Accurate, Instrumentation-Free, and Visible Attack Investigation for GUI Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
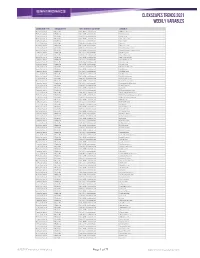
Clickscapes Trends 2021 Weekly Variables
ClickScapes Trends 2021 Weekly VariableS Connection Type Variable Type Tier 1 Interest Category Variable Home Internet Website Arts & Entertainment 1075koolfm.com Home Internet Website Arts & Entertainment 8tracks.com Home Internet Website Arts & Entertainment 9gag.com Home Internet Website Arts & Entertainment abs-cbn.com Home Internet Website Arts & Entertainment aetv.com Home Internet Website Arts & Entertainment ago.ca Home Internet Website Arts & Entertainment allmusic.com Home Internet Website Arts & Entertainment amazonvideo.com Home Internet Website Arts & Entertainment amphitheatrecogeco.com Home Internet Website Arts & Entertainment ancestry.ca Home Internet Website Arts & Entertainment ancestry.com Home Internet Website Arts & Entertainment applemusic.com Home Internet Website Arts & Entertainment archambault.ca Home Internet Website Arts & Entertainment archive.org Home Internet Website Arts & Entertainment artnet.com Home Internet Website Arts & Entertainment atomtickets.com Home Internet Website Arts & Entertainment audible.ca Home Internet Website Arts & Entertainment audible.com Home Internet Website Arts & Entertainment audiobooks.com Home Internet Website Arts & Entertainment audioboom.com Home Internet Website Arts & Entertainment bandcamp.com Home Internet Website Arts & Entertainment bandsintown.com Home Internet Website Arts & Entertainment barnesandnoble.com Home Internet Website Arts & Entertainment bellmedia.ca Home Internet Website Arts & Entertainment bgr.com Home Internet Website Arts & Entertainment bibliocommons.com -

Just Eat Annual Report & Accounts 2017
Just Eat plc Annual Report & Accounts 2017 Annual Report Creating the world’s greatest food community Annual Report & Accounts 2017 WorldReginfo - f5b0c721-e5d8-4dfc-a2c6-df7579591a37 Delivering more choice and convenience to create the world’s greatest food community WorldReginfo - f5b0c721-e5d8-4dfc-a2c6-df7579591a37 Introduction Our vision is to create the world’s greatest food community For our Customers, it is about offering them >> Read more about our the widest choice – whatever, whenever Customers on page 7 and wherever they want to eat. For our Restaurant Partners, we help them >> Read more about our Restaurant Partners on to reach more Customers, support their page 21 businesses and improve standards in the industry. >> Read more about our For our People, it is being part of an People on page 37 amazing global team, helping to connect 21.5 million Active Customers with our 82,300 Restaurant Partners. Strategic report Corporate governance Financial statements 2 Highlights 44 Corporate governance report 84 Independent auditor’s report 4 At a glance 46 Our Board 90 Consolidated income statement 8 Chairman’s statement 48 Report of the Board 91 Consolidated statement of other 10 Chief Executive Officer’s review 56 Report of the Audit Committee comprehensive income 14 Our business model 61 Report of the Nomination Committee 92 Consolidated balance sheet 16 Our markets 65 Report of the Remuneration 93 Consolidated statement of changes 18 Our strategy Committee in equity 19 Our key performance indicators 67 Annual report on remuneration -

