Hyper-Image Network?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Image Spam Detection: Problem and Existing Solution
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 06 Issue: 02 | Feb 2019 www.irjet.net p-ISSN: 2395-0072 Image Spam Detection: Problem and Existing Solution Anis Ismail1, Shadi Khawandi2, Firas Abdallah3 1,2,3Faculty of Technology, Lebanese University, Lebanon ----------------------------------------------------------------------***--------------------------------------------------------------------- Abstract - Today very important means of communication messaging spam, Internet forum spam, junk fax is the e-mail that allows people all over the world to transmissions, and file sharing network spam [1]. People communicate, share data, and perform business. Yet there is who create electronic spam are called spammers [2]. nothing worse than an inbox full of spam; i.e., information The generally accepted version for source of spam is that it crafted to be delivered to a large number of recipients against their wishes. In this paper, we present a numerous anti-spam comes from the Monty Python song, "Spam spam spam spam, methods and solutions that have been proposed and deployed, spam spam spam spam, lovely spam, wonderful spam…" Like but they are not effective because most mail servers rely on the song, spam is an endless repetition of worthless text. blacklists and rules engine leaving a big part on the user to Another thought maintains that it comes from the computer identify the spam, while others rely on filters that might carry group lab at the University of Southern California who gave high false positive rate. it the name because it has many of the same characteristics as the lunchmeat Spam that is nobody wants it or ever asks Key Words: E-mail, Spam, anti-spam, mail server, filter. -

The Imagined Voice 2017 JULY
Cover Page The handle http://hdl.handle.net/1887/58691 holds various files of this Leiden University dissertation. Author: Kyriakides, Y. Title: Imagined Voices : a poetics of Music-Text-Film Issue Date: 2017-12-21 Imagined Voices A Poetics of Music-Text-Film Yannis Kyriakides Imagined Voices A Poetics of Music-Text-Film Proefschrift ter verkrijging van de graad van Doctor aan de Universiteit Leiden op gezag van Rector Magnificus prof.mr. C.J.J.M. Stolker, volgens besluit van het College voor Promoties te verdedigen op donderdag 21 december 2017 klokke 15.00 uur door Yannis Kyriakides geboren te Limassol (CY) in 1969 Promotores Prof. Frans de Ruiter Universiteit Leiden Prof.dr. Marko Ciciliani Universität für Musik und darstellende Kunst, Graz Copromotor Dr. Catherine Laws University of York/ Orpheus Instituut, Gent Promotiecommissie Prof.dr. Marcel Cobussen Universiteit Leiden Prof.dr. Nicolas Collins School of the Art Institute of Chicago Prof.dr. Sander van Maas Universiteit van Amsterdam Prof.dr. Cathy van Eck Bern University of the Arts Dr. Vincent Meelberg Radboud Universiteit, Nijmegen/ docARTES, Gent Faculteit der Geesteswetenschappen Academy of Creative and Performing Arts (ACPA) Table of Contents Acknowledgements 1 Introduction 4 PART I: Three Voices 16 Chapter 1: The Mimetic Voice 17 1.1 Art Imitates 18 1.2 Cognitive Immersion 24 1.3 Vocal Embodiment 27 1.4 Subvocalisation 32 1.5 Inner Speech 35 1.6 Silent Voices 38 Chapter 2: The Diegetic Voice 41 2.1 Narration 43 2.2 Paratext 46 2.3 Narrational Network 48 2.4 Temporality -

