Vista and Activex Control
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

When Using the Wireless Function with a Windows Vista Computer 3. Computer Network Settings 1. Projector Settings 2. Computer IP
2. Computer IP address settings When using the wireless function with a Windows Vista computer 1 Select [Start] → [Network]. “Wireless Manager mobile edition 3.0”, which is stored on the CD-ROM that is provided, does not work when using the wireless function with a Windows Vista computer. “Wireless Manager mobile edition 3.0a” is a version that is compatible with Windows Vista. Use this version by downloading and installing it from the URL below. However, please be aware it will still not be possible to use the functions described below. URL: http://panasonic.co.jp/pavc/global/projector/download/ 2 Select [Network and Sharing Center]. Functions that cannot be used: • Easy wireless set up (automatic set up of the wireless network) • Sound transmission • Wireless prompter (secondary display transmission) • Selective area transmission • Check with your system administrator before performing the network settings with the procedures below. Select [Manage network connections]. If network settings have already been made for using the computer in a wireless 3 environment for a different purpose, and after changing the settings as described in these instructions you want to go back to using the computer for the original purpose, then remember to return the network settings to their previous condition. • See “Wireless Function Edition”, the Operating Instructions in the provided CD-ROM, for details on the projector network settings and the wireless function. 1. Projector settings 4 Right click the mouse and open the Select [MENU] → [WIRELESS] → [NETWORK], and change to [USER1]. Wireless Network Connection Properties. Default settings of USER1 DHCP OFF IP ADDRESS 192.168.10.100 SUBNETMASK 255.255.255.0 SSID Panasonic Projector MODE ADHOC Enter [TCP/IPv4] as the setting and press 5 [OK]. -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -
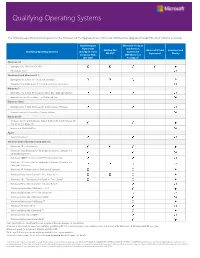
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 10 Download for Windows Vista Windows 10 Download for Windows Vista
windows 10 download for windows vista Windows 10 download for windows vista. Dummies has always stood for taking on complex concepts and making them easy to understand. Dummies helps everyone be more knowledgeable and confident in applying what they know. Whether it’s to pass that big test, qualify for that big promotion or even master that cooking technique; people who rely on dummies, rely on it to learn the critical skills and relevant information necessary for success. Learning Made Easy. Copyright © 2021 & Trademark by John Wiley & Sons, Inc. All rights reserved. Upgrade from Windows Vista to Windows 10 or 8.1? If you pay for 7 and then try for a free upgrade to 10 you may not get it as that offer expired in 2016. And 10 is cheaper than 7 to buy. But check everything first:: It depends on the hardware requirements of later operating systems and also whether the computer/laptop manufacturer supports and supplies drivers for the later operating systems as to whether it is possible or feasible to upgrade or not. There is no free upgrade from Vista to 7, 8.1 or 10. Follow these steps before you buy Windows 7; extended support Windows 7 SP1 until January 14, 2020 . Microsoft no longer sells 7; try amazon.com. Go to your Computer / Laptop Manufacturer's website and see if Windows 7 Drivers are available for your Make and Model Computer / Laptop. If not available, Windows 7 will not work correctly for you. Run the "Windows 7 Upgrade Advisor" Check to see if your System Specifications are compatible for Windows 7: "Windows 7 system requirements" Windows 7 Upgrade paths: Follow these steps before you buy and Upgrade (clean install) to Windows 8.1; extended support ends January 10, 2023 . -

Upgrading from Windows Vista to Windows 7
Upgrading from Windows Vista to Windows 7 Depending on your hardware and your current edition of Windows Vista, you can use the Upgrade option during Windows 7 installation to upgrade from Windows Vista to a corresponding or higher edition of Windows 7. Upgrading is the most convenient way to get Windows 7 on your computer, because it keeps your files, settings, and programs from Windows Vista in place. If you want to install Windows 7 on a netbook, purchasing Windows 7 online from the Microsoft Store (http://go.microsoft.com/fwlink/?LinkId=160999) is the easiest method. For more information, see Installing Windows 7 on a netbook (http://windows.microsoft.com/en-us/windows7/installing-windows- 7-on-a-netbook). Overview ....................................................................................................................................................... 2 Make sure that your programs and devices will work with Windows 7 ................................................... 2 Step 1: Which version of Windows 7 can I upgrade to? ............................................................................... 2 32-bit or 64-bit: Which version of Windows 7 to install? ......................................................................... 2 What if I can't choose the Upgrade option? ............................................................................................. 3 Step 2: Installing Windows 7 ........................................................................................................................ -

