ANTI-VIRUS ARTIFACTS III // by Devisha Rochlani
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cost of a Cyber Incident)
CO ST OF A CYBER INCIDENT: S YSTEMATIC REVIEW AND C ROSS-VALIDATION OCTOBER 26, 2020 1 Acknowledgements We are grateful to Dr. Allan Friedman, Dr. Lawrence Gordon, Jay Jacobs, Dr. Sasha Romanosky, Matthew Shabat, Kelly Shortridge, Steven Surdu, David Tobar, Brett Tucker and Sounil Yu for the review comments and helpful feedback on the earlier draft of the report. The authors would like to thank CISA staff for support and advice on this project. 2 Table of Contents 1. Objectives .................................................................................................................................................................... 7 2. Results in Brief .......................................................................................................................................................... 8 3. Analysis ...................................................................................................................................................................... 16 3.1. Per-Incident Cost and Loss Estimates .............................................................................................. 18 3.1.1. Cross-Validation: Primary Loss Data for Large and Small Incidents .................................. 20 3.1.2. Reconciliation of Per-Incident Cost Studies .................................................................................. 26 3.1.3. Per-Record Estimates ............................................................................................................................. 29 3.2. Aggregate -

Checks to Avoid Malware Protect Your Laptop with Security Essentials
What is Malware? Malware is software that can infect you computer and can be a virus or malicious software that can harm & slow your system or try to steal your personal information. To help avoid malware follow the check list below. Checks to avoid Malware Check you have updated Antivirus software installed such as Microsoft Security Essentials Install and run an Anti-Malware program such as Malwarebytes Uninstall any Peer 2 Peer software such as Limewire or Vuze Be careful with email attachments and never respond to mails asking for your password Protect your Laptop with Security Essentials Microsoft Security Essentials is a free antivirus software product for Windows Vista, 7 & 8. It pro- vides protection against different types of malware such as computer virus, spyware, rootkits, trojans & other malicious software. Download & install Security Essentials from the following link http:// www.microsoft.com/security_essentials/ Clear Infections using Malwarebytes Malware bytes is free to download & install from http://www.malwarebytes.org Once installed it is recommended that you run a Full Scan of your laptop to check for any malware that may reside on the system. Once complete, follow the on screen instructions to finish removing any threats found. You should regularly run updates and scans to ensure your system remains clean. It is also advisable to scan external storage devices such as USB keys as they can spread infections. If the above criteria are fully met, ISS staff at the service desk on the ground floor of the library are happy to investigate problems on your laptop For more information go to http://www.dcu.ie/iss ISS online service desk: https://https://iss.servicedesk.dcu.ie Follow ISS on Twitter @ISSservice . -
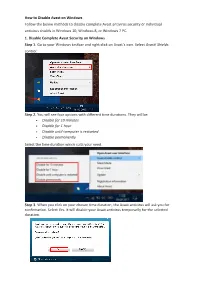
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Kaspersky Managed Service Providers Program
Kaspersky for Business MOBILE CONTROLS CLOUD ENDPOINT NETWORK SECURITY REPORTING VIRTUALIZATION SIEM SUPPORT SERVERS SERVICES CLOUD APPS Kaspersky Managed Service Providers Program Technical Reference Guide www.kaspersky.com #truecybersecurity Table of contents Program benefits 1 MSP program requirements 1 Products 2 Training and certification 5 Professional services 5 Technical designs 6 Kaspersky Endpoint Security Cloud 6 Kaspersky Endpoint Security for Business Select 6 Kaspersky Endpoint Security for Business Advanced 6 Kaspersky Hybrid Cloud Security 7 Kaspersky Security for Microsoft Office 365 8 Kaspersky Security for Mail Server 8 Kaspersky Security for Internet Gateways 9 Customer onboarding checklist 10 Appendix A 11 Appendix B 12 Appendix C 13 Appendix D 17 Program benefits • Flexible licensing allow you to choose between a monthly subscription and an annual license. Because you own the product license, there’s no need to spend time administrating contract renewals with customers — extending licenses is easy; no special action is required. • Increase sales revenues with volume-based discounts — the more customers you have, the less you pay. Pricing depends on the total number of devices of all customers. Sell more and gain bigger discounts. • Be even more efficient and grow your client base without having to hire additional engineers. With built-in best practices that drive operational efficiency, you’ll improve your tech-to-device ratio and boost your bottom line. Increase your scalability and protect more endpoints with fewer headaches. • Improved usability. Kaspersky Lab understands the importance of ease of use when it comes to security, and our design and usability specialists are closely involved in product development. -

