Copyright by Lane Thomas Holloway 2016 the Dissertation Committee for Lane Thomas Holloway Certifies That This Is the Approved Version of the Following Dissertation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Campus Knowledge of Esports Kenny Sugishita University of South Carolina - Columbia
University of South Carolina Scholar Commons Theses and Dissertations 12-14-2015 Campus Knowledge of eSports Kenny Sugishita University of South Carolina - Columbia Follow this and additional works at: https://scholarcommons.sc.edu/etd Part of the Sports Management Commons Recommended Citation Sugishita, K.(2015). Campus Knowledge of eSports. (Master's thesis). Retrieved from https://scholarcommons.sc.edu/etd/3296 This Open Access Thesis is brought to you by Scholar Commons. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of Scholar Commons. For more information, please contact [email protected]. CAMPUS KNOWLEDGE OF ESPORTS by Kenny Sugishita Bachelor of Science University of South Carolina Upstate, 2013 Submitted in Partial Fulfillment of the Requirements For the Degree of Master of Sport and Entertainment Management in Sport and Entertainment Management College of Hospitality, Retail, and Sport Management University of South Carolina 2015 Accepted by: Mark Nagel, Director of Thesis Amber Fallucca, Reader Lacy Ford, Senior Vice Provost and Dean of Graduate Studies © Copyright by Kenny Sugishita, 2015 All Rights Reserved. ii ABSTRACT This research study investigates private college and university admission’s officers levels of familiarity of the electronic sports (eSports) industry along with determining the level of emphasis universities place on academics and co-curricular activities. A thorough examination of the professional eSports space is extensively detailed providing information about the history of video games, the development of professional eSports, and the development of collegiate eSports. Additionally, examination of trends in higher education, especially as it relates to private institutions, is explained in detail. -

Video Game Systems Uncovered
Everything You Ever Wanted To Know About... VIDEO GAMES But Never Dared To Ask! Introduction: 1 With the holidays quickly approaching the odds are you will be purchasing some type of video game system. The majority of U.S. households currently have at least one of these systems. With the ever changing technology in the video world it is hard to keep up with the newest systems. There is basically a system designed for every child’s needs, ranging from preschool to young adult. This can overwhelming for parents to choose a system that not only meets your child’s needs but also gives us the best quality system for our money. With the holidays coming that means many retailers will be offering specials on video game systems and of course the release of long awaited games. Now is also the time you can purchase systems in bundles with games included. Inside you will learn about all of these topics as well as other necessities and games to accompany to recent purchase. What you’ll find here: 2 In this ebook you will learn about console and portable video game systems, along with the accessories available. You will also find how many games each system has to offer. You will get an in depth look at the pro’s and con’s of each current system available in stores today, and the upcoming systems available in the near future. As a concerned parent you should also be aware of the rating label of the games and what the rating exactly means. -