DMC2161 Installation Instructions on Microsoft Windows Vista Operating System
DMC2161 Installation instructions on Microsoft Windows Vista Operating System Lorex mCam software version 2.0.1 and above is compatible with Microsoft Windows Vista™ Operating System. The Video Driver for DMC2161 has been upgraded to work on Windows Vista and a dedicated driver directory “DVS Driver for Vista” is included on your installation CD and posted to the Lorex website (www.lorexcctv.com/support). While Lorex is continuing its efforts to upgrade the audio driver of the DMC2161 camera to work in a Windows Vista environment, mCam software does support audio using any external audio device (e.g. microphone) that is compatible with Windows Vista. Please note that both video and audio are fully supported in Windows XP. If during your installation on a Microsoft Windows Vista Operating System you get a message that your driver was not successfully installed OR Please follow the steps below to complete the installation: 1. Open the Device Manager: • Click Start / Settings / Control Panel / Device Manager • Click the ‘Continue’ Button on the ‘Microsoft Management Console’ window to continue. The Device Manager window will open. • A list of all System Devices will be displayed. Right Click on the “DVS Composite Device” listed under Universal Serial Bus Controls, and select “Update Driver Software” NOTE: If the device is not displayed, click on the ‘+’ beside the Universal Serial Bus Controllers option. 2. Browse for the Driver location www.lorexcctv.com Copyright © 2007 Lorex Technology Inc. 3. Click the ‘Browse’ button to select the Driver Location. This will typically be either the CD ROM drive, or the location where you saved the “DVS Driver for Vista” (.after downloading from the website) 4. -

Windows Powershell 1.0 Essentials
Windows PowerShell Essentials Windows PowerShell Essentials Windows PowerShell Essentials – Edition 1.0 © 2009 Payload Media. This eBook is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved. The content of this book is provided for informational purposes only. Neither the publisher nor the author offers any warranties or representation, express or implied, with regard to the accuracy of information contained in this book, nor do they accept any liability for any loss or damage arising from any errors or omissions. Find more eBooks at www.ebookfrenzy.com 2 © 2009 Payload Media Windows PowerShell Essentials Table of Contents Chapter 1. Installing Windows PowerShell ............................................................................... 10 1.1 Installing Windows PowerShell on Windows Server 2008 ............................................ 10 1.2 Performing a Windows Server 2008 PowerShell Command Line Installation ............... 10 1.3 Installing PowerShell on Windows Server 2003, XP and Vista Systems ........................ 11 Chapter 2. The Basics of the Windows PowerShell Interactive Shell ....................................... 13 2.1 The Windows PowerShell Command Prompt ................................................................ 13 2.2 PowerShell Command Line Editing Keys ........................................................................ 14 2.3 PowerShell Command Completion ............................................................................... -
Skype Old Version Download for Windows Vista Skype for Windows Vista
skype old version download for windows vista Skype for Windows Vista. Below there is a list of all versions of Skype for Windows Vista. Click on the version number to find out the details and download the full installer for free (note that only version 7.31 and higher are officially supported). Versions for 2017 Operating system Skype version Release date Windows Vista 7.36.0.150 9 may 2017 Windows Vista 7.35.0.103 5 may 2017 Windows Vista 7.35.0.102 2 may 2017 Windows Vista 7.35.0.101 11 april 2017 Windows Vista 7.34.0.103 3 april 2017 Windows Vista 7.34.0.102 22 march 2017 Windows Vista 7.33.0.105 14 march 2017 Windows Vista 7.33.0.104 20 february 2017 Windows Vista 7.32.0.104 9 february 2017 Windows Vista 7.32.0.103 30 january 2017 Windows Vista 7.31.0.104 10 january 2017. Versions for 2016 Operating system Skype version Release date Windows Vista 7.30.0.105 21 november 2016 Windows Vista 7.30.0.103 9 november 2016 Windows Vista 7.29.0.102 20 october 2016 Windows Vista 7.29.0.101 13 october 2016 Windows Vista 7.28.0.101 19 september 2016 Windows Vista 7.27.0.101 24 august 2016 Windows Vista 7.26.0.101 26 july 2016 Windows Vista 7.25.0.106 1 july 2016 Windows Vista 7.25.0.103 16 june 2016 Windows Vista 7.24.0.104 20 may 2016 Windows Vista 7.23.0.105 29 april 2016 Windows Vista 7.23.0.104 28 april 2016 Windows Vista 7.22.0.109 16 april 2016 Windows Vista 7.22.0.108 5 april 2016 Windows Vista 7.22.0.107 30 march 2016 Windows Vista 7.22.0.104 24 march 2016 Windows Vista 7.21.0.100 10 march 2016 Windows Vista 7.18.0.112 11 february 2016 Windows Vista 7.18.0.111 3 february 2016 Windows Vista 7.18.0.109 19 january 2016 Windows Vista 7.18.0.103 11 january 2016. -

