Available Here
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Basics of OS Upgrades
Basics of OS Upgrades Everything you need to prepare for macOS Big Sur and iOS 14 Apple OS upgrades are coming. Are you ready? Exciting new versions of macOS (for Mac), iPadOS (for iPad) and iOS (for iPhone) are heading to a device near you. Your job is simple. Get these features into the hands of users, all without disrupting workflows or slowing productivity. As most organizations know, this can often be easier said than done, especially when factoring in the speed at which Apple users like to upgrade. Now for the good news. At Jamf, we’ve been doing this for more than 17 years, and are here to provide step-by-step guidance for successful Apple upgrades — regardless if it is your first, fifth or 17th OS season. Why an Contrary to other ecosystems, a variety of devices and OS platforms with major new versions of Apple’s a single management solution. Without the Apple operating systems are released complications and cost of licensing, Apple’s annually. A combination of the user-initiated upgrades are easy for end users upgrade is simple upgrade path and $0 to carry out autonomously. This is one of the cost help drive industry-leading reasons Apple’s operating systems have the highest adoption rate of any ecosystem. different adoption rates for consumers. End users are so excited to access the This trend is further accelerated by Apple’s new features; yet, you’re responsible for vertical integration of hardware and software: maintaining security controls and an accurate any new Mac, iPad or iPhone will always systems inventory at all times. -

Ipad Benutzerhandbuch Für Ios 4.3 Software Inhalt
iPad Benutzerhandbuch Für iOS 4.3 Software Inhalt 9 Kapitel 1: Auf einen Blick 10 Tasten 12 Fach für Mikro-SIM-Karte 12 Home-Bildschirm 17 Multi-Touch-Bildschirm 19 Bildschirmtastatur 25 Kapitel 2: Einführung 25 Voraussetzungen 25 Konfigurieren des iPad 26 Synchronisieren mit iTunes 32 Herstellen der Internetverbindung 34 Hinzufügen von E-Mail-, Kontakt- und Kalender-Accounts 36 Trennen des iPad von Ihrem Computer 36 Anzeigen des Benutzerhandbuchs auf dem iPad 37 Batterie 38 Verwenden und Reinigen des iPad 40 Kapitel 3: Grundlagen 40 Verwenden von Apps 45 Drucken 48 Suchen 49 Verwenden von Bluetooth-Geräten 50 Dateifreigabe 51 Verwenden von AirPlay 52 Sicherheits- und Schutzfunktionen 54 Kapitel 4: Safari 54 Informationen über Safari 54 Anzeigen von Webseiten 58 Suchen im Internet 59 Lesezeichen 60 Weblinks 2 61 Kapitel 5: Mail 61 Informationen über Mail 61 Konfigurieren von E-Mail-Accounts 62 Senden von E-Mails 63 Abrufen und Lesen von E-Mails 66 Durchsuchen von E-Mails 67 Drucken von Nachrichten und Anhängen 68 Verwalten von E-Mails 69 Kapitel 6: Kamera 69 Informationen über Kamera 69 Aufnehmen von Fotos und Videos 71 Ansehen und Senden von Fotos und Videos 71 Trimmen von Videos 72 Laden von Fotos und Videos auf Ihren Computer 73 Kapitel 7: FaceTime 73 Informationen über FaceTime 74 Anmelden 75 Anrufen mit FaceTime 75 Während des Telefonats 77 Kapitel 8: Photo Booth 77 Informationen über Photo Booth 77 Auswählen eines Effekts 78 Aufnehmen eines Fotos 79 Anzeigen und Freigeben von Fotos 79 Laden von Fotos auf Ihren Computer 80 Kapitel -

2018 – Volume 6, Number
THE POPULAR CULTURE STUDIES JOURNAL VOLUME 6 NUMBER 2 & 3 2018 Editor NORMA JONES Liquid Flicks Media, Inc./IXMachine Managing Editor JULIA LARGENT McPherson College Assistant Editor GARRET L. CASTLEBERRY Mid-America Christian University Copy Editor KEVIN CALCAMP Queens University of Charlotte Reviews Editor MALYNNDA JOHNSON Indiana State University Assistant Reviews Editor JESSICA BENHAM University of Pittsburgh Please visit the PCSJ at: http://mpcaaca.org/the-popular-culture- studies-journal/ The Popular Culture Studies Journal is the official journal of the Midwest Popular and American Culture Association. Copyright © 2018 Midwest Popular and American Culture Association. All rights reserved. MPCA/ACA, 421 W. Huron St Unit 1304, Chicago, IL 60654 Cover credit: Cover Artwork: “Bump in the Night” by Brent Jones © 2018 Courtesy of Pixabay/Kellepics EDITORIAL ADVISORY BOARD ANTHONY ADAH PAUL BOOTH Minnesota State University, Moorhead DePaul University GARY BURNS ANNE M. CANAVAN Northern Illinois University Salt Lake Community College BRIAN COGAN ASHLEY M. DONNELLY Molloy College Ball State University LEIGH H. EDWARDS KATIE FREDICKS Florida State University Rutgers University ART HERBIG ANDREW F. HERRMANN Indiana University - Purdue University, Fort Wayne East Tennessee State University JESSE KAVADLO KATHLEEN A. KENNEDY Maryville University of St. Louis Missouri State University SARAH MCFARLAND TAYLOR KIT MEDJESKY Northwestern University University of Findlay CARLOS D. MORRISON SALVADOR MURGUIA Alabama State University Akita International -

