Automated Malware Analysis Report for 234125. Exe
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Program Name Run Command About Windows Winver Add a Device
List of Run Commands in Win7/8 to Windows Managment By Shree Krishna Maharjan in some commands need to use .msc Program Name Run Command About Windows winver Add a Device devicepairingwizard Add Hardware Wizard hdwwiz Advanced User Accounts netplwiz Authorization Manager azman Backup and Restore sdclt Bluetooth File Transfer fsquirt Calculator calc Certificates certmgr Change Computer Performance Settings systempropertiesperformance Change Data Execution Prevention Settings systempropertiesdataexecutionprevention Change Printer Settings printui Character Map charmap ClearType Tuner cttune Color Management colorcpl Command Prompt cmd Component Services comexp Component Services dcomcnfg Computer Management compmgmt.msc Computer Management compmgmtlauncher Connect to a Network Projector netproj Connect to a Projector displayswitch Control Panel control Create A Shared Folder Wizard shrpubw Create a System Repair Disc recdisc Credential Backup and Restore Wizard credwiz Data Execution Prevention systempropertiesdataexecutionprevention Default Location locationnotifications Device Manager devmgmt.msc Device Pairing Wizard devicepairingwizard Diagnostics Troubleshooting Wizard msdt Digitizer Calibration Tool tabcal DirectX Diagnostic Tool dxdiag Disk Cleanup cleanmgr Disk Defragmenter dfrgui Disk Management diskmgmt.msc Display dpiscaling Display Color Calibration dccw Display Switch displayswitch DPAPI Key Migration Wizard dpapimig Driver Verifier Manager verifier Ease of Access Center utilman EFS REKEY Wizard rekeywiz Encrypting File System -

Directx 11 Extended to the Implementation of Compute Shader
DirectX 1 DirectX About the Tutorial Microsoft DirectX is considered as a collection of application programming interfaces (APIs) for managing tasks related to multimedia, especially with respect to game programming and video which are designed on Microsoft platforms. Direct3D which is a renowned product of DirectX is also used by other software applications for visualization and graphics tasks such as CAD/CAM engineering. Audience This tutorial has been prepared for developers and programmers in multimedia industry who are interested to pursue their career in DirectX. Prerequisites Before proceeding with this tutorial, it is expected that reader should have knowledge of multimedia, graphics and game programming basics. This includes mathematical foundations as well. Copyright & Disclaimer Copyright 2019 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at [email protected] -

The Tweakguides Tweaking Companion Download Page, Or to the Main Tweakguides Page Without Seeking Written Permission
WWW.TWEAKGUIDES.COM [Version 3.00 ‐ January 2006] T HE T WEAKG UIDES T WEAKING C OMPANION TABLE OF CONTENTS Table Table of Contents ........................................................................................................................................................... 2 of Copyright & Credits..................................................................................................................................................... 10 Contents Introduction................................................................................................................................................................... 11 Using this Guide .......................................................................................................................................................... 12 Basic Requirements ........................................................................................................................................................................................... 12 Different Versions of Windows ......................................................................................................................................................................... 12 Why is the Guide So Long? .............................................................................................................................................................................. 12 Recommended Software .................................................................................................................................................................................. -

Windows 7, Configuring
Microsoft 70-680 Windows 7, Configuring Microsoft 70-680 Dumps Available Here at: https://www.certification-questions.com/microsoft-exam/70-680-dumps.html Enrolling now you will get access to 551 questions in a unique set of 70- 680 dumps Question 1 Your network consists of an Active Directory domain and a Direct Access infrastructure. You install Windows 7 on a new portable computer and join the computer to the domain. You need to ensure that the computer can establish Direct Access connections. What should you do? Options: A. Install a computer certificate. B. Create a new network connection. C. Enable the Network Discovery firewall exception. D. Add the computer account to the Network Configuration Operators group. Answer: A Explanation: Certificates The Direct Access IPsec session is established when the client running Windows 7 and the Direct Access server authenticate with each other using computer certificates. Direct Access supports only certificate- based authentication. Direct Access Client Configuration Clients receive their Direct Access configuration through Group Policy. This differs from traditional VPN configuration where connections are configured manually or distributed through the connection manager administration kit. Once you have added the computer’s client account to the designated security group, you need to install a computer certificate on the client for the purpose of Direct Access authentication. An organization needs to deploy Active Directory Certificate Services so that clients can automatically enroll with the appropriate certificates. Question 2 You have a portable computer named Computer1 that runs Windows 7. https://www.certification-questions.com Microsoft 70-680 You have a file server named Server1 that runs Windows Server 2008. -

