AES-CBC + Elephant Diffuser a Disk Encryption Algorithm for Windows
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Operating System Boot from Fully Encrypted Device
Masaryk University Faculty of Informatics Operating system boot from fully encrypted device Bachelor’s Thesis Daniel Chromik Brno, Fall 2016 Replace this page with a copy of the official signed thesis assignment and the copy of the Statement of an Author. Declaration Hereby I declare that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Daniel Chromik Advisor: ing. Milan Brož i Acknowledgement I would like to thank my advisor, Ing. Milan Brož, for his guidance and his patience of a saint. Another round of thanks I would like to send towards my family and friends for their support. ii Abstract The goal of this work is description of existing solutions for boot- ing Linux and Windows from fully encrypted devices with Secure Boot. Before that, though, early boot process and bootloaders are de- scribed. A simple Linux distribution is then set up to boot from a fully encrypted device. And lastly, existing Windows encryption solutions are described. iii Keywords boot process, Linux, Windows, disk encryption, GRUB 2, LUKS iv Contents 1 Introduction ............................1 1.1 Thesis goals ..........................1 1.2 Thesis structure ........................2 2 Boot Process Description ....................3 2.1 Early Boot Process ......................3 2.2 Firmware interfaces ......................4 2.2.1 BIOS – Basic Input/Output System . .4 2.2.2 UEFI – Unified Extended Firmware Interface .5 2.3 Partitioning tables ......................5 2.3.1 MBR – Master Boot Record . -

When Using the Wireless Function with a Windows Vista Computer 3. Computer Network Settings 1. Projector Settings 2. Computer IP
2. Computer IP address settings When using the wireless function with a Windows Vista computer 1 Select [Start] → [Network]. “Wireless Manager mobile edition 3.0”, which is stored on the CD-ROM that is provided, does not work when using the wireless function with a Windows Vista computer. “Wireless Manager mobile edition 3.0a” is a version that is compatible with Windows Vista. Use this version by downloading and installing it from the URL below. However, please be aware it will still not be possible to use the functions described below. URL: http://panasonic.co.jp/pavc/global/projector/download/ 2 Select [Network and Sharing Center]. Functions that cannot be used: • Easy wireless set up (automatic set up of the wireless network) • Sound transmission • Wireless prompter (secondary display transmission) • Selective area transmission • Check with your system administrator before performing the network settings with the procedures below. Select [Manage network connections]. If network settings have already been made for using the computer in a wireless 3 environment for a different purpose, and after changing the settings as described in these instructions you want to go back to using the computer for the original purpose, then remember to return the network settings to their previous condition. • See “Wireless Function Edition”, the Operating Instructions in the provided CD-ROM, for details on the projector network settings and the wireless function. 1. Projector settings 4 Right click the mouse and open the Select [MENU] → [WIRELESS] → [NETWORK], and change to [USER1]. Wireless Network Connection Properties. Default settings of USER1 DHCP OFF IP ADDRESS 192.168.10.100 SUBNETMASK 255.255.255.0 SSID Panasonic Projector MODE ADHOC Enter [TCP/IPv4] as the setting and press 5 [OK]. -

Self-Encrypting Deception: Weaknesses in the Encryption of Solid State Drives
Self-encrypting deception: weaknesses in the encryption of solid state drives Carlo Meijer Bernard van Gastel Institute for Computing and Information Sciences School of Computer Science Radboud University Nijmegen Open University of the Netherlands [email protected] and Institute for Computing and Information Sciences Radboud University Nijmegen Bernard.vanGastel@{ou.nl,ru.nl} Abstract—We have analyzed the hardware full-disk encryption full-disk encryption. Full-disk encryption software, especially of several solid state drives (SSDs) by reverse engineering their those integrated in modern operating systems, may decide to firmware. These drives were produced by three manufacturers rely solely on hardware encryption in case it detects support between 2014 and 2018, and are both internal models using the SATA and NVMe interfaces (in a M.2 or 2.5" traditional form by the storage device. In case the decision is made to rely on factor) and external models using the USB interface. hardware encryption, typically software encryption is disabled. In theory, the security guarantees offered by hardware encryp- As a primary example, BitLocker, the full-disk encryption tion are similar to or better than software implementations. In software built into Microsoft Windows, switches off software reality, we found that many models using hardware encryption encryption and completely relies on hardware encryption by have critical security weaknesses due to specification, design, and implementation issues. For many models, these security default if the drive advertises support. weaknesses allow for complete recovery of the data without Contribution. This paper evaluates both internal and external knowledge of any secret (such as the password). -

