Drive Investigation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

List of MS-DOS Commands - Wikipedia, the Free Encyclopedia Page 1 of 25
List of MS-DOS commands - Wikipedia, the free encyclopedia Page 1 of 25 List of MS-DOS commands From Wikipedia, the free encyclopedia In the personal computer operating systems MS -DOS and PC DOS, a number of standard system commands were provided for common Contents tasks such as listing files on a disk or moving files. Some commands were built-in to the command interpreter, others existed as transient ■ 1 Resident and transient commands commands loaded into memory when required. ■ 2 Command line arguments Over the several generations of MS-DOS, ■ 3 Windows command prompt commands were added for the additional ■ 4 Commands functions of the operating system. In the current ■ 4.1 @ Microsoft Windows operating system a text- ■ 4.2 : mode command prompt window can still be ■ 4.3 ; used. Some DOS commands carry out functions ■ 4.4 /* equivalent to those in a UNIX system but ■ 4.5 ( ) always with differences in details of the ■ 4.6 append function. ■ 4.7 assign ■ 4.8 attrib ■ 4.9 backup and restore Resident and transient ■ 4.10 BASIC and BASICA commands ■ 4.11 call ■ 4.12 cd or chdir ■ 4.13 chcp The command interpreter for MS-DOS runs ■ 4.14 chkdsk when no application programs are running. ■ 4.15 choice When an application exits, if the command ■ 4.16 cls interpreter in memory was overwritten, MS- ■ 4.17 copy DOS will re-load it from disk. The command ■ 4.18 ctty interpreter is usually stored in a file called ■ 4.19 defrag "COMMAND.COM". Some commands are ■ 4.20 del or erase internal and built-into COMMAND.COM, ■ 4.21 deltree others are stored on disk in the same way as ■ 4.22 dir application programs. -
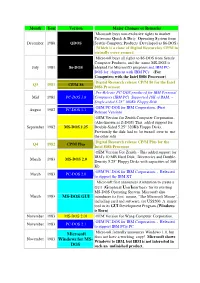
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

File Allocation Table - Wikipedia, the Free Encyclopedia Page 1 of 22
File Allocation Table - Wikipedia, the free encyclopedia Page 1 of 22 File Allocation Table From Wikipedia, the free encyclopedia File Allocation Table (FAT) is a file system developed by Microsoft for MS-DOS and is the primary file system for consumer versions of Microsoft Windows up to and including Windows Me. FAT as it applies to flexible/floppy and optical disc cartridges (FAT12 and FAT16 without long filename support) has been standardized as ECMA-107 and ISO/IEC 9293. The file system is partially patented. The FAT file system is relatively uncomplicated, and is supported by virtually all existing operating systems for personal computers. This ubiquity makes it an ideal format for floppy disks and solid-state memory cards, and a convenient way of sharing data between disparate operating systems installed on the same computer (a dual boot environment). The most common implementations have a serious drawback in that when files are deleted and new files written to the media, directory fragments tend to become scattered over the entire disk, making reading and writing a slow process. Defragmentation is one solution to this, but is often a lengthy process in itself and has to be performed regularly to keep the FAT file system clean. Defragmentation should not be performed on solid-state memory cards since they wear down eventually. Contents 1 History 1.1 FAT12 1.2 Directories 1.3 Initial FAT16 1.4 Extended partition and logical drives 1.5 Final FAT16 1.6 Long File Names (VFAT, LFNs) 1.7 FAT32 1.8 Fragmentation 1.9 Third party -

Azure RTOS Filex User Guide
Azure RTOS FileX User Guide Published: February 2020 For the latest information, please see azure.com/rtos This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. © 2020 Microsoft. All rights reserved. Microsoft Azure RTOS, Azure RTOS FileX, Azure RTOS GUIX, Azure RTOS GUIX Studio, Azure RTOS NetX, Azure RTOS NetX Duo, Azure RTOS ThreadX, Azure RTOS TraceX, Azure RTOS Trace, event-chaining, picokernel, and preemption-threshold are trademarks of the Microsoft group of companies. All other trademarks are property of their respective owners. Safety Certifications IEC 61508 up to SIL 4 IEC 62304 up to SW safety Class C ISO 26262 ASIL D EN 50128 SW-SIL 4 UL/IEC 60730, UL/IEC 60335, UL 1998 MISRA-C:2004 Compliant MISRA C:2012 Compliant Part Number: 000-1001 Revision 6.0 Contents About This Guide 7 • Organization 7 • Guide Conventions 8 • FileX Data Types 9 • Customer Support Center 10 Chapter 1: Introduction to FileX 13 • FileX Unique Features 14 • Safety Certifications 15 • Powerful Services of FileX 17 • Easy-to-use API 18 • exFAT Support 18 • Fault Tolerant Support 19 • Callback Functions 21 • Easy Integration 21 Chapter 2: Installation and Use of FileX 23 • Host Considerations 24 • Target Considerations 25 • Product Distribution 25 • FileX Installation -