Set up Your PC for Gaming
WINDOWS® GUIDE Set Up Your PC for Gaming IN THIS GUIDE Optimizing for Graphics and Speed Page 2 Instant Messaging While Gaming Page 11 Great Games and Accessories Page 12 What You’ll Need n Windows Live™ Messenger and a Windows Live ID n A computer with Windows Vista® Windows Guides is a library of easy-to-use guides that show you how to get more from your Windows experience. Share these guides with your friends and family. © 2008 Microsoft. All rights reserved. WINDOWS GUIDE Set Up Your PC For Gaming Optimizing for Graphics and Speed With more family-friendly features, a huge catalog of games, lots of new titles, and more powerful graphics technology than ever before, Windows Vista makes gaming on your PC easier and more fun. New enhancements make it easier to access, play, and manage your computer games while also experiencing next generation gaming graphics. UPDatE SOFtwaRE AND DRIVERS You can optimize your Windows Vista PC for gaming by making sure that you’re running the latest software and drivers, and that your PC hardware meets the demands of the games you play. Update Microsoft DirectX DirectX® is a Windows® software program that enables higher performance in graphics and sound when you’re playing games on your PC. Make sure that you have the latest version of DirectX so that you can take advantage of all of the new features. On a computer running Windows Vista, you should have DirectX 10 or later. Here’s how to check which version of DirectX is on your computer: 1. -

Harmony Computer Configuration Requirements
Harmony Information Systems Harmony Computer Configuration Requirements - to Access, Preview, Print and Download from Harmony Applications November 2012 Harmony Information Systems, Inc. 12120 Sunset Hills Rd, Suite 500 Reston, VA 20190 Customer Support Hotline 800-318-7260 Email Support: [email protected] Page 1 Harmony Information Systems Table of Contents TABLE OF CONTENTS .......................................................................................................... 2 HARDWARE/SOFTWARE MINIMUM REQUIREMENTS ........................................................... 3 ADDING THE HARMONY CUSTOMER PORTAL & HARMONY APPLICATIONS AS TRUSTED SITES IN INTERNET EXPLORER .......................................................................................................... 7 PREVIEWING PDF DOCUMENTS ........................................................................................ 11 MODIFYING THE WAY THAT REPORT PREVIEW IS DISPLAYED ............................................. 11 PRINTING ........................................................................................................................ 12 FILE ATTACHMENTS/MERGE DOCUMENTS ........................................................................ 15 Page 2 Harmony Information Systems Computer Configuration Requirements to Access, Preview, Print and Download from Harmony Applications This document provides basic steps that will assist you with accessing Harmony applications, previewing reports, printing reports or downloading files using Harmony applications. -
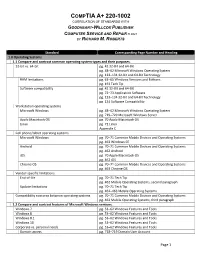
Comptia A+ 220-1002 Correlation of Standards with Goodheart-Willcox Publisher
COMPTIA A+ 220-1002 CORRELATION OF STANDARDS WITH GOODHEART-WILLCOX PUBLISHER COMPUTER SERVICE AND REPAIR © 2021 BY RICHARD M. ROBERTS Standard Corresponding Page Number and Heading 1.0 Operating Systems 1.1 Compare and contrast common operating system types and their purposes. 32-bit vs. 64-bit pg. 42 32-Bit and 64-Bit pg. 48–62 Microsoft Windows Operating System pg. 133–134 32-Bit and 64-Bit Technology RAM limitations pg. 63–65 Windows Versions and Editions pg. 192 Tech Tip Software compatibility pg. 42 32-Bit and 64-Bit pg. 72–73 Application Software pg. 133–134 32-Bit and 64-Bit Technology pg. 134 Software Compatibility Workstation operating systems Microsoft Windows pg. 48–62 Microsoft Windows Operating System pg. 719–729 Microsoft Windows Server Apple Macintosh OS pg. 70 Apple Macintosh OS Linux pg. 71 Linux Appendix C Cell phone/tablet operating systems Microsoft Windows pg. 70–71 Common Mobile Devices and Operating Systems pg. 463 Windows CE Android pg. 70–71 Common Mobile Devices and Operating Systems pg. 462 Android iOS pg. 70 Apple Macintosh OS pg. 462 iOS Chrome OS pg. 70–71 Common Mobile Devices and Operating Systems pg. 463 Chrome OS Vendor-specific limitations End-of-life pg. 70–71 Tech Tip pg. 462 Mobile Operating Systems, second paragraph Update limitations pg. 70–71 Tech Tip pg. 462–463 Mobile Operating Systems Compatibility concerns between operating systems pg. 70–71 Common Mobile Devices and Operating Systems pg. 462 Mobile Operating Systems, third paragraph 1.2 Compare and contrast features of Microsoft Windows versions. -

