Iso/Iec Tr 24028:2020(E)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Standards Analysis Ict Sector Luxembourg
Version 6.0 – June 2016 ISSN 2354-483X STANDARDS ANALYSIS ICT SECTOR LUXEMBOURG · V5.0/09.2015 LUXEMBOURG LUXEMBOURG ICT SECTOR ICT CONTACT : ILNAS & ANEC STANDARDS ANALYSIS ANALYSIS STANDARDS Southlane Tower I · 1, avenue du Swing · L-4367 Belvaux Tel. : (+352) 24 77 43 -70 · Fax : (+352) 24 79 43 -70 E-mail : [email protected] ANS/AN03 www.portail-qualite.lu 2015 · © ILNAS/ANEC September Executive summary In 2012 the “Institut Luxembourgeois de la Normalisation, de l’Accréditation, de la Sécurité et qualité des produits et services” (ILNAS) initiated an analysis of European and international standards in the Information and Communication Technology (ICT) sector. The aim of this analysis is to develop an information and exchange network for ICT standardization knowledge in the Grand Duchy of Luxembourg. Since 2013, this analysis has been carried out in the frame of the implementation of the “Luxembourg’s policy on ICT technical standardization” (which was last updated in 2015)1. The ICT sector is already an active sector at the national standardization level with 65 national delegates currently registered by ILNAS2. These delegates are involved in standardization technical committees to participate actively and follow closely the work performed at international level and have the task of ensuring that the views and positions of Luxembourg are understood and known by the technical committees. ILNAS is convinced that this sector could be even more active, especially since some ICT subsectors do not yet benefit from a sufficient representation of national delegates (e.g.: Internet of Things, Cloud Computing, Big Data, Smart Cities). Thus, the purposes of this analysis are firstly, to provide useful information to national stakeholders regarding standardization activities in the field of ICT and secondly, to involve them into an integrated and innovative approach of standardization. -

Standards Analysis Ict Sector Luxembourg
Version 5.0 – September 2015 ISSN 2354-483X STANDARDS ANALYSIS ICT SECTOR LUXEMBOURG · V5.0/09.2015 LUXEMBOURG LUXEMBOURG ICT SECTOR ICT CONTACT : ILNAS & ANEC STANDARDS ANALYSIS ANALYSIS STANDARDS Southlane Tower I · 1, avenue du Swing · L-4367 Belvaux Tel. : (+352) 24 77 43 -70 · Fax : (+352) 24 79 43 -70 E-mail : [email protected] ANS/AN03 www.portail-qualite.lu 2015 · © ILNAS/ANEC September Executive summary The “Institut Luxembourgeois de la Normalisation, de l’Accréditation, de la Sécurité et qualité des produits et services” (ILNAS) has inititated in 2012 an analysis of European and international standards in the Information and Communication Technology (ICT) sector. This analysis intends to develop an information and exchange network for ICT standardization knowledge in the Grand Duchy of Luxembourg. Since 2013, this analysis has been carried out in the frame of the implementation of the “Luxembourg’s policy on ICT technical standardization” (which was last updated in 2015)1. The ICT sector is already an active sector at the national standardization level with 53 national delegates currently registered by ILNAS. These delegates are involved in standardization technical committees to participate actively and follow closely the work performed at international level and have the task of ensuring that the views and positions of the country are understood and known by the technical committees. ILNAS is convinced that this sector could be even more active, especially since some ICT subsectors do not yet have national delegates (e.g.: Sensor Networks, Internet of Things). Thus, the purposes of this analysis are firstly, to provide useful information to national stakeholders regarding standardization activities in the field of ICT and secondly, to involve them into an integrated and innovative approach of standardization. -

