POL211H1F: Intelligence, Disinformation, and Deception— Challenges of Global Governance in the Digital Age
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PDF Van Tekst
Onze Taal. Jaargang 73 bron Onze Taal. Jaargang 73. Genootschap Onze Taal, Den Haag 2004 Zie voor verantwoording: https://www.dbnl.org/tekst/_taa014200401_01/colofon.php Let op: werken die korter dan 140 jaar geleden verschenen zijn, kunnen auteursrechtelijk beschermd zijn. 1 [Nummer 1] Onze Taal. Jaargang 73 4 Vervlakt de intonatie? Ouderen en jongeren met elkaar vergeleken Vincent J. van Heuven - Fonetisch Laboratorium, Universiteit Leiden Ouderen kunnen jongeren vaak maar moeilijk verstaan. Ze praten te snel, te slordig en vooral te monotoon, zo luidt de klacht. Zou dat wijzen op een verandering? Wordt de Nederlandse zinsmelodie inderdaad steeds vlakker? Twee onderzoeken bieden meer duidelijkheid. Ik heb twee zoons in de adolescente leeftijdsgroep, zo tussen de 16 en de 20. Toen ik ze nog dagelijks om me heen had (ze zijn inmiddels technisch gesproken volwassen en het huis uit), mocht ik graag luistervinken als ze in gesprek waren met hun vrienden. Dan viel op dat alle jongens, niet alleen de mijne, snel spraken, met weinig stemverheffing, en vooral met weinig melodie. Het leek wel of ze het erom deden. Een Amerikaanse collega, die elk jaar een paar weken bij mij logeert om zijn Nederlands bij te houden, gaf ongevraagd toe dat hij in het algemeen weinig moeite heeft om Nederlanders te verstaan, behalve dan mijn zoons en hun vrienden. Een paar jaar eerder was ik in een onderzoek beoordelaar van de uitspraak van 120 Nederlanders, in leeftijd variërend van puber tot bejaarde. Mij viel op dat de bejaarden zo veel prettiger waren om naar te luisteren. Niet alleen spraken ze langzamer dan de jongeren, maar vooral maakten ze veel beter gebruik van de mogelijkheden die onze taal biedt om de boodschap met behulp van het stemgebruik te structureren. -

Deception, Disinformation, and Strategic Communications: How One Interagency Group Made a Major Difference by Fletcher Schoen and Christopher J
STRATEGIC PERSPECTIVES 11 Deception, Disinformation, and Strategic Communications: How One Interagency Group Made a Major Difference by Fletcher Schoen and Christopher J. Lamb Center for Strategic Research Institute for National Strategic Studies National Defense University Institute for National Strategic Studies National Defense University The Institute for National Strategic Studies (INSS) is National Defense University’s (NDU’s) dedicated research arm. INSS includes the Center for Strategic Research, Center for Complex Operations, Center for the Study of Chinese Military Affairs, Center for Technology and National Security Policy, Center for Transatlantic Security Studies, and Conflict Records Research Center. The military and civilian analysts and staff who comprise INSS and its subcomponents execute their mission by conducting research and analysis, publishing, and participating in conferences, policy support, and outreach. The mission of INSS is to conduct strategic studies for the Secretary of Defense, Chairman of the Joint Chiefs of Staff, and the Unified Combatant Commands in support of the academic programs at NDU and to perform outreach to other U.S. Government agencies and the broader national security community. Cover: Kathleen Bailey presents evidence of forgeries to the press corps. Credit: The Washington Times Deception, Disinformation, and Strategic Communications: How One Interagency Group Made a Major Difference Deception, Disinformation, and Strategic Communications: How One Interagency Group Made a Major Difference By Fletcher Schoen and Christopher J. Lamb Institute for National Strategic Studies Strategic Perspectives, No. 11 Series Editor: Nicholas Rostow National Defense University Press Washington, D.C. June 2012 Opinions, conclusions, and recommendations expressed or implied within are solely those of the contributors and do not necessarily represent the views of the Defense Department or any other agency of the Federal Government. -

