractive option is to scrap Linux and start over. Many ACM Reference Format: past works focus on building more secure and correct op- Jialin Li, Samantha Miller, Danyang Zhuo, Ang Chen, Jon Howell, erating systems from the ground up: ones based on strong and Thomas Anderson. -
A How to for Windows Updates in Windows 10
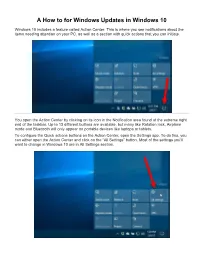
A How to for Windows Updates in Windows 10 Windows 10 includes a feature called Action Center. This is where you see notifications about the items needing attention on your PC, as well as a section with quick actions that you can initiate. You open the Action Center by clicking on its icon in the Notification area found at the extreme right end of the taskbar. Up to 13 different buttons are available, but many like Rotation lock, Airplane mode and Bluetooth will only appear on portable devices like laptops or tablets. To configure the Quick actions buttons on the Action Center, open the Settings app. To do this, you can either open the Action Center and click on the “All Settings” button. Most of the settings you'll want to change in Windows 10 are in All Settings section. or you can open the Start menu and click the “Settings” button on the lower-left side of the menu. Windows settings is organized into various categories: System, Devices, Network & Internet, Personalization, Apps, Accounts, Time & language, Ease of Access, Privacy, and Update & security. You click on a category to view and change more settings for that category. Settings in Windows 10 – alternatively use Win () + I key combination. The Settings app from Windows 10 holds almost all the settings governing the way your computer or device works. The traditional way of getting to one setting or to another is to open the appropriate settings category and browse through it until you find what you’re looking for. The Setting app from Windows 10 is very well organized, a lot better than the old Control Panel used to be. -

Simple File System (SFS) Format
Simple File System (SFS) Format Version SFS-V00.01 The SFS is a simple file system format optimized for writing and for low overhead.. The advantages of this format are: • Event navigation is possible using simple content-independent file system like functions. • Very low overhead. No loss due to block size granularity • Entire valid file system can be created by appending content On the other hand, random access directory navigation is rather slow because there is no built-in indexing or directory hierarchy. For a 500MB file system containing files with 5k bytes this represents an initial search overhead of ~1-2 sec (~100,000 seeks). SFS Structure The structure of a SFS file is as follows VolumeSpec Head File1 File1 Binary Data File2 File2 Binary Data ... ... Tail VolumeSpec: This is simply a 12 byte character string representing filesystem version. For example: “SFS V00.01” Head: This is a short header record. The byte order only applies to the time field of this record. type = “HEAD” byte_order = 0x04030201 time File: The File records are a variable length record containing information about a file. type = “FILE” byte_order = 0x04030201 Sz head_sz attr reserved name.... name (continued).... “byte_order” corresponds only to this header. The endiness of the data is undefined by SFS “sz” corresponds to the datafile size. This may be any number, but the file itself will be padded to take up a multiple of 4 bytes “head_sz” this must be a multiple of 4 “attr” SFS_ATTR_INVALID: file deleted SFS_ATTR_PUSHDIR: push current path to path stack SFS_ATTR_POPDIR: pop current path from path stack SFS_ATTR_NOCD: this record doesn’t reset the basedir “name” the name of the file. -

A Plethora of Paths
A Plethora of Paths Eric Larson Seattle University [email protected] Abstract A common static software bug detection technique is to use path simulation. Each execution path is simulated using symbolic variables to determine if any software errors could occur. The scalability of this and other path-based approaches is dependent on the number of paths in the pro- gram. This paper explores the number of paths in 15 differ- ent programs. Often, there are one or two functions that contribute a large percentage of the paths within a program. A unique aspect in this study is that slicing was used in dif- ferent ways to determine its effect on the path count. In par- ticular, slicing was applied to each interesting statement individually to determine if that statement could be analyzed without suffering from path explosion. Results show that slic- ing is only effective if it can completely slices away a func- tion that suffers from path explosion. While most programs had several statements that resulted in short path counts, slicing was not adequate in eliminating path explosion occurrences. Looking into the tasks that suffer from path explosion, we find that functions that process input, produce stylized output, or parse strings or code often have signifi- Figure 1. Sample Control Flow Graph. cantly more paths than other functions. a reasonable amount of time. One technique to address path 1. Introduction explosion is to use program slicing [11, 20] to remove code not relevant to the property being verified. Static analysis is an important tool in software verifica- Consider the sample control flow graph in Figure 1. -