Industrial Automation
ISO Focus The Magazine of the International Organization for Standardization Volume 4, No. 12, December 2007, ISSN 1729-8709 Industrial automation • Volvo’s use of ISO standards • A new generation of watches Contents 1 Comment Alain Digeon, Chair of ISO/TC 184, Industrial automation systems and integration, starting January 2008 2 World Scene Highlights of events from around the world 3 ISO Scene Highlights of news and developments from ISO members 4 Guest View ISO Focus is published 11 times Katarina Lindström, Senior Vice-President, a year (single issue : July-August). It is available in English. Head of Manufacturing in Volvo Powertrain and Chairman of the Manufacturing, Key Technology Committee Annual subscription 158 Swiss Francs Individual copies 16 Swiss Francs 8 Main Focus Publisher • Product data – ISO Central Secretariat Managing (International Organization for information through Standardization) the lifecycle 1, ch. de la Voie-Creuse CH-1211 Genève 20 • Practical business Switzerland solutions for ontology Telephone + 41 22 749 01 11 data exchange Fax + 41 22 733 34 30 • Modelling the E-mail [email protected] manufacturing enterprise Web www.iso.org • Improving productivity Manager : Roger Frost with interoperability Editor : Elizabeth Gasiorowski-Denis • Towards integrated Assistant Editor : Maria Lazarte manufacturing solutions Artwork : Pascal Krieger and • A new model for machine data transfer Pierre Granier • The revolution in engineering drawings – Product definition ISO Update : Dominique Chevaux data sets Subscription enquiries : Sonia Rosas Friot • A new era for cutting tools ISO Central Secretariat • Robots – In industry and beyond Telephone + 41 22 749 03 36 Fax + 41 22 749 09 47 37 Developments and Initiatives E-mail [email protected] • A new generation of watches to meet consumer expectations © ISO, 2007. -

Stephan Goericke Editor the Future of Software Quality Assurance the Future of Software Quality Assurance Stephan Goericke Editor
Stephan Goericke Editor The Future of Software Quality Assurance The Future of Software Quality Assurance Stephan Goericke Editor The Future of Software Quality Assurance Editor Stephan Goericke iSQI GmbH Potsdam Germany Translated from the Dutch Original book: ‘AGILE’, © 2018, Rini van Solingen & Manage- ment Impact – translation by tolingo GmbH, © 2019, Rini van Solingen ISBN 978-3-030-29508-0 ISBN 978-3-030-29509-7 (eBook) https://doi.org/10.1007/978-3-030-29509-7 This book is an open access publication. © The Editor(s) (if applicable) and the Author(s) 2020 Open Access This book is licensed under the terms of the Creative Commons Attribution 4.0 Inter- national License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence and indicate if changes were made. The images or other third party material in this book are included in the book’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the book’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. -

Artificial Intelligence Standardization White Paper (2018 Edition) �����������2018
Translation The following government-issued white paper describes China's approach to standards-setting for artificial intelligence. Appendices list all of China's current (as of January 2018) and planned AI standardization protocols, and provide examples of applications of AI by China's leading tech companies. Title Artificial Intelligence Standardization White Paper (2018 Edition) 2018 Author China Electronics Standardization Institute (CESI; ; ) is the "compiling unit" () for this white paper. The 2nd Industrial Department () of the Standardization Administration of China (SAC; ) is the "guidance unit" () for this white paper. Source CESI website, January 24, 2018. CESI is a think tank subordinate to the PRC Ministry of Industry and Information Technology (MIIT; ); CESI is also known as the 4th Electronics Research Institute (; ) of MIIT. SAC is a component of the PRC State Administration for Market Regulation (), a ministry-level agency under China's cabinet, the State Council. The Chinese source text is available online at: http://www.cesi.cn/images/editor/20180124/20180124135528742.pdf Translation Date Translator Editor May 12, 2020 Etcetera Language Group, Inc. Ben Murphy, CSET Translation Lead Contributing institutions (in no particular order) China Electronics Standardization Institute Shanghai Development Center of Computer (CESI) Software Technology Institute of Automation, Chinese Academy Shanghai Xiao-i Robot Technology Co., Ltd. of Sciences Beijing Institute of Technology Beijing iQIYI Technology Co., Ltd. Tsinghua University Beijing Yousheng Zhiguang Technology Co., Ltd. (mavsyin) Peking University Extreme Element (Beijing) Intelligent Technology Co., Ltd. Renmin University of China Beijing ByteDance Technology Co., Ltd. Beihang University Beijing Sensetime Technology Development Co., Ltd. iFLYTEK Co., Ltd. Zhejiang Ant Small and Micro Financial Services Group Co., Ltd. -