Information Warfare, International Law, and the Changing Battlefield
ARTICLE INFORMATION WARFARE, INTERNATIONAL LAW, AND THE CHANGING BATTLEFIELD Dr. Waseem Ahmad Qureshi* ABSTRACT The advancement of technology in the contemporary era has facilitated the emergence of information warfare, which includes the deployment of information as a weapon against an adversary. This is done using a numBer of tactics such as the use of media and social media to spread propaganda and disinformation against an adversary as well as the adoption of software hacking techniques to spread viruses and malware into the strategically important computer systems of an adversary either to steal confidential data or to damage the adversary’s security system. Due to the intangible nature of the damage caused By the information warfare operations, it Becomes challenging for international law to regulate the information warfare operations. The unregulated nature of information operations allows information warfare to Be used effectively By states and nonstate actors to gain advantage over their adversaries. Information warfare also enhances the lethality of hyBrid warfare. Therefore, it is the need of the hour to arrange a new convention or devise a new set of rules to regulate the sphere of information warfare to avert the potential damage that it can cause to international peace and security. ABSTRACT ................................................................................................. 901 I. INTRODUCTION ......................................................................... 903 II. WHAT IS INFORMATION WARFARE? ............................. -

The Impact of Disinformation on Democratic Processes and Human Rights in the World
STUDY Requested by the DROI subcommittee The impact of disinformation on democratic processes and human rights in the world @Adobe Stock Authors: Carme COLOMINA, Héctor SÁNCHEZ MARGALEF, Richard YOUNGS European Parliament coordinator: Policy Department for External Relations EN Directorate General for External Policies of the Union PE 653.635 - April 2021 DIRECTORATE-GENERAL FOR EXTERNAL POLICIES POLICY DEPARTMENT STUDY The impact of disinformation on democratic processes and human rights in the world ABSTRACT Around the world, disinformation is spreading and becoming a more complex phenomenon based on emerging techniques of deception. Disinformation undermines human rights and many elements of good quality democracy; but counter-disinformation measures can also have a prejudicial impact on human rights and democracy. COVID-19 compounds both these dynamics and has unleashed more intense waves of disinformation, allied to human rights and democracy setbacks. Effective responses to disinformation are needed at multiple levels, including formal laws and regulations, corporate measures and civil society action. While the EU has begun to tackle disinformation in its external actions, it has scope to place greater stress on the human rights dimension of this challenge. In doing so, the EU can draw upon best practice examples from around the world that tackle disinformation through a human rights lens. This study proposes steps the EU can take to build counter-disinformation more seamlessly into its global human rights and democracy policies. -
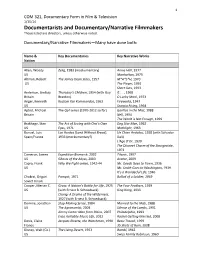
Documentarists and Documentary/Narrative Filmmakers Those Listed Are Directors, Unless Otherwise Noted
1 COM 321, Documentary Form in Film & Television 1/15/14 Documentarists and Documentary/Narrative Filmmakers Those listed are directors, unless otherwise noted. Documentary/Narrative Filmmakers—Many have done both: Name & Key Documentaries Key Narrative Works Nation Allen, Woody Zelig, 1983 (mockumentary) Annie Hall, 1977 US Manhattan, 1979 Altman, Robert The James Dean Story, 1957 M*A*S*H, 1970 US The Player, 1992 Short Cuts, 1993 Anderson, Lindsay Thursday’s Children, 1954 (with Guy if. , 1968 Britain Brenton) O Lucky Man!, 1973 Anger, Kenneth Kustom Kar Kommandos, 1963 Fireworks, 1947 US Scorpio Rising, 1964 Apted, Michael The Up! series (1970‐2012 so far) Gorillas in the Mist, 1988 Britain Nell, 1994 The World is Not Enough, 1999 Brakhage, Stan The Act of Seeing with One’s Own Dog Star Man, 1962 US Eyes, 1971 Mothlight, 1963 Bunuel, Luis Las Hurdes (Land Without Bread), Un Chien Andalou, 1928 (with Salvador Spain/France 1933 (mockumentary?) Dali) L’Age D’Or, 1930 The Discreet Charm of the Bourgeoisie, 1972 Cameron, James Expedition Bismarck, 2002 Titanic, 1997 US Ghosts of the Abyss, 2003 Avatar, 2009 Capra, Frank Why We Fight series, 1942‐44 Mr. Deeds Goes to Town, 1936 US Mr. Smith Goes to Washington, 1939 It’s a Wonderful Life, 1946 Chukrai, Grigori Pamyat, 1971 Ballad of a Soldier, 1959 Soviet Union Cooper, Merian C. Grass: A Nation’s Battle for Life, 1925 The Four Feathers, 1929 US (with Ernest B. Schoedsack) King Kong, 1933 Chang: A Drama of the Wilderness, 1927 (with Ernest B. Schoedsack) Demme, Jonathan Stop Making Sense, -