List of Brands
Global Consumer 2019 List of Brands Table of Contents 1. Digital music 2 2. Video-on-Demand 4 3. Video game stores 7 4. Digital video games shops 11 5. Video game streaming services 13 6. Book stores 15 7. eBook shops 19 8. Daily newspapers 22 9. Online newspapers 26 10. Magazines & weekly newspapers 30 11. Online magazines 34 12. Smartphones 38 13. Mobile carriers 39 14. Internet providers 42 15. Cable & satellite TV provider 46 16. Refrigerators 49 17. Washing machines 51 18. TVs 53 19. Speakers 55 20. Headphones 57 21. Laptops 59 22. Tablets 61 23. Desktop PC 63 24. Smart home 65 25. Smart speaker 67 26. Wearables 68 27. Fitness and health apps 70 28. Messenger services 73 29. Social networks 75 30. eCommerce 77 31. Search Engines 81 32. Online hotels & accommodation 82 33. Online flight portals 85 34. Airlines 88 35. Online package holiday portals 91 36. Online car rental provider 94 37. Online car sharing 96 38. Online ride sharing 98 39. Grocery stores 100 40. Banks 104 41. Online payment 108 42. Mobile payment 111 43. Liability insurance 114 44. Online dating services 117 45. Online event ticket provider 119 46. Food & restaurant delivery 122 47. Grocery delivery 125 48. Car Makes 129 Statista GmbH Johannes-Brahms-Platz 1 20355 Hamburg Tel. +49 40 2848 41 0 Fax +49 40 2848 41 999 [email protected] www.statista.com Steuernummer: 48/760/00518 Amtsgericht Köln: HRB 87129 Geschäftsführung: Dr. Friedrich Schwandt, Tim Kröger Commerzbank AG IBAN: DE60 2004 0000 0631 5915 00 BIC: COBADEFFXXX Umsatzsteuer-ID: DE 258551386 1. -

APSCC Monthly E-Newsletter JANUARY 2017
APSCC Monthly e-Newsletter JANUARY 2017 The Asia-Pacific Satellite Communications Council (APSCC) e-Newsletter is produced on a monthly basis as part of APSCC’s information services for members and professionals in the satellite industry. Subscribe to the APSCC monthly newsletter and be updated with the latest satellite industry news as well as APSCC activities! To renew your subscription, please visit www.apscc.or.kr/sub4_5.asp. To unsubscribe, send an email to [email protected] with a title “Unsubscribe.” News in this issue has been collected from 1 to 31 December 2016. INSIDE APSCC APSCC Session at PTC'17, What do End Users Actually Want? 16 January 2017, Honolulu, Hawaii, USA, www.ptc.org/ptc17 While new technology is good, as are lower prices, are we actually meeting end user needs in the Pacific? Why/why not? What is being provisioned now and future? What gaps we must fill? Where does the satcom model fall short? The session, “What do End Users Actually Want?” would discuss end user needs across various applications and markets. Pierre-Jean Beylier, CEO, SpeedCast Richard Swardh, SVP, Comtech EF Data Imran Malik, RVP, O3b Networks Jacques-Samuel Prolon, General Manager, Kacific Broadband Satellites Moderated by Chris Baugh, President, NSR APSCC members can enjoy discounted rate when PTC’17 registration. Gregg Daffner Elected as APSCC President Gregg Daffner (CEO, GapSat) was elected and inaugurated as the President of APSCC at the 2016 APSCC General Assembly held on 13 December 2016. As the main representative of APSCC, Gregg will be responsible for setting the policies and goals of APSCC in consultation with the APSCC Board of Directors, Vice Presidents and Executive Director. -

Contentreport C
CISCCONTENTONTENT:CONTENRTRREPORTEPORTEPORT CC ReviewОбзорОбзор of новостейaudiovisualновостей рынка content производства production and ии дистрибуциидистрибуции distribution аудиовизуальногоаудиовизуальногоin the CIS countries контента контента Media«»«MediaМ«»ÌЕДИÅÄÈ ResourcesА ResourcesÀРЕСУРСЫÐÅÑÓÐÑÛ МManagement ÌManagementЕНЕДЖМЕНТÅÍÅÄÆÌÅÍÒ» №21,№ №2№121(9) December №2 13 1April января, April, 1 April, 30, 20142012 20132011 2012 тема FOCUSномераfocUs DEARсловоDEAR CCOLLEAGUES редакциOLLEAgUESи УжеWeWe areareв первые happy to дни presentpresent нового you you the годаthe December Aprilнам, issue редак issue of цthe иofи andПервыйLast seriesautumn номер you’ll members alsoContent find of Russian theReport detailed association выходит report of вon televiк ануthe н- EgorКИНОТЕАТРАЛЬНЫ BorschEvsky:Й ContentCIS:the CIS:Content Report, Content Report сразу Report whereстало where понятно,we we tried tried toчто to gathergather в 2011 theм recentСтарогоsion and deals movie Нового of producers international года, который chose distributors Red (наконецто) Square with Screen the за - mostmost interesting interesting up-to-date up-to-date information information about about rapidly rap- CIS-partners.ings as the most important industry event of the season. РЫН О К В КРАИН Е все мы будем усердно и неустанно трудиться. За вершает череду праздников, поэтому еще раз “TodayTV MARKETS: Ukrainian У visual : нимаясьdevelopingidly developing подготовкой content content production первого production andвыпуска distributionand обзораdistribution mar -