Zenworks 2017 Update 4 Troubleshooting Full Disk Encryption January 2019
ZENworks 2017 Update 4 Troubleshooting Full Disk Encryption January 2019 This document provides troubleshooting guidelines for common problems related to ZENworks Full Disk Encryption. If, after completing the troubleshooting steps, the problem is not resolved, you should contact Technical Support (https://www.novell.com/support/) for additional help. 1 Windows PE Emergency Recovery Disk (ERD) is not working Make sure you have installed the correct WAIK architecture (32-bit vs 64-bit) (Windows 7 only) If you manually created the ERD, use the PowerShell script provided in the Cool Solutions “Windows Powershell script to create a Windows PE emergency recovery disk for ZENworks Full Disk Encryption” article. Try creating the ERD using the ADK for Windows instead of Windows AIK. See “Creating a Windows PE Emergency Recovery Disk” in the ZENworks Full Disk Encryption Emergency Recovery Reference. Try burning the ERD to a DVD rather than a CD. 2 Issues with PBA login or boot sequence After pre-boot authentication occurs, the BIOS or UEFI settings must be correctly set for Windows. With unusual DMI hardware configurations, the standard ZENworks PBA boot method and Linux kernel configuration used to provide the BIOS settings, might not work, resulting in hardware that does not function correctly or is not recognized by Windows. Beginning in ZENworks 2017 Update 2, the Full Disk Encryption Agent includes DMI menu options to repair the boot sequence for issues relating to these DMI configurations. This menu is accessible by using the Ctrl + G keyboard command at a brief point when Full Disk Encryption is shown during a device restart. -

Disk Encryption with 100Gbe Crypto Accelerator
Disk Encryption with 100GbE Crypto Accelerator Chelsio T6 vs. Intel AES-NI vs. Software Enabled Encryption Executive Summary Chelsio Crypto Accelerator is a co-processor designed specifically to perform computationally intensive cryptographic operations more efficiently than general-purpose CPUs. Servers with system load, comprising of cryptographic operations, see great performance improvement by offloading crypto operations on to the Chelsio Unified Wire adapter. Chelsio’s solution uses the standard crypto API framework provided by the operating system and enables the offloading of crypto operations to the adapter. This paper showcases the disk encryption acceleration capabilities of Chelsio T6 adapters by comparing its performance with Intel AES-NI and software encryption. Chelsio solution excels with 100Gbps Crypto rate performance for both encryption and decryption with less than 50% CPU usage. Chelsio’s T6 encryption solution assures complete data protection to datacenters, while providing substantial savings on CPU and memory. Chelsio Disk Encryption Offload The Terminator 6 (T6) ASIC from Chelsio Communications, Inc. is a sixth generation, high performance 1/10/25/40/50/100Gbps unified wire engine which offers crypto offload capability for AES and SHA variants. Chelsio’s disk encryption solution is a special case of data at rest protection where the storage media is a sector-addressable device. Chelsio offloads the AES-XTS mode, which is designed for encrypting data stored on hard disks where there is no additional space for an integrity field. AES-XTS builds on the security of AES by protecting the storage device from many dictionary and copy/paste attacks. Chelsio crypto driver registers with the kernel crypto framework with high priority and ensures that any disk encryption request is offloaded and processed by T6 adapter. -

