Computer Simulation of M2M Communication Subscriber Locating
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2G 3G 4G 5G > 181,400
Annual report 2019 Operational Results Infrastructure Network expansion MegaFon is the unrivalled leader in Russia 1 by number of base stations, with We are committed to maximising the speed and reliability of communications services for our subscribers, and are continuously investing in infrastructure and innovative technology. > 181,400 stations 2G 3G 4G 5G 1990s 2000s 2010s 2016–2019 Voice and SMS Mobile data and high- Mobile broadband and full- Ultrafast mobile internet, quality voice services scale IP network full-scale support of IoT ecosystems, and ultra-reliability MegaFon was the first in Russia to • provide 2G services in all • roll out a full-scale • launch the first 4G • demonstrate a record Russian regions commercial 3G network network (2012); connection speed • launch a commercial of 2.46 Gbit/s VoLTE network (2016); on a smartphone • demonstrate a data on a 5G network (2019); rate in excess of 1 Gbit/s • launch a 5G on a commercial lab – in collaboration smartphone (2018) with Saint Petersburg State University’s Graduate School of Management (2019) 1 According to Roscomnadzor as of 19 March 2020. 48 About MegaFon 14–35 Strategic report 36–81 Sustainability 82–109 Corporate governance, securities, and risk management 110–147 Financial statements and appendix 148–226 MegaFon’s base stations, ‘000 4G/LTE coverage, % 2019 70.0 50.7 60.7 181.4 2019 82 2018 70.5 49.4 49.6 169.5 2018 79 2017 69.1 48.0 40.6 157.7 2017 74 2G 3G 4G/LTE MegaFon’s strong portfolio of unique high-speed data 4G/LTE networks spectrum assets is an important competitive advantage. -

Northern African Wireless Communications Is a Controlled Circulation Bi-Monthly Magazine
For communications professionals in north, west, east & central Africa NORTHERN AFRICAN WIRELESSCOMMUNICATIONS FEBRUARY/MARCH 2021 Volume 19 Number 6 l Satellite: a thing of the past or technology for the future? l The growing importance of FWA and Wi-Fi on the move l Sanjeev Verma of Squire Technologies on mobile fraud NAWC 2103 p1 (Cover).indd 1 07/04/2021 18:03 NEWS 4 SOUTHERN AFRICAN WIRELESS COMMUNICATIONS January/February 2019 NAWC 2011 p2.indd 4 09/11/2020 18:16 NORTHERN AFRICAN CONTENTS WIRELESSCOMMUNICATIONS FEBRUARY/ 5 NEWS u MARCH 2021 Connecting Europe with Africa u Algerian minister says ‘5G not a priority’ Volume 19 u TheAngle and ABS extend partnership Number 6 u South Sudan launches first ever 4G internet u Nexign helps CSPs 5 NEWS u Kenyan auditor raises concerns over fibre u Safaricom launches commercial 5G network 18 FEATURE u Tunisia launches first home-made satellite u TE and Libyans discuss joint cooperation Liquid Intelligent Technologies is u MTN Uganda and NITA launch health app a pan-African technology group with u Outages affect WIOCC clients across Africa capabilities across 14 countries, primarily u Expresso Senegal gets 4G green light in Sub-Saharan Africa. Established in u Libya seeks help from international partners 2005, Liquid has firmly established 13 WIRELESS BUSINESS itself as the leading pan-African digital WIOCC names new sales manager infrastructure provider with an extensive 24 FEATURE network spanning over 73,000 KM. Liquid 18 FEATURE Intelligent Technologies is redefining Shaping the future of satcoms Network, Cloud and Cyber Security offerings through strategic partnerships 22 INDUSTRY VIEW Necessity is the mother of invention with leading global players, innovative business applications, intelligent cloud 24 FEATURE services and world-class security to the 28 WIRELESS SOLUTIONS Fixed wireless access and Wi-Fi on the move African continent. -

