12 Investigating Windows Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Exploring the X64
Exploring the x64 Junichi Murakami Executive Officer, Director of Research Fourteenforty Research Institute, Inc. Who am I? • Junichi Murakami – @Fourteenforty Research Institute, Inc. – Both Windows and Linux kernel development – Reversing malware and P2P software, etc. – Speaker at: • Black Hat 2008 US and Japan, AVAR 2009, RSA Conference(2009-) – Instructor at Security & Programming Camp(2006-) 2 Environment • Windows 7 x64 Edition • Visual Studio 2008 • Windbg • IDA Pro Advanced – STD doesn’t support x64, an offering is needed! 4 Agenda • Windows x64 • ABI(Application Binary Interface) • API Hooking • Code Injection 5 Windows x64 • Native x64 and WoW64 • Virtual Address Space – 2^64 = 16 Exa Byte ( Exa: 10^18) – but, limited to 16TB by Microsoft • File/Registry reflection • New 64-bit APIs – IsWow64Process, GetNativeSystemInfo, etc. 6 ABI • Binary Format • Register • Calling Convention • Exception Handling • Systemcall(x64, WoW64) 11 Binary Format(Cont.) • Some fields were extended to 64-bits – IMAGE_NT_HEADERS.IMAGE_OPTIONAL_HEADER • ImageBase • SizeOfStackReserve • SizeOfStackCommit • SizeOfHeapReserve • SizeOfHeapCommit 13 Calling Convention • first 4 parameters are passed by RCX, RDX, R8, R9 – 5th and later are passed on the stack • caller allocates register home space on the stack • RAX is used for return values • leaf / non-leaf function – leaf function: never use stack – PE32+ contains non-leaf function’s information in its EXCEPTION DIRECTORY • Register’s volatility – volatile: RAX, RCX, RDX, R8-R11 15 Exception Handling • -

Through the Looking Glass: Webcam Interception and Protection in Kernel
VIRUS BULLETIN www.virusbulletin.com Covering the global threat landscape THROUGH THE LOOKING GLASS: and WIA (Windows Image Acquisition), which provides a WEBCAM INTERCEPTION AND still image acquisition API. PROTECTION IN KERNEL MODE ATTACK VECTORS Ronen Slavin & Michael Maltsev Reason Software, USA Let’s pretend for a moment that we’re the bad guys. We have gained control of a victim’s computer and we can run any code on it. We would like to use his camera to get a photo or a video to use for our nefarious purposes. What are our INTRODUCTION options? When we talk about digital privacy, the computer’s webcam The simplest option is just to use one of the user-mode APIs is one of the most relevant components. We all have a tiny mentioned previously. By default, Windows allows every fear that someone might be looking through our computer’s app to access the computer’s camera, with the exception of camera, spying on us and watching our every move [1]. And Store apps on Windows 10. The downside for the attackers is while some of us think this scenario is restricted to the realm that camera access will turn on the indicator LED, giving the of movies, the reality is that malware authors and threat victim an indication that somebody is watching him. actors don’t shy away from incorporating such capabilities A sneakier method is to spy on the victim when he turns on into their malware arsenals [2]. the camera himself. Patrick Wardle described a technique Camera manufacturers protect their customers by incorporating like this for Mac [8], but there’s no reason the principle into their devices an indicator LED that illuminates when can’t be applied to Windows, albeit with a slightly different the camera is in use. -