An Engineer's Guide to Industrial Robot Designs
e-book An Engineer’s Guide to Industrial Robot Designs A compendium of technical documentation on robotic system designs ti.com/robotics Q2 | 2020 Table of Contents/Overview 1. Introduction 3. Robot arm and driving system (manipulator) 1.1 An introduction to an industrial robot system. 3 3.1.1 How to protect battery power management systems from thermal damage. 45 2. Robot system controller 3.1.2 Protecting your battery isn’t as hard as 2.1 Control panel you think.....................................46 2.1.1 Using Sitara™ processors for Industry 3.1.3 Position feedback-related reference designs 4.0 servo drives.......................9 for robotic systems............................47 2.2 Servo drives for robotic systems 4. Sensing and vision technologies 2.2.1 The impact of an isolated gate driver. 13 4.1 TI mmWave radar sensors in robotics 2.2.2 Understanding peak source and applications..................................48 sink current parameters . 17 4.2 Intelligence at the edge powers autonomous 2.2.3 Low-side gate drivers with UVLO versus factories .....................................53 BJT totem poles ......................19 4.3 Use ultrasonic sensing for graceful robots. 55 2.2.4 An external gate-resistor design guide for 4.4 How sensor data is powering AI in robotics. 57 gate drivers.......................... 20 4.5 Bringing machine learning to embedded 2.2.5 High-side motor current monitoring for systems .....................................61 overcurrent protection. 22 4.6 Robots get wheels to address new 2.2.6 Five benefits of enhanced PWM rejection for challenges and functions. 65 in-line motor control. 24 4.7 Vision and sensing-technology reference 2.2.7 How to protect control systems from thermal designs for robotic systems. -

MAPPING the DEVELOPMENT of AUTONOMY in WEAPON SYSTEMS Vincent Boulanin and Maaike Verbruggen
MAPPING THE DEVELOPMENT OF AUTONOMY IN WEAPON SYSTEMS vincent boulanin and maaike verbruggen MAPPING THE DEVELOPMENT OF AUTONOMY IN WEAPON SYSTEMS vincent boulanin and maaike verbruggen November 2017 STOCKHOLM INTERNATIONAL PEACE RESEARCH INSTITUTE SIPRI is an independent international institute dedicated to research into conflict, armaments, arms control and disarmament. Established in 1966, SIPRI provides data, analysis and recommendations, based on open sources, to policymakers, researchers, media and the interested public. The Governing Board is not responsible for the views expressed in the publications of the Institute. GOVERNING BOARD Ambassador Jan Eliasson, Chair (Sweden) Dr Dewi Fortuna Anwar (Indonesia) Dr Vladimir Baranovsky (Russia) Ambassador Lakhdar Brahimi (Algeria) Espen Barth Eide (Norway) Ambassador Wolfgang Ischinger (Germany) Dr Radha Kumar (India) The Director DIRECTOR Dan Smith (United Kingdom) Signalistgatan 9 SE-169 72 Solna, Sweden Telephone: +46 8 655 97 00 Email: [email protected] Internet: www.sipri.org © SIPRI 2017 Contents Acknowledgements v About the authors v Executive summary vii Abbreviations x 1. Introduction 1 I. Background and objective 1 II. Approach and methodology 1 III. Outline 2 Figure 1.1. A comprehensive approach to mapping the development of autonomy 2 in weapon systems 2. What are the technological foundations of autonomy? 5 I. Introduction 5 II. Searching for a definition: what is autonomy? 5 III. Unravelling the machinery 7 IV. Creating autonomy 12 V. Conclusions 18 Box 2.1. Existing definitions of autonomous weapon systems 8 Box 2.2. Machine-learning methods 16 Box 2.3. Deep learning 17 Figure 2.1. Anatomy of autonomy: reactive and deliberative systems 10 Figure 2.2. -

Robotics2007-09-Jack
Robotics Domain Task Force Final Agenda ver.1.0.2 robotics/2007-09-01 OMG Technical Meeting - Jacksonville, FL, USA -- Sep. 24-28 , 2007 TF/SIG http://robotics.omg.org/ Host Joint (Invited) Agenda Item Purpose Room Monday WG activity 9:00 10:00 Robotics Robotics Steering Committee Arrangement - all volunteers City Terrace 11, 3rd FL 10:00 12:00 Robotics Services WG(2h): Human Robot Interaction RFP draft Mee ing discussion - Su-Young Chi City Terrace 11, 3rd FL 12:00 13:00 LUNCH River Terrace 1, 3rd FL 13:00 18:00 Architecture Board Plenary City Terrace 9, 3rd FL 13:00 17:00 Robotics Services WG(4h): Robotic Localiza ion Services Meeting discussion - Kyuseo Han, Yeon-Ho Kim and Shuichi Nishio City Terrace 10, 3rd FL Tuesday WG activities 10:00 12:00 Robotics Services WG(3h): Human Robot Interaction RFP draft Mee ing discussion - Su-Young Chi City Terrace 11, 3rd FL 12:00 13:00 LUNCH River Terrace 1, 3rd FL 13:00 17:00 Robotics Services WG(4h): Robotic Localiza ion Services Meeting discussion - Kyuseo Han, Yeon-Ho Kim and Shuichi Nishio City Terrace 11, 3rd FL Wednesday Robotics Plenary 9:00 10:00 Robotics WG Reports and Roadmap Discussion reporting and (Service WG) discussion 10:00 11:00 Robotics Contact Reports: presentation and City Terrace 5, 3rd FL - Makoto Mizukawa(Shibaura-IT), and Yun-Koo Chung(ETRI) discussion 11:00 11:30 Robotics Publicity SC Report, Next meeting Agenda Discussion presentation and discussion 11:30 Adjourn joint plenary mee ing 11:30 12:00 Robotics Robotics WG Co-chairs Planning Session planning for next City Terrace -