DVD-Ofimática 2014-07
(continuación 2) Calizo 0.2.5 - CamStudio 2.7.316 - CamStudio Codec 1.5 - CDex 1.70 - CDisplayEx 1.9.09 - cdrTools FrontEnd 1.5.2 - Classic Shell 3.6.8 - Clavier+ 10.6.7 - Clementine 1.2.1 - Cobian Backup 8.4.0.202 - Comical 0.8 - ComiX 0.2.1.24 - CoolReader 3.0.56.42 - CubicExplorer 0.95.1 - Daphne 2.03 - Data Crow 3.12.5 - DejaVu Fonts 2.34 - DeltaCopy 1.4 - DVD-Ofimática Deluge 1.3.6 - DeSmuME 0.9.10 - Dia 0.97.2.2 - Diashapes 0.2.2 - digiKam 4.1.0 - Disk Imager 1.4 - DiskCryptor 1.1.836 - Ditto 3.19.24.0 - DjVuLibre 3.5.25.4 - DocFetcher 1.1.11 - DoISO 2.0.0.6 - DOSBox 0.74 - DosZip Commander 3.21 - Double Commander 0.5.10 beta - DrawPile 2014-07 0.9.1 - DVD Flick 1.3.0.7 - DVDStyler 2.7.2 - Eagle Mode 0.85.0 - EasyTAG 2.2.3 - Ekiga 4.0.1 2013.08.20 - Electric Sheep 2.7.b35 - eLibrary 2.5.13 - emesene 2.12.9 2012.09.13 - eMule 0.50.a - Eraser 6.0.10 - eSpeak 1.48.04 - Eudora OSE 1.0 - eViacam 1.7.2 - Exodus 0.10.0.0 - Explore2fs 1.08 beta9 - Ext2Fsd 0.52 - FBReader 0.12.10 - ffDiaporama 2.1 - FileBot 4.1 - FileVerifier++ 0.6.3 DVD-Ofimática es una recopilación de programas libres para Windows - FileZilla 3.8.1 - Firefox 30.0 - FLAC 1.2.1.b - FocusWriter 1.5.1 - Folder Size 2.6 - fre:ac 1.0.21.a dirigidos a la ofimática en general (ofimática, sonido, gráficos y vídeo, - Free Download Manager 3.9.4.1472 - Free Manga Downloader 0.8.2.325 - Free1x2 0.70.2 - Internet y utilidades). -

157 Software Tools. No Fees. No Expiration Dates. No Problems
BestFree Software 157 software tools. No fees. No expiration dates. No problems. Sometimes even no downloads. No kidding. By Eric Griffith and PC Magazine staff We did the math: If you bought popular GIMP www.gimp.org add-ons means there's not much this apps instead of trying their gratis counter- Windows ! MacOS | Linux The GNU Im- program won't do, from calendars to parts, at the manufacturers' iist prices age Manipulation Program (GIMP) does encryption. you'd be out $5,183 and change! Why spend most of what Photoshop does; the Gimp- money when you can get what you need shop project [plastiebugs.com) even UbuntU www.ubuntu.com for nothing? Sometimes, you do get what makes it look like Photoshop. Linux This Linux-based OS comes with you don't pay for. many of these Hall of Fame products iTunes www,apple.com/itunes (Firefox. OpenOffice.org) preinstalled. Hall of Fame windows I MacOS When you're attached to (See "OS Wars," page 87.) the top media player in the land (iPod), Adobe Reader www.adobe.com success is a given. iTunes continues to Win Amp www.winamp.com windows I MacOS I LinuK | Mobile This sim- build sales and refine its organization Windows After a decade of playing mu- plest of Adobe's PDF programs lets you of songs, video, games, podcasts, and sic, the "skinnable" WinAmp has several do just about anything PDF-related (be- more. versions, including one with full CD rip- sides create new ones), including online ping and burning. collaboration. It includes a host of fea- OpenOffice.org www.openoff ice.org tures to aid users with disabilities. -

Anti-Spam Methods
INTRODUCTION Spamming is flooding the Internet with many copies of the same message, in an attempt to force the message on people who would not otherwise choose to receive it. Most spam is commercial advertising, often for dubious products, get-rich-quick schemes, or quasi- legal services. Spam costs the sender very little to send -- most of the costs are paid for by the recipient or the carriers rather than by the sender. There are two main types of spam, and they have different effects on Internet users. Cancellable Usenet spam is a single message sent to 20 or more Usenet newsgroups. (Through long experience, Usenet users have found that any message posted to so many newsgroups is often not relevant to most or all of them.) Usenet spam is aimed at "lurkers", people who read newsgroups but rarely or never post and give their address away. Usenet spam robs users of the utility of the newsgroups by overwhelming them with a barrage of advertising or other irrelevant posts. Furthermore, Usenet spam subverts the ability of system administrators and owners to manage the topics they accept on their systems. Email spam targets individual users with direct mail messages. Email spam lists are often created by scanning Usenet postings, stealing Internet mailing lists, or searching the Web for addresses. Email spams typically cost users money out-of-pocket to receive. Many people - anyone with measured phone service - read or receive their mail while the meter is running, so to speak. Spam costs them additional money. On top of that, it costs money for ISPs and online services to transmit spam, and these costs are transmitted directly to subscribers. -