Set up Your PC for Gaming
WINDOWS® GUIDE Set Up Your PC for Gaming IN THIS GUIDE Optimizing for Graphics and Speed Page 2 Instant Messaging While Gaming Page 11 Great Games and Accessories Page 12 What You’ll Need n Windows Live™ Messenger and a Windows Live ID n A computer with Windows Vista® Windows Guides is a library of easy-to-use guides that show you how to get more from your Windows experience. Share these guides with your friends and family. © 2008 Microsoft. All rights reserved. WINDOWS GUIDE Set Up Your PC For Gaming Optimizing for Graphics and Speed With more family-friendly features, a huge catalog of games, lots of new titles, and more powerful graphics technology than ever before, Windows Vista makes gaming on your PC easier and more fun. New enhancements make it easier to access, play, and manage your computer games while also experiencing next generation gaming graphics. UPDatE SOFtwaRE AND DRIVERS You can optimize your Windows Vista PC for gaming by making sure that you’re running the latest software and drivers, and that your PC hardware meets the demands of the games you play. Update Microsoft DirectX DirectX® is a Windows® software program that enables higher performance in graphics and sound when you’re playing games on your PC. Make sure that you have the latest version of DirectX so that you can take advantage of all of the new features. On a computer running Windows Vista, you should have DirectX 10 or later. Here’s how to check which version of DirectX is on your computer: 1. -

Bitlocker Introduction
BitLocker FAQ Introduction BitLocker Drive Encryption is a feature first introduced by Microsoft in Windows Vista, and helps to protect the confidential data on your computer from unauthorized access. BitLocker helps to ensure that sensitive information is not revealed should your computer be lost, stolen, or tampered with. 1. How does BitLocker protect my data? Unlike many other encryption products that protect individual files, BitLocker Drive Encryption utilizes advance encryption standards to protect your entire hard drive. BitLocker can also encrypt and protect secondary hard drives, as well as USB thumb drives, to ensure the data they store is not improperly accessed. In addition to data encryption, BitLocker is designed to utilize your computer's Trusted Platform Module (TPM) to monitor and protect critical firmware and operating system files from unauthorized tampering. If BitLocker detects that someone, or something, may be attempting to access your protected data, the encrypted drive is automatically locked and can only be accessed by providing a secret Recovery Key or password. 2. How can I use BitLocker to protect my Towson University computer? Certain departments within the University have been identified as "High-Risk" due to their work with, and access to, confidential data. If you work in one of these departments, your computer may already have BitLocker Drive Encryption or a comparable encryption product installed and enabled and no further action is required. If you are unsure if your computer is protected by BitLocker Drive Encryption, or if you work in a department not identified as "High-Risk" but wish to have your device encrypted, please contact the Faculty/Staff Help Center. -

AES-CBC + Elephant Diffuser a Disk Encryption Algorithm for Windows
AES-CBC + Elephant di®user A Disk Encryption Algorithm for Windows Vista Niels Ferguson Microsoft [email protected] August 2006 Abstract The Bitlocker Drive Encryption feature of Windows Vista poses an interesting set of secu- rity and performance requirements on the encryption algorithm used for the disk data. We discuss why no existing cipher satis¯es the requirements of this application and document our solution which consists of using AES in CBC mode with a dedicated di®user to improve the security against manipulation attacks. Copyright °c Microsoft Corp. Disclaimer This is a preliminary document and may be changed substantially prior to ¯nal commercial release of the software described. The information contained in this document represents the current view of Microsoft Cor- poration on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WAR- RANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intel- lectual property rights covering subject matter in this document. -

Absolute and Microsoft Bitlocker Maintaining Encryption Health with Absolute
ABSOLUTE AND MICROSOFT BITLOCKER MAINTAINING ENCRYPTION HEALTH WITH ABSOLUTE TECHNOTE THE CHALLENGES WITH MANAGING ENCRYPTION SOFTWARE Encryption is a critical security control measure for organizations to protect against unauthorized access to sensitive data. Many industry-specific and country/continent regulations require organizations to encrypt data, and more importantly prove that data encryption is healthy and functioning at the time of a security incident. This ability to prove encryption, and that data was not accessed post-incident, can save organizations from having to issue a data breach notification, mitigating both reputational and financial damage. While there are many variations of encryption solutions available, ranging from full-disk, to file and folder based and even self-encrypting drives, one of the more widely deployed solutions is Microsoft® BitLocker, a full-disk encryption product available with Windows. WHAT IS BITLOCKER? BitLocker Drive Encryption allows a user or administrator to encrypt all data stored on the Windows operating system volume and configured data volumes. BitLocker is supported on the following versions of Windows: • Ultimate and Enterprise editions of Windows 7 • Pro and Enterprise editions of Windows 8 and 8.1 • Pro, Enterprise and Education versions of Windows 10 • Windows Server 2008 and later BitLocker provides the most protection when used with a Trusted Platform Module (TPM). The TPM is a hardware component installed in devices by manufacturers. The TPM works with BitLocker to help protect user data by ensuring that the system components have not been tampered with and that the encrypted drive is located in the original computer. MAINTAINING BITLOCKER HEALTH While Encryption is a good data security practice and an important component of a defense-in-depth strategy, encryption can only protect data when the solution is properly configured and functional.