Windows Server 2016 Security Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Logs & Event Analysis and Password Cracking
Logs & Event Analysis and Password Cracking MODULE 6 Page 1 of 29 Contents 6.1 Learning Objectives ............................................................................................................. 4 6.2 Introduction .......................................................................................................................... 4 6.3 Windows registry ................................................................................................................. 5 6.3.1 Registry and forensics ................................................................................................... 5 6.3.1.1 System information ................................................................................................ 5 6.4 Windows event log file ........................................................................................................ 9 6.4.1 Windows Event Log File Format .................................................................................. 9 6.4.2 Reading from Windows event log file ........................................................................ 11 6.4.3 Using Microsoft log parser ......................................................................................... 11 6.4.4 Understanding Windows user account management logs .......................................... 13 6.4.5 Understanding Windows file and other object Access sets ........................................ 14 6.4.6 Auditing policy change .............................................................................................. -

Analysis the Structure of SAM and Cracking Password Base on Windows Operating System
International Journal of Future Computer and Communication, Vol. 5, No. 2, April 2016 Analysis the Structure of SAM and Cracking Password Base on Windows Operating System Jiang Du and Jiwei Li latest Windows 10, the registry contains information that Abstract—Cracking Windows account password is critical to Windows continually references during operation, such as the forensic analyst. The general methods of decipher password profiles for each user, the applications installed on the include clean the password, guess by social engineering, computer and the types of documents, property sheet settings mathematical analyzing, exhaustive attacking, dictionary attacking and rainbow tables algorithm. This paper provides the of folders and application icons, what hardware exists on the details about the Security Account Manager(SAM) database system, and the ports that are being used [3]. On disk, the and describes how to get the user information from SAM and Windows registry is not only a large file but a set of discrete cracks account password of Windows 10 that the latest files called hives. Each hive is a hierarchical tree which operating system of Microsoft. identified by a root key to provide access to all sub-keys in the tree up to 512 levels deep. Index Terms—SAM, decipher password, crack password, Windows 10. III. SECURITY ACCOUNT MANAGER (SAM) I. INTRODUCTION Security Account Manager (SAM) is a database used to In the process of computer forensic the analyst need to store user account information, including password, account enter the Windows operating system by cracking windows groups, access rights, and special privileges in Windows account password to collect evidence at times. -

Lotus Notes and Domino R5.0 Security Infrastructure Revealed
CT6TPNAwhite.qxd 4/28/99 4:00 PM Page 1 Lotus Notes and Domino R5.0 Security Infrastructure Revealed Søren Peter Nielsen, Frederic Dahm, Marc Lüscher, Hidenobu Yamamoto, Fiona Collins, Brian Denholm, Suresh Kumar, John Softley International Technical Support Organization http://www.redbooks.ibm.com SG24-5341-00 44 Lotus Notes and Domino R5.0 Security Infrastructure Revealed SG24-5341-00 International Technical Support Organization Lotus Notes and Domino R5.0 Security Infrastructure Revealed May 1999 Take Note! Before using this information and the product it supports, be sure to read the general information in the Special Notices section at the back of this book. First Edition (May 1999) This edition applies to Lotus Domino Release 5.0. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. JN9B Building 045 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © International Business Machines Corporation 1999. All rights reserved. Note to U.S. Government Users: Documentation related to restricted rights. Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Preface ....................... vii 2 What Is Lotus Domino? ........21 The Team That Wrote This Redbook ...... viii Domino R5.0 Server .................21 Comments Welcome ................. x Lotus QuickPlace .................21 1 Basic Security Concepts Domino Mail Server ...............22 Revealed ....................... 1 Domino Application Server ...........22 Important Terminology ............... 2 Domino Enterprise Server ............22 Computer System ................ -
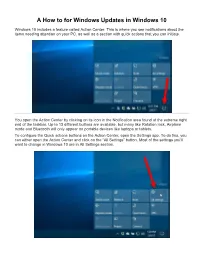
A How to for Windows Updates in Windows 10
A How to for Windows Updates in Windows 10 Windows 10 includes a feature called Action Center. This is where you see notifications about the items needing attention on your PC, as well as a section with quick actions that you can initiate. You open the Action Center by clicking on its icon in the Notification area found at the extreme right end of the taskbar. Up to 13 different buttons are available, but many like Rotation lock, Airplane mode and Bluetooth will only appear on portable devices like laptops or tablets. To configure the Quick actions buttons on the Action Center, open the Settings app. To do this, you can either open the Action Center and click on the “All Settings” button. Most of the settings you'll want to change in Windows 10 are in All Settings section. or you can open the Start menu and click the “Settings” button on the lower-left side of the menu. Windows settings is organized into various categories: System, Devices, Network & Internet, Personalization, Apps, Accounts, Time & language, Ease of Access, Privacy, and Update & security. You click on a category to view and change more settings for that category. Settings in Windows 10 – alternatively use Win () + I key combination. The Settings app from Windows 10 holds almost all the settings governing the way your computer or device works. The traditional way of getting to one setting or to another is to open the appropriate settings category and browse through it until you find what you’re looking for. The Setting app from Windows 10 is very well organized, a lot better than the old Control Panel used to be. -