2020 Annual Report
Online Annual Report Gazprom Neft Performance review Sustainable 2020 at a glance 62 Resource base and production development CONTENTS 81 Refining and manufacturing 4 Geographical footprint 94 Sales of oil and petroleum products 230 Sustainable development 6 Gazprom Neft at a glance 114 Financial performance 234 Health, safety and environment (HSE) 8 Gazprom Neft’s investment case 241 Environmental safety 10 2020 highlights 250 HR Management 12 Letter from the Chairman of the Board of Directors 254 Social policy Technological Strategic report development Appendices 264 Consolidated financial statements as at and for the year ended 31 December 2020, with the 16 Letter from the Chairman of the Management Board 122 Innovation management independent auditor’s report About the Report 18 Market overview 131 2020 highlights and key projects 355 Company history This Report by Public Joint Stock Company Gazprom Neft (“Gazprom 28 2020 challenges 135 Import substitution 367 Structure of the Gazprom Neft Group Neft PJSC”, the “company”) for 2020 includes the results of operational activities of Gazprom Neft PJSC and its subsidiaries, 34 2030 Strategy 370 Information on energy consumption at Gazprom collectively referred to as the Gazprom Neft Group (the “Group”). 38 Business model Neft Gazprom Neft PJSC is the parent company of the Group and provides consolidated information on the operational and financial 42 Company transformation 371 Excerpts from management’s discussion and performance of the Group’s key assets for this Annual Report. The analysis of financial condition and results of list of subsidiaries covered in this Report and Gazprom Neft PJSC’s 44 Digital transformation operations interest in their capital are disclosed in notes to the consolidated Governance system IFRS financial statements for 2020. -

Samena Trends March 2021
Feb-Mar, Volume 12, 2021 A SAMENA Telecommunications Council Publication www.samenacouncil.org S AMENA TRENDS FOR SAMENA TELECOMMUNICATIONS COUNCIL'S MEMBERS BUILDING DIGITAL ECONOMIES Eng. Olayan M. H.E. Hamad Obaid Al H.E. Dr. Mohamed Al Alwetaid Mansoori Tamimi Group CEO Director General Governor stc, Saudi Arabia TDRA, UAE CITC, Saudi Arabia THIS MONTH DIGITAL ECONOMIC GROWTH: FROM POLICY TO REALITY FEB-MAR, VOLUME 12, 2021 Contributing Editors Knowledge Contributions Publisher Izhar Ahmad BT SAMENA Telecommunications Council SAMENA Javaid Akhtar Malik China Mobile International Etisalat Subscriptions TRENDS goetzpartners [email protected] Huawei Editor-in-Chief Nexign Advertising Bocar A. BA Omantel [email protected] PCCW Global RIPE NCC SAMENA TRENDS Speedchecker [email protected] Tech Mahindra Tel: +971.4.364.2700 CONTENTS 04 EDITORIAL FEATURED 05 13 REGIONAL & MEMBERS UPDATES Members News Regional News 75 SATELLITE UPDATES Satellite News 87 WHOLESALE UPDATES Governor-CITC (Saudi Arabia) Wholesale News Speaks to SAMENA Council 07 93 TECHNOLOGY UPDATES Technology News The SAMENA TRENDS eMagazine is wholly owned and operated by The SAMENA 99 REGULATORY & POLICY UPDATES Telecommunications Council (SAMENA Regulatory News Council). Information in the eMagazine is not intended as professional services advice, A Snapshot of Regulatory and SAMENA Council disclaims any liability Activities in the SAMENA Region for use of specific information or results thereof. Articles and information contained Regulatory Activities DG-TDRA (UAE) Speaks to in this publication are the copyright of Beyond the SAMENA Region SAMENA Council SAMENA Telecommunications Council, (unless otherwise noted, described or stated) 09 and cannot be reproduced, copied or printed ARTICLES in any form without the express written 54 Etisalat Driving the Digital Future to permission of the publisher. -

Annual Report 2020 a Message from Nexign CEO Nexign Annual Report 2020
Annual Report 2020 A Message from Nexign CEO Nexign Annual Report 2020 In 2020 our life moved into virtual space. Habitual and much need- We were actively working on Nexign's product portfolio in order to ed physical contact, as well as face-to-face meetings, became in- support operators in the conditions of the 'new normal'. advisable and even dangerous. We all ended up in a digital world where communication with colleagues and relatives is maintained That is exactly why we developed the Nexign Instant BSS solution through a thin screen and friendly voices are heard only through that makes it possible to launch new business projects within less headphones. than 4 months. In this artificial space we had to deal with a number of urgent To develop the capabilities for omnichannel interaction with challenges. How do we continue to hold negotiations with new subscribers, Nexign purchased the company called STORM customers and carry out our obligations under existing projects Technologies, an expert in the area of digital user experience while in isolation? How can we support the team? How do we management. add new specialists to the team? How do we keep the high work standards that we are so used to? In addition, Nexign started developing the Open-Source-based Universal Digital Billing product. This way we will assist our I cannot claim that those challenges were completely new for us. customers in optimising TCO and adapting quicker to changing As any company with subdivisions based in different countries and business needs. regions, we tried to operate in such a way that our business process- es would not depend on a certain location on the map. -