Minimum Hardware and Operating System
Hardware and OS Specifications File Stream Document Management Software – System Requirements for v4.5 NB: please read through carefully, as it contains 4 separate specifications for a Workstation PC, a Web PC, a Server and a Web Server. Further notes are at the foot of this document. If you are in any doubt as to which specification is applicable, please contact our Document Management Technical Support team – we will be pleased to help. www.filestreamsystems.co.uk T Support +44 (0) 118 989 3771 E Support [email protected] For an in-depth list of all our features and specifications, please visit: http://www.filestreamsystems.co.uk/document-management-specification.htm Workstation PC Processor (CPU) ⁴ Supported AMD/Intel x86 (32bit) or x64 (64bit) Compatible Minimum Intel Pentium IV single core 1.0 GHz Recommended Intel Core 2 Duo E8400 3.0 GHz or better Operating System ⁴ Supported Windows 8, Windows 8 Pro, Windows 8 Enterprise (32bit, 64bit) Windows 10 (32bit, 64bit) Memory (RAM) ⁵ Minimum 2.0 GB Recommended 4.0 GB Storage Space (Disk) Minimum 50 GB Recommended 100 GB Disk Format NTFS Format Recommended Graphics Card Minimum 128 MB DirectX 9 Compatible Recommended 128 MB DirectX 9 Compatible Display Minimum 1024 x 768 16bit colour Recommended 1280 x 1024 32bit colour Widescreen Format Yes (minimum vertical resolution 800) Dual Monitor Yes Font Settings Only 96 DPI font settings are supported Explorer Internet Minimum Microsoft Internet Explorer 11 Network (LAN) Minimum 100 MB Ethernet (not required on standalone PC) Recommended -

Programming Model Intel Itanium 64
11/11/2003 64-bit computing AMD Opteron 64 Application of Win32 Executable File Legacy 64 bit platforms Inbuilt 128-bit bus DDR memory controller with memory bandwidth speed up to 5.3GB/s. Infectors on Intel Itanium and AMD Benefits of 64-bit processors Opteron Based Win64 Systems Use of hyper transport protocol, “glueless” architecture. Oleg Petrovsky and Shali Hsieh Increased integer dynamic range Computer Associates International Inc. Available in up to 8 way configuration with the clock speeds 1 Computer Associates Plaza, Islandia, NY 11749, Much larger addressable memory space of 1.4 GHz, 1.6 GHz and 1.8 GHz . USA Benefits to database, scientific and cryptography Reuses already familiar 32-bit x86 instruction set and applications extends it to support 64-bit operands, registers and memory pointers. AMD64 Programming Model AMD64: Programming model Intel Itanium 64 X86 32-64 64 bit Itanium line of processors is being developed by Intel XMM8 X86 80-Bit Extends general use registers to 64-bit, adds additional eight 64-Bit X87 general purpose 64-bit registers. Itanium - 800 MHz, no on die L3 cache, Itanium 2 - 1GHz, RAX EAX AX 3MB L3 on die, Itanium 2003 (Madison) - 1.5 GHz, 6MB L3 on die cache, 410M transistors, largest integration on a RBX Reuses x86 instruction set. single silicon crystal today. XMM15 RCX Runs 32-bit code without emulation or translation to a native Itanium line of processors utilizes more efficient and robust XMM0 than legacy x86 instruction set architecture F instruction set. R8 L A Itanium has to use x86-to-IA-64 decoder a specifically Minimizes learning curve. -
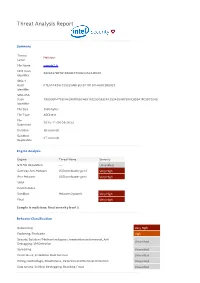
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Converting ASCII Files
Converting Data from ASCII to SPSS System Files Some data files, especially older ones, will not be available as SPSS system files, but instead will be provided with a fixed-format ASCII (American Standard Code for Information Interchange) file and an SPSS syntax file. Once you have downloaded your files and, if necessary, unzipped them: • Start SPSS and open the syntax file (the one with the “.sps” extension). • Find the “FILE HANDLE” command and replace “data-filename” with the path to your data file (the one ending in “.txt”). For example, if you download ICPSR Study 4131 (ABC News Pennsylvania Poll, Sept. 2004) in a directory on your “C” drive called “Temp,” the path created will be "C:\Temp\5268001\ICPSR_04131\DS0001_ABC_News_Pennsylvania_Poll,_Sept ember_2004__\04131-0001-Data.txt." (This is admittedly pretty unwieldy, and it might be a good idea to move and rename the file before proceeding). The FILE HANDLE: FILE HANDLE DATA / NAME="data-filename" LRECL=225. would become: FILE HANDLE DATA / NAME="C:\Temp\5268001\ICPSR_04131\DS0001_ABC_News_Pennsylvania_P oll,_September_2004__\04131-0001-Data.txt " LRECL=225. • Find the “SAVE OUTFILE” command (probably the last one in the file), and replace “spss-filename.sav” with the name and path of the SPSS system file you wish to create. If the command is preceded by an asterisk, remove the asterisk. For example, SAVE OUTFILE="spss-filename.sav". would become: SAVE OUTFILE="C:\Temp\5268001\ICPSR_04131\DS0001_ABC_News_Pennsylvania _Poll,_September_2004__\04131-0001-Data.sav". From the menu bar, click on “Run” and “All.” If no "SAVE OUTFILE" command exits, create one from scratch. -