The Common Forms of Contemporary Videogames: a Proposed Content Analysis Model
1 The Common Forms of Contemporary Videogames: A Proposed Content Analysis Model STEVEN ALLICK A thesis submitted in partial fulfilment of the requirements of Teesside University for the degree of Doctor of Philosophy Teesside University School of Computing April 2012 2 Contents Acknowledgements 5 Declaration 9 Abstract 10 1. Introduction 11 1.1. Background 11 1.2. Motivation 12 1.3. Understanding Tropes 14 1.4. Thesis Statement 15 1.4.1 Aims 15 1.4.2 Thesis 16 1.5 Approach 17 1.6 Methods Used 19 1.6.1 Analysis and Data Gathering 19 1.6.2 Sampling Criterion 20 1.6.3 Scales and Measures 23 1.7 Thesis Organisation 23 2. Literature Review 28 2.1. Semiotics Literature 28 2.1.1 Semiotic Principles 28 2.1.2 Computing Semiotics 31 2.1.3 Artistic and Media Semiotics 33 2.1.4 General Semiotic Research Critique 33 2.2 Rhetoric and Tropes Literature 34 2.2.1 Principles of Tropes 34 2.2.2 Metaphor and Myth 35 2.2.3 Metonym, Synecdoche and Irony 36 2.2.4 Aporia and Epiphany 37 2.2.5 Tropical Research Critique 38 3 2.3 Genre Theory Literature 39 2.3.1 Background and Origin 39 2.3.2 Videogame Genres 40 2.3.3 Genre Theory Critique 41 2.4 Development Models and Methods 43 2.4.1 Perceptual Opportunities 43 2.4.2 Qualitative Design Models 44 2.4.3 Quantitative Design Models 45 2.4.4 Heuristic / Rule Models 45 2.4.5 Development Model Critique 46 2.5 Emotion, Enjoyment and Immersion Models 47 2.5.1 Emotion and Enjoyment 47 2.5.2 Immersion 49 2.5.3 Frustration 50 2.5.4 Player Centric Model Critique 50 2.6 Time 52 2.7 Representational Dimensions 53 2.8 Observations and Conclusions 55 3. -
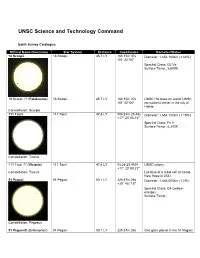
UNSC Science and Technology Command
UNSC Science and Technology Command Earth Survey Catalogue: Official Name/(Common) Star System Distance Coordinates Remarks/Status 18 Scorpii {TCP:p351} 18 Scorpii {Fact} 45.7 LY 16h 15m 37s Diameter: 1,654,100km (1.02R*) {Fact} -08° 22' 06" {Fact} Spectral Class: G2 Va {Fact} Surface Temp.: 5,800K {Fact} 18 Scorpii ?? (Falaknuma) 18 Scorpii {Fact} 45.7 LY 16h 15m 37s UNSC HQ base on world. UNSC {TCP:p351} {Fact} -08° 22' 06" recruitment center in the city of Halkia. {TCP:p355} Constellation: Scorpio 111 Tauri 111 Tauri {Fact} 47.8 LY 05h:24m:25.46s Diameter: 1,654,100km (1.19R*) {Fact} +17° 23' 00.72" {Fact} Spectral Class: F8 V {Fact} Surface Temp.: 6,200K {Fact} Constellation: Taurus 111 Tauri ?? (Victoria) 111 Tauri {Fact} 47.8 LY 05:24:25.4634 UNSC colony. {GoO:p31} {Fact} +17° 23' 00.72" Constellation: Taurus Location of a rebel cell at Camp New Hope in 2531. {GoO:p31} 51 Pegasi {Fact} 51 Pegasi {Fact} 50.1 LY 22h:57m:28s Diameter: 1,668,000km (1.2R*) {Fact} +20° 46' 7.8" {Fact} Spectral Class: G4 (yellow- orange) {Fact} Surface Temp.: Constellation: Pegasus 51 Pegasi-B (Bellerophon) 51 Pegasi 50.1 LY 22h:57m:28s Gas giant planet in the 51 Pegasi {Fact} +20° 46' 7.8" system informally named Bellerophon. Diameter: 196,000km. {Fact} Located on the edge of UNSC territory. {GoO:p15} Its moon, Pegasi Delta, contained a Covenant deuterium/tritium refinery destroyed by covert UNSC forces in 2545. {GoO:p13} Constellation: Pegasus 51 Pegasi-B-1 (Pegasi 51 Pegasi 50.1 LY 22h:57m:28s Moon of the gas giant planet 51 Delta) {GoO:p13} +20° 46' 7.8" Pegasi-B in the 51 Pegasi star Constellation: Pegasus system; a Covenant stronghold on the edge of UNSC territory. -

List of Teen Zone Games
Gaming is Available When the Teen Zone is Staffed Must be Ages 13-19 & Have a Valid Library Card in Good Standing to Play Battlefield 1 Assassin’s Creed IV: Black Flag Battlefield 4 Battlefield 4 Gears of War 4 Call of Duty: Ghosts Halo 5 Call of Duty: Black Ops III Call of Duty: Infinite Warfare Army of Two Battalion Wars 2 Dark Souls III Assassin’s Creed Boom Blox Batman: Arkham Asylum & City Cabela’s Big Game Hunter 2010 Deus Ex Battlefield: 3 & Bad Company Cooking Mama Cookoff Fallout 4 BioShock DDR Hottest Party 2 Mortal Kombat X Burnout Paradise Dancing with the Stars Ace Combat 6 Call of Duty: Modern Warfare 1, 2 & 3 Deca Sports Avatar: The Game Star Wars Battlefront Call of Duty: World at War Geometry Wars Galaxies Batman: Arkham Asylum The Witcher Wild Hunt Call of Duty: Black Ops 1 & 2 Glee Karaoke Crackdown Uncharted 4: A Thief’s End Condemned 2: Bloodshot Just Dance 2, 3 & 4 Dead or Alive 4 Dead Space Legend of Zelda Twilight Princess DeadRising Devil May Cry 4 Lego: Batman 1, 2 & Star Wars Earth Defense Force 2017 Fallout 3 Mario & Sonic at the Olympic Games F.E.A.R. 2 FIFA 08 Mario Party 8 Gears of War: 1, 2 & 3 Fight Night Round 3 Mario Strikers Charged Halo: 3, 4, ODST & Wars Ghost Recon 2 MarioKart Left for Dead: 1 & 2 Dance Dance Revolution Guitar Hero: 3, 5, Aerosmith, Metallica Medal of Honor Heroes 2 Lost Planet God of War II & World Tour Metroid Prime Guitar Hero 2 Madden NFL: 09, 10 & 12 Madden NFL 09 New Carnival Games NBA 2K8 Madden 08 Metal Gear Solid 4 No More Heroes NCAA 08 Football NCAA Football 08 Mortal Kombat vs. -