Southern Asian Region SOUTHERN ASIAN
For communications professionals in the southern Asian region SOUTHERN ASIAN WIRELESSCOMMUNICATIONS Q1 2021 Volume 14 Number 1 l Satellite: a thing of the past or a thing of the future? l The growing importance of FWA and Wi-Fi on the move l Southern Asian mobile fraud, according to Evina Experts in RF over Fiber SASIA 21Q1 p1 (Cover).indd 1 01/04/2021 17:12 NEWS 4 SOUTHERN AFRICAN WIRELESS COMMUNICATIONS January/February 2019 SASIA 19Q4 p4 (Rajant).indd 4 01/04/2021 13:03 SOUTHERN ASIAN CONTENTS COMMUNICATIONSWIRELESS Q1 2021 5 NEWS 5 NEWS u Volume 14 Cambodia’s NIG going ahead u Globe sees traffic spike Number 1 u Nokia chosen for 5G rollout u NBTC considers payment for 5G licences u SES supplies broadband to villages u Etisalat launches 4G LTE service u Wireless Logic expands global footprint 18 FEATURE I u Thaicom searches for LEO partner u Bangladeshi players fork out ViaLite designs and manufactures u Pakistan’s internet disrupted RF over fiber links and systems for a u Maldives to Sri Lanka subsea cable goes live range of applications including Satcom, 13 WIRELESS BUSINESS LEO and MEO; transporting satellite Vyke and x-Mobility sign two new deals for signals between antennas and control APAC expansion rooms. The links are also used in Mil- 25 FEATURE II 18 FEATURE Aero, Defence, Broadcast, Cellular and Shaping the future of satcoms Network Timing etc. ViaLite’s links 22 INDUSTRY VIEW include: L-Band HTS, VSAT, C-Band Evina’s David Lofti explains how mobile (covering 500 MHz-7.5 GHz), Hyper- carriers can stop the financial havoc Wide Dynamic Range, Ultra-Wideband, 25 FEATURE UHF/VHF, Satellite IF, SIGINT, GPS & 28 WIRELESS SOLUTIONS Fixed wireless access and Wi-Fi on the move more. -

Russian M&A Review 2019
Russian M&A Review 2019 February 2020 KPMG in Russia and the CIS kpmg.ru Foreword Lydia Petrashova Head of Deal Advisory Russia and the CIS Partner We are pleased to present you with This year has already seen a the fifteenth anniversary edition number of M&A market studies of our annual KPMG Russian M&A being released, which underlines Review. the importance and relevance of understanding its changes. At the The past year witnessed the most same time, each study comes to positive trends in investment activity a markedly different conclusion, for the whole post-sanctions period. and we wish to draw our readers’ This was reflected in an increased attention to which analysis number of deals, growth in average methodology is used. KPMG has deal value, and greater foreign been releasing the Russian M&A investment – not only from the East review for 15 consecutive years, (which has become the main focus consistently applying the same of investment relations with Russia), methodology. Our conclusions and but also western companies. We forecasts are based on a thorough have observed that, despite some analysis of M&A market data and our issues persisting vis-à-vis internal extensive experience in supporting and external political and economic M&A deals and processes across plans, investors are now more the Russian market. confident about executing their deal strategies within a stabilising In this edition of the Russian M&A Russian environment. Review we reflect on key recent trends and how these will influence A further shift in focus by the M&A in upcoming years. -

