RED HAT ENTERPRISE LINUX 5, 6, and 7 Common Administrative
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Don't Trust Traceroute (Completely)
Don’t Trust Traceroute (Completely) Pietro Marchetta, Valerio Persico, Ethan Katz-Bassett Antonio Pescapé University of Southern California, CA, USA University of Napoli Federico II, Italy [email protected] {pietro.marchetta,valerio.persico,pescape}@unina.it ABSTRACT In this work, we propose a methodology based on the alias resolu- tion process to demonstrate that the IP level view of the route pro- vided by traceroute may be a poor representation of the real router- level route followed by the traffic. More precisely, we show how the traceroute output can lead one to (i) inaccurately reconstruct the route by overestimating the load balancers along the paths toward the destination and (ii) erroneously infer routing changes. Categories and Subject Descriptors C.2.1 [Computer-communication networks]: Network Architec- ture and Design—Network topology (a) Traceroute reports two addresses at the 8-th hop. The common interpretation is that the 7-th hop is splitting the traffic along two Keywords different forwarding paths (case 1); another explanation is that the 8- th hop is an RFC compliant router using multiple interfaces to reply Internet topology; Traceroute; IP alias resolution; IP to Router to the source (case 2). mapping 1 1. INTRODUCTION 0.8 Operators and researchers rely on traceroute to measure routes and they assume that, if traceroute returns different IPs at a given 0.6 hop, it indicates different paths. However, this is not always the case. Although state-of-the-art implementations of traceroute al- 0.4 low to trace all the paths -
Oracle® Solaris 11.4 Network Administration Cheatsheet
Oracle Solaris 11.4 Network Administration Cheatsheet This cheatsheet includes examples of commonly used network administration commands. See the dladm(8), ipadm(8), and route(8) man pages for further details. For more information about configuring the network in Oracle Solaris 11.4, see Configuring and Managing Network Components in Oracle Solaris 11.4. Commonly Used Network Administration Commands Note - Some of following commands include parameters and values that are provided as examples only. Action Command Administering Datalinks Display all of the datalinks (physical and virtual) on a system. # dladm show-link Display all of the physical datalinks on a system. # dladm show-phys Display all of the properties for all of the datalinks on a system. # dladm show-linkprop Display all of the properties for a specific datalink on a system. # dladm show-linkprop net0 Display a specific property for a specific datalink on a system. # dladm show-linkprop -p mtu net0 Administering IP Interfaces and Addresses Display general information about a system's IP interfaces. # ipadm Display a system's IP interfaces and addresses. # ipadm show-addr Create an IP interface and then configure a static IPv4 address for that interface. # ipadm create-ip net0 # ipadm create-addr -a 203.0.113.0/24 net0/addr Obtain an IP address from a DHCP server. # ipadm create-ip net0 # ipadm create-addr -T dhcp net0/addr Create an auto-generated IPv6 address. # ipadm create-ip net0 # ipadm create-addr -T addrconf net0/addr Change the netmask property for an IP address object name (net3/v4) to 8. # ipadm set-addrprop -p prefixlen=8 net3/v4 Configure a persistent default route on a system. -

Blue Coat SGOS Command Line Interface Reference, Version 4.2.3
Blue Coat® Systems ProxySG™ Command Line Interface Reference Version SGOS 4.2.3 Blue Coat ProxySG Command Line Interface Reference Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/contact.html [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™, RA Connector™, RA Manager™, Remote Access™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, The Ultimate Internet Sharing Solution®, Permeo®, Permeo Technologies, Inc.®, and the Permeo logo are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information. -
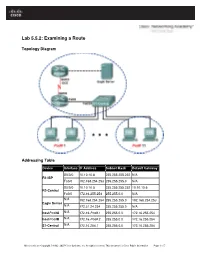
Lab 5.5.2: Examining a Route
Lab 5.5.2: Examining a Route Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S0/0/0 10.10.10.6 255.255.255.252 N/A R1-ISP Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5 255.255.255.252 10.10.10.6 R2-Central Fa0/0 172.16.255.254 255.255.0.0 N/A N/A 192.168.254.254 255.255.255.0 192.168.254.253 Eagle Server N/A 172.31.24.254 255.255.255.0 N/A host Pod# A N/A 172.16. Pod#.1 255.255.0.0 172.16.255.254 host Pod# B N/A 172.16. Pod#. 2 255.255.0.0 172.16.255.254 S1-Central N/A 172.16.254.1 255.255.0.0 172.16.255.254 All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 CCNA Exploration Network Fundamentals: OSI Network Layer Lab 5.5.1: Examining a Route Learning Objectives Upon completion of this lab, you will be able to: • Use the route command to modify a Windows computer routing table. • Use a Windows Telnet client command telnet to connect to a Cisco router. • Examine router routes using basic Cisco IOS commands. Background For packets to travel across a network, a device must know the route to the destination network. This lab will compare how routes are used in Windows computers and the Cisco router. -

