New Crypto Currency Mining Malware Also Disables Security Services
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BUGS in the SYSTEM a Primer on the Software Vulnerability Ecosystem and Its Policy Implications
ANDI WILSON, ROSS SCHULMAN, KEVIN BANKSTON, AND TREY HERR BUGS IN THE SYSTEM A Primer on the Software Vulnerability Ecosystem and its Policy Implications JULY 2016 About the Authors About New America New America is committed to renewing American politics, Andi Wilson is a policy analyst at New America’s Open prosperity, and purpose in the Digital Age. We generate big Technology Institute, where she researches and writes ideas, bridge the gap between technology and policy, and about the relationship between technology and policy. curate broad public conversation. We combine the best of With a specific focus on cybersecurity, Andi is currently a policy research institute, technology laboratory, public working on issues including encryption, vulnerabilities forum, media platform, and a venture capital fund for equities, surveillance, and internet freedom. ideas. We are a distinctive community of thinkers, writers, researchers, technologists, and community activists who Ross Schulman is a co-director of the Cybersecurity believe deeply in the possibility of American renewal. Initiative and senior policy counsel at New America’s Open Find out more at newamerica.org/our-story. Technology Institute, where he focuses on cybersecurity, encryption, surveillance, and Internet governance. Prior to joining OTI, Ross worked for Google in Mountain About the Cybersecurity Initiative View, California. Ross has also worked at the Computer The Internet has connected us. Yet the policies and and Communications Industry Association, the Center debates that surround the security of our networks are for Democracy and Technology, and on Capitol Hill for too often disconnected, disjointed, and stuck in an Senators Wyden and Feingold. unsuccessful status quo. -

How to Analyze the Cyber Threat from Drones
C O R P O R A T I O N KATHARINA LEY BEST, JON SCHMID, SHANE TIERNEY, JALAL AWAN, NAHOM M. BEYENE, MAYNARD A. HOLLIDAY, RAZA KHAN, KAREN LEE How to Analyze the Cyber Threat from Drones Background, Analysis Frameworks, and Analysis Tools For more information on this publication, visit www.rand.org/t/RR2972 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-1-9774-0287-5 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2020 RAND Corporation R® is a registered trademark. Cover design by Rick Penn-Kraus Cover images: drone, Kadmy - stock.adobe.com; data, Getty Images. Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. Support RAND Make a tax-deductible charitable contribution at www.rand.org/giving/contribute www.rand.org Preface This report explores the security implications of the rapid growth in unmanned aerial systems (UAS), focusing specifically on current and future vulnerabilities. -

The CLASP Application Security Process
The CLASP Application Security Process Secure Software, Inc. Copyright (c) 2005, Secure Software, Inc. The CLASP Application Security Process The CLASP Application Security Process TABLE OF CONTENTS CHAPTER 1 Introduction 1 CLASP Status 4 An Activity-Centric Approach 4 The CLASP Implementation Guide 5 The Root-Cause Database 6 Supporting Material 7 CHAPTER 2 Implementation Guide 9 The CLASP Activities 11 Institute security awareness program 11 Monitor security metrics 12 Specify operational environment 13 Identify global security policy 14 Identify resources and trust boundaries 15 Identify user roles and resource capabilities 16 Document security-relevant requirements 17 Detail misuse cases 18 Identify attack surface 19 Apply security principles to design 20 Research and assess security posture of technology solutions 21 Annotate class designs with security properties 22 Specify database security configuration 23 Perform security analysis of system requirements and design (threat modeling) 24 Integrate security analysis into source management process 25 Implement interface contracts 26 Implement and elaborate resource policies and security technologies 27 Address reported security issues 28 Perform source-level security review 29 Identify, implement and perform security tests 30 The CLASP Application Security Process i Verify security attributes of resources 31 Perform code signing 32 Build operational security guide 33 Manage security issue disclosure process 34 Developing a Process Engineering Plan 35 Business objectives 35 Process -