Simple File System (SFS) Format
Simple File System (SFS) Format Version SFS-V00.01 The SFS is a simple file system format optimized for writing and for low overhead.. The advantages of this format are: • Event navigation is possible using simple content-independent file system like functions. • Very low overhead. No loss due to block size granularity • Entire valid file system can be created by appending content On the other hand, random access directory navigation is rather slow because there is no built-in indexing or directory hierarchy. For a 500MB file system containing files with 5k bytes this represents an initial search overhead of ~1-2 sec (~100,000 seeks). SFS Structure The structure of a SFS file is as follows VolumeSpec Head File1 File1 Binary Data File2 File2 Binary Data ... ... Tail VolumeSpec: This is simply a 12 byte character string representing filesystem version. For example: “SFS V00.01” Head: This is a short header record. The byte order only applies to the time field of this record. type = “HEAD” byte_order = 0x04030201 time File: The File records are a variable length record containing information about a file. type = “FILE” byte_order = 0x04030201 Sz head_sz attr reserved name.... name (continued).... “byte_order” corresponds only to this header. The endiness of the data is undefined by SFS “sz” corresponds to the datafile size. This may be any number, but the file itself will be padded to take up a multiple of 4 bytes “head_sz” this must be a multiple of 4 “attr” SFS_ATTR_INVALID: file deleted SFS_ATTR_PUSHDIR: push current path to path stack SFS_ATTR_POPDIR: pop current path from path stack SFS_ATTR_NOCD: this record doesn’t reset the basedir “name” the name of the file. -

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

IBM Education Assistance for Z/OS V2R1
IBM Education Assistance for z/OS V2R1 Item: ASCII Unicode Option Element/Component: UNIX Shells and Utilities (S&U) Material is current as of June 2013 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option Agenda ■ Trademarks ■ Presentation Objectives ■ Overview ■ Usage & Invocation ■ Migration & Coexistence Considerations ■ Presentation Summary ■ Appendix Page 2 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Version Trademarks ■ See url http://www.ibm.com/legal/copytrade.shtml for a list of trademarks. Page 3 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Presentation Objectives ■ Introduce the features and benefits of the new z/OS UNIX Shells and Utilities (S&U) support for working with ASCII/Unicode files. Page 4 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Version Overview ■ Problem Statement –As a z/OS UNIX Shells & Utilities user, I want the ability to control the text conversion of input files used by the S&U commands. –As a z/OS UNIX Shells & Utilities user, I want the ability to run tagged shell scripts (tcsh scripts and SBCS sh scripts) under different SBCS locales. ■ Solution –Add –W filecodeset=codeset,pgmcodeset=codeset option on several S&U commands to enable text conversion – consistent with support added to vi and ex in V1R13. –Add –B option on several S&U commands to disable automatic text conversion – consistent with other commands that already have this override support. –Add new _TEXT_CONV environment variable to enable or disable text conversion. -