Taming the Trolls: the Need for an International Legal Framework to Regulate State Use of Disinformation on Social Media
Taming the Trolls: The Need for an International Legal Framework to Regulate State Use of Disinformation on Social Media * ASHLEY C. NICOLAS INTRODUCTION Consider a hypothetical scenario in which hundreds of agents of the Russian GRU arrive in the United States months prior to a presidential election.1 The Russian agents spend the weeks leading up to the election going door to door in vulnerable communities, spreading false stories intended to manipulate the population into electing a candidate with policies favorable to Russian positions. The agents set up television stations, use radio broadcasts, and usurp the resources of local newspapers to expand their reach and propagate falsehoods. The presence of GRU agents on U.S. soil is an incursion into territorial integrity⎯a clear invasion of sovereignty.2 At every step, Russia would be required to expend tremendous resources, overcome traditional media barriers, and risk exposure, making this hypothetical grossly unrealistic. Compare the hypothetical with the actual actions of the Russians during the 2016 U.S. presidential election. Sitting behind computers in St. Petersburg, without ever setting foot in the United States, Russian agents were able to manipulate the U.S. population in the most sacred of domestic affairs⎯an election. Russian “trolls” targeted vulnerable populations through social media, reaching millions of users at a minimal cost and without reliance on established media institutions.3 Without using * Georgetown Law, J.D. expected 2019; United States Military Academy, B.S. 2009; Loyola Marymount University M.Ed. 2016. © 2018, Ashley C. Nicolas. The author is a former U.S. Army Intelligence Officer. -

Michael Moore: a Man on a Mission Or How Far A
Michael Moore: A Man on a Mission or How Far a Reinvigorated Populism Can Take Us Garry Watson (Cineaction 70) My focus in this essay will be on Michael Mooreʼs four documentaries – Roger and Me (1989), The Big One (1997), Bowling for Columbine (2002) and Fahrenheit 9/11 (2004) – with most of my attention being given to the first and third of these, and least to the second. These four films are significant and worth studying for a number of reasons: (i) The size of the audiences they have succeeded in reaching; (ii) the political impact they have had (on which, among other things, see Robert Brent Toplinʼs useful book on Michael Mooreʼs “Fahreneit 9/11”: How One Film Divided A Nation [2006]); (iii) and the extent to which they helped prepare the reception for such recent political documentaries as, for example, Errol Morrisʼs The Fog of War (2004), Mark Achbar and Jennifer Abbottʼs The Corporation (2005), Alex Gibneyʼs Enron: The Smartest Guys in the Room (2005), Eugene Jareckiʼs Why We Fight (2005), David Guggenheimʼs An Inconvenient Truth (2006), and Chris Paineʼs Who Killed the Electric Car? (2006). It may not be redundant to rehearse some of the facts. If Roger and Me was more successful at the box office than any documentary that preceded it, Moore went on to break the same record on two subsequent occasions – first with Bowling for Columbine, then with Fahrenheit 9/11. And as far as the latter is concerned, we get some sense of the excitement that was generated when it first screened in the US by the Foreword that John Berger wrote in 2004 for The Official “Fahrenheit 9/11” Reader (while the film was “still playing in hundreds of theaters across America”1). -