Threats and Vulnerabilities in Federation Protocols and Products
Threats and Vulnerabilities in Federation Protocols and Products Teemu Kääriäinen, CSSLP / Nixu Corporation OWASP Helsinki Chapter Meeting #30 October 11, 2016 Contents • Federation Protocols: OpenID Connect and SAML 2.0 – Basic flows, comparison between the protocols • OAuth 2.0 and OpenID Connect Vulnerabilities and Best Practices – Background for OAuth 2.0 security criticism, vulnerabilities related discussion and publicly disclosed vulnerabilities, best practices, JWT, authorization bypass vulnerabilities, mobile application integration. • SAML 2.0 Vulnerabilities and Best Practices – Best practices, publicly disclosed vulnerabilities • OWASP Top Ten in Access management solutions – Focus on Java deserialization vulnerabilites in different commercial and open source access management products • Forgerock OpenAM, Gluu, CAS, PingFederate 7.3.0 Admin UI, Oracle ADF (Oracle Identity Manager) Federation Protocols: OpenID Connect and SAML 2.0 • OpenID Connect is an emerging technology built on OAuth 2.0 that enables relying parties to verify the identity of an end-user in an interoperable and REST-like manner. • OpenID Connect is not just about authentication. It is also about authorization, delegation and API access management. • Reasons for services to start using OpenID Connect: – Ease of integration. – Ability to integrate client applications running on different platforms: single-page app, web, backend, mobile, IoT. – Allowing 3rd party integrations in a secure, interoperable and scalable manner. • OpenID Connect is proven to be secure and mature technology: – Solves many of the security issues that have been an issue with OAuth 2.0. • OpenID Connect and OAuth 2.0 are used frequently in social login scenarios: – E.g. Google and Microsoft Account are OpenID Connect Identity Providers. Facebook is an OAuth 2.0 authorization server. -

Fuzzing with Code Fragments
Fuzzing with Code Fragments Christian Holler Kim Herzig Andreas Zeller Mozilla Corporation∗ Saarland University Saarland University [email protected] [email protected] [email protected] Abstract JavaScript interpreter must follow the syntactic rules of JavaScript. Otherwise, the JavaScript interpreter will re- Fuzz testing is an automated technique providing random ject the input as invalid, and effectively restrict the test- data as input to a software system in the hope to expose ing to its lexical and syntactic analysis, never reaching a vulnerability. In order to be effective, the fuzzed input areas like code transformation, in-time compilation, or must be common enough to pass elementary consistency actual execution. To address this issue, fuzzing frame- checks; a JavaScript interpreter, for instance, would only works include strategies to model the structure of the de- accept a semantically valid program. On the other hand, sired input data; for fuzz testing a JavaScript interpreter, the fuzzed input must be uncommon enough to trigger this would require a built-in JavaScript grammar. exceptional behavior, such as a crash of the interpreter. Surprisingly, the number of fuzzing frameworks that The LangFuzz approach resolves this conflict by using generate test inputs on grammar basis is very limited [7, a grammar to randomly generate valid programs; the 17, 22]. For JavaScript, jsfunfuzz [17] is amongst the code fragments, however, partially stem from programs most popular fuzzing tools, having discovered more that known to have caused invalid behavior before. LangFuzz 1,000 defects in the Mozilla JavaScript engine. jsfunfuzz is an effective tool for security testing: Applied on the is effective because it is hardcoded to target a specific Mozilla JavaScript interpreter, it discovered a total of interpreter making use of specific knowledge about past 105 new severe vulnerabilities within three months of and common vulnerabilities. -