Chefs Redefine Southeast Asian Cuisine
FOOD FANATICS FOOD FOOD PEOPLE MONEY & SENSE PLUS Burgers Road Trip! Cost Cutters Trends Can it ever be too big? There’s a food revolution in Ten steps to savings, What’s warming up, page 12 Philadelphia, page 39 page 51 page 19 GOT THE CHOPS GOT FOODFANATICS.COM SPRING 2013 GOT THE CHOPS SPRING 2013 Chefs redefine Southeast Asian cuisine PAGE 20 SPRING 2013 ™ SPEAK SPICE, SOUTHEAST ASIAN STYLE Sweet DOWNLOAD THE MAGAZINE ON IPAD success FOOD The Cooler Side of Soup 08 Chill down seasonal soups for a hot crowd pleaser. Flippin’ Burgers 12 Pile on the wow factor to keep up with burger pandemonium. All Grown Up 16 Tricked out interpretations of the classic tater tot prove that this squat spud is little no more. COVER STORY Dude, It’s Not Fusion 20 Chefs dig deep into Southeast Asian cuisine for modern takes on flavors they love. Sticky Spicy Sweets and Wings FOOD PEOPLE Want a Piece of Me? 32 Millennials make up the dining demographic that every operator wants. Learn how to get them. Road Trip to Philadelphia 39 A food revolution is happening in the See this recipe made right birthplace of the Declaration of Independence. now on your smartphone Simplot Sweets® don’t take away from traditional fry sales, they simply sweeten your Who Can Cook? bottom line. With their farm-cured natural sweetness and variety of kitchen-friendly cuts, 40 Martin Yan can, of course. And after 34 years in the business, there’s no stopping him. you can use them to create stunning appetizers in addition to incredible fry upgrades. -
Kroger: Value Trap Or Value Investment - a Deep Due Diligence Dive
Kroger: Value Trap Or Value Investment - A Deep Due Diligence Dive seekingalpha.com /article/4115509-kroger-value-trap-value-investment-deep-due-diligence-dive Chuck 10/23/2017 Walston The acquisition of Whole Foods Market, announced by Amazon ( AMZN) last June sent shockwaves through the grocery industry. 1/20 When the deal was finalized in August, Amazon announced plans to lower the prices of certain products by as much as a third. The company also hinted at additional price reductions in the future. Amazon Prime members will be given special savings and other in-store benefits once the online retail giant integrates its point of sale system into Whole Foods stories. 2/20 Analysts immediately predicted a future of widespread margin cuts across the industry. Well before Amazon's entry into stick and brick groceries, Kroger ( KR) experienced deterioration in comparable store sales. 3/20 (Source: Kroger Investor Presentation slideshow) (Source: SEC Filings via SA contributor Quad 7 Capital) Additionally, Kroger's recent results reflect gross margin compression. 4/20 (Source: SEC Filings via SA contributor Quad 7 Capital) After the takeover, Whole Foods initiated a price war. According to Reuters, prices at a Los Angeles Whole Foods store are lower on some products than comparable goods sold in a nearby Ralph's store owned by Kroger. The Threat From Amazon Research conducted by Foursquare Labs Inc. indicates the publicity surrounding Amazon's recent acquisition of Whole Foods, combined with the announcement of deep price cuts, resulted in a 25% surge in customer traffic. Not content to attack conventional grocers with their panoply of online food services and margin cuts, Amazon registered a trademark application for a meal-kit service. -