PERSUADE OR PERISH Addressing Gaps in the U.S
PERSUADE OR PERISH Addressing Gaps in the U.S. Posture to Confront Propaganda and Disinformation Threats Dr. Haroro J. Ingram Program on Extremism Policy Paper February 2020 PERSUADE OR PERISH 1 INGRAM | PROGRAM ON EXTREMISM Abstract: The purpose of this policy paper is to assess the U.S. government’s posture to deal with malicious ‘influence activities’ (i.e. propaganda and disinformation) by state and nonstate actors. It argues that while the U.S. government has provided inconsistent support for its foreign policy and national security information sector for decades, since 2017 an effort has been made to lay the foundations for a rejuvenated U.S. posture to address propaganda and disinformation threats. However, significant gaps remain that will weaken those foundation building efforts if left unaddressed. This paper concludes with four recommendations focusing on (i.) the need to learn lessons from the institutions’ history, (ii.) the value of an overarching paradigm through which to understand a spectrum of threats, (iii.) the important role of overt attributed U.S government messaging, and (iv.) initiatives to strategically cohere interagency activities. The United States and its allies are facing a complex spectrum of propaganda and disinformation threats that are rapidly evolving strategically, operationally, and technologically. 1 The U.S. government’s ability to address these malicious ‘influence activities’ will depend on its adoption of an appropriately balanced, resourced, and legislatively empowered posture that will be as much a product of institutional history as contemporary strategic-policy decisions. This policy paper assesses the U.S. government’s posture to deal with these threats and outlines ways in which strategic-policy gaps, drawn from this analysis, can be tackled. -

Bibliography
Bibliography [1] M Aamir Ali, B Arief, M Emms, A van Moorsel, “Does the Online Card Payment Landscape Unwittingly Facilitate Fraud?” IEEE Security & Pri- vacy Magazine (2017) [2] M Abadi, RM Needham, “Prudent Engineering Practice for Cryptographic Protocols”, IEEE Transactions on Software Engineering v 22 no 1 (Jan 96) pp 6–15; also as DEC SRC Research Report no 125 (June 1 1994) [3] A Abbasi, HC Chen, “Visualizing Authorship for Identification”, in ISI 2006, LNCS 3975 pp 60–71 [4] H Abelson, RJ Anderson, SM Bellovin, J Benaloh, M Blaze, W Diffie, J Gilmore, PG Neumann, RL Rivest, JI Schiller, B Schneier, “The Risks of Key Recovery, Key Escrow, and Trusted Third-Party Encryption”, in World Wide Web Journal v 2 no 3 (Summer 1997) pp 241–257 [5] H Abelson, RJ Anderson, SM Bellovin, J Benaloh, M Blaze, W Diffie, J Gilmore, M Green, PG Neumann, RL Rivest, JI Schiller, B Schneier, M Specter, D Weizmann, “Keys Under Doormats: Mandating insecurity by requiring government access to all data and communications”, MIT CSAIL Tech Report 2015-026 (July 6, 2015); abridged version in Communications of the ACM v 58 no 10 (Oct 2015) [6] M Abrahms, “What Terrorists Really Want”,International Security v 32 no 4 (2008) pp 78–105 [7] M Abrahms, J Weiss, “Malicious Control System Cyber Security Attack Case Study – Maroochy Water Services, Australia”, ACSAC 2008 [8] A Abulafia, S Brown, S Abramovich-Bar, “A Fraudulent Case Involving Novel Ink Eradication Methods”, in Journal of Forensic Sciences v41(1996) pp 300-302 [9] DG Abraham, GM Dolan, GP Double, JV Stevens, -
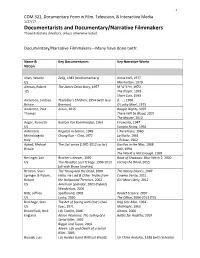
Documentarists and Documentary/Narrative Filmmakers Those Listed Are Directors, Unless Otherwise Noted
1 COM 321, Documentary Form in Film, Television, & Interactive Media 1/27/17 Documentarists and Documentary/Narrative Filmmakers Those listed are directors, unless otherwise noted. Documentary/Narrative Filmmakers—Many have done both: Name & Key Documentaries Key Narrative Works Nation Allen, Woody Zelig, 1983 (mockumentary) Annie Hall, 1977 US Manhattan, 1979 Altman, Robert The James Dean Story, 1957 M*A*S*H, 1970 US The Player, 1992 Short Cuts, 1993 Anderson, Lindsay Thursday’s Children, 1954 (with Guy if. , 1968 Britain Brenton) O Lucky Man!, 1973 Anderson, Paul Junun, 2015 Boogie Nights, 1997 Thomas There Will be Blood, 2007 The Master, 2012 Anger, Kenneth Kustom Kar Kommandos, 1963 Fireworks, 1947 US Scorpio Rising, 1964 Antonioni, Ragazze in bianco, 1949 L’Avventura, 1960 Michelangelo Chung Kuo – Cina, 1972 La Notte, 1961 Italy L'Eclisse, 1962 Apted, Michael The Up! series (1970‐2012 so far) Gorillas in the Mist, 1988 Britain Nell, 1994 The World is Not Enough, 1999 Berlinger, Joe Brother’s Keeper, 1992 Book of Shadows: Blair Witch 2, 2000 US The Paradise Lost Trilogy, 1996-2011 Facing the Wind, 2015 (all with Bruce Sinofsky) Berman, Shari The Young and the Dead, 2000 The Nanny Diaries, 2007 Springer & Pulcini, Hello, He Lied & Other Truths from Cinema Verite, 2011 Robert the Hollywood Trenches, 2002 Girl Most Likely, 2012 US American Splendor, 2003 (hybrid) Wanderlust, 2006 Blitz, Jeffrey Spellbound, 2002 Rocket Science, 2007 US Lucky, 2010 The Office, 2006-2013 (TV) Brakhage, Stan The Act of Seeing with One’s Own Dog Star Man, -