Microsoft Windows NT
Microsoft Windows NT Securing Windows NT Installation October 23, 1997 Microsoft Corporation Contents Abstract Establishing Computer Security Levels of Security Off-the-Shelf vs. Custom Software Minimal Security Standard Security High-Level Security High-Level Software Security Considerations User Rights Protecting Files and Directories Protecting the Registry Secure EventLog Viewing Secure Print Driver Installation The Schedule Service (AT Command) Secure File Sharing FTP Service NetBios Access From Internet Hiding the Last User Name Restricting the Boot Process Allowing Only Logged-On Users to Shut Down the Computer Controlling Access to Removable Media Securing Base System Objects Enabling System Auditing Enhanced Protection for Security Accounts Manager Database Restricting Anonymous network access to Registry Restricting Anonymous network access to lookup account names and groups and network shares Enforcing strong user passwords Disabling LanManager Password Hash Support Wiping the System Page File during clean system shutdown Disable Caching of Logon Credentials during interactive logon. C2 Security Evaluation vs. Certification Setting up a C2-compliant System Abstract Microsoft® Windows NT® operating system provides a rich set of security features. However, the default out-of-the-box configuration is highly relaxed, especially on the Workstation product. This is because the operating system is sold as a shrink-wrapped product with an assumption that an average customer may not want to worry about a highly restrained but secure system on their desktop. This assumption has changed over the years as Windows NT gains popularity largely because of its security features. Microsoft is investigating a better secured default configuration for future releases. In the meantime, this white paper talks about various security issues with respect to configuring all Windows NT version 4.0 OS products for a highly secure computing environment. -

Professor Messer's
Professor Messer’s CompTIA 220-1002 Core 2 A+ Course Notes James “Professor” Messer http://www.ProfessorMesser.com Professor Messer’s CompTIA 220-1002 Core 2 A+ Course Notes Written by James “Professor” Messer Copyright © 2018 by Messer Studios, LLC http://www.ProfessorMesser.com All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without written permission from the publisher. First Edition: September 2018 Trademark Acknowledgments All product names and trademarks are the property of their respective owners, and are in no way associated or affiliated with Messer Studios LLC. “Professor Messer” is a registered trademark of Messer Studios LLC. “CompTIA” and “A+” are registered trademarks of CompTIA, Inc. Warning and Disclaimer This book is designed to provide information about the CompTIA 220-1002 A+ certification exam. However, there may be typographical and/or content errors. Therefore, this book should serve only as a general guide and not as the ultimate source of subject information. The author shall have no liability or responsibility to any person or entity regarding any loss or damage incurred, or alleged to have incurred, directly or indirectly, by the information contained in this book. Contents 1.0 - Operating Systems 1 1.1 - Operating Systems Overview 1 1.2 - An Overview of Windows 7 2 1.2 - An Overview of Windows 8 and 8.1 3 1.2 - An Overview of Windows 10 4 1.2 -