Technical Notes All Changes in Fedora 13
Fedora 13 Technical Notes All changes in Fedora 13 Edited by The Fedora Docs Team Copyright © 2010 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https:// fedoraproject.org/wiki/Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. All other trademarks are the property of their respective owners. Abstract This document lists all changed packages between Fedora 12 and Fedora 13. -

Freeware-List.Pdf
FreeWare List A list free software from www.neowin.net a great forum with high amount of members! Full of information and questions posted are normally answered very quickly 3D Graphics: 3DVia http://www.3dvia.com...re/3dvia-shape/ Anim8or - http://www.anim8or.com/ Art Of Illusion - http://www.artofillusion.org/ Blender - http://www.blender3d.org/ CreaToon http://www.creatoon.com/index.php DAZ Studio - http://www.daz3d.com/program/studio/ Freestyle - http://freestyle.sourceforge.net/ Gelato - http://www.nvidia.co...ge/gz_home.html K-3D http://www.k-3d.org/wiki/Main_Page Kerkythea http://www.kerkythea...oomla/index.php Now3D - http://digilander.li...ng/homepage.htm OpenFX - http://www.openfx.org OpenStages http://www.openstages.co.uk/ Pointshop 3D - http://graphics.ethz...loadPS3D20.html POV-Ray - http://www.povray.org/ SketchUp - http://sketchup.google.com/ Sweet Home 3D http://sweethome3d.sourceforge.net/ Toxic - http://www.toxicengine.org/ Wings 3D - http://www.wings3d.com/ Anti-Virus: a-squared - http://www.emsisoft..../software/free/ Avast - http://www.avast.com...ast_4_home.html AVG - http://free.grisoft.com/ Avira AntiVir - http://www.free-av.com/ BitDefender - http://www.softpedia...e-Edition.shtml ClamWin - http://www.clamwin.com/ Microsoft Security Essentials http://www.microsoft...ity_essentials/ Anti-Spyware: Ad-aware SE Personal - http://www.lavasoft....se_personal.php GeSWall http://www.gentlesec...m/download.html Hijackthis - http://www.softpedia...ijackThis.shtml IObit Security 360 http://www.iobit.com/beta.html Malwarebytes' -
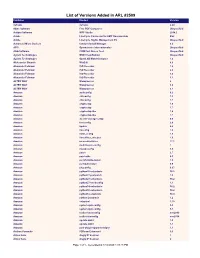
List of Versions Added in ARL #2509
List of Versions Added in ARL #2509 Publisher Product Version 3uTools 3uTools 2.20 4dots Software Free PDF Compress Unspecified Actipro Software WPF Studio 2014.2 Adobe LiveCycle Connector for EMC Documentum ES2 Adobe LiveCycle Rights Management ES Unspecified Advanced Micro Devices Catalyst Install Manager 8.0 AFIP Operaciones Internacionales Unspecified AGG Software COM Port Stress Test Unspecified Agilent Technologies MSD ChemStation Unspecified Agilent Technologies OpenLAB MatchCompare 1.0 Aleksander Simonic WinEdt 8.0 Alexander Feinman ISO Recorder 1.0 Alexander Feinman ISO Recorder 2.0 Alexander Feinman ISO Recorder 3.0 Alexander Feinman ISO Recorder 3.1 ALTER WAY WampServer 2 ALTER WAY WampServer 3.0 ALTER WAY WampServer 3.1 Amazon authconfig 6.2 Amazon chkconfig 1.3 Amazon chkconfig 1.7 Amazon cryptsetup 1.6 Amazon cryptsetup 1.7 Amazon cryptsetup-libs 1.6 Amazon cryptsetup-libs 1.7 Amazon docker-storage-setup 0.6 Amazon fontconfig 2.8 Amazon kpatch 0.4 Amazon libconfig 1.4 Amazon libini_config 1.3 Amazon libnetfilter_cthelper 1.0 Amazon mesa-dri-drivers 17.1 Amazon multilib-rpm-config 1 Amazon mysql-config 5.5 Amazon patch 2.7 Amazon patchutils 0.3 Amazon perl-ExtUtils-Install 1.5 Amazon perl-Sub-Install 0.9 Amazon pkgconfig 0.27 Amazon python26-setuptools 36.2 Amazon python27-jsonpatch 1.2 Amazon python27-setuptools 36.2 Amazon python27-sssdconfig 1.1 Amazon python34-setuptools 36.2 Amazon python36-setuptools 36.2 Amazon python3-setuptools 38.4 Amazon python-jsonpatch 1.2 Amazon setuptool 1.19 Amazon system-rpm-config 9.0 Amazon -

