Ios 8 – What It Changes for Forensic Investigators
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Creationstation ® Guide
SAFARI Montage CreationStation User Guide SAFARI Montage CreationStation® Overview SAFARI Montage CreationStation is an easy-to-use integrated module that enables schools and districts to upload user-created digital content and licensed media to the SAFARI Montage system's Learning Object Repository (LOR). User types granted upload privileges, such as Student with Upload, Teacher with Upload and higher level user types can add items either individually or in bulk. Once uploaded, content can be meta-tagged with information such as a detailed description, relevant grade ranges and year of copyright, uploads can be correlated to curriculum standards and designated for home access, download, etc. Video and audio content can be segmented into chapters and key concepts, each with their own segment descriptions. Flexible Digital Rights Management provides control over the content to ensure that the correct users have access to digital resources. Media and web links uploaded via CreationStation are fully searchable in conjunction with licensed content, providing a wealth of digital resources that are easily accessible and able to be used with other system features for instructional purposes. When used in conjunction with SAFARI Montage WAN Manager, digital resources can be shared with others in the same school as the user who uploaded it, or published to all schools in the district. Student user types have an appropriately limited ability to upload to the SAFARI Montage system through the CreationStation feature, My Locker. To learn more, refer to the following Help topics: Uploading Media into CreationStation Adding and Editing Metadata Searching for Uploaded Content Using Uploaded Content My Locker for Students - CreationStation video tutorial Accessing CreationStation 1 SAFARI_Montage_creation 1. -

Initial Setup of Your IOS Device
1. When you first turn on your iOS device, you'll see a screen displaying Hello in different languages. Slide from left to right anywhere on this screen. 2. Select the language you want your iOS device to use, and then the region in which you'll be using your iOS device. This will affect things such as date, time, and contact formatting. 3. Your iOS device requires an Internet connection to set up. Tap the name of your desired Wi-Fi network to begin device activation. § If you're activating an iPhone or iPad (Wi-Fi + Cellular) with active cellular service, you can instead choose cellular activation. 4. Choose whether to enable Location Services. 5. Set up your iPhone as a new device, from an iCloud backup, or from an iTunes backup. § If restoring from backup, you can learn how to restore your content. 6. Sign in with your Apple ID, which you've created previously, or create a free Apple ID. § Alternatively, you can tap Skip This Step to sign in or create an Apple ID later. § If necessary, learn how to create a free Apple ID: 1. Select your birthday, then tap Next: 2. Enter your first and last name, then tap Next: 3. You can then use either your current email address, or choose to get a free iCloud email address. Select the option you'd like, then tap Next. 4. Enter your current email address, or what you'd like for your iCloud email, then tap Next. 5. Enter what you'd like for your password and tap Next. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -

Apple TV Management
WHITE PAPER Apple TV Management Moving education forward If you think Apple TV devices are just for entertainment, think again. In a recent Jamf Nation survey, 99 percent of the 502 school respondents report leveraging Apple TV devices in their education institution, and for good reason. They enable wireless sharing without the need for adapters, and they make the classroom a more collaborative and engaging learning environment. Apple TV is also applicable outside the classroom. But until recently, they haven’t necessarily been easy to set up and manage. That all changed with tvOS 10.2, which recently became available with all fourth-generation Apple TV devices. IN THIS WHITE PAPER, LEARN: • Why Apple TV matters for education. • How to make set up and management easy with mobile device management. • How to leverage Apple TV beyond the classroom. Why Apple TV for education Like Mac and iPad, Apple TV is a powerful tool for educators. Twenty-three percent of schools surveyed about their Apple TV usage have 51-100 Apple TV devices, with a further 23 percent citing 101-500 TV devices. From promoting interaction and collaboration to fitting seamlessly within the Apple ecosystem, the use cases and benefits are vast. Before expanding on these, let’s examine three core Apple TV fundamentals that are key to its appeal. GOODBYE DONGLES. HELLO AIRPLAY. AIRPLAY FOR NON-APPLE DEVICES AirPlay is a wireless streaming technology. Introduced While AirPlay is built into all Apple devices, Apple in 2004, it eliminates the need for display adapters, TV works with common non-Apple platforms and changing the way presentations are delivered and devices, such as Windows and Chromebook. -