APEX® Compounding System List of Microsoft Windows 10 Patches That Have Been Verified for Use with APEX
APEX® Compounding System List of Microsoft Windows 10 Patches That Have Been Verified For Use with APEX 2021-02 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4601318) 2021-02 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4601392) 2021-02 .NET Core 3.1.12 Security Update for x64 Client Security Update for Windows 10 Version 1607 for x64-based Systems (KB4535680) Security Update for SQL Server 2016 Service Pack 2 CU (KB4583461) Security Intelligence Update for Microsoft Defender Antivirus - KB2267602 (UP TO Version 1.331.666.0) 2020-12 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4593226) Update for Microsoft Defender Antivirus antimalware platform - KB4052623 (UP TO Version 4.18.2011.6) 2020-11 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4586830) Windows Malicious Software Removal Tool x64 -UP TO v5.86 (KB890830) Intel - Ports - 2011.0.7.0 2020-10 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4580346) 2020-10 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4580325) 2020-09 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4577015) 2020-09 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4576750) 2020-08 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4571694) 2020-07 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4565912) 2020-07 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4565511) 2020-06 Security Update for Adobe Flash Player for Windows 10 Version 1607 for x64-based Systems (KB4561600) 2020-06 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4561616) 2020-06 Servicing Stack Update for Windows 10 Version 1607 for x64-based Systems (KB4562561) B. -

An Introduction to Windows Operating System
EINAR KROGH AN INTRODUCTION TO WINDOWS OPERATING SYSTEM Download free eBooks at bookboon.com 2 An Introduction to Windows Operating System 2nd edition © 2017 Einar Krogh & bookboon.com ISBN 978-87-403-1935-4 Peer review by Høgskolelektor Lars Vidar Magnusson, Høgskolen i Østfold Download free eBooks at bookboon.com 3 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS CONTENTS Introduction 9 1 About Windows history 10 1.1 MS-DOS 10 1.2 The first versions of Windows 11 1.3 Windows NT 12 1.4 Windows versions based on Windows NT 13 1.5 Windows Server 15 1.6 Control Questions 17 2 The tasks of an operating system 18 2.1 About the construction of computers 19 2.2 Central tasks for an operating system 20 2.3 Control Questions 22 �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� www.discovermitas.comMaersk.com/Mitas �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� Maersk.com/Mitas Month 16 I wwasas a construction Month 16 supervisorI wwasas in a construction the North Sea supervisor in advising and the North Sea Real work helpinghe foremen advising and IInternationalnternationaal opportunities ��reeree wworkoro placements solves Real work problems helpinghe foremen IInternationalnternationaal opportunities ��reeree wworkoro placements solves problems Download free eBooks at bookboon.com Click on the ad to read more 4 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS 3 Some concepts and terms of the Windows operating system 23 3.1 -
![[MS-SAMR-Diff]: Security Account Manager (SAM) Remote Protocol (Client- To-Server)](https://docslib.b-cdn.net/cover/6487/ms-samr-diff-security-account-manager-sam-remote-protocol-client-to-server-1206487.webp)
[MS-SAMR-Diff]: Security Account Manager (SAM) Remote Protocol (Client- To-Server)
[MS-SAMR-Diff]: Security Account Manager (SAM) Remote Protocol (Client- to-Server) Intellectual Property Rights Notice for Open Specifications Documentation . Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages, standards as well as overviews of the interaction among each of these technologies. Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you may make copies of it in order to develop implementations of the technologies described in the Open Specifications and may distribute portions of it in your implementations using these technologies or your documentation as necessary to properly document the implementation. You may also distribute in your implementation, with or without modification, any schema, IDL's, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications. No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. Patents. Microsoft has patents that may cover your implementations of the technologies described in the Open Specifications. Neither this notice nor Microsoft's delivery of the documentation grants any licenses under those or any other Microsoft patents. However, a given Open Specification may be covered by Microsoft Open Specification Promise or the Community Promise. If you would prefer a written license, or if the technologies described in the Open Specifications are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. Trademarks. -
March 2021 Abstract: Critical Or Security Patches – March 2021
BD Product Name: BD Pyxis™ IV Prep Date of Critical or Security Patches: March 2021 Abstract: Critical or Security Patches – March 2021 Microsoft® & Third-Party Patches BD has identified patches from Microsoft that have been identified as critical or security related for March 2021. These patches were not found to adversely affect BD products and will be applied according to customers’ service agreement. Customers that maintain patches independent of BD automated delivery should ensure the validated patches are installed on their BD systems as the acting responsible entity in order to maintain the correct security posture of the system(s). Patch Name Description Patch ID Notes 2021-03 Cumulative A security issue has been KB5000803 None Update for Windows identified in a Microsoft Server 2016 for x64- software product that could based Systems affect your system. You can help protect your system by installing this update from Microsoft. For a complete listing of the issues that are included in this update, 2021-01 Update for Install this update to resolve KB4589210 None Windows Server 2016 for issues in Windows. For a x64-based Systems complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article for more information. Windows Malicious After the download, this tool KB890830 None Software Removal Tool runs one time to check your x64 - v5.87 computer for infection by specific, prevalent malicious software (including Blaster, Sasser, and Mydoom) and helps remove any infection that is found. If an infection is found, the tool will display a status report the next time that you start your computer. -