FULL LIST of APPS ACE-MSI SR2 1040 Works Acroprint Attendance Rx 1040Scan ACT! 1099-Etc
FULL LIST OF APPS ACE-MSI SR2 1040 Works Acroprint Attendance Rx 1040Scan ACT! 1099-Etc. Act-3D Lumion Free 1Password actiTime 247Security DVRViewer Active State Password Gorilla 2BrightSparks SyncBackPro ActiveHelper Support Panel Desktop 2X SecureRDP Acumatica ERP 3M Products for Microsoft Office Adams Tax Forms Helper 3Rivers Cotton Merchant Application AdaptCRM Enterprise 4Team Sync2 Address Accelerator/ Postal Saver Plugin for Raiser's Edge 5 Minute Financials ADLware QuickBooks Integration 7-Zip Adobe Acrobat Standard A2iA CheckReader Adobe Acrobat AutoPortfolio AbacusLaw Adobe Acrobat Pro AbacusLaw Accounting Adobe Acrobat Reader AbacusLaw Workstation Adobe AIR ABBYY FineReader Adobe Contribute Abila Fundraising Adobe Creative Cloud Abila MIP Fund Accounting Adobe Creative Suite Ability PC-ACE Adobe Customization Wizard Able2Extract Adobe Digital Editions Able2Extract PDF Converter Adobe Dreamweaver About Time Adobe Firework AbstractExpress Adobe Flash Player Accelrys Materials Studio Adobe FormsCentral Account Ability Import Adobe Illustrator Account Ability PDF Writer Adobe InCopy CS6 Account Ability Tax Form Preparation Adobe InDesign Accountants Workflow Solutions Access Database Adobe LiveCycle Designer AccountEdge Pro Adobe PageMaker Accounting CS Adobe PDF iFilter Accounting Link for NAPA TracsAcct1st Adobe Photoshop ACCTivate! Adobe Reader Accubid ChangeOrder Adobe Shockwave Player Accubid Livecount ADP PayConnexion Accubid Pro ADP Payroll for Windows AccuLink Adapter ADP PaySpecialist AccuPOS ADP ReportSmith AccuServer -

Gépfejlesztés 2011 Befoltozva
DVD DVD Windows fejlesztése ingyen R 60 1 Friss 9 GB 2011 A LEGÚJABB DRIVEREK, HASZNOS PROGRAMOK, Tuningolja fel PC-jét eredeti, szuperbiztonságos Microsoft eszközökkel – mind a DVD-n! A HÓNAP JÁTÉKAI, EXKLUZÍV CSOMAgok… Így lesz tökéletesen néma a PC-je! R 74 GO DIGITAL! Anonim az interneten Okos cserékkel a lehető legkevesebből 2011/1 _ CHIPONLINE.HU A nagy biztonsági csomag A legjobb vírusirtók, valóban Egy kattintással: védett mód böngészőjében, maximális védelem minden fontos adatának 760 biztonsági rés Mindent frissít Új biztonsági szoftver: zseniális automatikus frissítés funkcióval befoltozva Rések, hibák, bugok: így védheti meg PC-jét a hanyagul programozott szoftverektől R 28 A legjobb Minden HDD eszközök internetes Drive Washer+ nyomkövető Disk Rescue törölve! Mit érdemes bővíteni? Exkluzív! Most a DVD-n: Gépfejlesztés 2011 Az összes korábbi Spóroljon sokat: csak a leghatékonyabb fejlesztések 40 teljes verzió R A 25 legjobb fizetős program Nagy karácsonyi ajándékcsomag: mind ingyen, mind teljes funkcionalitással R 18 Plusz: Az optikai tárolás vége 6 további exkluzív Ellepték a CD/DVD lemezek? Nem bízik bennük? CHIP csomag Megmutatjuk, mivel helyettesítse őket megbízhatóan R 46 1995 Ft, előfizetéssel 1395 Ft XXIII. évfolyam, 1. szám, 2011. január 25 teljes verzió most ajándékba 760 >> biztonsági rés befoltozva Windows >> fejlesztése ingyen Az >> optikai adattárolás Gépfejlesztésvége >> 2011A tökéletesen>> néma PCA 10>> legjobb jelszótipp PC-hozzáférés >> bárhonnan Kiadja a Motor-Presse Budapest Lapkiadó Kft. DVD DVD Windows -