Speeding up Linux Disk Encryption Ignat Korchagin @Ignatkn $ Whoami
Speeding Up Linux Disk Encryption Ignat Korchagin @ignatkn $ whoami ● Performance and security at Cloudflare ● Passionate about security and crypto ● Enjoy low level programming @ignatkn Encrypting data at rest The storage stack applications @ignatkn The storage stack applications filesystems @ignatkn The storage stack applications filesystems block subsystem @ignatkn The storage stack applications filesystems block subsystem storage hardware @ignatkn Encryption at rest layers applications filesystems block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers applications filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers applications ecryptfs, ext4 encryption or fscrypt filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Encryption at rest layers DBMS, PGP, OpenSSL, Themis applications ecryptfs, ext4 encryption or fscrypt filesystems LUKS/dm-crypt, BitLocker, FileVault block subsystem SED, OPAL storage hardware @ignatkn Storage hardware encryption Pros: ● it’s there ● little configuration needed ● fully transparent to applications ● usually faster than other layers @ignatkn Storage hardware encryption Pros: ● it’s there ● little configuration needed ● fully transparent to applications ● usually faster than other layers Cons: ● no visibility into the implementation ● no auditability ● sometimes poor security https://support.microsoft.com/en-us/help/4516071/windows-10-update-kb4516071 @ignatkn Block -

No More Excuses: Windows 7 Makes It Easy to Manage Computer Power
• Products that earn the ENERGY STAR® prevent greenhouse gas emissions by meeting strict energy efficiency guidelines set by the U.S. Environmental Protection Agency and the U.S. Department of Energy. www.energy star.gov NO MORE EXCUSES: WINDOWS 7 MAKES IT EASY TO MANAGE COMPUTER POWER CONSUMPTION ORGANIZATION-WIDE Here’s how you can take advantage of Windows 7’s new power management features The University of Wisconsin at Oshkosh is no stranger to the idea of sustainability. In 2003 it became the first university in the state to join the Environmental Protection Agency’s Green Power Partnership. Its green initiatives also earned the university high marks from the Sierra Club, which ranked the university nationally in its Cool Schools survey. Given this commitment to green, it’s no surprise that the university first deployed computer power management back in 2005, and that it was one of the first Energy Star power management success stories. At that time, the University’s computers ran the Windows XP and Windows 2000 operating systems, neither of which included native tools for the central administration of power management features. To implement power management settings on these machines, the University used third-party software from ENERGY STAR called EZ GPO. For detailed information and resources concerning Now that Windows 7 has CPM client management features built in, it’s much the power management of easier to administer power management. This case study will show you how the University of Wisconsin at Oshkosh took full advantage of computer power PCs running Windows XP, management features on Windows Vista and Windows 7 clients managed by please see the ENERGY STAR Windows Server 2008. -

The Growing Impact of Full Disk Encryption on Digital Forensics
digital investigation 8 (2011) 129e134 Available online at www.sciencedirect.com journal homepage: www.elsevier.com/locate/diin The growing impact of full disk encryption on digital forensics Eoghan Casey a,*, Geoff Fellows b, Matthew Geiger c, Gerasimos Stellatos d a cmdLabs, 1101 E. 33rd Street, Suite C301, Baltimore, MD 21218, United States b LG Training Partnership, United Kingdom c CERT, United States d CACI International, United States article info abstract Article history: The increasing use of full disk encryption (FDE) can significantly hamper digital investi- Received 16 March 2011 gations, potentially preventing access to all digital evidence in a case. The practice of Received in revised form shutting down an evidential computer is not an acceptable technique when dealing with 17 September 2011 FDE or even volume encryption because it may result in all data on the device being Accepted 24 September 2011 rendered inaccessible for forensic examination. To address this challenge, there is a pressing need for more effective on-scene capabilities to detect and preserve encryption Keywords: prior to pulling the plug. In addition, to give digital investigators the best chance of Digital forensics obtaining decrypted data in the field, prosecutors need to prepare search warrants with Full disk encryption FDE in mind. This paper describes how FDE has hampered past investigations, and how Hard drive encryption circumventing FDE has benefited certain cases. This paper goes on to provide guidance for Volatile data gathering items at the crime scene that may be useful for accessing encrypted data, and for Memory forensics performing on-scene forensic acquisitions of live computer systems. -