Sustainable Development Report 2019 / 2 / 1 As Respecting Humanrights
Sustainable Development Report 2019 Sustainable Development Report 2019 4 Statement from the chairman of the management board Gazprom Neft CONTENTS at a glance Responsibility for the well-being of future generations and care for the environment are integrated in our strategy and business model Online Sustainable Development Report 2019 8 Gazprom Neft at a glance 11 Geographical footprint 12 Business model 18 Company strategy and sustainable development About the Report Dear Readers, We are delighted to present Gazprom Neft’s Sustainable Sustainability Repot1 for 2019. This is the company’s 12th non-financial public report, which outlines the company’s approaches to complying development with the principles of corporate social responsibility, its contribution to sustainable social and economic management development, and its environmental initiatives. Management system based on the accommodation The Report discloses information of stakeholders’ interests and balanced management about Gazprom Neft PJSC as well as its subsidiaries and controlled entities (referred of economic, environmental and social aspects of business to in this Report as “Gazprom Neft” or “the company”) for the calendar year of 20192. The company’s financial and operating performance is presented based on Gazprom Neft PJSC’s consolidated data. Unless otherwise specified, 28 Corporate culture the data on the company’s labour relations, social initiatives and environmental performance relates 32 Corporate governance to Gazprom Neft PJSC as well as its subsidiaries 38 Sustainability risk management and controlled entities in Russia and the CIS. 42 Anti-corruption activities Information provided herein was obtained from corporate reports, information requests in line 43 Respecting human rights with the guidelines contained in the nonfinancial 45 Sustainability technologies reporting standards, and corporate media. -

Pdf Annual Report 2019 Pdf 6.0 MB
Annual report 2019 Providing opportunities Annual report 2019 Contents 4 Chairman’s Statement 8 Chief Executive’s Review 36 82 110 Strategic Report Sustainability Corporate 38 Market Overview 84 Our approach Governance, Securities, 14 to sustainability 42 Disital Strategy in Action and Risk Management About MegaFon 86 Stakeholder engagement 46 Business Model 112 Corporate Governance 20 Performance Highlights 97 Occupational health 48 Operational Results and safety 133 Securities 22 Providing Opportunities 78 Financial Performance 98 Social responsibility 137 Risk Management and Internal Control 26 Assets and resources and charity 32 Geography 106 Procurement 34 History 107 Ethics and human rights 35 Key Events 108 Anti-corruption 148 108 Our approach to environmental protection Financial Statements and Appendix 150 Consolidated Financial Statements 218 Material Topics and Materiality Matrix 220 GRI tables 223 Glossary 225 Contacts About this Report Preliminarily approved by the Board of Directors In this Report “MegaFon” or the “Company” of PJSC MegaFon on 6 May 2020. refer to PJSC MegaFon and its controlled entities, For more PJSC “MegaFon” refers to Public Joint-Stock information Read This Annual Report presents data from 1 January through Company “MegaFon”. please visit: Online Report at: 31 December 2019 and information about certain events https://corp.megafon.com ar2019.megafon.eng occurring in 2020. Immaterial discrepancies in totals and subtotals in the charts and tables of the Annual Report are This Annual Report has been prepared in accordance due to rounding. with the Global Reporting Initiative (GRI) Guidelines for reporting on sustainable development. For more information see Appendix: Material Topics and Materiality Matrix. -

