Nav Ng Igati Compliance and Security for Unified Communications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Broadcasting Decision CRTC 2016-196
Broadcasting Decision CRTC 2016-196 PDF version Reference: 2016-147 Ottawa, 24 May 2016 Various licensees Various locations across Canada Various terrestrial broadcasting distribution undertakings – Administrative renewals 1. The Commission renews the broadcasting licences for the terrestrial broadcasting distribution undertakings set out in the appendix to this decision from 1 September 2016 to 30 November 2016, subject to the terms and conditions in effect under the current licences. 2. This decision does not dispose of any issue that may arise with respect to the renewal of these licences, including past non-compliance issues. The Commission is considering the renewal of these licences in Call for licence renewal applications: Submission of renewal applications for broadcasting licences of terrestrial distribution undertakings (BDUs) that will expire in 2016 and 2017; implementation of certain conditions of licence and review of practices in regard to the small basic and flexible packaging requirements for all BDU licensees, Broadcasting Notice of Consultation CRTC 2016-147, 21 April 2016. Secretary General *This decision is to be appended to each licence. Appendix to Broadcasting Decision CRTC 2016-196 Terrestrial broadcasting distribution undertakings for which the broadcasting licences have been administratively renewed until 30 November 2016 Licensee Locations Access Communications Co-operative Limited Regina (including White City), Saskatchewan Cogeco Cable Canada GP Inc. (the general Belleville, Burlington, Georgetown, partner) -

QUESTION 20-1/2 Examination of Access Technologies for Broadband Communications
International Telecommunication Union QUESTION 20-1/2 Examination of access technologies for broadband communications ITU-D STUDY GROUP 2 3rd STUDY PERIOD (2002-2006) Report on broadband access technologies eport on broadband access technologies QUESTION 20-1/2 R International Telecommunication Union ITU-D THE STUDY GROUPS OF ITU-D The ITU-D Study Groups were set up in accordance with Resolutions 2 of the World Tele- communication Development Conference (WTDC) held in Buenos Aires, Argentina, in 1994. For the period 2002-2006, Study Group 1 is entrusted with the study of seven Questions in the field of telecommunication development strategies and policies. Study Group 2 is entrusted with the study of eleven Questions in the field of development and management of telecommunication services and networks. For this period, in order to respond as quickly as possible to the concerns of developing countries, instead of being approved during the WTDC, the output of each Question is published as and when it is ready. For further information: Please contact Ms Alessandra PILERI Telecommunication Development Bureau (BDT) ITU Place des Nations CH-1211 GENEVA 20 Switzerland Telephone: +41 22 730 6698 Fax: +41 22 730 5484 E-mail: [email protected] Free download: www.itu.int/ITU-D/study_groups/index.html Electronic Bookshop of ITU: www.itu.int/publications © ITU 2006 All rights reserved. No part of this publication may be reproduced, by any means whatsoever, without the prior written permission of ITU. International Telecommunication Union QUESTION 20-1/2 Examination of access technologies for broadband communications ITU-D STUDY GROUP 2 3rd STUDY PERIOD (2002-2006) Report on broadband access technologies DISCLAIMER This report has been prepared by many volunteers from different Administrations and companies. -

Application for Forbearance from the Regulation of Residential Local Exchange Services
Telecom Decision CRTC 2018-109 PDF version Ottawa, 29 March 2018 Public record: 8640-S22-201711648 Saskatchewan Telecommunications – Application for forbearance from the regulation of residential local exchange services The Commission approves SaskTel’s request for forbearance from the regulation of residential local exchange services in the exchange of North Battleford, Saskatchewan. Application 1. The Commission received an application from Saskatchewan Telecommunications (SaskTel), dated 15 December 2017, in which the company requested forbearance from the regulation of residential local exchange services1 in the exchange of North Battleford, Saskatchewan. 2. The Commission received a submission regarding SaskTel’s application from Rogers Communications Canada Inc. (RCCI). Commission’s analysis and determinations 3. Pursuant to the Commission’s requirements in Telecom Decision 2006-15, SaskTel provided evidence to support its forbearance request, including competitor quality of service (Q of S) results for the six months preceding its application, and a draft communications plan for the Commission’s approval. The Commission has assessed SaskTel’s application based on the local forbearance test set out in Telecom Decision 2006-15 by examining the four criteria set out below. Product market 4. The Commission received no comments with respect to SaskTel’s proposed list of residential local exchange services. 5. SaskTel is seeking forbearance from the regulation of 11 tariffed residential local exchange services. The Commission notes that 10 of these services were included in the list of services set out in Telecom Decision 2005-35-1. The other service, Feature 1 In this decision, “residential local exchange services” refers to local exchange services used by residential customers to access the public switched telephone network and any associated service charges, features, and ancillary services. -