Dan's Motorcycle Windows Commands
1 Complete List of Run Commands in Windows XP, Vista, 7, 8 & 8.1 ¶ People can get stuck if they are attacked with viruses or in any way can’t access different Applications in Windows. Sometimes it gets difficult to find the commands to start the applications directly. Knowing the Run Command for a program in different Windows versions can be very useful. if you’d like to start a program from a script file or if you only have access to a command line interface this can be helpful. For example, If you have Microsoft Word installed (Any version of Microsoft Office®) rather then searching or clicking the start icon, locating the Microsoft Office folder and then clicking the Microsoft Word. You can use the Windows Run Box instead to access the application directly. Just Click Start and Click Run or press "Window Key + R" and type "Winword" and press enter, Microsoft Word will open immediately. Here is a, hopefully, Complete list of RUN Commands in Windows XP, Vista, 7, 8 and 8.1 for your quick and easy access. Description of Applications Run Command 32-bit ODBC driver under 64-bit platform = C:\windows\sysWOW64\ odbcad32.exe 64 bit ODBC driver under 64-bit platform = C:\windows\system32\ odbcad32.exe Accessibility Controls access.cpl Accessibility Options control access.cpl Accessibility Wizard accwiz Copyright © 1999-2016 dansmc.com. All rights reserved. Adapter Troubleshooter (Vista/Win7) AdapterTroubleshooter 2 Add Features to Windows 8 Win8 windowsanytimeupgradeui Add Hardware Wizard Win8 hdwwiz Add New Hardware Wizard hdwwiz.cpl Add/Remove -

Microsoft Shared Computer Toolkit for Windows XP Handbook
Microsoft Shared Computer Toolkit for Windows XP Handbook The Microsoft Shared Computer Toolkit for Windows XP, v1.0 The information in this document and any document referenced herein is provided for informational purposes only, is provided AS IS AND WITH ALL FAULTS and cannot be understood as substituting for customized service and information that might be developed by Microsoft Corporation for a particular user based upon that user’s particular environment. RELIANCE UPON THIS DOCUMENT AND ANY DOCUMENT REFERENCED HEREIN IS AT THE USER’S OWN RISK. MICROSOFT CORPORATION PROVIDES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION CONTAINED IN THIS DOCUMENT AND ANY DOCUMENT REFERENCED HEREIN. Microsoft Corporation provides no warranty and makes no representation that the information provided is in this document or any document referenced herein is suitable or appropriate for any situation, and Microsoft Corporation cannot be held liable for any claim or damage of any kind that users of this document or any document referenced herein may suffer. Your retention of and/or use of this document and/or any document referenced herein constitutes your acceptance of these terms and conditions. If you do not accept these terms and conditions, Microsoft Corporation does not provide you with any right to use any part of this document or any document referenced herein. Complying with the applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. -

Microsoft Windows System Utilities
CompTIA A+ Microsoft Windows System Utilities Introduction Lab Topology Exercise 1 - Get to Know Various System Utilities Review Introduction Windows system utilities A+ Microsoft Dxdiag MSinfo32 MSTSC MMC Welcome to the Microsoft Windows System Utilities Practice Lab. In this module, you will be provided with the instructions and devices needed to develop your hands-on skills. Learning Outcomes In this module, you will complete the following exercise: Exercise 1 - Get to know Various System Utilities After completing this lab, you will be able to: Explore Registry Editor Use the Services Console Use the Microsoft Terminal Services Client (MSTSC) Use Notepad Use File Explorer Use MSinfo32 Use the Microsoft Management Console (MMC) Use Dxdiag Use the Defragment and Optimize Drives Utility Use Windows Update Exam Objectives The following exam objectives are covered in this lab: 220-1002: 1.8 Getting to know Microsoft system utilities Note: Our main focus is to cover the practical, hands-on aspects of the exam objectives. We recommend referring to course material or a search engine to research theoretical topics in more detail. Lab Duration It will take approximately 1 hour to complete this lab. Help and Support For more information on using Practice Labs, please see our Help and Support page. You can also raise a technical support ticket from this page. Click Next to view the Lab topology used in this module. Lab Topology During your session, you will have access to the following lab configuration. Depending on the exercises, you may or may not use all of the devices, but they are shown here in the layout to get an overall understanding of the topology of the lab. -

Zenon Manual Project and Workspace
zenon manual Project and workspace v.7.11 ©2014 Ing. Punzenberger COPA-DATA GmbH All rights reserved. Distribution and/or reproduction of this document or parts thereof in any form are permitted solely with the written permission of the company COPA-DATA. The technical data contained herein has been provided solely for informational purposes and is not legally binding. Subject to change, technical or otherwise. Contents 1. Welcome to COPA-DATA help ...................................................................................................... 5 2. Project and workspace ................................................................................................................. 5 3. Workspace .................................................................................................................................. 6 3.1 Create new workspace ................................................................................................................................ 7 3.2 Save workspace ........................................................................................................................................... 7 3.3 Edit existing workspace ............................................................................................................................... 8 3.4 Backup and restore of workspaces ............................................................................................................. 9 4. Project .......................................................................................................................................