What's New in Windows 10
Contents What's new in Windows 10 What's new in Windows 10, version 1903 What's new in Windows 10, version 1809 What's new in Windows 10, version 1803 What's new in Windows 10, version 1709 What's new in Windows 10, version 1703 What's new in Windows 10, version 1607 What's new in Windows 10, versions 1507 and 1511 What's new in Windows 10 5/21/2019 • 2 minutes to read • Edit Online Windows 10 provides IT professionals with advanced protection against modern security threats and comprehensive management and control over devices and apps, as well as flexible deployment, update, and support options. Learn about new features in Windows 10 for IT professionals, such as Windows Information Protection, Windows Hello, Device Guard, and more. In this section What's new in Windows 10, version 1903 What's new in Windows 10, version 1809 What's new in Windows 10, version 1803 What's new in Windows 10, version 1709 What's new in Windows 10, version 1703 What's new in Windows 10, version 1607 What's new in Windows 10, versions 1507 and 1511 Learn more Windows 10 release information Windows 10 update history Windows 10 content from Microsoft Ignite Compare Windows 10 Editions See also Windows 10 Enterprise LTSC Edit an existing topic using the Edit link What's new in Windows 10, version 1903 IT Pro content 6/18/2019 • 10 minutes to read • Edit Online Applies to Windows 10, version 1903 This article lists new and updated features and content that are of interest to IT Pros for Windows 10 version 1903, also known as the Windows 10 May 2019 Update. -

ASOC Security Bulletin
Advanced Security Operations Center Telelink Business Services www.tbs.tech Monthly Security Bulletin August 2021 This security bulletin is powered by Telelink’s Advanced Security Operations Center The modern cybersecurity threat landscape is constantly evolving. New vulnerabilities and zero-day attacks are discovered every day. The old Why Advanced Security Operations vulnerabilities still exist. The tools to exploit these vulnerabilities are Center (ASOC) by Telelink? applying more complex techniques. But are getting easier to use. • Delivered as a service, which Mitigating modern cyber threats require solutions for continuous guarantees fast implementation, monitoring, correlation, and behavior analysis that are expensive and clear responsibility in the require significant amount of time to be implemented. Moreover, many Supplier and ability to cancel the organizations struggle to hire and retain the expensive security experts contract on a monthly basis. needed to operate those solutions and provide value by defending the • Built utilizing state of the art organizations. leading vendor’s solutions. The ASOC by Telelink allows organizations get visibility, control, and • Can be sized to fit small, recommendations on improving their security posture for a fixed and medium and large business predictable monthly fee. needs. • No investment in infrastructure, team, trainings or required technology. • Flexible packages and add-ons that allow pay what you need approach. • Provided at a fraction of the cost of operating your own SOC. LITE