FAT32 File Structure Prof
FAT32 File Structure Prof. James L. Frankel Harvard University Version of 9:45 PM 24-Mar-2021 Copyright © 2021 James L. Frankel. All rights reserved. FAT32 Source Documentation • The reference document you should use is the Microsoft Extensible Firmware Initiative FAT32 File System Specification • On class web site under The NXP/Freescale ARM -> microSDHC Card • It is available on the class web site at https://cscie92.dce.harvard.edu/spring2021/Microsoft%20Extensible%20Firmware%20Initiative%20FAT32%2 0File%20System%20Specification,%20Version%201.03,%2020001206.pdf under Online Papers Used in Class • Important correction to this document concerns the DIR_CrtTimeTenth field in the FAT 32 Byte Directory Entry Structure • The name and description of this field is incorrect • Instead of DIR_CrtTimeTenth, we will use the name DIR_CrtTimeHundth • Here is the correct description of this field (to update the text on page 23): • Hundredths of a second time at file creation time. This field contains a count of hundredths of a second. Because the seconds portion of the DIR_CrtTime field denotes a creation time with a granularity of 2 seconds, this field contains a number of hundredths of a second (0 to 199, inclusively) that denotes a number of seconds from 0 to 1.99, inclusively, that may increment the number of seconds in addition to supplying the number of hundredths of a second. • There is also a typo on page 25 where a field is referred to as DIR_CrtTimeMil (which does not exist), and, as corrected here, should be DIR_CrtTimeHundth 2 SD Documentation • Documentation for the SD controller in the K70 • K70 Sub-Family Reference Manual, Rev. -

OS/2 and Windows Operating Environments
89 CHAPTER 12 OS/2 and Windows Operating Environments Specifying File Attributes for OS/2 or Windows 89 Determining the SAS Release Used to Create a Member 89 Using Version 8 Short Filename Extensions on FAT-style Disk Drives 90 Creating a Transport File on Tape 91 OS/2 and Windows Idiosyncrasies 91 Error Message 91 Encrypted data is invalid 91 Specifying File Attributes for OS/2 or Windows You can apply file attributes by using FTP or the FTP access method options in the FILENAME statement, whichever is applicable. For details about the syntax for the FILENAME statement, see SAS Language Reference: Dictionary. For details, see “Using the FILENAME Statement to Specify File Attributes for All Hosts” on page 32. Determining the SAS Release Used to Create a Member Table 12.1 on page 89 identifies the supported file types that are created on the OS/2 or the Windows host by member and by SAS release: Table 12.1 OS/2 and Windows Filename Extension by Member and SAS Release Member Type Version 6 Filename Version 8 Filename Extensions1 Extension (Short) (Long) SAS .sas .sas .sas PROGRAM (DATA .ss2 .ss7 .sas7bpgm step) DATA .sd2 .sd7 .sas7bdat INDEX .si2 .si7 .sas7bndx CATALOG .sc2 .sc7 .sas7bcat MDDB .sm2 .sm7 .sas7bmdb 90 Using Version 8 Short Filename Extensions on FAT-style Disk Drives R Chapter 12 Member Type Version 6 Filename Version 8 Filename Extensions1 Extension (Short) (Long) DMDB .sb2 .s7m .sas7bdmd PROC SQL view .sv2 .sv7 .sas7bvew 1 For details about OS/2 and Windows Version 8 short and long filename extensions, see “Using Version 8 Short Filename Extensions on FAT-style Disk Drives” on page 90. -