Avocent® ACS800/8000 Advanced Console System Command Reference Guide TABLE of CONTENTS
Avocent® ACS800/8000 Advanced Console System Command Reference Guide The information contained in this document is subject to change without notice and may not be suitable for all applications. While every precaution has been taken to ensure the accuracy and completeness of this document, Vertiv assumes no responsibility and disclaims all liability for damages resulting from use of this information or for any errors or omissions. Refer to other local practices or building codes as applicable for the correct methods, tools, and materials to be used in performing procedures not specifically described in this document. The products covered by this instruction manual are manufactured and/or sold by Vertiv. This document is the property of Vertiv and contains confidential and proprietary information owned by Vertiv. Any copying, use or disclosure of it without the written permission of Vertiv is strictly prohibited. Names of companies and products are trademarks or registered trademarks of the respective companies. Any questions regarding usage of trademark names should be directed to the original manufacturer. Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual to see if the issue can be resolved by following outlined procedures. Visit https://www.VertivCo.com/en-us/support/ for additional assistance. Vertiv™ | Avocent® ACS800/8000 Advanced Console System Command Reference Guide TABLE OF CONTENTS 1 Introduction, Navigation and Commands 1 1.1 AccessOptionsand -

Ubuntu Server Guide Basic Installation Preparing to Install
Ubuntu Server Guide Welcome to the Ubuntu Server Guide! This site includes information on using Ubuntu Server for the latest LTS release, Ubuntu 20.04 LTS (Focal Fossa). For an offline version as well as versions for previous releases see below. Improving the Documentation If you find any errors or have suggestions for improvements to pages, please use the link at thebottomof each topic titled: “Help improve this document in the forum.” This link will take you to the Server Discourse forum for the specific page you are viewing. There you can share your comments or let us know aboutbugs with any page. PDFs and Previous Releases Below are links to the previous Ubuntu Server release server guides as well as an offline copy of the current version of this site: Ubuntu 20.04 LTS (Focal Fossa): PDF Ubuntu 18.04 LTS (Bionic Beaver): Web and PDF Ubuntu 16.04 LTS (Xenial Xerus): Web and PDF Support There are a couple of different ways that the Ubuntu Server edition is supported: commercial support and community support. The main commercial support (and development funding) is available from Canonical, Ltd. They supply reasonably- priced support contracts on a per desktop or per-server basis. For more information see the Ubuntu Advantage page. Community support is also provided by dedicated individuals and companies that wish to make Ubuntu the best distribution possible. Support is provided through multiple mailing lists, IRC channels, forums, blogs, wikis, etc. The large amount of information available can be overwhelming, but a good search engine query can usually provide an answer to your questions. -

Linux Commands Arp -A Display the Content of the ARP Cache
Linux Commands arp -a Display the content of the ARP cache. arp –d IPaddress Deletes the entry with the IP address IPaddress. arp –s IPaddress MACAddress Adds a static entry to the ARP cache that is never overwritten by network events. The MAC address is entered as 6 hexadecimal bytes separated by colons. Example: arp –s 10.0.1.12 00:02:2D:0D:68:C1 ip –s –s neigh flush all command to clear the arp cache ip address add IPAddr/xx dev interface Adds IPAddr with prefix xx to interface. E.g., ip address add 128.10.1.10/24 dev eth0 ip address del IPAddr/xx dev interface Deletes IPAddr with prefix xx on interface. E.g., ip address del 128.10.1.10/24 dev eth0 ip address flush dev interface Deletes all statically assigned IP addresses for dev interface. ip address show dev interface Shows all assigned IP addresses for dev interface. netstat –i Displays a table with statistics of the currently configured network interfaces. netstat –rn Displays the kernel routing table. The –n option forces netstat to print the IP addresses. Without this option, netstat attempts to display the host names. netstat –an netstat –tan netstat -uan Displays the active network connections. The –a option display all active network connections, the –ta option displays only information on TCP connections, and the –tu option displays only information on UDP traffic. Omitting the –n option prints host names, instead of IP addresses. netstat –s Displays summary statistics for each protocol that is currently running on the host. -

Implementing Cisco IP Routing Course Overview
ROUTE: Implementing Cisco IP Routing Course Overview This course provides students with the knowledge and skills to implement Cisco IP routing, including configuring EIGRP and the OSPF protocol. Course Introduction 3m Course Introduction Chapter 01 - Routing Services 1h 1m Lesson 1: Complex Enterprise Network Frameworks, Architectures, and Models Traffic Conditions in a Converged Network IIN: Cisco Intelligent Information Network Three Phases of the Intelligent Information Network Three Phases of the Intelligent Information Network Graph Cisco SONA Framework Cisco SONA Framework Layers SONA: Networked Infrastructure Layer SONA: Interactive Services Layer SONA: Application Layer Updated SONA Framework Cisco Enterprise Architecture Campus Architecture Branch Architecture Data Center Architecture Teleworker Architecture Cisco Hierarchical Network Model Hierarchical Campus Model The Hierarchical Model in a Wide Area Network The Enterprise Composite Network Model Lesson 2: Creating, Documenting, and Executing an Implementation Plan Creating an Implementation Plan Structured Approach Ad-hoc Approach Methodologies and Models Cisco Lifecycle Services (PPDIOO) Model Implementation Plan Documentation Sample Implementation Plan Example of Project Contact List Example of Implementation Task List Example of Tools Required Example of Equipment Floor Plan Lesson 3: Overview of IP Routing IP Routing Dynamic Routing Static Routing Third Option: OnDemand Routing Link-State Versus Distance Vector Protocols Classless Versus Classful Routing Discontiguous -