The Relationship Between Local Content, Internet Development and Access Prices
THE RELATIONSHIP BETWEEN LOCAL CONTENT, INTERNET DEVELOPMENT AND ACCESS PRICES This research is the result of collaboration in 2011 between the Internet Society (ISOC), the Organisation for Economic Co-operation and Development (OECD) and the United Nations Educational, Scientific and Cultural Organization (UNESCO). The first findings of the research were presented at the sixth annual meeting of the Internet Governance Forum (IGF) that was held in Nairobi, Kenya on 27-30 September 2011. The views expressed in this presentation are those of the authors and do not necessarily reflect the opinions of ISOC, the OECD or UNESCO, or their respective membership. FOREWORD This report was prepared by a team from the OECD's Information Economy Unit of the Information, Communications and Consumer Policy Division within the Directorate for Science, Technology and Industry. The contributing authors were Chris Bruegge, Kayoko Ido, Taylor Reynolds, Cristina Serra- Vallejo, Piotr Stryszowski and Rudolf Van Der Berg. The case studies were drafted by Laura Recuero Virto of the OECD Development Centre with editing by Elizabeth Nash and Vanda Legrandgerard. The work benefitted from significant guidance and constructive comments from ISOC and UNESCO. The authors would particularly like to thank Dawit Bekele, Constance Bommelaer, Bill Graham and Michuki Mwangi from ISOC and Jānis Kārkliņš, Boyan Radoykov and Irmgarda Kasinskaite-Buddeberg from UNESCO for their work and guidance on the project. The report relies heavily on data for many of its conclusions and the authors would like to thank Alex Kozak, Betsy Masiello and Derek Slater from Google, Geoff Huston from APNIC, Telegeography (Primetrica, Inc) and Karine Perset from the OECD for data that was used in the report. -

