LESSON 2 ESSENTIAL COMMANDS Lesson 2: Essential Commands
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cisco Telepresence Codec SX20 API Reference Guide
Cisco TelePresence SX20 Codec API Reference Guide Software version TC6.1 April 2013 Application Programmer Interface (API) Reference Guide Cisco TelePresence SX20 Codec D14949.03 SX20 Codec API Reference Guide TC6.1, April 2013. 1 Copyright © 2013 Cisco Systems, Inc. All rights reserved. Cisco TelePresence SX20 Codec API Reference Guide What’s in this guide? Table of Contents Introduction Using HTTP ....................................................................... 20 Getting status and configurations ................................. 20 TA - ToC - Hidden About this guide .................................................................. 4 The top menu bar and the entries in the Table of Sending commands and configurations ........................ 20 text anchor User documentation ........................................................ 4 Contents are all hyperlinks, just click on them to Using HTTP POST ......................................................... 20 go to the topic. About the API Feedback from codec over HTTP ......................................21 Registering for feedback ................................................21 API fundamentals ................................................................ 9 Translating from terminal mode to XML ......................... 22 We recommend you visit our web site regularly for Connecting to the API ..................................................... 9 updated versions of the user documentation. Go to: Password ........................................................................ -

RED HAT ENTERPRISE LINUX 5, 6, and 7 Common Administrative
RED HAT ENTERPRISE LINUX 5, 6, AND 7 SOFTWARE MANAGEMENT NETWORKING Common administrative commands TASK RHEL TASK RHEL yum install iptables and ip6tables 5 6 5 yum groupinstall /etc/sysconfig/ip*tables Install software iptables and ip6tables 1 Be aware of potential issues when using subscription-manager yum install 7 Configure firewall /etc/sysconfig/ip*tables 6 SYSTEM BASICS on Red Hat Enterprise Linux 5: https://access.redhat.com/ yum group install system-config-firewall solutions/129003. TASK RHEL yum info firewall-cmd 2 Subscription-manager is used for Satellite 6, Satellite 5.6 with 5 6 7 SAM and newer, and Red Hat’s CDN. yum groupinfo firewall-config /etc/sysconfig/rhn/systemid 5 3 RHN tools are deprecated on Red Hat Enterprise Linux 7. View software info /etc/hosts yum info 5 6 rhn_register should be used for Satellite server 5.6 and newer 7 /etc/resolv.conf /etc/sysconfig/rhn/systemid yum group info View subscription information 6 only. For details, see: Satellite 5.6 unable to register RHEL 7 Configure name subscription-manager identity client system due to rhn-setup package not included in Minimal resolution /etc/hosts installation (https://access.redhat.com/solutions/737373) Update software yum update 5 6 7 /etc/resolv.conf 7 subscription-manager identity 7 nmcli con mod rhn_register 5 Upgrade software yum upgrade 5 6 7 /etc/sysconfig/network 5 6 subscription-manager 1 Configure hostname hostnamectl rhn_register Configure software subscription-manager repos 5 6 7 /etc/hostname 7 rhnreg_ks 6 /etc/yum.repos.d/*.repo Configure -

Customizing and Extending Powerdesigner SAP Powerdesigner Documentation Collection Content
User Guide PUBLIC SAP PowerDesigner Document Version: 16.6.2 – 2017-01-05 Customizing and Extending PowerDesigner SAP PowerDesigner Documentation Collection Content 1 PowerDesigner Resource Files.................................................... 9 1.1 Opening Resource Files in the Editor.................................................10 1.2 Navigating and Searching in Resource Files............................................ 11 1.3 Editing Resource Files........................................................... 13 1.4 Saving Changes................................................................13 1.5 Sharing and Embedding Resource Files...............................................13 1.6 Creating and Copying Resource Files.................................................14 1.7 Specifying Directories to Search for Resource Files.......................................15 1.8 Comparing Resource Files........................................................ 15 1.9 Merging Resource Files.......................................................... 16 2 Extension Files................................................................18 2.1 Creating an Extension File.........................................................19 2.2 Attaching Extensions to a Model....................................................20 2.3 Exporting an Embedded Extension File for Sharing.......................................21 2.4 Extension File Properties......................................................... 21 2.5 Example: Adding a New Attribute from a Property -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

TRSDOS 6.2 to LS-DOS 6.3.0 Manual Update
LS-DOSÔ 6.3 UPDATE FOR TRSDOSâ 6.2.X The LS-DOS 6.3 release is an upgrade for the TRSDOS 6.2 operating system. Several important changes have been made to extend and enhance the operating system and its utilities. The date ranging has been expanded to accept dates through the year 1999. Files will now carry a modification time as well as a date. The DATECONV/CMD program is provided to translate version 6.2 or earlier disks to the 6.3 style dating. The user password has been eliminated from the system. The owner password still remains. The library command ID was added to display a customer service number. Several enhancements have been made to BASIC. The new DISKCOPY/CMD program will duplicate 5" double density floppy disks. Because the LS-DOS 6.3 update is a series of enhancements to TRSDOS 6.2, the primary documentation remains the 6.2 manual and Technical Reference manual. If you have a version of TRSDOS earlier than 6.2, you can obtain the manuals from Radio Shack under the catalog numbers 26-0316 (TRSDOS Version 6 [6.2 DOS manual and disk]), 26-2110 (Model 4/4D [6.2] Technical Reference Manual), or 26-1117 (6.2 DOS manual only). This documentation should be treated as an addendum to the TRSDOS 6.2 information. LS-DOS 6.3 installation instructions Before performing the upgrade, it is recommended that you make several backup copies of the 6.3 master disk. The simplest way to do this is to boot your system using the 6.3 diskette, insert a blank diskette to receive the copy in drive 1, and type the command: DISKCOPY :0 :1 When the copy finishes, you can insert another destination diskette and make another copy. -