The Effect of School Closure On
Public Gaming: eSport and Event Marketing in the Experience Economy by Michael Borowy B.A., University of British Columbia, 2008 Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Arts in the School of Communication Faculty of Communication, Art, and Technology Michael Borowy 2012 SIMON FRASER UNIVERSITY Summer 2012 All rights reserved. However, in accordance with the Copyright Act of Canada, this work may be reproduced, without authorization, under the conditions for “Fair Dealing.” Therefore, limited reproduction of this work for the purposes of private study, research, criticism, review and news reporting is likely to be in accordance with the law, particularly if cited appropriately. Approval Name: Michael Borowy Degree: Master of Arts (Communication) Title of Thesis: Public Gaming: eSport and Event Marketing in the Experience Economy Examining Committee: Chair: David Murphy, Senior Lecturer Dr. Stephen Kline Senior Supervisor Professor Dr. Dal Yong Jin Supervisor Associate Professor Dr. Richard Smith Internal Examiner Professor Date Defended/Approved: July 06, 2012 ii Partial Copyright Licence iii STATEMENT OF ETHICS APPROVAL The author, whose name appears on the title page of this work, has obtained, for the research described in this work, either: (a) Human research ethics approval from the Simon Fraser University Office of Research Ethics, or (b) Advance approval of the animal care protocol from the University Animal Care Committee of Simon Fraser University; or has conducted the research (c) as a co-investigator, collaborator or research assistant in a research project approved in advance, or (d) as a member of a course approved in advance for minimal risk human research, by the Office of Research Ethics. -

An Interpretive Phenomenological Study of the Meaning of Video Games In
1 “It feels more real”: An Interpretive Phenomenological Study of the Meaning of Video Games in Adolescent Lives Susan R. Forsyth, PhD, RN Assistant Adjunct Professor, Social & Behavioral Sciences University of California, San Francisco Assistant Professor School of Nursing, Samuel Merritt University, Oakland, CA Catherine A. Chesla, RN, PhD, FAAN Professor and Interim Chair, Family Health Care Nursing University of California, San Francisco Roberta S. Rehm, PhD, RN, FAAN Professor, Family Health Care Nursing University of California, San Francisco Ruth E. Malone, PhD, RN, FAAN Professor and Chair, Department of Social & Behavioral Sciences School of Nursing University of California, San Francisco Corresponding author: Susan R. Forsyth Department of Social and Behavioral Sciences 3333 California Street, LHts-455, Box 0612 San Francisco, CA 94118 [email protected] 2 510.512-8290 Acknowledgements: We thank Quinn Grundy, Kate Horton and Leslie Dubbin for their invaluable feedback. Declarations of Conflicting Interests The authors declare no potential conflicts of interest with respect to the research, authorship and/or publication of this article. Funding The authors disclosed the receipt of the following financial support for the research, authorship and/or publication of this article. Susan Forsyth is funded by a dissertation award from the Tobacco-Related Disease Research Program (TRDRP), grant #22DT- 0003. Published in Advances in Nursing Science, October 4, 2017 http://journals.lww.com/advancesinnursingscience/toc/publishahead 3 Abstract The pervasiveness of video gaming among adolescents today suggests a need to understand how gaming affects identity formation. We interviewed 20 adolescents about their experiences of playing, asking them to describe how they used games and how game playing affected their real-world selves. -
![Download/90/67> [22 May 2015] Hofstee, E](https://docslib.b-cdn.net/cover/9857/download-90-67-22-may-2015-hofstee-e-2919857.webp)
Download/90/67> [22 May 2015] Hofstee, E
An analysis of its origin and a look at its prospective future growth as enhanced by Information Technology Management tools. Master in Science (M.Scs.) At Coventry University Management of Information Technology September 2014 - September 2015 Supervised by: Stella-Maris Ortim Course code: ECT078 / M99EKM Student ID: 6045397 Handed in: 16 August 2015 DECLARATION OF ORIGINALITY Student surname: OLSEN Student first names: ANDERS, HVAL Student ID No: 6045397 Course: ECT078 – M.Scs. Management of Information Technology Supervisor: Stella-Maris Ortim Second marker: Owen Richards Dissertation Title: The Evaluation of eSports: An analysis of its origin and a look at its prospective future growth as enhanced by Information Technology Management tools. Declaration: I certify that this dissertation is my own work. I have read the University regulations concerning plagiarism. Anders Hval Olsen 15/08/2015 i ABSTRACT As the last years have shown a massive growth within the field of electronic sports (eSports), several questions emerge, such as how much is it growing, and will it continue to grow? This research thesis sees this as its statement of problem, and further aims to define and measure the main factors that caused the growth of eSports. To further enhance the growth, the benefits and disbenefits of implementing Information Technology Management tools is appraised, which additionally gives an understanding of the future of eSports. To accomplish this, the thesis research the existing literature within the project domain, where the literature is evaluated and analysed in terms of the key research questions, and further summarised in a renewed project scope. As for methodology, a pragmatism philosophy with an induction approach is further used to understand the field, and work as the outer layer of the methodology. -