From Deficits and Dependence to Balanced Budgets and Independence
From Deficits and Dependence to Balanced Budgets and Independence The Arab Local Authorities’ Revenue Sources Michal Belikoff and Safa Agbaria Edited by Shirley Racah Jerusalem – Haifa – Nazareth April 2014 From Deficits and Dependence to Balanced Budgets and Independence The Arab Local Authorities’ Revenue Sources Michal Belikoff and Safa Agbaria Edited by Shirley Racah Jerusalem – Haifa – Nazareth April 2014 From Deficits and Dependence to Balanced Budgets and Independence The Arab Local Authorities’ Revenue Sources Research and writing: Michal Belikoff and Safa Ali Agbaria Editing: Shirley Racah Steering committee: Samah Elkhatib-Ayoub, Ron Gerlitz, Azar Dakwar, Mohammed Khaliliye, Abed Kanaaneh, Jabir Asaqla, Ghaida Rinawie Zoabi, and Shirley Racah Critical review and assistance with research and writing: Ron Gerlitz and Shirley Racah Academic advisor: Dr. Nahum Ben-Elia Co-directors of Sikkuy’s Equality Policy Department: Abed Kanaaneh and Shirley Racah Project director for Injaz: Mohammed Khaliliye Hebrew language editing: Naomi Glick-Ozrad Production: Michal Belikoff English: IBRT Jerusalem Graphic design: Michal Schreiber Printed by: Defus Tira This pamphlet has also been published in Arabic and Hebrew and is available online at www.sikkuy.org.il and http://injaz.org.il Published with the generous assistance of: The European Union This publication has been produced with the assistance of the European Union. Its contents are the sole responsibility of Sikkuy and Injaz and can in no way be taken to reflect the views of the European Union. The Moriah Fund UJA-Federation of New York The Jewish Federations of North America Social Venture Fund for Jewish-Arab Equality and Shared Society The Alan B. -

Paul Youn from Isec Partners
Where do security bugs come from? MIT 6.858 (Computer Systems Security), September 19th, 2012 Paul Youn • Technical Director, iSEC Partners • MIT 18/6-3 (‘03), M.Eng ’04 Tom Ritter • Security Consultant, iSEC Partners • (Research) Badass Agenda • What is a security bug? • Who is looking for security bugs? • Trust relationships • Sample of bugs found in the wild • Operation Aurora • Stuxnet • I’m in love with security; whatever shall I do? What is a Security Bug? • What is security? • Class participation: Tacos, Salsa, and Avocados (TSA) What is security? “A system is secure if it behaves precisely in the manner intended – and does nothing more” – Ivan Arce • Who knows exactly what a system is intended to do? Systems are getting more and more complex. • What types of attacks are possible? First steps in security: define your security model and your threat model Threat modeling: T.S.A. • Logan International Airport security goal #3: prevent banned substances from entering Logan • Class Participation: What is the threat model? • What are possible avenues for getting a banned substance into Logan? • Where are the points of entry? • Threat modeling is also critical, you have to know what you’re up against (many engineers don’t) Who looks for security bugs? • Engineers • Criminals • Security Researchers • Pen Testers • Governments • Hacktivists • Academics Engineers (create and find bugs) • Goals: • Find as many flaws as possible • Reduce incidence of exploitation • Thoroughness: • Need coverage metrics • At least find low-hanging fruit • Access: -

The National Left (First Draft) by Shmuel Hasfari and Eldad Yaniv
The National Left (First Draft) by Shmu'el Hasfari and Eldad Yaniv Open Source Center OSC Summary: A self-published book by Israeli playwright Shmu'el Hasfari and political activist Eldad Yaniv entitled "The National Left (First Draft)" bemoans the death of Israel's political left. http://www.fas.org/irp/dni/osc/israel-left.pdf Statement by the Authors The contents of this publication are the responsibility of the authors, who also personally bore the modest printing costs. Any part of the material in this book may be photocopied and recorded. It is recommended that it should be kept in a data-storage system, transmitted, or recorded in any form or by any electronic, optical, mechanical means, or otherwise. Any form of commercial use of the material in this book is permitted without the explicit written permission of the authors. 1. The Left The Left died the day the Six-Day War ended. With the dawn of the Israeli empire, the Left's sun sank and the Small [pun on Smol, the Hebrew word for Left] was born. The Small is a mark of Cain, a disparaging term for a collaborator, a lover of Arabs, a hater of Israel, a Jew who turns against his own people, not a patriot. The Small-ists eat pork on Yom Kippur, gobble shrimps during the week, drink espresso whenever possible, and are homos, kapos, artsy-fartsy snobs, and what not. Until 1967, the Left actually managed some impressive deeds -- it took control of the land, ploughed, sowed, harvested, founded the state, built the army, built its industry from scratch, fought Arabs, settled the land, built the nuclear reactor, brought millions of Jews here and absorbed them, and set up kibbutzim, moshavim, and agriculture. -