Filed by Grubhub Inc. Pursuant to Rule 425 Under the Securities Act of 1933 and Deemed Filed Pursuant to Rule 14A-12 Under the S
Filed by Grubhub Inc. pursuant to Rule 425 under the Securities Act of 1933 and deemed filed pursuant to Rule 14a-12 under the Securities Exchange Act of 1934 Subject Company: Grubhub Inc. Commission File No.: 001-36389 GRUB Employee Email From: Matt Maloney, CEO Subject: A New Chapter for Grubhub Team, I know this note reaches you all at a time of great uncertainty. In addition to a pandemic that has disrupted our lives and impacted our friends and family, our country is struggling with widespread frustration, anger and sadness based on recent events that have reminded us, yet again, that we have a long way to go before our country achieves racial equality. As you know, Grubhub is committed to supporting you and doing our part to help you and our broader community, including our diners, restaurants and drivers through this incredibly challenging time. However, this email is to communicate something different – an important decision made by the board today and with my recommendation. After 20 years of building this industry from the ground up in the U.S., today we begin a new chapter for Grubhub. We have signed a definitive agreement with European industry leader Just Eat Takeaway.com in an all-stock merger to create the largest global online ordering/delivery company in the world (outside of China). Together, we will connect more than 360,000 restaurants to over 70 million active diners in 25 countries. You can read the press release here, and I encourage you to join our town hall meeting at 4:30 p.m. -

Just Eat Annual Report & Accounts 2017
Just Eat plc Annual Report & Accounts 2017 Annual Report Creating the world’s greatest food community Annual Report & Accounts 2017 WorldReginfo - f5b0c721-e5d8-4dfc-a2c6-df7579591a37 Delivering more choice and convenience to create the world’s greatest food community WorldReginfo - f5b0c721-e5d8-4dfc-a2c6-df7579591a37 Introduction Our vision is to create the world’s greatest food community For our Customers, it is about offering them >> Read more about our the widest choice – whatever, whenever Customers on page 7 and wherever they want to eat. For our Restaurant Partners, we help them >> Read more about our Restaurant Partners on to reach more Customers, support their page 21 businesses and improve standards in the industry. >> Read more about our For our People, it is being part of an People on page 37 amazing global team, helping to connect 21.5 million Active Customers with our 82,300 Restaurant Partners. Strategic report Corporate governance Financial statements 2 Highlights 44 Corporate governance report 84 Independent auditor’s report 4 At a glance 46 Our Board 90 Consolidated income statement 8 Chairman’s statement 48 Report of the Board 91 Consolidated statement of other 10 Chief Executive Officer’s review 56 Report of the Audit Committee comprehensive income 14 Our business model 61 Report of the Nomination Committee 92 Consolidated balance sheet 16 Our markets 65 Report of the Remuneration 93 Consolidated statement of changes 18 Our strategy Committee in equity 19 Our key performance indicators 67 Annual report on remuneration -

Download on Our Platform and We Have Obtained Licenses from Many Content Providers
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Form 20-F (Mark One) ¨ REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR 12(g) OF THE SECURITIES EXCHANGE ACT OF 1934 or x ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2013. or ¨ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to or ¨ SHELL COMPANY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 Date of event requiring this shell company report Commission file number: 000-51469 Baidu, Inc. (Exact name of Registrant as specified in its charter) N/A (Translation of Registrant’s name into English) Cayman Islands (Jurisdiction of incorporation or organization) Baidu Campus No. 10 Shangdi 10th Street Haidian District, Beijing 100085 The People’s Republic of China (Address of principal executive offices) Jennifer Xinzhe Li, Chief Financial Officer Telephone: +(86 10) 5992-8888 Email: [email protected] Facsimile: +(86 10) 5992-0000 Baidu Campus No. 10 Shangdi 10th Street, Haidian District, Beijing 100085 The People’s Republic of China (Name, Telephone, Email and/or Facsimile number and Address of Company Contact Person) Securities registered or to be registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered American depositary shares (ten American depositary shares representing one Class A ordinary share, The NASDAQ Stock Market LLC par value US$0.00005 per share) (The NASDAQ Global Select Market) Class A ordinary shares, par value US$0.00005 per share* The NASDAQ Stock Market LLC (The NASDAQ Global Select Market) * Not for trading, but only in connection with the listing on The NASDAQ Global Select Market of American depositary shares. -