Robots and Robotic Devices -- Safety Requirements for Personal Care Robots
Robots and robotic devices -- Safety requirements for personal care robots Foreword ISO (the International Organization for Standardization) is a worldwide federation of national standards bodies (ISO member bodies). The work of preparing International Standards is normally carried out through ISO technical committees. Each member body interested in a subject for which a technical committee has been established has the right to be represented on that committee. International organizations, governmental and non- governmental, in liaison with ISO, also take part in the work. ISO collaborates closely with the International Electrotechnical Commission (IEC) on all matters of electrotechnical standardization. The procedures used to develop this document and those intended for its further maintenance are described in the ISO/IEC Directives, Part 1. In particular the different approval criteria needed for the different types of ISO documents should be noted. This document was drafted in accordance with the editorial rules of the ISO/IEC Directives, Part 2. www.iso.org/directives Attention is drawn to the possibility that some of the elements of this document may be the subject of patent rights. ISO shall not be held responsible for identifying any or all such patent rights. Details of any patent rights identified during the development of the document will be in the Introduction and/or on the ISO list of patent declarations received. www.iso.org/patents Any trade name used in this document is information given for the convenience of users and does not constitute an endorsement. The committee responsible for this document is ISO/TC 184, Automation systems and integration, Subcommittee SC 2, Robots and robotic devices. -