List of MS-DOS Commands - Wikipedia, the Free Encyclopedia Page 1 of 25
List of MS-DOS commands - Wikipedia, the free encyclopedia Page 1 of 25 List of MS-DOS commands From Wikipedia, the free encyclopedia In the personal computer operating systems MS -DOS and PC DOS, a number of standard system commands were provided for common Contents tasks such as listing files on a disk or moving files. Some commands were built-in to the command interpreter, others existed as transient ■ 1 Resident and transient commands commands loaded into memory when required. ■ 2 Command line arguments Over the several generations of MS-DOS, ■ 3 Windows command prompt commands were added for the additional ■ 4 Commands functions of the operating system. In the current ■ 4.1 @ Microsoft Windows operating system a text- ■ 4.2 : mode command prompt window can still be ■ 4.3 ; used. Some DOS commands carry out functions ■ 4.4 /* equivalent to those in a UNIX system but ■ 4.5 ( ) always with differences in details of the ■ 4.6 append function. ■ 4.7 assign ■ 4.8 attrib ■ 4.9 backup and restore Resident and transient ■ 4.10 BASIC and BASICA commands ■ 4.11 call ■ 4.12 cd or chdir ■ 4.13 chcp The command interpreter for MS-DOS runs ■ 4.14 chkdsk when no application programs are running. ■ 4.15 choice When an application exits, if the command ■ 4.16 cls interpreter in memory was overwritten, MS- ■ 4.17 copy DOS will re-load it from disk. The command ■ 4.18 ctty interpreter is usually stored in a file called ■ 4.19 defrag "COMMAND.COM". Some commands are ■ 4.20 del or erase internal and built-into COMMAND.COM, ■ 4.21 deltree others are stored on disk in the same way as ■ 4.22 dir application programs. -
![Maintaining a File System File System Integrity Utility: Fsck -P [Filesystem]](https://docslib.b-cdn.net/cover/5831/maintaining-a-file-system-file-system-integrity-utility-fsck-p-filesystem-1105831.webp)
Maintaining a File System File System Integrity Utility: Fsck -P [Filesystem]
Maintaining a File System File System Integrity utility: fsck -p [fileSystem] fsck (file system check) scans the specified file systems and checks them for consistency. The kind of consistency errors that can exist include: • A block is marked as free in the bitmap but is also referenced from an inode. • A block is marked as used in the bitmap but is never referenced from an inode. • More than one inode refers to the same block. • An invalid block number. • An inode's link count is incorrect. • A used inode is not referenced from any directory. 1 file system integrity fsck -p [fileSystem] If the -p option is used, fsck automatically corrects any errors that it finds. Without the -p option, it prompts the user for confirmation of any corrections that it suggests. If fsck finds a block that is used but is not associated with a named file, it connects it to a file whose name is equal to the block's inode number in the "/lost+found" directory. If no file systems are specified, fsck checks the standard file systems listed in "/etc/fstab." Linux has specialized fsck programs for different types of file systems. For example, when checking an ext2 or ext3 file system, fsck act as a front-end to e2fsck, which is the program that actually checks the file system. 2 Display disk statistics My disk is full, my files are not saved, why?!@#$ du -- display disk usage displays the number of kB that are allocated to each of the specified filenames. If a filename refers to a directory, its files are recursively described -h option displays more human-readable -

Oracle Database Platform Guide for Windows
Oracle® Database Platform Guide 10g Release 1 (10.1) for Windows Part No. B10113-01 December 2003 Oracle Database Platform Guide, 10g Release 1 (10.1) for Windows Part No. B10113-01 Copyright © 1996, 2003 Oracle Corporation. All rights reserved. Primary Author: Craig B. Foch Contributing Author: Mark Kennedy and Helen Slattery Contributor: David Collelo The Programs (which include both the software and documentation) contain proprietary information of Oracle Corporation; they are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright, patent and other intellectual and industrial property laws. Reverse engineering, disassembly or decompilation of the Programs, except to the extent required to obtain interoperability with other independently created software or as specified by law, is prohibited. The information contained in this document is subject to change without notice. If you find any problems in the documentation, please report them to us in writing. This document is not warranted to be error-free. Except as may be expressly permitted in your license agreement for these Programs, no part of these Programs may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose. If the Programs are delivered to the U.S. Government or anyone licensing or using the programs on behalf of the U.S. Government, the following notice is applicable: Restricted Rights Notice Programs delivered subject to the DOD FAR Supplement are "commercial computer software" and use, duplication, and disclosure of the Programs, including documentation, shall be subject to the licensing restrictions set forth in the applicable Oracle license agreement.