Applications: S
Applications: S This chapter contains the following sections: • Sabah, on page 9 • Safari, on page 10 • SAFT, on page 11 • Sage, on page 12 • Sahibinden, on page 13 • Saks Fifth Avenue, on page 14 • Salesforce.com, on page 15 • Salesforce.com Live Agent, on page 16 • Sam's Club, on page 17 • Sametime, on page 18 • SAMR, on page 19 • Samsung, on page 20 • Samsung Push Notification, on page 21 • SANity, on page 22 • Sanook.com, on page 23 • SAP, on page 24 • SAP HostControl, on page 25 • SASCDN, on page 26 • SATNET, on page 27 • SATNET and Backroom EXPAK, on page 28 • SATNET Monitoring, on page 29 • SaveFrom, on page 30 • Sberbank of Russia, on page 31 • SBS, on page 32 • SCC Security, on page 33 • SCCM, on page 34 • SCCM Remote Control, on page 35 • SCCP, on page 36 • Schedule Transfer Protocol, on page 37 • schuelerVZ, on page 38 • Schwab, on page 39 • ScienceDirect, on page 40 Applications: S 1 Applications: S • SCO Desktop Administration Server, on page 41 • Sco I2 Dialog Daemon, on page 42 • SCO System Administration Server, on page 43 • SCO Web Server Manager 3, on page 44 • SCO WebServer Manager, on page 45 • scohelp, on page 46 • Scopia, on page 47 • Scopia Audio, on page 48 • Scopia Video, on page 49 • Scorecard Research, on page 50 • Scottrade, on page 51 • SCPS, on page 52 • Scribd, on page 53 • Scribd Upload, on page 54 • Scribol, on page 55 • SCSI-ST, on page 56 • SCTP, on page 57 • scx-proxy, on page 58 • SDNS-KMP, on page 59 • SDRP, on page 60 • Seamonkey, on page 61 • Search-Result.com, on page 62 • Searchnu, on page 63 • -

User Browsing Graph: Structure, Evolution and Application1
User Browsing Graph: Structure, Evolution and Application1 Yiqun Liu, Min Zhang, Shaoping Ma, Liyun Ru State Key Lab of Intelligent Technology and Systems Tsinghua National Laboratory for Information Science and Technology Department of Computer Science and Technology Tsinghua University, Beijing, 100084, China P.R. [email protected] ABSTRACT don’t work very well in this new situation. This paper focuses on ‘user browsing graph’ which is constructed Recently, the wisdom of the crowd is paid much attention in with users’ click-through behavior modeled with Web access logs. Web search researches, e.g. [7], [8] and [9]. In their work, users’ User browsing graph has recently been adopted to improve Web browsing behavior is usually considered as implicit feedback search performance and the initial study shows it is more reliable information for page relevance and importance. For example, Liu than hyperlink graph for inferring page importance. However, et. al. constructed ‘user browsing graph’ with search log data [10]. structure and evolution of the user browsing graph haven’t been They proposed a page importance estimation algorithm called fully studied and many questions remain to be answered. In this BrowseRank which performs on the user browsing graph. It is paper, we look into the structure of the user browsing graph and believed that the link structure in user browsing graph is more its evolution over time. We try to give a quantitative analysis on reliable than hyperlink graph because users actually follow links the difference in graph structure between hyperlink graph and in the browsing graph. user browsing graph, and then find out why link analysis Liu’s initial study shows that the BrowseRank algorithm works algorithms perform better on the browsing graph.