A Walled Garden Turned Into a Rain Forest
A Walled Garden Turned Into a Rain Forest Pelle Snickars More than ten months after the iPhone was introduced, Lev Grossman in Time Magazine, reflected upon the most valuable invention of 2007. At first he could not make up his mind. Admittedly, he argued, there had been a lot written about the iPhone —and if truth be told, a massive amount of articles, extensive media coverage, hype, “and a lot of guff too.” Grossman hesitated: he confessed that he could not type on the iPhone; it was too slow, too expensive, and even too big. “It doesn’t support my work e- mail. It’s locked to AT&T. Steve Jobs secretly hates puppies. And—all together now— we’re sick of hearing about it!” Yet, when Grossman had finished with his litany of complains, the iPhone was nevertheless in his opinion, “the best thing invented this year.” He gave five reasons why this was the case. First of all, the iPhone had made design important for smartphones. At a time when most tech companies did not treat form seriously at all, Apple had made style a trademark of their seminal product. Of course, Apple had always knew that good design was as important as good technology, and the iPhone was therefore no exception. Still, it was something of a stylistic epitome, and to Grossman even “pretty”. Another of his reasons had to do with touch. Apple didn’t invent the touchscreen, but according to Grossman the company engineers had finally understood what to do with it. In short, Apple’s engineers used the touchscreen to sort of innovate past the GUI, which Apple once pioneered with the Mac, to create “a whole new kind of interface, a tactile one that gives users the illusion of actually physically manipulating data with their hands.” Other reasons, in Grossman view, why the iPhone was the most valuable invention of 2007, was its benefit to the mobile market in general. -

The Department of Justice Versus Apple Inc. -- the Great Encryption Debate Between Privacy and National Security
Catholic University Journal of Law and Technology Volume 27 Issue 2 Spring 2019 Article 3 2019 The Department of Justice Versus Apple Inc. -- The Great Encryption Debate Between Privacy and National Security Julia P. Eckart Follow this and additional works at: https://scholarship.law.edu/jlt Part of the Communications Law Commons, Constitutional Law Commons, First Amendment Commons, Intellectual Property Law Commons, Internet Law Commons, Other Law Commons, Privacy Law Commons, and the Science and Technology Law Commons Recommended Citation Julia P. Eckart, The Department of Justice Versus Apple Inc. -- The Great Encryption Debate Between Privacy and National Security, 27 Cath. U. J. L. & Tech 1 (2019). Available at: https://scholarship.law.edu/jlt/vol27/iss2/3 This Article is brought to you for free and open access by CUA Law Scholarship Repository. It has been accepted for inclusion in Catholic University Journal of Law and Technology by an authorized editor of CUA Law Scholarship Repository. For more information, please contact [email protected]. THE DEPARTMENT OF JUSTICE VERSUS APPLE INC.—THE GREAT ENCRYPTION DEBATE BETWEEN PRIVACY AND NATIONAL SECURITY Julia P. Eckart* I. THE FACTS UNDERLYING THE DOJ–APPLE DISPUTE ........................3 A. Timeline of the Parties’ Court-Filed Documents ......................................6 B. Issues Presented in the DOJ–Apple Litigation ..........................................8 II. APPLE’S iOS9.0 SECURITY GUIDE ..........................................................9 A. Some of Apple’s Encryption and Non-Encryption Security Features ........9 B. Other Hardware and Software System Security Features .......................11 III. DOES THIS CASE PERTAIN TO A SINGLE IPHONE OR ALL IPHONES? .......................................................................................................12 A. DOJ’s Position—It is About One, Single iPhone ....................................12 B. -