Designing New Operating Primitives to Improve Fuzzing Performance
Designing New Operating Primitives to Improve Fuzzing Performance Wen Xu Sanidhya Kashyap Changwoo Miny Taesoo Kim Georgia Institute of Technology Virginia Techy ABSTRACT from malicious attacks, various financial organizations and com- Fuzzing is a software testing technique that finds bugs by repeatedly munities, that implement and use popular software and OS kernels, injecting mutated inputs to a target program. Known to be a highly have invested major efforts on finding and fixing security bugsin practical approach, fuzzing is gaining more popularity than ever their products, and one such effort to finding bugs in applications before. Current research on fuzzing has focused on producing an and libraries is fuzzing. Fuzzing is a software-testing technique input that is more likely to trigger a vulnerability. that works by injecting randomly mutated input to a target pro- In this paper, we tackle another way to improve the performance gram. Compared with other bug-finding techniques, one of the of fuzzing, which is to shorten the execution time of each itera- primary advantages of fuzzing is that it ensures high throughput tion. We observe that AFL, a state-of-the-art fuzzer, slows down by with less manual efforts and pre-knowledge of the target software. 24× because of file system contention and the scalability of fork() In addition, it is one of the most practical approach to finding system call when it runs on 120 cores in parallel. Other fuzzers bugs in various critical software. For example, the state-of-the-art are expected to suffer from the same scalability bottlenecks inthat coverage-driven fuzzer, American Fuzzy Lop (AFL), has discovered they follow a similar design pattern. -