Telecom Decision CRTC 2007-59
Telecom Decision CRTC 2007-59 Ottawa, 25 July 2007 Bell Aliant – Applications for forbearance from the regulation of residential local exchange services Reference: 8640-B54-200706096, 8640-B54-200706111, 8640-B54-200706129, 8640-B54-200706153, 8640-B54-200706632 (New Brunswick); 8640-B54-200705551, 8640-B54-200705809, 8640-B54-200705824, 8640-B54-200705874, 8640-B54-200705890, 8640-B54-200705957, 8640-B54-200705981, 8640-B54-200705999, 8640-B54-200706020, 8640-B54-200706038, 8640-B54-200706731 (Nova Scotia); 8640-B54-200706046, 8640-B54-200706054, 8640-B54-200706062, 8640-B54-200706070, 8640-B54-200706723 (Prince Edward Island); and 8640-C12-200706351 (general) In this Decision, the Commission approves Bell Aliant Regional Communications, Limited Partnership's (Bell Aliant) request for forbearance from the regulation of residential local exchange services in 72 exchanges in New Brunswick, Nova Scotia, and Prince Edward Island. The Commission denies Bell Aliant's request for forbearance in 8 exchanges. Introduction 1. The Commission received applications by Bell Aliant Regional Communications, Limited Partnership (Bell Aliant), dated between 11 and 30 April 2007, in which the company requested forbearance from the regulation of residential local exchange services1 in 80 exchanges in New Brunswick, Nova Scotia – including exchanges in the priority census metropolitan area (CMA) of Halifax2 – and Prince Edward Island. 2. In a letter dated 7 May 2007, the Commission directed incumbent local exchange carriers (ILECs), competitive local exchange -
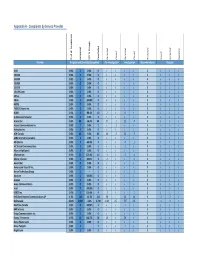
Appendix A: Complaints by Service Provider
Appendix A ‐ Complaints by Service Provider Complaints Change all % of Concluded Resolved Closed Resolved Closed Accepted Issued Accepted Rejected Accepted Y/Y % Provider Accepted and Concluded Complaints Pre‐Investigation Investigation Recommendation Decision #100 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010100 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010580 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010620 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1010738 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 1011295.com 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 295.ca 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 3Web 0.0% 0 ‐100.0% 0 0 0 0 0 0 0 0 0 450Tel 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 768812 Ontario Inc. 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 8COM 0.1% 8 ‐88.4% 10 2 0 8 0 0 0 0 0 A dimension humaine 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 Acanac Inc. 0.6% 64 ‐16.9% 64 37 1224 0 0 0 0 Access Communications Inc. 0.0% 1 0.0% 1 0 1 0 0 0 0 0 0 Achatplus Inc. 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 ACN Canada 0.8% 82 9.3% 81 54 2 22 3 0 0 0 0 AEBC Internet Corporation 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 AEI Internet 0.0% 3 ‐40.0% 5 0 0 41 0 0 0 0 AIC Global Communications 0.0% 1 0.0% 1 0 0 1 0 0 0 0 0 Alberta High Speed 0.0% 0 0.0% 0 0 0 0 0 0 0 0 0 Allstream Inc. -

Seaside Code of Conduct and Understand It Represents Mandatory Policies of the Organization
Code of Conduct November 1, 2015 Edition TABLE OF CONTENTS SECTION ONE ETHICS AND COMPLIANCE PROGRAM Program Structure ...................................................................................................................................... 1 Setting Standards ........................................................................................................................................ 1 Training and Communication ............................................................................................................... 1 Resources for Guidance and Reporting Concerns ....................................................................... 2 Personal Obligation to Report ............................................................................................................... 3 Internal Investigations of Reports........................................................................................................ 3 Corrective Action ......................................................................................................................................... 3 Discipline ......................................................................................................................................................... 3 Measuring Program Effectiveness ....................................................................................................... 4 Acknowledgment Process ..................................................................................................................... -
ONN 6 Eng Codelist Only Webversion.Indd
6-DEVICE UNIVERSAL REMOTE Model: 100020904 CODELIST Need help? We’re here for you every day 7 a.m. – 9 p.m. CST. Give us a call at 1-888-516-2630 Please visit the website “www.onn-support.com” to get more information. 1 TABLE OF CONTENTS CODELIST TV 3 STREAM 5 STB 5 AUDIO SOUNDBAR 21 BLURAY DVD 22 2 CODELIST TV TV EQD 2014, 2087, 2277 EQD Auria 2014, 2087, 2277 Acer 4143 ESA 1595, 1963 Admiral 3879 eTec 2397 Affinity 3717, 3870, 3577, Exorvision 3953 3716 Favi 3382 Aiwa 1362 Fisher 1362 Akai 1675 Fluid 2964 Akura 1687 Fujimaro 1687 AOC 3720, 2691, 1365, Funai 1595, 1864, 1394, 2014, 2087 1963 Apex Digital 2397, 4347, 4350 Furrion 3332, 4093 Ario 2397 Gateway 1755, 1756 Asus 3340 GE 1447 Asustek 3340 General Electric 1447 Atvio 3638, 3636, 3879 GFM 1886, 1963, 1864 Atyme 2746 GPX 3980, 3977 Audiosonic 1675 Haier 2309, 1749, 1748, Audiovox 1564, 1276, 1769, 3382, 1753, 3429, 2121 2293, 4398, 2214 Auria 4748, 2087, 2014, Hannspree 1348, 2786 2277 Hisense 3519, 4740, 4618, Avera 2397, 2049 2183, 5185, 1660, Avol 2735, 4367, 3382, 3382, 4398 3118, 1709 Hitachi 1643, 4398, 5102, Axen 1709 4455, 3382, 0679 Axess 3593 Hiteker 3118 BenQ 1756 HKPro 3879, 2434 Blu:sens 2735 Hyundai 4618 Bolva 2397 iLo 1463, 1394 Broksonic 1892 Insignia 2049, 1780, 4487, Calypso 4748 3227, 1564, 1641, Champion 1362 2184, 1892, 1423, Changhong 4629 1660, 1963, 1463 Coby 3627 iSymphony 3382, 3429, 3118, Commercial Solutions 1447 3094 Conia 1687 JVC 1774, 1601, 3393, Contex 4053, 4280 2321, 2271, 4107, Craig 3423 4398, 5182, 4105, Crosley 3115 4053, 1670, 1892, Curtis -