Managing Apple TV Devices with Tvos 10.2 Or Later Using Jamf Pro
Managing Apple TV Devices with tvOS 10.2 or Later Using Jamf Pro Technical Paper Jamf Pro 10.4.0 or Later 11 April 2018 © copyright 2002-2018 Jamf. All rights reserved. Jamf has made all efforts to ensure that this guide is accurate. Jamf 100 Washington Ave S Suite 1100 Minneapolis, MN 55401-2155 (612) 605-6625 The CASPER SUITE, Jamf, the Jamf Logo, JAMF SOFTWARE®, and the JAMF SOFTWARE Logo® are registered or common law trademarks of JAMF SOFTWARE, LLC in the U.S. and other countries. Apple, the Apple logo, Apple TV, AirPlay, iPad, iPod touch, and tvOS are trademarks of Apple Inc., registered in the United States and other countries. App Store is a service mark of Apple Inc., registered in the United States and other countries. IOS is a trademark or registered trademark of Cisco in the United States and other countries. All other product and service names mentioned herein are either registered trademarks or trademarks of their respective companies. Contents Contents 4 Introduction 4 What’s in This Guide 4 Additional Resources 5 Overview 5 Requirements 6 tvOS PreStage Enrollments 6 Requirements 6 Configuring a tvOS PreStage Enrollment 7 Related Information 8 tvOS Configuration Profiles 8 Restrictions Payload Settings for Apple TV 9 Single App Mode Payload Settings for Apple TV 9 Conference Room Display Payload Settings for Apple TV 10 Home Screen Layout Payload Settings for Apple TV 10 TV Remote Payload Settings for Apple TV 10 Related Information 11 Other tvOS Management Options 11 Enforcing a tvOS Device Name 11 tvOS Remote Commands 12 AirPlay Display Options 3 Introduction What’s in This Guide This guide provides step-by-step instructions for enrolling and managing Apple TV devices with tvOS 10.2 or later. -

Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Recor
Online Platforms and Market Power Part 6: Examining the Dominance of Amazon, Apple, Facebook, and Google Questions for the Record from the Honorable David N. Cicilline, Chairman, Subcommittee on Antitrust, Commercial and Administrative Law of the Committee on the Judiciary Questions for Mr. Tim Cook, CEO, Apple, Inc. 1. You testified that Apple’s apps “go through the same rules” that third-party apps are required to follow. The App Store Guidelines (“Guidelines”) are designed to ensure that the App Store remains a safe and trusted place for consumers to discover and download software for their Apple devices. The Guidelines apply to any app, Apple or third-party, that is available on the App Store in the first instance. a. How many Apple apps are pre-loaded on current iPhone models? The first iPhone included 13 integrated Apple apps. There were no third-party apps available for that iPhone. Apple’s subsequent decision to open the iPhone to third-party app development unleashed a wave of innovation and competition. Thirteen years later, there are more than 1.8 million third-party apps available through the App Store and only about 40 Apple apps integrated into the current iPhone models. Apple’s focus has always been to deliver a great consumer experience out of the box. That is why the iPhone comes with Apple apps like Phone, Notes, Settings, Files, Clock, Tips, Measure, and Reminders to provide basic functionality. In addition, apps like FaceTime, iMessage, Apple Music, TV, and others help differentiate the iPhone in a competitive smartphone market. The few apps that Apple has integrated into the iPhone are a drop in the bucket of the overall app ecosystem. -

Pangu 9 Internals
Pangu 9 Internals Tielei Wang & Hao Xu & Xiaobo Chen Team Pangu Agenda ✤ iOS Security Overview ✤ Pangu 9 Overview ✤ Userland Exploits ✤ Kernel Exploits & Kernel Patching ✤ Persistent Code Signing Bypass ✤ Conclusion Who We Are ✤ A security research team based in Shanghai, China ✤ Have broad research interests, but known for releasing jailbreak tools for iOS 7.1, iOS 8, and iOS 9 ✤ Regularly present research at BlackHat, CanSecWest, POC, RuxCon, etc. ✤ Run a mobile security conference named MOSEC (http://mosec.org) with POC in Shanghai iOS Security Overview ✤ Apple usually releases a white paper to explain its iOS security architecture ✤ Secure Booting Chain ✤ Mandatary Code Signing ✤ Restricted Sandbox ✤ Exploit Mitigation (ASLR, DEP) ✤ Data Protection ✤ Hypervisor and Secure Enclave Processor Agenda ✤ iOS Security Overview ✤ Pangu 9 Overview ✤ Userland Exploits ✤ Kernel Exploits & Kernel Patching ✤ Persistent Code Signing Bypass ✤ Conclusion What Jailbreak is “iOS jailbreaking is the removing of software restrictions imposed by iOS, Apple's operating system, on devices running it through the use of software exploits” –Wikipedia ✤ Jailbreak has to rely on kernel exploits to achieve the goal, because many software restrictions are enforced by the kernel Kernel Attack Surfaces Difficulty Gaining of the Privilege root with special entitlements root, no sandbox mobile, no sandbox mobile, less restrictive sandbox mobile, container sandbox Amount of Kernel Attack Surface Gained Our Preference Difficulty Gaining of the Privilege root with special -

Ios SDK Release Notes for Ios 8.0 Beta 5
iOS SDK Release Notes for iOS 8.0 Beta 5 Important: This is a preliminary document for an API or technology in development. Apple is supplying this information to help you plan for the adoption of the technologies and programming interfaces described herein for use on Apple‑branded products. This information is subject to change, and software implemented according to this document should be tested with final operating system software and final documentation. Newer versions of this document may be provided with future betas of the API or technology. Contents: Introduction Bug Reporting Notes and Known Issues Introduction iOS SDK 8.0 provides support for developing iOS apps. It is packaged with a complete set of Xcode tools, compilers, and frameworks for creating apps for iOS and OS X. These tools include the Xcode IDE and the Instruments analysis tool, among many others. With this software you can develop apps for iPhone, iPad, or iPod touch running iOS 8. You can also test your apps using the included iOS Simulator, which supports iOS 8. iOS SDK 8.0 requires a Mac computer running OS X v10.9.3 (Mavericks) or later. This version of iOS is intended for installation only on devices registered with the Apple Developer Program. Attempting to install this version of iOS in an unauthorized manner could put your device in an unusable state. For more information and additional support resources, visit http://developer.apple.com/programs/ios/. Bug Reporting For issues not mentioned in the Notes and Known Issues section, please file bugs through the Apple Developer website (https://developer.apple.com/bug‑reporting/ios/). -