IBM Education Assistance for Z/OS V2R1
IBM Education Assistance for z/OS V2R1 Item: ASCII Unicode Option Element/Component: UNIX Shells and Utilities (S&U) Material is current as of June 2013 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option Agenda ■ Trademarks ■ Presentation Objectives ■ Overview ■ Usage & Invocation ■ Migration & Coexistence Considerations ■ Presentation Summary ■ Appendix Page 2 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Version Trademarks ■ See url http://www.ibm.com/legal/copytrade.shtml for a list of trademarks. Page 3 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Presentation Objectives ■ Introduce the features and benefits of the new z/OS UNIX Shells and Utilities (S&U) support for working with ASCII/Unicode files. Page 4 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Version Overview ■ Problem Statement –As a z/OS UNIX Shells & Utilities user, I want the ability to control the text conversion of input files used by the S&U commands. –As a z/OS UNIX Shells & Utilities user, I want the ability to run tagged shell scripts (tcsh scripts and SBCS sh scripts) under different SBCS locales. ■ Solution –Add –W filecodeset=codeset,pgmcodeset=codeset option on several S&U commands to enable text conversion – consistent with support added to vi and ex in V1R13. –Add –B option on several S&U commands to disable automatic text conversion – consistent with other commands that already have this override support. –Add new _TEXT_CONV environment variable to enable or disable text conversion. -

APEX® Compounding System List of Microsoft Windows 10 Patches That Have Been Verified for Use with APEX
APEX® Compounding System List of Microsoft Windows 10 Patches That Have Been Verified For Use with APEX 2021-02 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4601318) 2021-02 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4601392) 2021-02 .NET Core 3.1.12 Security Update for x64 Client Security Update for Windows 10 Version 1607 for x64-based Systems (KB4535680) Security Update for SQL Server 2016 Service Pack 2 CU (KB4583461) Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (UP TO Version 1.331.666.0) 2020-12 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4593226) Update for Microsoft Defender Antivirus antimalware platform - KB4052623 (UP TO Version 4.18.2011.6) 2020-11 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4586830) Windows Malicious Software Removal Tool x64 -UP TO v5.86 (KB890830) Intel - Ports - 2011.0.7.0 2020-10 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4580346) 2020-10 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4580325) 2020-09 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4577015) 2020-09 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4576750) 2020-08 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4571694) 2020-07 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4565912) 2020-07 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4565511) 2020-06 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4561600) 2020-06 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4561616) 2020-06 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4562561) B. -

An Introduction to Windows Operating System
EINAR KROGH AN INTRODUCTION TO WINDOWS OPERATING SYSTEM Download free eBooks at bookboon.com 2 An Introduction to Windows Operating System 2nd edition © 2017 Einar Krogh & bookboon.com ISBN 978-87-403-1935-4 Peer review by Høgskolelektor Lars Vidar Magnusson, Høgskolen i Østfold Download free eBooks at bookboon.com 3 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS CONTENTS Introduction 9 1 About Windows history 10 1.1 MS-DOS 10 1.2 The first versions of Windows 11 1.3 Windows NT 12 1.4 Windows versions based on Windows NT 13 1.5 Windows Server 15 1.6 Control Questions 17 2 The tasks of an operating system 18 2.1 About the construction of computers 19 2.2 Central tasks for an operating system 20 2.3 Control Questions 22 �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� www.discovermitas.comMaersk.com/Mitas �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� Maersk.com/Mitas Month 16 I wwasas a construction Month 16 supervisorI wwasas in a construction the North Sea supervisor in advising and the North Sea Real work helpinghe foremen advising and IInternationalnternationaal opportunities ��reeree wworkoro placements solves Real work problems helpinghe foremen IInternationalnternationaal opportunities ��reeree wworkoro placements solves problems Download free eBooks at bookboon.com Click on the ad to read more 4 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS 3 Some concepts and terms of the Windows operating system 23 3.1