Return of Organization Exempt from Income
Return of Organization Exempt From Income Tax Form 990 Under section 501 (c), 527, or 4947( a)(1) of the Internal Revenue Code (except black lung benefit trust or private foundation) 2005 Department of the Treasury Internal Revenue Service ► The o rganization may have to use a copy of this return to satisfy state re porting requirements. A For the 2005 calendar year , or tax year be and B Check If C Name of organization D Employer Identification number applicable Please use IRS change ta Qachange RICA IS RAEL CULTURAL FOUNDATION 13-1664048 E; a11gne ^ci See Number and street (or P 0. box if mail is not delivered to street address) Room/suite E Telephone number 0jretum specific 1 EAST 42ND STREET 1400 212-557-1600 Instruo retum uons City or town , state or country, and ZIP + 4 F nocounwro memos 0 Cash [X ,camel ded On° EW YORK , NY 10017 (sped ► [l^PP°ca"on pending • Section 501 (Il)c 3 organizations and 4947(a)(1) nonexempt charitable trusts H and I are not applicable to section 527 organizations. must attach a completed Schedule A ( Form 990 or 990-EZ). H(a) Is this a group return for affiliates ? Yes OX No G Website : : / /AICF . WEBNET . ORG/ H(b) If 'Yes ,* enter number of affiliates' N/A J Organization type (deckonIyone) ► [ 501(c) ( 3 ) I (insert no ) ] 4947(a)(1) or L] 527 H(c) Are all affiliates included ? N/A Yes E__1 No Is(ITthis , attach a list) K Check here Q the organization' s gross receipts are normally not The 110- if more than $25 ,000 . -
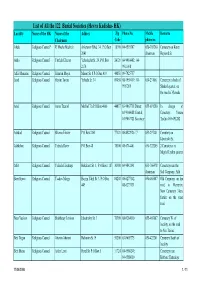
List of All the 122 Burial Societies (Hevra Kadisha- HK) Locality Name of the HK Name of the Addres Zip Phone No
List of All the 122 Burial Societies (Hevra Kadisha- HK) Locality Name of the HK Name of the Addres Zip Phone No. Mobile Remarks Chairman Code phone no. Afula Religious Council* R' Moshe Mashiah Arlozorov Blvd. 34, P.O.Box 18100 04-6593507 050-303260 Cemetery on Keren 2041 chairman Hayesod St. Akko Religious Council Yitzhak Elharar Yehoshafat St. 29, P.O.Box 24121 04-9910402; 04- 2174 9911098 Alfei Menashe Religious Council Shim'on Moyal Manor St. 8 P.O.Box 419 44851 09-7925757 Arad Religious Council Hayim Tovim Yehuda St. 34 89058 08-9959419; 08- 050-231061 Cemetery in back of 9957269 Shaked quarter, on the road to Massada Ariel Religious Council Amos Tzuriel Mish'ol 7/a P.O.Box 4066 44837 03-9067718 Direct; 055-691280 In charge of 03-9366088 Central; Cemetery: Yoram 03-9067721 Secretary Tzefira 055-691282 Ashdod Religious Council Shlomo Eliezer P.O.Box 2161 77121 08-8522926 / 7 053-297401 Cemetery on Jabotinski St. Ashkelon Religious Council Yehuda Raviv P.O.Box 48 78100 08-6714401 050-322205 2 Cemeteries in Migdal Tzafon quarter Atlit Religious Council Yehuda Elmakays Hakalanit St. 1, P.O.Box 1187 30300 04-9842141 053-766478 Cemetery near the chairman Salt Company, Atlit Beer Sheva Religious Council Yaakov Margy Hayim Yahil St. 3, P.O.Box 84208 08-6277142, 050-465887 Old Cemetery on the 449 08-6273131 road to Harzerim; New Cemetery 3 km. further on the same road Beer Yaakov Religious Council Shabbetay Levison Jabotinsky St. 3 70300 08-9284010 055-465887 Cemetery W. -

Empirical Analysis and Automated Classification of Security Bug Reports
Graduate Theses, Dissertations, and Problem Reports 2016 Empirical Analysis and Automated Classification of Security Bug Reports Jacob P. Tyo Follow this and additional works at: https://researchrepository.wvu.edu/etd Recommended Citation Tyo, Jacob P., "Empirical Analysis and Automated Classification of Security Bug Reports" (2016). Graduate Theses, Dissertations, and Problem Reports. 6843. https://researchrepository.wvu.edu/etd/6843 This Thesis is protected by copyright and/or related rights. It has been brought to you by the The Research Repository @ WVU with permission from the rights-holder(s). You are free to use this Thesis in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you must obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Thesis has been accepted for inclusion in WVU Graduate Theses, Dissertations, and Problem Reports collection by an authorized administrator of The Research Repository @ WVU. For more information, please contact [email protected]. Empirical Analysis and Automated Classification of Security Bug Reports Jacob P. Tyo Thesis submitted to the Benjamin M. Statler College of Engineering and Mineral Resources at West Virginia University in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering Katerina Goseva-Popstojanova, Ph.D., Chair Roy S. Nutter, Ph.D. Matthew C. Valenti, Ph.D. Lane Department of Computer Science and Electrical Engineering CONFIDENTIAL. NOT TO BE DISTRIBUTED. Morgantown, West Virginia 2016 Keywords: Cybersecurity, Machine Learning, Issue Tracking Systems, Text Mining, Text Classification Copyright 2016 Jacob P.