The Apple Ecosystem
APPENDIX A The Apple Ecosystem There are a lot of applications used to manage Apple devices in one way or another. Additionally, here’s a list of tools, sorted alphabetically per category in order to remain vendor agnostic. Antivirus Solutions for scanning Macs for viruses and other malware. • AVG: Basic antivirus and spyware detection and remediation. • Avast: Centralized antivirus with a cloud console for tracking incidents and device status. • Avira: Antivirus and a browser extension. Avira Connect allows you to view device status online. • BitDefender: Antivirus and malware managed from a central console. • CarbonBlack: Antivirus and Application Control. • Cylance: Ransomware, advanced threats, fileless malware, and malicious documents in addition to standard antivirus. • Kaspersky: Antivirus with a centralized cloud dashboard to track device status. © Charles Edge and Rich Trouton 2020 707 C. Edge and R. Trouton, Apple Device Management, https://doi.org/10.1007/978-1-4842-5388-5 APPENDIX A THe AppLe ECOSYSteM • Malware Bytes: Antivirus and malware managed from a central console. • McAfee Endpoint Security: Antivirus and advanced threat management with a centralized server to track devices. • Sophos: Antivirus and malware managed from a central console. • Symantec Mobile Device Management: Antivirus and malware managed from a central console. • Trend Micro Endpoint Security: Application whitelisting, antivirus, and ransomware protection in a centralized console. • Wandera: Malicious hot-spot monitoring, jailbreak detection, web gateway for mobile threat detection that integrates with common MDM solutions. Automation Tools Scripty tools used to automate management on the Mac • AutoCasperNBI: Automates the creation of NetBoot Images (read: NBI’s) for use with Casper Imaging. • AutoDMG: Takes a macOS installer (10.10 or newer) and builds a system image suitable for deployment with Imagr, DeployStudio, LANrev, Jamf Pro, and other asr or Apple Systems Restore-based imaging tools. -

How to Catch a Unicorn
How to Catch a Unicorn An exploration of the universe of tech companies with high market capitalisation Author: Jean Paul Simon Editor: Marc Bogdanowicz 2016 EUR 27822 EN How to Catch a Unicorn An exploration of the universe of tech companies with high market capitalisation This publication is a Technical report by the Joint Research Centre, the European Commission’s in-house science service. It aims to provide evidence-based scientific support to the European policy-making process. The scientific output expressed does not imply a policy position of the European Commission. Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of this publication. JRC Science Hub https://ec.europa.eu/jrc JRC100719 EUR 27822 EN ISBN 978-92-79-57601-0 (PDF) ISSN 1831-9424 (online) doi:10.2791/893975 (online) © European Union, 2016 Reproduction is authorised provided the source is acknowledged. All images © European Union 2016 How to cite: Jean Paul Simon (2016) ‘How to catch a unicorn. An exploration of the universe of tech companies with high market capitalisation’. Institute for Prospective Technological Studies. JRC Technical Report. EUR 27822 EN. doi:10.2791/893975 Table of Contents Preface .............................................................................................................. 2 Abstract ............................................................................................................. 3 Executive Summary .......................................................................................... -

Using an Ipad Or Iphone on Apple Ios 11
Using an iPad or iPhone on Apple iOS 11 Table of Contents Important Icons ......................................................................................................................................... 2 Common Gestures ..................................................................................................................................... 3 Common Buttons....................................................................................................................................... 3 Keyboard .................................................................................................................................................... 4 Settings ...................................................................................................................................................... 5 Accessibility ............................................................................................................................................... 5 iOS vs Model Version ................................................................................................................................ 6 Airplane Mode ........................................................................................................................................... 6 Security ...................................................................................................................................................... 7 Notes ......................................................................................................................................................... -
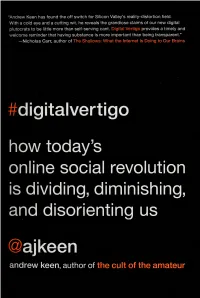
Digital Vertigo Provides a Timely And
"Andrew Keen has found the off switch for Silicon Valley's reality-distortion field. With a cold eye and a cutting wit, he reveals the grandiose claims of our new digital plutocrats to be little more than self-serving cant. Digital Vertigo provides a timely and welcome reminder that having substance is more important than being transparent." -Nicholas Carr, author of The Shallows: What the Internet Is Doing to Our Brains #digitalvertigo how today's online social revolution is dividing, diminishing, and disorienting us ajkeen andrew keen, author of the cult of the amateur $25.99/$2< 'Digital Vertigo provides an articulate, measured, rian voice against a sea of hype about auo.ai nnedia. As an avowed technology optii..._ -Larry Downes, author of ishina the Killer does mark zuckerberg know A/hv are we al details of their lives and Google+ ? In Digital Vertigo, Andrew Keen exposes the atest Silicon Valley mania: today's trillion-dollar cr^r-ia| networking revolution online start-up, he reveals—from commerce to communications to entertainment-is now going 3.0." social in a transformation called "Web ^hat he calls this "cult of the socii individual privacy and i jeopardizing both our liberty. Using one of Alfred Hitchcock's greatest films. Vertigo, as his starting point, he argues that social media, with its generation of massive mounts of personal data, is encouraging us to fall in love with something that is too good to be true-a radically transparent twenty-first-century society in which we can all supposedly realize oi"- luthentic identities on the Internet. -