Electronic Sports
Electronic sports This article is about video game competitions. For de- the esports label.[4] In 2012, the most popular titles fea- pictions of traditional sports in video games, see sports tured in professional competition were real time strat- game. For games involving exercise, see exergaming. egy and multiplayer online battle arena games Dota 2, Electronic sports (also known as esports or competi- League of Legends, and StarCraft II.[5] Shooting games like Counter Strike and Call of Duty have enjoyed some success as esports, although their viewer numbers have remained below those of their competitors.[6] 1 Overview Geographically, esports competitions have their roots in developed countries. South Korea has the best es- tablished esports organizations, officially licensing pro- gamers since the year 2000.[7] Official recognition of es- ports competitions outside South Korea has come some- what slower. In 2013, Canadian League of Legends player Danny “Shiphtur” Le became the first pro-gamer to re- ceive a United States P-1A visa, a category designated for Players at the 2013 Intel Extreme Masters in Katowice, Poland “Internationally Recognized Athletes”.[8][9] Along with South Korea, most competitions take place in Europe, tive gaming) is a term for organized video game compe- North America, Australia and China. Despite its large titions, especially between professionals. The most com- video game market, esports in Japan is relatively un- mon video game genres associated with electronic sports derdeveloped, which has been attributed largely to its are real-time strategy, fighting, first-person shooter, and broad anti-gambling laws.[10] In 2014, the largest inde- multiplayer online battle arena. -

TECMO, LTD. (Tokyo Stock Exchange/First Section: 9650) August 23, 2007 Company Profile Company: TECMO, LTD
CORPORATE PROFILE TECMO, LTD. (Tokyo Stock Exchange/First Section: 9650) August 23, 2007 Company Profile Company: TECMO, LTD. Established: July 31, 1967(40 years since its founding) Business 1. Home Console Games (Planning / Development/ Sales) Category 2. On-line Games (Planning / Development/ Sales /Service) 3. Mobile Contents (Planning / Development/ Sales /Service) 4. Commercial Equipment/Software (Planning / Development/ Sales) 5. Amusement Facility Management No. of Employees Non-consolidated: 354 Consolidated: 489 ( as of June 30, 2007) Capital ¥5,823,000,000 Stock Listing Tokyo Stock Exchange/First Section (Securities Code: 9650) Information/Communication Industry Issued No. of 24,879,000 shares Shares Copyright © 2007 TECMO,LTD. All Rights Reserved. 1 TECMO’S BUSINESS ACTIVITIES With development/sales of games as our core business, TECMO is engaged in extensive business activities HomeHome Console Console GamesGames Business Business Planning, development, research and sales of On-lineOn-line Games Games Business Business home console game software Popular home console game titles remade into Rights Business on-line games Rights Business Planning and development of user-create type titles Planning and sales of character items MobileMobile Contents Contents Business Business Planning, development, research and sales of contents for mobile terminals CommercialCommercial Equipment Equipment / / AmusementAmusement FacilityFacility SoftwareSoftware Business Business ManagementManagement BusinessBusiness Planning, development, research -