12 Investigating Windows Systems
CNIT 121: Computer Forensics 12 Investigating Windows Systems NTFS and File System Analysis NTFS and FAT • FAT was the old file system used by MS-DOS, Windows 95, Windows 98 • NTFS was the replacement Master File Table (MFT) • Defines how disk space is allocated and utilized • How files are created and deleted • How metadata is stored and updates MFT Contents • Primary source of metadata in NTFS • Contains or references everything about a file • Timestamps • Size • Attributes (such as permissions) • Parent directory • Contents The Evidence • Each NTFS volume has its own MFT • Stored in the volume root as a file named $MFT • You need raw disk access to acquire $MFT • It's not accessible through Windows Explorer or standard API calls MFT Structure • On a standard hard drive with 512-byte sectors • A series of 1024-byte records or "entries" • One for each file and directory on a volume • First 16 entries are reserved for essential NTFS artifacts • $MFT itself, $LogFile, and more MFT in WinHex MFT Entry Contents • Record type (file or directory) • Record # (integer) • Parent record # • Active/Inactive flag • Deleted files are inactive • Attributes (metadata) Attributes • $STANDARD_INFORMATION • $FILE_NAME • $DATA Deleted Files • Deleting a file causes its MFT record to be marked "inactive" • Nothing else is changed, until this record is re-used • The file's contents and its metadata can be recovered • But NTFS will always re-use an existing MFT entry before creating a new one • So inactive entries only last for seconds or minutes on the operating system -

Filesystem On-Disk Structures for FAT, HPFS, NTFS, JFS, Extn and Reiserfs Presentation Contents
On-disk filesystem structures Jan van Wijk Filesystem on-disk structures for FAT, HPFS, NTFS, JFS, EXTn and ReiserFS Presentation contents Generic filesystem architecture (Enhanced) FAT(32), File Allocation Table variants HPFS, High Performance FileSystem (OS/2 only) NTFS, New Technology FileSystem (Windows) JFS, Journaled File System (IBM classic or bootable) EXT2, EXT3 and EXT4 Linux filesystems ReiserFS, Linux filesystem FS-info: FAT, HPFS, NTFS, JFS, EXTn, Reiser © 2019 JvW Who am I ? Jan van Wijk Software Engineer, C, C++, Rexx, PHP, Assembly Founded FSYS Software in 2001, developing and supporting DFSee from version 4 to 16.x First OS/2 experience in 1987, developing parts of OS/2 1.0 EE (Query Manager, later DB2) Used to be a systems-integration architect at a large bank, 500 servers and 7500 workstations Developing embedded software for machine control and appliances from 2008 onwards Home page: https://www.dfsee.com/ FS-info: FAT, HPFS, NTFS, JFS, EXTn, Reiser © 2019 JvW Information in a filesystem Generic volume information Boot sector, super blocks, special files ... File and directory descriptive info Directories, FNODEs, INODEs, MFT-records Tree hierarchy of files and directories Free space versus used areas Allocation-table, bitmap Used disk-sectors for each file/directory Allocation-table, run-list, bitmap FS-info: FAT, HPFS, NTFS, JFS, EXTn, Reiser © 2019 JvW File Allocation Table The FAT filesystem was derived from older CPM filesystems for the first (IBM) PC Designed for diskettes and small hard -

|||||||||III US005579517A United States Patent (19) 11) Patent Number: 5,579,517 Reynolds Et Al
|||||||||III US005579517A United States Patent (19) 11) Patent Number: 5,579,517 Reynolds et al. (45) Date of Patent: Nov. 26, 1996 (54) COMMON NAME SPACE FOR LONG AND 5,313,646 5/1994 Hendricks et al. ..................... 395/600 SHORT FILENAMES 5,359,725 10/1994 Garcia et al. ... ... 395/500 5,371,885 12/1994 Letwin ... ... 395/600 (75) Inventors: Aaron R. Reynolds, Redmond; Dennis E. 2. 2. Ea. 3: R. Adler, Mercer Island; Ralph A. a 4/5 allc. ... Lipe, Woodinville; Ray D. Pedrizetti, 5,421,001 5/1995 Methe ..................................... 395/500 Issaquah; Jeffrey T. Parsons; OTHER PUBLICATIONS Rasipuram V. Arun, both of Redmond, & T. all of Wash. Ray Duncan, "Using long filenames and extended attributes' parts 1 & 2, PC Magazine vol. 9 nos 8 & 9. pp. Assignee: Microsoft Corporation, Redmond, 317 & 305, Apr. 24 & May 15, 1990. (73) Wash. Ray Duncan, "Design Goals and Implementation of the new High Performance File System” Microsoft Systems Journal, Appl. No.: 427,004 vol. 4, No. 5, pp. 1-13, Sep. 1989. (21) a v V 9 Filed: Apr. 24, 1995 Primary Examiner-Thomas G. Black (22) Assistant Examiner-C. Pham Related U.S. Application Data Attorney, Agent, or Firm-Seed and Berry (63) Continuation of Ser. No. 41497, Apr. 1, 1993, abandoned. ' ABSTRACT (51) Int. Cl. ................................. G06F 17/30 An operating system provides a common name space for U.S. Cl 395/616. 395/425: 395/500; both long filenames and short filenames. In this common (52) A1 "395,575,364,246,364/DIG 1364,254; namespace, a long filename and a short filename are pro 66526,366. -