Access and Inclusion Digital Communications for All
Access and Inclusion Digital communications for all Consultation Publication date: 18 March 2009 Closing Date for Responses: 3 June 2009 Main Heading Contents Section Page One page overview 3 1 Executive summary 4 2 Introduction 10 3 Ofcom’s role 13 4 Which services matter for access and inclusion? 19 5 Availability 28 6 Take-up 41 7 Ability to use services effectively 48 8 Priority areas 61 Annex Page 1 Responding to this consultation 84 2 Ofcom’s consultation principles 86 3 Consultation response cover sheet 87 4 Consultation questions 89 5 Quality of service for text relay 91 6 Broadband take-up 94 7 Glossary of terms and definitions 116 Access and Inclusion One page overview Digital services have long been recognised as important for citizens’ participation in society, the economy and the democratic process. While Ofcom’s work to encourage competition has helped to deliver the three central goals of availability, take-up and effective use of key services, the market alone may fail to secure them universally. As a result, we have worked directly to make progress towards those three goals. As examples, we help to define and enforce the Universal Service Obligation for fixed line telephony and are ensuring that at least 98.5% of the population will receive digital terrestrial television following switchover. But the digital world is changing. Given the growth of broadband and mobile services, of digital broadcasting and of technologies and services which could provide greater benefits for disabled users, the time is right for us to check whether our approach to access and inclusion issues remains appropriate. -

Court File No. CV-16-11257-00CL ONTARIO SUPERIOR COURT of JUSTICE COMMERCIAL LIST
Court File No. CV-16-11257-00CL ONTARIO SUPERIOR COURT OF JUSTICE COMMERCIAL LIST IN THE MATTER OF THE COMPANIES’ CREDITORS ARRANGEMENT ACT, R.S.C. 1985, c. C-36, AS AMENDED AND IN THE MATTER OF A PLAN OF COMPROMISE OR ARRANGEMENT OF PT HOLDCO, INC., PRIMUS TELECOMMUNICATIONS CANADA, INC., PTUS, INC., PRIMUS TELECOMMUNICATIONS, INC., AND LINGO, INC. (Applicants) APPROVAL AND VESTING ORDER SERVICE LIST GENERAL STIKEMAN ELLIOTT LLP Samantha Horn 5300 Commerce Court West Tel: (416) 869- 5636 199 Bay Street Email: [email protected] Toronto, ON M5L 1B9 Maria Konyukhova Tel: (416) 869-5230 Email: [email protected] Kathryn Esaw Tel: (416) 869-6820 Email: [email protected] Vlad Calina Tel: (416) 869-5202 Lawyers for the Applicants Email: [email protected] FTI CONSULTING CANADA INC. Nigel D. Meakin TD Waterhouse Tower Tel: (416) 649-8100 79 Wellington Street, Suite 2010 Fax: (416) 649-8101 Toronto, ON M5K 1G8 Email: [email protected] Steven Bissell Tel: (416) 649-8100 Fax: (416) 649-8101 Email: [email protected] Kamran Hamidi Tel: (416) 649-8100 Fax: (416) 649-8101 Monitor Email: [email protected] 2 BLAKE, CASSELS & GRAYDON LLP Linc Rogers 199 Bay Street Tel: (416) 863-4168 Suite 4000, Commerce Court West Fax: (416) 863-2653 Toronto, ON M5L 1A9 Email: [email protected] Aryo Shalviri Tel: (416) 863- 2962 Fax: (416) 863-2653 Lawyers for the Monitor Email: [email protected] DAVIES WARD PHILLIPS VINEBERG LLP Natasha MacParland 155 Wellington Street West Tel: (416) 863 5567 Toronto, ON M5V 3J7 Fax: (416) 863 0871 Email: [email protected] Lawyers for the Bank of Montreal, as Administrative Agent for the Syndicate FOGLER, RUBINOFF LLP Gregg Azeff 77 King Street West Tel: (416) 365-3716 Suite 3000, P.O. -