Lab 2.8.1: Basic Static Route Configuration
Lab 2.8.1: Basic Static Route Configuration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 172.16.3.1 255.255.255.0 N/A R1 S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2 S0/0/0 172.16.2.2 255.255.255.0 N/A S0/0/1 192.168.1.2 255.255.255.0 N/A FA0/0 192.168.2.1 255.255.255.0 N/A R3 S0/0/1 192.168.1.1 255.255.255.0 N/A PC1 NIC 172.16.3.10 255.255.255.0 172.16.3.1 PC2 NIC 172.16.1.10 255.255.255.0 172.16.1.1 PC3 NIC 192.168.2.10 255.255.255.0 192.168.2.1 Learning Objectives Upon completion of this lab, you will be able to: • Cable a network according to the Topology Diagram. • Erase the startup configuration and reload a router to the default state. • Perform basic configuration tasks on a router. All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 20 CCNA Exploration Routing Protocols and Concepts: Static Routing Lab 2.8.1: Basic Static Route Configuration • Interpret debug ip routing output. • Configure and activate Serial and Ethernet interfaces. • Test connectivity. • Gather information to discover causes for lack of connectivity between devices. • Configure a static route using an intermediate address. -

Chapter 16, “Configuring IP Services,”
CHAPTER 16 Configuring IP Services Cisco MDS 9000 Family switches can route IP traffic between Ethernet and Fibre Channel interfaces. The IP static routing feature is used to route traffic between VSANs. To do so, each VSAN must be in a different IP subnetwork. Each Cisco MDS 9000 Family switch provides the following services for network management systems (NMS): • IP forwarding on the out-of-band Ethernet interface (mgmt0) on the front panel of the supervisor modules. • IP forwarding or in-band Fibre Channel interface using the IP over Fibre Channel (IPFC) function—IPFC specifies how IP frames can be transported over Fibre Channel using encapsulation techniques. IP frames are encapsulated into Fibre Channel frames so NMS information can cross the Fibre Channel network without using an overlay Ethernet network. • IP routing (default routing and static routing) —If your configuration does not need an external router, you can configure a default route using static routing. Switches are compliant with RFC 2338 standards for Virtual Router Redundancy Protocol (VRRP) features. VRRP is a restartable application that provides a redundant, alternate path to the gateway switch. This chapter includes the following sections: • Traffic Management Services, page 16-2 • Configuring the Ethernet Management Port, page 16-2 • Configuring the Default Gateway, page 16-3 • Configuring the Default Network, page 16-4 • Configuring IPFC, page 16-5 • Configuring IP Static Routes, page 16-6 • Displaying IP Interface Information, page 16-7 • Configuring Overlay VSANs, page 16-8 • Configuring Multiple VSANs, page 16-10 • Configuring VRRP, page 16-12 • Configuring DNS Server, page 16-19 • Default Settings, page 16-20 Cisco MDS 9000 Family Configuration Guide 78-14893-01, Cisco MDS SAN-OS Release 1.0(2) 16-1 Chapter 16 Configuring IP Services Traffic Management Services Traffic Management Services In-band options are compliant with and use the RFC 2625 standards. -

LESSON 2 ESSENTIAL COMMANDS Lesson 2: Essential Commands
LESSON 2 ESSENTIAL COMMANDS Lesson 2: Essential Commands WARNING The Hacker Highschool Project is a learning tool and as with any learning tool there are dangers. Some lessons, if abused, may result in physical injury. Some additional dangers may also exist where there is not enough research on possible effects of emanations from particular technologies. Students using these lessons should be supervised yet encouraged to learn, try, and do. However ISECOM cannot accept responsibility for how any information herein is abused. The following lessons and workbooks are open and publicly available under the following terms and conditions of ISECOM: All works in the Hacker Highschool Project are provided for non-commercial use with elementary school students, junior high school students, and high school students whether in a public institution, private institution, or a part of home-schooling. These materials may not be reproduced for sale in any form. The provision of any class, course, training, or camp with these materials for which a fee is charged is expressly forbidden without a license, including college classes, university classes, trade-school classes, summer or computer camps, and similar. To purchase a license, visit the LICENSE section of the HHS web page at http://www.hackerhighschool.org/licensing.html. The Hacker Highschool Project Project is an open community effort and if you find value in this project, we ask that you support us through the purchase of a license, a donation, or sponsorship. 2 Lesson 2: Essential Commands Table