What's New for Business
What’s New for Business WWDC 2021 The latest software updates from Apple enable employees to be more productive and collaborative. IT and security enhancements simplify deployment and management. And platform updates help developers build the next generation of business apps. Connect with your team Enhanced security and deployment for Mac Updates to FaceTime on iOS 15, iPadOS 15 and macOS Apple Configurator for iPhone now makes it possible to add a Monterey enable employees to easily share their screen or T2 or Apple silicon Mac to Apple Business Manager regardless interact with other content with SharePlay. New camera and of where it was purchased. Admins can now remotely install and microphone modes help reduce background distractions. Links remove System Extensions using MDM. Security enhancements to FaceTime calls can now be added to calendar invites and calls include the ability to set a password for recoveryOS and set can now be joined from any device, including other platforms. remote lock on Mac computers with Apple silicon. Software updates have new enforcement options and a Mac can now Be in the moment more seamlessly erase all content and settings in one step. New Focus modes across iOS, iPadOS and macOS help make it easy to concentrate on current tasks by muting non-urgent Extended iPhone and iPad management notifications. Focus status can be broadcast in messaging apps. Managed Open-In controls the flow of corporate data between Notifications have been redesigned and the all-new notification managed or unmanaged apps and has now been extended to summary helps to deliver the right content at the right time. -

Using an Ipad Or Iphone on Apple Ios 11
Using an iPad or iPhone on Apple iOS 11 Table of Contents Important Icons ......................................................................................................................................... 2 Common Gestures ..................................................................................................................................... 3 Common Buttons....................................................................................................................................... 3 Keyboard .................................................................................................................................................... 4 Settings ...................................................................................................................................................... 5 Accessibility ............................................................................................................................................... 5 iOS vs Model Version ................................................................................................................................ 6 Airplane Mode ........................................................................................................................................... 6 Security ...................................................................................................................................................... 7 Notes ......................................................................................................................................................... -
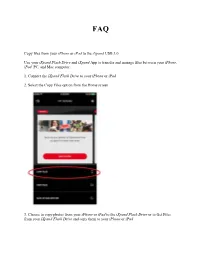
Copy Files from Your Iphone Or Ipad to the Ixpand USB 3.0 Use Your
FAQ Copy files from your iPhone or iPad to the iXpand USB 3.0 Use your iXpand Flash Drive and iXpand App to transfer and manage files between your iPhone, iPad, PC, and Mac computer. 1. Connect the iXpand Flash Drive to your iPhone or iPad 2. Select the Copy Files option from the Home screen 3. Choose to copy photos from your iPhone or iPad to the iXpand Flash Drive or to Get Files from your iXpand Flash Drive and copy them to your iPhone or iPad. 4. Select the photos to choose from the iPhone or iPad 5. Press Copy to iXpand Flash Drive 6. Select your destination folder from the list of folders on the iXpand Flash Drive or choose Create new to create a new folder 7. The selected files will be saved to your iXpand Flash Drive Backup and Restore files using the app iXpand Flash Drive The Back Up and Restore selection from the Home screen will allow you to do several tasks. Click on the "Back Up and Restore" option from the Home screen. You will be presented with a screen with the following option: 1. Back Up & Restore Photo Library to the iXpand Flash Drive 2. Back Up & Restore photos from Social Media accounts to the iXpand Flash Drive 3. Back Up & Restore Contacts Back Up or Restore your Camera Library You can back up your camera library to the iXpand Flash Drive by setting up auto-back up or manually back up as needed. Turn on Automatic back up by sliding the switch. -

Apple File System Reference
Apple File System Reference Developer Contents About Apple File System 7 General-Purpose Types 9 paddr_t .................................................. 9 prange_t ................................................. 9 uuid_t ................................................... 9 Objects 10 obj_phys_t ................................................ 10 Supporting Data Types ........................................... 11 Object Identifier Constants ......................................... 12 Object Type Masks ............................................. 13 Object Types ................................................ 14 Object Type Flags .............................................. 20 EFI Jumpstart 22 Booting from an Apple File System Partition ................................. 22 nx_efi_jumpstart_t ........................................... 24 Partition UUIDs ............................................... 25 Container 26 Mounting an Apple File System Partition ................................... 26 nx_superblock_t ............................................. 27 Container Flags ............................................... 36 Optional Container Feature Flags ...................................... 37 Read-Only Compatible Container Feature Flags ............................... 38 Incompatible Container Feature Flags .................................... 38 Block and Container Sizes .......................................... 39 nx_counter_id_t ............................................. 39 checkpoint_mapping_t ........................................