TECMO, LTD.(Tokyo Stock Exchange:9650)
CORPORATE PROFILE TECMO, LTD.(Tokyo Stock Exchange:9650) February 21, 2008 Company Profile Company: TECMO, LTD. Established: July 31, 1967 1. Games Business 2. Multi-Contents (Online / Mobile) Business Business Category: 3. SP (Pachinko/Pachislot LCD Software Development)Business 4. Rights Business 5. Amusement Facilities Management Business Non-consolidated: 352 Consolidated: 471 (as of Dec. 31, No. of Employees: 2007) Capital: ¥5,823,000,000 Tokyo Stock Exchange/ First Section (Securities Code:9650) Stock Listing: Information/Communication Industry Issued No. of Shares: 24,879,000 shares Copyright © 2008 TECMO,LTD. All Rights Reserved. 1 TECMO’S Business Expansion Global expansion of contents business with development and sales of games at its core. Outstanding strength in action-game development capability and brand power in N. America. GamesGames Planning, development, research and sales of home console games software SPSP Multi-ContentsMulti-Contents Planning, development and sales Contents planning, development, sales of pachinko/pachislot LCD and service for PC online-games software and mobile phones Amusement Facilities Rights Amusement Facilities Rights ManagementManagement Planning, development and management of Planning and sales of character items amusement facilities Copyright © 2008 TECMO,LTD. All Rights Reserved. 2 TECMO Visionary 2010 ー To become a world-wide contents provider devoted to fulfilling people’s lives ー TECMO Visionary 2010 Establish a business foundation that befits the status of a visionary company by 2010 Make transition to a management system based upon management vision and visionary business strategies Aim for success in the 2008 global market through collaboration Management Vision ① Provision of high quality contents and services catering to customer preference ② Leading the world with propositions and technologies ③ Sound management through emphasis on cash flow ④ Capacity building of a daring workforce and creating of an attractive work environment Copyright © 2008 TECMO,LTD. -

Xbox 360 Games List (Sorted by Title A-Z)
Xbox 360 Games List (Sorted by title A-Z) Title Genre Theme 007 Legends Arcade N/A Ace Combat 6 Flying N/A Adventure Time Arcade N/A Arcania RPG N/A Battlestation Midway Simulation N/A Blur Racing N/A Burnout Paradise Racing N/A Call of Jaurez - Bound in Blood Shooter N/A Crysis 2 Shooter N/A Dance Central Other Kinnect Dead or Alive 4 Fighting N/A Destiny - The Taken King Shooter N/A Dirt 3 Racing Dirt DIRT Showdown Racing Dirt Doom 3 Shooter N/A Driver San Francisco Racing N/A Dungeon Siege 3 RPG N/A Elder Scrolls, The - Skyrim Sandbox/Open World N/A F1 2011 Racing F1 F1 2013 Racing F1 Fable 2 RPG N/A Far Cry 2 Shooter Far Cry Far Cry 3 Shooter Far Cry Far Cry 4 Shooter Far Cry Far Cry Instincts Predator Shooter Far Cry Forza Horizon Racing Forza Forza Horizon 2 Racing Forza Forza Motorsport 2 Racing Forza Forza Motorsport 3 Racing Forza Forza Motorsport 4 Racing Forza Frontlines Fuel of War Shooter N/A Gears of War Shooter Gears of War Gears of War 2 Shooter Gears of War Grand Theft Auto - Episodes from Liberty City Sandbox/Open World Grand Theft Auto Grand Theft Auto 4 Sandbox/Open World Grand Theft Auto Grand Theft Auto 5 Sandbox/Open World Grand Theft Auto Grease Other Kinnect Grid 2 Racing N/A Guitar Hero III Legends of Rock Simulation N/A Guitar Hero Live Simulation N/A Halo - 10th Anniversary Shooter Halo Halo 2 Shooter Halo Halo 3 Shooter Halo Halo 3: ODST Shooter Halo Halo 4 Shooter Halo Halo Reach Shooter Halo Halo Wars RPG Halo Xbox 360 Games List (Sorted by title A-Z) Title Genre Theme Homefront Shooter N/A Kinect Adventures