05 579 517 Patent Rejected
 UNITED STATES PATENT AND TRADEMARK OFFICE UNITEl> STATES DEPARTMENT OF COMMERCE Unilcd Slalcs Patent and Trademark Office Additss COMNflSSIONEK FOR I'ATEWTS PO Bin l4Ul Ali-xiiinlri;~ Viryniiii22313-I450 <tW\b ,,S"l<, g,,v APPI.ICATIC1N NCI FILING DATE I FIRST NAMED INVENTOR AUORNEY DOCKETNLI CONHKMATIUN NO 9~1/1107,007 041 19/2004 557951 7 2192 2W7 7590 091 16/2004 WOODCOCK WASHBURN LLP ONE LIBERTY PLACE, 46TH FLOOR / 1650 MARKET STRICT ART UNIT PAPER NUMBFK PHILADELPHIA, PA 19103 a'^ ^L DATE MAILED 119/lfi/2004 Please find below andlor attached an Office communication concerning this application or proceeding PTO-90C (Rev. 10f0.3) Control No. Patentunder Reexamination 901007,007 MICROSOFT CORP Office Action in Ex Parte Reexamination - Examiner Art Unit Charles Rones 21 75 I I I - The MAILING DATE ofthis communication appears on the cover sheet with the correspondence address -- 3m Responsive to the communication(s) filed on 4-10-04 . bDThis action is made FINAL. :E A statement under 37 CFR 1.530 has not been received from the patent owner. 4 shortened statutory period for response to this action is set to expire 2 month(s) from the mailing date of this letter. ^allure to respond within the period for response will result in termination of the proceeding and issuance of an ex parte reexamination :ertificate in accordance with this action. 37 CFR 1,55O(d). EXTENSIONS OF TIME ARE GOVERNED BY 37 CFR 1.550(c). f the period for response specified above is less than thirty (30) days, a response within the statutory minimum of thirty (30) days Mil be considered timely. -

Datalight ROM-DOS User's Guide
Datalight ROM-DOS User’s Guide Created: April 2005 Datalight ROM-DOS User’s Guide Copyright © 1999-2005 by Datalight, Inc . Portions copyright © GpvNO 2005 All Rights Reserved. Datalight, Inc. assumes no liability for the use or misuse of this software. Liability for any warranties implied or stated is limited to the original purchaser only and to the recording medium (disk) only, not the information encoded on it. U.S. Government Restricted Rights. Use, duplication, reproduction, or transfer of this commercial product and accompanying documentation is restricted in accordance with FAR 12.212 and DFARS 227.7202 and by a license agreement. THE SOFTWARE DESCRIBED HEREIN, TOGETHER WITH THIS DOCUMENT, ARE FURNISHED UNDER A SEPARATE SOFTWARE OEM LICENSE AGREEMENT AND MAY BE USED OR COPIED ONLY IN ACCORDANCE WITH THE TERMS AND CONDITIONS OF THAT AGREEMENT. Datalight and ROM-DOS are registered trademarks of Datalight, Inc. FlashFX ® is a trademark of Datalight, Inc. All other product names are trademarks of their respective holders. Part Number: 3010-0200-0716 Contents Chapter 1, ROM-DOS Introduction..............................................................................................1 About ROM-DOS ......................................................................................................................1 Conventions Used in this Manual .......................................................................................1 Terminology Used in this Manual ......................................................................................1