Voice Over Internet Protocol (Voip) Competitive Landscape
Attachment 1 Page 1 of 69 Voice over Internet Protocol (VoIP) Competitive Landscape 28 July 2005 "For many, the phone jack in the wall that connects to the phone company's network is just a useless hole." Wall Street Journal; August 25, 2004 Attachment 1 Page 2 of 69 Table of Contents Page 1.0 GENERAL .........................................................................................................................3 2.0 RESIDENTIAL MARKET...................................................................................................8 2.1 Introduction............................................................................................................8 2.2 Competitive Overview ...........................................................................................9 2.2.1 VoIP Service Providers..............................................................................9 2.2.1.1 Telephony Offered by Cablecos ...............................................16 2.2.1.2 VoIP Forecasts .........................................................................24 2.2.2 Wireless Voice.........................................................................................26 2.2.3 Fixed Line Voice ......................................................................................29 2.2.4 Fixed and Wireless Text ..........................................................................31 2.3 Competitive Intensity ...........................................................................................32 3.0 Business market..............................................................................................................40 -

ACCESS COMMUNICATIONS GENERAL TARIFF CRTC 21640 Original Page 1
TARIFF PAGE GENERAL TARIFF ACCESS COMMUNICATIONS CO-OPERATIVE LIMITED GENERAL TARIFF This Tariff sets out the rates, terms and conditions applicable to the interconnection arrangements provisioned to providers of telecommunications services and facilities. Filing Date: January 19, 2007 Effective Date: February 2, 2007 Approved in Telecom Order 2007-38 TARIFF PAGE ACCESS COMMUNICATIONS GENERAL TARIFF CRTC 21640 Original Page 1 EXPLANATION OF SYMBOLS The following symbols are used in this Tariff and have meanings as shown: A Increase in rate or charge C Change in wording D Discontinued rate or regulation F Reformatting of existing material with no change to rate or charge M Matter moved from its previous location N New wording, rate or charge R Reduction in rate or charge S Reissued matter Filing Date: January 19, 2007 Effective Date: February 2, 2007 Approved in Telecom Order 2007-38 TARIFF PAGE ACCESS COMMUNICATIONS GENERAL TARIFF CRTC 21640 3rd Revised Page 2 Check Page Revision Number Page Number Revision Number Page Number Original Title Page Original 17 Original 1 Original 18 3rd Revised Check Page Original 19 1st Revised 3 Original 20 Original 5 3rd Revised 21 Original 6 1st Revised 22 Original 7 1st Revised 23 Original 8 1st Revised 24 Original 9 3rd Revised 25 Original 10 1st Revised 26 Original 11 1st Revised 27 Original 12 1st Revised 28 Original 13 1st Revised 29 Original 14 1st Revised 30 Original 15 2nd Revised 31 Original 16 Filing Date: January 19, 2007 Effective Date: February 2, 2007 Approved in Telecom Order 2007-38 TARIFF PAGE ACCESS COMMUNICATIONS GENERAL TARIFF CRTC 21640 CO-OPERATIVE LIMITED 1st Revised Page 3 F TABLE OF CONTENTS Page Title Page Title Page Explanation of Symbols 1 Check Page 2 Table of Contents 3 PART A Definitions and General Terms ITEM 100 General 5 ITEM 101 Definitions 6 ITEM 102 General Rights and Obligations 10 1.