Standardiseringsprosjekter Og Nye Standarder
Annonseringsdato: 2012-11-23 Listenummer: 11/2012 Standardiseringsprosjekter og nye standarder Listenummer: 11/2012 Side: 1 av 180 01 Generelt. Terminologi. Standardisering. Dokumentasjon 01 Generelt. Terminologi. Standardisering. Dokumentasjon Standardforslag til høring - europeiske (CEN) EN ISO 8044:1999/prA1 Korrosjon av metaller og legeringer - Grunnleggende termer og definisjoner - Endringsblad 1 (ISO 8044:1999/DAM 1:2012) Corrosion of metals and alloys - Basic terms and definitions - Amendment 1 (ISO 8044:1999/DAM 1:2012) Språk: en Kommentarfrist: 18.03.2013 prEN ISO 2692 Geometrical product specifications (GPS) - Geometrical tolerancing - Maximum material requirement (MMR), least material requirement (LMR) and reciprocity requirement (RPR) (ISO/DIS 2692:2012) Språk: en Kommentarfrist: 26.12.2012 prEN ISO 5527 Korn - Terminologi (ISO/DIS 5527:2012) Cereals - Vocabulary (ISO/DIS 5527:2012) Språk: en Kommentarfrist: 05.12.2012 Standardforslag til høring - internasjonale (ISO) ISO 3040:2009/DAmd 1 Språk: en Kommentarfrist: 02.01.2013 ISO/DIS 2076 Textiles - Man-made fibres - Generic names [Revision of third edition (ISO 2076:1989)] Språk: en Kommentarfrist: 12.12.2012 ISO/DIS 2076 Textiles -- Man-made fibres -- Generic names Språk: en Kommentarfrist: 09.12.2012 ISO/DIS 2692 Geometrical Product Specification (GPS) -- Geometrical tolerancing -- Maximum material requirement (MMR) and least material requirement (LMR) Språk: en Kommentarfrist: 26.12.2012 ISO/DIS 2692 Geometrical product specifications (GPS) -- Geometrical tolerancing -- Maximum material requirement (MMR), least material requirement (LMR) and reciprocity requirement (RPR) Språk: en Kommentarfrist: 23.12.2012 ISO/DIS 2789 Information and documentation -- International library statistics Språk: en Kommentarfrist: 11.01.2013 ISO/DIS 5527 Cereals -- Vocabulary Språk: en Kommentarfrist: 05.12.2012 Listenummer: 11/2012 Side: 2 av 180 01 Generelt. -
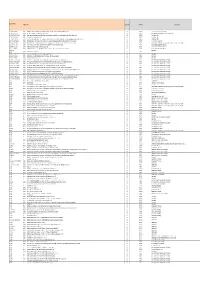
STANDARDS LIST Neu.Xlsx
Document‐Number Published Title Organization Committee Committee Title IEC 100/2536/CD * IEC 63002 2015‐07 IEC 63002, Ed. 1.0: Idenficaon and CommunicaonInteroperability Method for External Power Supplies Used WithPortable Compung Devices (TA 14) IEC IEC/TC 100 Audio, video and multimedia systems and equipment IEC 115/105/CD *IEC/TR 62978 2015‐01 IEC/TR 62978, Ed. 1: Guidelines on Asset Management forHVDC Installaons IEC IEC/TC 115 High Voltage Direct Current (HVDC) transmission for DC voltages above 100 kV IEC 118/29/DPAS* IEC/PAS 62746‐199 2013‐09 System interfaces and communication protocol profiles relevant for systems connected to the smart grid ‐ Open Automated Demand Response (OpenADR 2.0 Profile Specification) IEC IEC/PC 118 Smart grid user interface IEC 118/46/CD *IEC 62746‐10‐2 2014‐12 OASIS Energy Interoperation Version 1.0 Specification IEC IEC/PC 118 Smart grid user interface IEC 118/47/CD * IEC 62746‐10‐1 2015‐01 IEC 62746‐10‐1: Systems interface between customer energymanagement system and the power management system ‐ Part10 ‐1: Open Automated Demand Response (OpenADR 2.0bPro file Specificaon) IEC IEC/PC 118 Smart grid user interface IEC 22H/192/CD * IEC/TS 62040‐4‐1 2015‐04 IEC/TS 62040‐4‐1: Uninterrupble power systems (UPS) ‐ Part 4‐1: Environmental aspects ‐ Product Category Rules (PCR) for life Cycle Assessment and environmental declaraons IEC IEC/SC 22H Uninterruptible power systems (UPS) IEC 3/1224A/CD * IEC 81346‐2 2015‐05 Industrial systems, installaons and equipment and industrialproducts ‐ Structuring principles and reference designaons ‐ Part 2: Classificaon of objects and codes for classes IEC IEC/TC 3 Information structures and elements, identification and marking principles, documentation and graphical symbols IEC 3D/225A/CD * IEC 62656‐5 2014‐03 IEC 62656‐5, Ed. -

Standards Terms, Abbreviations, Codes & Titles
Association for Advancing Automation (A3) 2018 - Standards Terms, Abbreviations, Codes & Titles Standards Designation Code, Short Title or Definition Group Term, or Abbreviation Version ANSI STANDARDS & SUPPLEMENTAL DOCUMENTS ANSI B11 B11 B11, Safety of Machinery (Family of standards); managed by B11 Standards, Inc. ANSI ANSI B11.0-2015 B11.0 Safety of Machines: General requirements and risk assessment [being updated; planned publication: 2019] ANSI ANSI B11.19-2010 B11.19 Performance Criteria for Safeguarding [being updated; planned publication of revision: 2019] ANSI ANSI B11.20-2017 B11.20 Safety Requirements for the Integration of Machinery into a System [abbreviated IMS] [note new title; no technical changes] ANSI B56 B56 Industrial Truck Safety Standards (Family of standards); managed by ITSDF ANSI ANSI/ITSDF B56.5-2012 B56.5 Safety Standard for Driverless, Automatic Guided Industrial Vehicles and Automated Functions of Manned Industrial Vehicles [abbreviated AGV] ANSI ANSI/PMMI B155.1-2016 B155.1 Safety Requirements for Packaging and Processing Machinery ANSI R15 R15 Robot Safety Standards (Family of standards); managed by Robotic Industries Association (RIA) ANSI ANSI/RIA R15.06-2012 R15.06 American National Standard for Industrial Robots and Robot Systems - Safety Requirements [U.S. National Adoption of 10218- 1,2:2011] ANSI ANSI/RIA R15.08-201X R15.08 American National Standard on Industrial Mobile Robots and Robot Systems - Safety Requirements [in development] ANSI RIA TR R15.306-2016 TR 306 [Technical Report for Industrial