Cimdata Cpdm Late-Breaking News
PLM Industry Summary Sara Vos, Editor Vol. 21 No. 29 - Friday, July 19, 2019 Contents CIMdata News _____________________________________________________________________ 2 CIMdata to Host a Free Webinar on How to Measure Digital Transformation ________________________2 CIMdata Publishes China PLM Market Report ________________________________________________4 CIMdata Publishes PLM Market and Solution Provider Report ___________________________________6 CIMdata Vice-President Stan Przybylinski Featured in Digital Engineering Digital Thread Article – “Stuck in Neutral?” ____________________________________________________________________________8 Platform Architecture: A Core Digital Transformation Enabler (CIMdata Commentary) ________________8 Acquisitions ______________________________________________________________________ 12 Aspen Technology Acquires Mnubo and Sabisu to Deliver Scalable AI-Driven Solutions for the Smart Enterprise ____________________________________________________________________________12 Centric PLM: Individualizing the customer experience _________________________________________13 HCL Technologies Announces Close of Acquisition of Select IBM Products _______________________15 Lectra announces the acquisition of Retviews ________________________________________________15 Sandvik acquires stake in leading Additive Manufacturing service provider_________________________16 Company News ____________________________________________________________________ 17 Accenture Appoints Julie Sweet Chief Executive Officer and -
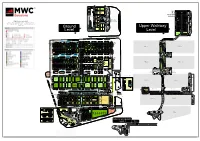
MWC Barcelona 2020 MWC Barcelona
33.75 8.0M100 10.5 10.5 354.38m² 33.75 i i 15 10 10 OA8.9 OA8.7 OA8.5 a 15.63 54.49 13 13 13 13 13 13 Apple Fluge a 8.0I20 Goods Lift 8.1 Max Weight - 4000 Kg Tree Size - 2.36m x 3.5m Door Width - 2.67m 8.0I50 S Door Height - 2.17m 195m² 130m² 130m² a a 15.81 15.81 Blue 15 10 10 Ant 23.76 23.76 20 gsmExchange OA8.11 15.63247.11m² 8.0I10 15.63 a a 8.08 8.08 Registration 20 20 OA8 dc 126.29m² 1294.68m² Optima 8.01 EXIT ONLY 15.63 57.1854.49 h 14.06 8.0H60 g FAST TRACK 7 4 4 4 4 4 4 4 6 6 4 4 4 4 4 4 4 CC8.16 CC8.15 CC8.14 CC8.13 CC8.12 CC8.11 CC8.10 CC8.9 CC8.8 CC8.7 CC8.6 CC8.5 CC8.4 CC8.3 CC8.2 CC8.1 OA8.3 8.0H50 3.5 3.5 3.5 3.5 a OpenX Limited MoPub 20 400m² HALL 4.5 21m² 4.521m² GSMA 8 8 8 8 8 8 8 8 8 8 8 8 8 8 8 8 8 8 8 SPA 8 8 SPA 8 8 SPA 8 8 8 8 8 20 Macom Meeting AlgoriX AppsFlyer Condor Condor Condor OA8.13 Nexign Nexign Nexign Nexign Taptica CC8.Tech2 10 10 6 6 Electronics Electronics Electronics ASA ASA Room 2 4.5 4.5 Rigging 10.13m² 6.36 CC8.Tech1 a 10.13m² 6.36 10 10 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 32m² 27.37 27.37 26.74 26.74 a 4 4 4 4 4 4 4 4 4 4 4 4 4 4 Blue Ant 70m² Badge 7 Cloakroom CC8 Rooms 20 200m² Fast Track 10 10 8 8 5 5 10 CC8.26 CC8.21 CC8.20 CC8.19 20 Goods Lift 8.2 CC8.30 CC8.28 6.36 CC8.17 Max Weight - 6000 Kg 4.5 4.5 Size - 2.36m x 5.28m CC8.Tech4 OA8.15 a Door Width - 2.69m 6.36 10.13m² Door Height - 2.78m GSMA CC8.Tech3 GSMA 8 Collection 8 8 8 8 8 8 10.13m² 8 8 8 Smaato8 8 8 8 Meeting 6 6 Meeting GSMA Room 3 CC8.24 CC8.23 Inc. -

Annual Report 2019 Gazprom Neft at a Glance
Annual Report 2019 Gazprom Neft at a glance Online TABLE CONTENTS OF Annual Report 2019 4 Gazprom Neft at a glance 6 Geographical footprint 8 Gazprom Neft investment case 10 2019 highlights 12 Letter from the Chairman of the Board of Directors About this Report This Report by the Public Joint Stock Company Strategic report Gazprom Neft (Gazprom Neft PJSC, the company) for 2019 includes the results of operational activity of Gazprom Neft PJSC and its subsidiaries, collectively referred to as the Gazprom Neft Group (the Group). Gazprom Neft PJSC is the parent company of the Group and provides consolidated information on the operational and financial performance of the Group’s key assets for this Annual Report. The list of subsidiaries 16 The implementation of Strategy 2030 covered in this Report and the shares held by Gazprom Neft PJSC in their capital are disclosed 18 Letter from the Chairman in notes to the consolidated IFRS financial of the Management Board statements for 2019. 20 Market overview This Report is prepared based on analysis of operational data, consolidated IFRS financial 28 Global trends and their impact indicators and international GRI guidelines. on the Gazprom Neft strategy Information provided in the Report has been verified 30 Strategy 2030 by the Audit Committee and approved by the Board of Directors and the Annual General Meeting 34 Business model of Shareholders of the Company. 36 2019 results In calculations of shareholdings, percentages, 38 Digital transformation and total amounts, the Annual Report may contain discrepancies as a result of rounding. Data provided 42 Operational transformation in the Annual Report may differ insignificantly 46 Organisational transformation from previous disclosures, also as a result of rounding.