Key Benefits Core Technologies and Technical Features
Advanced threat prevention Malwarebytes Endpoint Security is an innovative platform that delivers powerful multi- layered defense for smart endpoint protection. Malwarebytes Endpoint Security enables small and large enterprise businesses to thoroughly protect against the latest malware and advanced threats—including stopping known and unknown exploit attacks. Key Benefits Blocks zero-hour malware Easy management Reduces the chances of data exfiltration and saves Simplifies endpoint security management and identifies on IT resources by protecting against zero-hour vulnerable endpoints. Streamlines endpoint security malware that traditional security solutions can miss. deployment and maximizes IT management resources. Saves legacy systems Scalable threat prevention Protects unsupported programs by armoring Deploys protection for every endpoint and scales as vulnerabilities against exploits. your company grows. Increases productivity Detects unprotected systems Maintains end-user productivity by preserving Discovers all endpoints and installed software on your system performance and keeping staff on revenue- network. Systems without Malwarebytes that are positive projects. vulnerable to cyber attacks can be easily secured. Core Technologies and Technical Features Anti-Malware Proactive anti-malware/anti-spyware scanning Three system scan modes (Quick, Flash, Full) engine Enables selection of the most efficient system scan Detects and eliminates zero-hour and known based on endpoint security requirements and available viruses, Trojans, worms, rootkits, adware, and system resources. spyware in real time to ensure data security and network integrity. Extends its protection to Windows Server operating systems. | Santa Clara, CA | malwarebytes.com | [email protected] | 1.800.520.2796 Advanced threat prevention Malicious website blocking Advanced malware remediation Prevents access to known malicious IP addresses Employs delete-on-reboot to remove persistent or so that end users are proactively protected from deeply embedded malware. -

Antivirus – Internet Security Software
AntiVirus – Internet Security Software Recommended AntiVirus Software to use with OfficeEMR™: Norton AntiVirus Symantec Endpoint Protection Business Class – Enterprise – AntiVirus Solution AntiVirus ONLY software products WITHOUT additional Firewalls What Happens with Internet Security Software Products and OfficeEMR™: Provide an additional Firewall and/or Shields Can prevent you from accessing secure Web Sites such as https://www.officemd.net Scan every Web Page that you go to when it loads Can make screens in OfficeEMR™ take a long time to load Can prevent our AutoConfigure from running Can prevent scanning documents into OfficeEMR™ from completing What You Can Do: Setup our Web Site www.officemd.net as an exception in its Firewall. --- or --- Turn off (Disable) the additional Firewall included and / or applicable Shields Contact Technical Support via the software company’s Web Site o many offer e-mail, phone, and/or chat for technical support o get help with and options available to be able to access secure (https://...) Web --- or --- Sites o get help with and options available for making www.officemd.net an exception o get help with and options available for turning off their Firewall and / or applicable Shields. --- or --- Uninstall and Install the AntiVirus ONLY version of that software product. --- or --- Uninstall and Install a different AntiVirus ONLY software product. Revised 05/2009 AntiVirus – Internet Security Software More Detailed Information: Internet Security Software Products provide an added Firewall and / or Shields to help block malicious content or Web Sites while surfing on the Web. Without changing settings, by default, Internet Security Software Products will scan every Web Page that you go to when it loads. -

Antivirus Software Before It Can Detect Them
Computer virus A computer virus is a computer program that can copy itself and infect a computer without the permission or knowledge of the owner. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware, and spyware programs that do not have the reproductive ability. A true virus can only spread from one computer to another (in some form of executable code) when its host is taken to the target computer; for instance because a user sent it over a network or the Internet, or carried it on a removable medium such as a floppy disk, CD, DVD, or USB drive. Viruses can increase their chances of spreading to other computers by infecting files on a network file system or a file system that is accessed by another computer.[1][2] The term "computer virus" is sometimes used as a catch-all phrase to include all types of malware. Malware includes computer viruses, worms, trojan horses, most rootkits, spyware, dishonest adware, crimeware, and other malicious and unwanted software), including true viruses. Viruses are sometimes confused with computer worms and Trojan horses, which are technically different. A worm can exploit security vulnerabilities to spread itself to other computers without needing to be transferred as part of a host, and a Trojan horse is a program that appears harmless but has a hidden agenda. Worms and Trojans, like viruses, may cause harm to either a computer system's hosted data, functional performance, or networking throughput, when they are executed. Some viruses and other malware have symptoms noticeable to the computer user, but many are surreptitious. -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10
Consumer Security Products Performance Benchmarks (Edition 2) Antivirus & Internet Security Windows 10 January 2020 Document: Consumer Security Products Performance Benchmarks (Edition 2) Authors: J. Han, D. Wren Company: PassMark Software Date: 13 January 2020 Edition: 2 File: Consumer_Security_Products_Performance_Benchmarks_2020_Ed_2.docx Consumer Security Performance Benchmarks 2019 PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 REVISION HISTORY ............................................................................................................................................ 3 REFERENCES ...................................................................................................................................................... 3 EXECUTIVE SUMMARY ...................................................................................................................................... 4 OVERALL SCORE ................................................................................................................................................ 5 PRODUCTS AND VERSIONS ............................................................................................................................... 6 PERFORMANCE METRICS SUMMARY ................................................................................................................ 7 TEST RESULTS ................................................................................................................................................ -

RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC
NOT FOR RELEASE, PUBLICATION OR DISTRIBUTION, IN WHOLE OR IN PART, DIRECTLY OR INDIRECTLY, IN, INTO OR FROM ANY JURISDICTION WHERE TO DO SO WOULD CONSTITUTE A VIOLATION OF THE RELEVANT LAWS OR REGULATIONS OF SUCH JURISDICTION FOR IMMEDIATE RELEASE THIS ANNOUNCEMENT CONTAINS INSIDE INFORMATION 10 August 2021 RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC. to be effected by means of a Scheme of Arrangement under Part 26 of the Companies Act 2006 Summary Further to the announcements made by NortonLifeLock Inc. (“NortonLifeLock”) and Avast plc (“Avast” or the “Company”) on 14 July 2021, the boards of NortonLifeLock and Avast are pleased to announce that they have reached agreement on the terms of a recommended merger of Avast with NortonLifeLock, in the form of a recommended offer by Nitro Bidco Limited (“Bidco”), a wholly- owned subsidiary of NortonLifeLock, for the entire issued and to be issued ordinary share capital of the Company (the “Merger”). It is intended that the Merger will be effected by means of a Court- sanctioned scheme of arrangement under Part 26 of the Companies Act (the “Scheme”). The boards of NortonLifeLock and Avast believe the Merger has compelling strategic logic and represents an attractive opportunity to create a new, industry leading consumer Cyber Safety business, leveraging the established brands, technical expertise and innovation of both groups to deliver substantial benefits to consumers, shareholders and other stakeholders. Under the terms of the Merger, Avast Shareholders will be entitled to receive: for each Avast Share held: USD 7.61 in cash and 0.0302 of a New NortonLifeLock Share in respect of their entire holding of Avast Shares (the “Majority Cash Option”). -

Aluria Security Center Avira Antivir Personaledition Classic 7
Aluria Security Center Avira AntiVir PersonalEdition Classic 7 - 8 Avira AntiVir Personal Free Antivirus ArcaVir Antivir/Internet Security 09.03.3201.9 x64 Ashampoo FireWall Ashampoo FireWall PRO 1.14 ALWIL Software Avast 4.0 Grisoft AVG 7.x Grisoft AVG 6.x Grisoft AVG 8.x Grisoft AVG 8.x x64 Avira Premium Security Suite 2006 Avira WebProtector 2.02 Avira AntiVir Personal - Free Antivirus 8.02 Avira AntiVir PersonalEdition Premium 7.06 AntiVir Windows Workstation 7.06.00.507 Kaspersky AntiViral Toolkit Pro BitDefender Free Edition BitDefender Internet Security BullGuard BullGuard AntiVirus BullGuard AntiVirus x64 CA eTrust AntiVirus 7 CA eTrust AntiVirus 7.1.0192 eTrust AntiVirus 7.1.194 CA eTrust AntiVirus 7.1 CA eTrust Suite Personal 2008 CA Licensing 1.57.1 CA Personal Firewall 9.1.0.26 CA Personal Firewall 2008 CA eTrust InoculateIT 6.0 ClamWin Antivirus ClamWin Antivirus x64 Comodo AntiSpam 2.6 Comodo AntiSpam 2.6 x64 COMODO AntiVirus 1.1 Comodo BOClean 4.25 COMODO Firewall Pro 1.0 - 3.x Comodo Internet Security 3.8.64739.471 Comodo Internet Security 3.8.64739.471 x64 Comodo Safe Surf 1.0.0.7 Comodo Safe Surf 1.0.0.7 x64 DrVirus 3.0 DrWeb for Windows 4.30 DrWeb Antivirus for Windows 4.30 Dr.Web AntiVirus 5 Dr.Web AntiVirus 5.0.0 EarthLink Protection Center PeoplePC Internet Security 1.5 PeoplePC Internet Security Pack / EarthLink Protection Center ESET NOD32 file on-access scanner ESET Smart Security 3.0 eTrust EZ Firewall 6.1.7.0 eTrust Personal Firewall 5.5.114 CA eTrust PestPatrol Anti-Spyware Corporate Edition CA eTrust PestPatrol