The Future of Digital Forensics
Royal Holloway Information Security Thesis Series | The future of digital forensics The future of digital forensics Investigators have three avenues of attack to use when tackling the complexities of full disk encryption by Nia Catlin, MSc in information security (Royal Holloway) and Lorenzo Cavallaro, ISG, Royal Holloway THINKSTOCK Royal Holloway Information Security Thesis Series | The future of digital forensics The future of digital forensics in the era of full disk encryption Full disk encryption presents a theoretically insurmountable challenge for digital forensics, but authorities still have three avenues of attack for attempting to analyse protected devices. Anti-forensic countermeasures pose a developing challenge, however by Nia Catlin and Lorenzo Cavallaro In the past, forensics relied on artifacts left behind on a suspect’s computer, an intimate knowledge of all the nooks and crannies in which incriminating evidence may be hidden, the tendency of criminals to fail even to attempt to assume they will not be caught, and the failure of criminals to cover their tracks. Unfortunately for digital forensic investigators, their work constitutes a physical security breach, and the use of full disk encryption can be as effective at preventing them carrying out that work as it is at preventing a laptop thief from stealing passwords. The severe consequences of the exposure of corporate and customer data have led to the development of user-friendly and very secure full disk encryption. Moreover, the fear of device theft has led to its widening adoption. Most of the encryption algorithms – when used correctly – are considered unbroken for practical purposes, so authorities trying to analyse such a protected device are left with three avenues of attack: key search, live forensic acquisition and forced key disclosure. -

Dell EMC Unity: Data at Rest Encryption a Detailed Review
Technical White Paper Dell EMC Unity: Data at Rest Encryption A Detailed Review Abstract This white paper explains the Data at Rest Encryption feature, which provides controller-based encryption of data stored on Dell EMC™ Unity storage systems to protect against unauthorized access to lost or stolen drives or system. The encryption technology as well as its implementation on Dell EMC Unity storage systems are discussed. June 2021 H15090.6 Revisions Revisions Date Description May 2016 Initial release – Unity OE 4.0 July 2017 Updated for Unity OE 4.2 June 2021 Template and format updates. Updated for Unity OE 5.1 Acknowledgments Author: Ryan Poulin The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. This document may contain certain words that are not consistent with Dell's current language guidelines. Dell plans to update the document over subsequent future releases to revise these words accordingly. This document may contain language from third party content that is not under Dell's control and is not consistent with Dell's current guidelines for Dell's own content. When such third party content is updated by the relevant third parties, this document will be revised accordingly. Copyright © 2016-2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. -
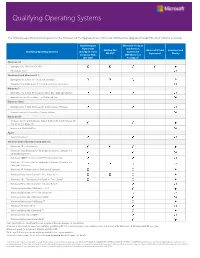
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 10 Download for Windows Vista Windows 10 Download for Windows Vista
windows 10 download for windows vista Windows 10 download for windows vista. Dummies has always stood for taking on complex concepts and making them easy to understand. Dummies helps everyone be more knowledgeable and confident in applying what they know. Whether it’s to pass that big test, qualify for that big promotion or even master that cooking technique; people who rely on dummies, rely on it to learn the critical skills and relevant information necessary for success. Learning Made Easy. Copyright © 2021 & Trademark by John Wiley & Sons, Inc. All rights reserved. Upgrade from Windows Vista to Windows 10 or 8.1? If you pay for 7 and then try for a free upgrade to 10 you may not get it as that offer expired in 2016. And 10 is cheaper than 7 to buy. But check everything first:: It depends on the hardware requirements of later operating systems and also whether the computer/laptop manufacturer supports and supplies drivers for the later operating systems as to whether it is possible or feasible to upgrade or not. There is no free upgrade from Vista to 7, 8.1 or 10. Follow these steps before you buy Windows 7; extended support Windows 7 SP1 until January 14, 2020 . Microsoft no longer sells 7; try amazon.com. Go to your Computer / Laptop Manufacturer's website and see if Windows 7 Drivers are available for your Make and Model Computer / Laptop. If not available, Windows 7 will not work correctly for you. Run the "Windows 7 Upgrade Advisor" Check to see if your System Specifications are compatible for Windows 7: "Windows 7 system requirements" Windows 7 Upgrade paths: Follow these steps before you buy and Upgrade (clean install) to Windows 8.1; extended support ends January 10, 2023 .