Magazine 2/2017
B56133 The Science Magazine of the Max Planck Society 2.2017 Big Data IT SECURITY IMAGING COLLECTIVE BEHAVIOR AESTHETICS Cyber Attacks on Live View of the Why Animals The Power Free Elections Focus of Disease Swarm for Swarms of Art Dossier – The Future of Energy Find out how we can achieve CO2 neutrality and the end of dependence on fossil fuels by 2100, thus opening a new age of electricity. siemens.com/pof-future-of-energy 13057_Print-Anzeige_V01.indd 2 12.10.16 14:47 ON LOCATION Photo: Astrid Eckert/Munich Operation Darkness When, on a clear night, you gaze at twinkling stars, glimmering planets or the cloudy band of the Milky Way, you are actually seeing only half the story – or, to be more precise, a tiny fraction of it. With the telescopes available to us, using all of the possible ranges of the electromagnetic spectrum, we can observe only a mere one percent of the universe. The rest remains hidden, spread between dark energy and dark matter. The latter makes up over 20 percent of the cosmos. And it is this mysterious substance that is the focus of scien- tists involved in the CRESST Experiment. Behind this simple sounding name is a complex experiment, the “Cryogenic Rare Event Search with Superconducting Thermometers.” The site of the unusual campaign is the deep underground laboratory under the Gran Sasso mountain range in Italy’s Abruzzo region. Fully shielded by 1,400 meters of rock, the researchers here – from the Max Planck Institute for Physics, among others – have installed a special device whose job is to detect particles of dark matter. -

Empathize with Your Enemy”
PEACE AND CONFLICT: JOURNAL OF PEACE PSYCHOLOGY, 10(4), 349–368 Copyright © 2004, Lawrence Erlbaum Associates, Inc. Lesson Number One: “Empathize With Your Enemy” James G. Blight and janet M. Lang Thomas J. Watson Jr. Institute for International Studies Brown University The authors analyze the role of Ralph K. White’s concept of “empathy” in the context of the Cuban Missile Crisis, Vietnam War, and firebombing in World War II. They fo- cus on the empathy—in hindsight—of former Secretary of Defense Robert S. McNamara, as revealed in the various proceedings of the Critical Oral History Pro- ject, as well as Wilson’s Ghost and Errol Morris’s The Fog of War. Empathy is the great corrective for all forms of war-promoting misperception … . It [means] simply understanding the thoughts and feelings of others … jumping in imagination into another person’s skin, imagining how you might feel about what you saw. Ralph K. White, in Fearful Warriors (White, 1984, p. 160–161) That’s what I call empathy. We must try to put ourselves inside their skin and look at us through their eyes, just to understand the thoughts that lie behind their decisions and their actions. Robert S. McNamara, in The Fog of War (Morris, 2003a) This is the story of the influence of the work of Ralph K. White, psychologist and former government official, on the beliefs of Robert S. McNamara, former secretary of defense. White has written passionately and persuasively about the importance of deploying empathy in the development and conduct of foreign policy. McNamara has, as a policymaker, experienced the success of political decisions made with the benefit of empathy and borne the responsibility for fail- Requests for reprints should be sent to James G.