Martin D. Burke – Curriculum Vitae
Martin D. Burke – Curriculum Vitae Professor of Chemistry phone: (217) 244-8726 University of Illinois at Urbana-Champaign email: [email protected] 454 Roger Adams Laboratory web: http://www.scs.illinois.edu/burke 600 South Mathews Ave. born: Feb. 5, 1976, Westminster, MD, USA Urbana, IL 61801 ________________________________________________________________________________________________________________________________________________________________________________________________________ Education 1998-2005 Harvard Medical School & Massachusetts Institute of Technology Division of Health Sciences and Technology National Institutes of Health Fellow in the Medical Scientist Training Program Boston, Massachusetts, Degree awarded: M.D. 1999-2003 Harvard University, Department of Chemistry and Chemical Biology Howard Hughes Medical Institutes Predoctoral Fellow Thesis advisor: Professor Stuart L. Schreiber Cambridge, Massachusetts, Degree Awarded: Ph.D. 1994-1998 Johns Hopkins University Howard Hughes Medical Institute Undergraduate Research Fellow Research advisors: Professors Henry Brem and Gary H. Posner Baltimore, Maryland, Degree Awarded: B.A. Chemistry Appointments 2018 Associate Dean of Research, Carle-Illinois College of Medicine 2014 Professor of Chemistry, University of Illinois at Urbana-Champaign 2011 Associate Professor of Chemistry, University of Illinois at Urbana-Champaign 2009-2015 Early Career Scientist, Howard Hughes Medical Institute 2009 Affiliate Faculty, Dept. of Biochemistry, University of Illinois at Urbana-Champaign -

And How to Overcome Its Flaws Remote Or Hybrid Workforces Are Here, and Users Are Using More and More Devices to Stay Connected and Productive
And how to overcome its flaws Remote or hybrid workforces are here, and users are using more and more devices to stay connected and productive. Organizations need to manage, support and secure the range of end-user devices, but may be asking, “How do we manage the various platforms in our environment?” Because organizations and their users have devices across different operating systems — and with employee-choice programs, this challenge will only be more prevalent in the modern workforce — different operating systems and devices deserve dedicated solutions. The notion of unified endpoint management (UEM), where all devices are managed with a single mobile device management (MDM) solution might sound great, but begs the question, “ What is universal across Microsoft, Apple and Google?” The reality is desktop operating systems — Windows, macOS and Chrome OS — have little in common. Each have a unique workflow to provision, encrypt, deploy, secure, update and support devices. The same distinctions apply to the mobile platforms: iOS/iPadOS, Windows Mobile and Android. UEM falls short; no one management tool is designed to support everything. So, your organization has likely considered: Managing devices by Attempting to manage Managing your devices platform type your devices with a by ecosystem unified tool. (i.e., desktop or mobile) (Apple, Microsoft, Google) This e-book breaks down your choices and their impacts on your organization and end users to help you determine the right management philosophy and solution. APPROACHING MANAGEMENT THROUGH THE LENS OF AN ECOSYSTEM Defining device management models The reality is that unified Let’s start by examining the various types of device management tools aren’t management models. -

The State of Vulkan on Apple 03June 2021
The State of Vulkan on Apple Devices Why you should be developing for the Apple ecosystem with Vulkan, and how to do it. Richard S. Wright Jr., LunarG June 3, 2021 If you are reading this, you likely already know what Vulkan is -- a low-overhead, high-performance, cross-platform, graphics and compute API designed to take maximum advantage of today's highly parallel and scalable graphics and compute hardware. To be sure, there are other APIs with this goal such as Microsoft’s DirectX and Apple’s Metal API. For a long time OpenGL matured to meet the needs of rapidly evolving hardware and met well the challenges of cross-platform development of high-performance graphics applications. OpenGL will remain viable for a very long time for many applications (and can actually be layered on top of Vulkan), but to take maximum advantage of modern hardware, a new and somewhat reinvented approach is called for. Everyone does not need the level of control that Vulkan provides, but if you do, you can think of Vulkan as a lower-level successor to OpenGL in that it attempts to enable highly portable, yet high-performance, application development across desktop and mobile device platforms. Writing platform specific code does have its advantages, and vendors such as Microsoft and Apple certainly adore having best of breed titles available exclusively for their customers as it adds value to their ecosystem. For developers though, it is often in our best interests to make our products available as widely as possible. Aside from gaming consoles with their mostly closed development environments, Windows, Linux, Apple, and Android combined represent most of the market for developers of end user software and games today.