F14 UK-Catalogue.Pdf
Harper UK Adult Fall 2014 Running Wild J. G. Ballard, Adam Phillips Summary A highsecurity luxury housing estate in the Thames Valley is the setting for a disturbing outbreak of violence in this compelling novella from the acclaimed author of 'Cocaine Nights' and 'SuperCannes'. Pangbourne Village housing estate is exclusive, expensive and protected from the outside world by the very latest in security systems. It should be the perfect place to bring up a child. So why, in the space of ten minutes early one morning, were the thirtytwo adult residents brutally murdered, and all thirteen children abducted? No kidnapper has ever come forward, and the police are mystified. It is only when psychiatrist Richard Greville is called in that the truth behind the massacre gradually becomes clear… Contributor Bio J. G. Ballard was born in 1930 in Shanghai, where his father was a businessman. After internment in a civilian prison camp, he and his family returned to England in 1946. He published his first novel, The Drowned World, in 1961. His 1984 bestseller Empire of the Fourth Estate Sun won the Guardian Fiction Prize and the James Tait Black Memorial Prize, and was 9780006548195 shortlisted for the Booker Prize. His memoir Miracles of Life was published in 2008. J. G. 0006548199 Ballard died in 2009. Pub Date: 9/2/2014 On Sale Date: 9/2/2014 Ship Date: 8/22/2014 Quotes $17.99/$17.99 Can./£8.99 UK 'A tight, macabre tale…A wellconstructed and superbly written novella. As a malevolent Bformat Paperback gesture in the direction of facts we prefer to ignore, it provides a salutary chill.' 112 Pages Jonathan Coe, Guardian Fiction / Literary FIC019000 'In words as crisp as a wellcut film, Ballard's gripping story shocks middleclass 130.000 mm W | 197.000 mm H | 90.000 gr Wt assumptions to the roots.' Mail on Sunday 5.12in W | 7.76in H | 90gr Wt Status:ACTIVE 'Has the impact of a blackandwhite television documentary. -

The Construction of the Baby Boomer Generation As a Social Problem in Britain.Pdf
Kent Academic Repository Full text document (pdf) Citation for published version Bristow, Jennie (2015) The construction of the Baby Boomer generation as a social problem in Britain. Doctor of Philosophy (PhD) thesis, University of Kent,. DOI Link to record in KAR https://kar.kent.ac.uk/47655/ Document Version UNSPECIFIED Copyright & reuse Content in the Kent Academic Repository is made available for research purposes. Unless otherwise stated all content is protected by copyright and in the absence of an open licence (eg Creative Commons), permissions for further reuse of content should be sought from the publisher, author or other copyright holder. Versions of research The version in the Kent Academic Repository may differ from the final published version. Users are advised to check http://kar.kent.ac.uk for the status of the paper. Users should always cite the published version of record. Enquiries For any further enquiries regarding the licence status of this document, please contact: [email protected] If you believe this document infringes copyright then please contact the KAR admin team with the take-down information provided at http://kar.kent.ac.uk/contact.html The construction of the Baby Boomer generation as a social problem in Britain. PhD Thesis Jennie Bristow School of Social Policy, Sociology and Social Research University of Kent Supervisors: Professor Frank Furedi Dr Ellie Lee 8 February 2015 1 Abstract The research presented in this thesis investigates how the ‘Baby Boomer generation’ has become constructed as a social problem in Britain. I begin by outlining the theoretical orientation of the research, which is grounded in Mannheim’s understanding that the problem of generations is to do with the interaction between generational location and wider social forces.