Don't Trust Traceroute (Completely)
Don’t Trust Traceroute (Completely) Pietro Marchetta, Valerio Persico, Ethan Katz-Bassett Antonio Pescapé University of Southern California, CA, USA University of Napoli Federico II, Italy [email protected] {pietro.marchetta,valerio.persico,pescape}@unina.it ABSTRACT In this work, we propose a methodology based on the alias resolu- tion process to demonstrate that the IP level view of the route pro- vided by traceroute may be a poor representation of the real router- level route followed by the traffic. More precisely, we show how the traceroute output can lead one to (i) inaccurately reconstruct the route by overestimating the load balancers along the paths toward the destination and (ii) erroneously infer routing changes. Categories and Subject Descriptors C.2.1 [Computer-communication networks]: Network Architec- ture and Design—Network topology (a) Traceroute reports two addresses at the 8-th hop. The common interpretation is that the 7-th hop is splitting the traffic along two Keywords different forwarding paths (case 1); another explanation is that the 8- th hop is an RFC compliant router using multiple interfaces to reply Internet topology; Traceroute; IP alias resolution; IP to Router to the source (case 2). mapping 1 1. INTRODUCTION 0.8 Operators and researchers rely on traceroute to measure routes and they assume that, if traceroute returns different IPs at a given 0.6 hop, it indicates different paths. However, this is not always the case. Although state-of-the-art implementations of traceroute al- 0.4 low to trace all the paths -

Excerpts of Chapters From
Excerpts of Chapters from A Practical Guide to Ubuntu Linux® FOURTH EDITION Mark G. Sobell ISBN-13: 978-0-13-392731-3 CopyrightExcerpt © 2015 Mark G. Sobell Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Blank Excerpt 3 Step-by-Step Installation 3Chapter3 In This Chapter Objectives Booting Ubuntu and Running a After reading this chapter you should be able to: Live Session. 56 Run a live session and use gnome-disks to view and Automatic Boot Sequence . 56 change disk partitioning Running a Live Session. 59 Install Ubuntu from a live session Installing from a Live Session . 60 Install Ubuntu using the Server Image Installing from the Desktop Modify system behavior using boot parameters Boot Menu . 61Excerpt Modify partitions during installation The ubiquity Graphical Installer. 61 The ubiquity Advanced Partitioning List the requirement and considerations for a dual- Screen. 67 boot configuration Advanced Installation. 71 Modifying Boot Parameters (Options) . 75 debian-installer: The Ubuntu Textual Installer . 78 gnome-disks: The GNOME Disk Utility . 88 Setting Up a Dual-Boot System . 91 5555 56 Chapter 3 Step-by-Step Installation Chapter 2 covered planning the installation of Ubuntu: determining the requirements; planning the layout of the hard disk; obtaining the files you need for the installation, including how to download and burn or write Desktop and Server Images to installa- tion media; and collecting information about the system. This chapter focuses on installing Ubuntu. Frequently the installation is quite simple, especially if you have done a good job of planning. -

Introduction to UNIX at MSI June 23, 2015 Presented by Nancy Rowe
Introduction to UNIX at MSI June 23, 2015 Presented by Nancy Rowe The Minnesota Supercomputing Institute for Advanced Computational Research www.msi.umn.edu/tutorial/ © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Overview • UNIX Overview • Logging into MSI © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Frequently Asked Questions msi.umn.edu > Resources> FAQ Website will be updated soon © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research What’s the difference between Linux and UNIX? The terms can be used interchangeably © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research UNIX • UNIX is the operating system of choice for engineering and scientific workstations • Originally developed in the late 1960s • Unix is flexible, secure and based on open standards • Programs are often designed “to do one simple thing right” • Unix provides ways for interconnecting these simple programs to work together and perform more complex tasks © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Getting Started • MSI account • Service Units required to access MSI HPC systems • Open a terminal while sitting at the machine • A shell provides an interface for the user to interact with the operating system • BASH is the default shell at MSI © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Bastion Host • login.msi.umn.edu • Connect to bastion host before connecting to HPC systems • Cannot run software on bastion host (login.msi.umn.edu) © 2015 Regents of the University of Minnesota. -

Netop Remote Control User's Guide
USER'S GUIDE 27 September 2017 Netop Remote Control User's Guide Copyright© 1981-2017 Netop Business Solutions A/S. All Rights Reserved. Portions used under license from third parties. Please send any comments to: Netop Business Solutions A/S Bregnerodvej 127 DK-3460 Birkerod Denmark E-mail: [email protected] Internet: www.netop.com Netop™ is a trademark of Netop Business Solutions A/S. All other products mentioned in this document are trademarks of their respective manufacturers. Netop Business Solutions A/S denies any and all responsibility for damages caused directly or indirectly as a result of using this document. The content of this document is subject to change without notice. Netop Business Solutions A/S retains the copyright to this document. The document is optimized for double-sided printing. 27 September 2017 Netop Remote Control User's Guide Contents 1 Overview ....................................................................................................................................................4 1.1 Remote Control modules ...............................................................................................................................................4 1.2 Security ...........................................................................................................................................4 1.3 Communication profiles ...............................................................................................................................................5 2 Managing Hosts ........................................................................................................................................6 -
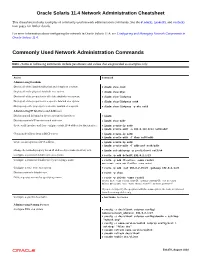
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre ..............................................................................................................................