AT Commands, S-Registers, and Result Codes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AT Command User Guide 80591ST10886A Rev
LN940 SERIES AT Command User Guide 80591ST10886A Rev. 1.4 – 2018-04-05 ] 7 .201 Mod. 0806 2017-01 Rev.6 01 [ SPECIFICATIONS ARE SUBJECT TO CHANGE WITHOUT NOTICE NOTICES LIST While reasonable efforts have been made to assure the accuracy of this document, Telit assumes no liability resulting from any inaccuracies or omissions in this document, or from use of the information obtained herein. The information in this document has been carefully checked and is believed to be reliable. However, no responsibility is assumed for inaccuracies or omissions. Telit reserves the right to make changes to any products described herein and reserves the right to revise this document and to make changes from time to time in content hereof with no obligation to notify any person of revisions or changes. Telit does not assume any liability arising out of the application or use of any product, software, or circuit described herein; neither does it convey license under its patent rights or the rights of others. It is possible that this publication may contain references to, or information about Telit products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that Telit intends to announce such Telit products, programming, or services in your country. COPYRIGHTS This instruction manual and the Telit products described in this instruction manual may be, include or describe copyrighted Telit material, such as computer programs stored in semiconductor memories or other media. Laws in the Italy and other countries preserve for Telit and its licensors certain exclusive rights for copyrighted material, including the exclusive right to copy, reproduce in any form, distribute and make derivative works of the copyrighted material. -

Lab - Observing DNS Resolution (Instructor Version) Instructor Note: Red Font Color Or Gray Highlights Indicate Text That Appears in the Instructor Copy Only
Lab - Observing DNS Resolution (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail Servers Background / Scenario The Domain Name System (DNS) is invoked when you type a Uniform Resource Locator (URL), such as http://www.cisco.com, into a web browser. The first part of the URL describes which protocol is used. Common protocols are Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol over Secure Socket Layer (HTTPS), and File Transfer Protocol (FTP). DNS uses the second part of the URL, which in this example is www.cisco.com. DNS translates the domain name (www.cisco.com) to an IP address to allow the source host to reach the destination host. In this lab, you will observe DNS in action and use the nslookup (name server lookup) command to obtain additional DNS information. Work with a partner to complete this lab. Required Resources 1 PC (Windows 7, Vista, or XP with Internet and command prompt access) Part 1: Observe the DNS Conversion of a URL to an IP Address a. Click the Windows Start button, type cmd into the search field, and press Enter. The command prompt window appears. b. At the command prompt, ping the URL for the Internet Corporation for Assigned Names and Numbers (ICANN) at www.icann.org. ICANN coordinates the DNS, IP addresses, top-level domain name system management, and root server system management functions. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

NETSTAT Command
NETSTAT Command | NETSTAT Command | Use the NETSTAT command to display network status of the local host. | | ┌┐────────────── | 55──NETSTAT─────6─┤ Option ├─┴──┬────────────────────────────────── ┬ ─ ─ ─ ────────────────────────────────────────5% | │┌┐───────────────────── │ | └─(──SELect───6─┤ Select_String ├─┴ ─ ┘ | Option: | ┌┐─COnn────── (1, 2) ──────────────── | ├──┼─────────────────────────── ┼ ─ ──────────────────────────────────────────────────────────────────────────────┤ | ├─ALL───(2)──────────────────── ┤ | ├─ALLConn─────(1, 2) ────────────── ┤ | ├─ARp ipaddress───────────── ┤ | ├─CLients─────────────────── ┤ | ├─DEvlinks────────────────── ┤ | ├─Gate───(3)─────────────────── ┤ | ├─┬─Help─ ┬─ ───────────────── ┤ | │└┘─?──── │ | ├─HOme────────────────────── ┤ | │┌┐─2ð────── │ | ├─Interval─────(1, 2) ─┼───────── ┼─ ┤ | │└┘─seconds─ │ | ├─LEVel───────────────────── ┤ | ├─POOLsize────────────────── ┤ | ├─SOCKets─────────────────── ┤ | ├─TCp serverid───(1) ─────────── ┤ | ├─TELnet───(4)───────────────── ┤ | ├─Up──────────────────────── ┤ | └┘─┤ Command ├───(5)──────────── | Command: | ├──┬─CP cp_command───(6) ─ ┬ ────────────────────────────────────────────────────────────────────────────────────────┤ | ├─DELarp ipaddress─ ┤ | ├─DRop conn_num──── ┤ | └─RESETPool──────── ┘ | Select_String: | ├─ ─┬─ipaddress────(3) ┬ ─ ───────────────────────────────────────────────────────────────────────────────────────────┤ | ├─ldev_num─────(4) ┤ | └─userid────(2) ─── ┘ | Notes: | 1 Only ALLCON, CONN and TCP are valid with INTERVAL. | 2 The userid -

Introduction to Unix Shell
Introduction to Unix Shell François Serra, David Castillo, Marc A. Marti- Renom Genome Biology Group (CNAG) Structural Genomics Group (CRG) Run Store Programs Data Communicate Interact with each other with us The Unix Shell Introduction Interact with us Rewiring Telepathy Typewriter Speech WIMP The Unix Shell Introduction user logs in The Unix Shell Introduction user logs in user types command The Unix Shell Introduction user logs in user types command computer executes command and prints output The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output ⋮ user logs off The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output ⋮ user logs off The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output ⋮ user logs off shell The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output -

Chapter 1 -Using the Command-Line Interface
CHAPTER 1 Using the Command-Line Interface The command-line interface (CLI) is a line-oriented user interface that provides commands for configuring, managing, and monitoring the Cisco wireless LAN controller. This chapter contains the following topics: • CLI Command Keyboard Shortcuts, page 1-2 • Using the Interactive Help Feature, page 1-3 Cisco Wireless LAN Controller Command Reference OL-19843-02 1-1 Chapter 1 Using the Command-Line Interface CLI Command Keyboard Shortcuts CLI Command Keyboard Shortcuts Table 1-1 lists CLI keyboard shortcuts to help you enter and edit command lines on the controller. Table 1-1 CLI Command Keyboard Shortcuts Action Description Keyboard Shortcut Change The word at the cursor to lowercase. Esc I The word at the cursor to uppercase. Esc u Delete A character to the left of the cursor. Ctrl-h, Delete, or Backspace All characters from the cursor to the beginning of Ctrl-u the line. All characters from the cursor to the end of the line. Ctrl-k All characters from the cursor to the end of the Esc d word. The word to the left of the cursor. Ctrw-w or Esc Backspace Display MORE Exit from MORE output. q, Q, or Ctrl-C output Next additional screen. The default is one screen. Spacebar To display more than one screen, enter a number before pressing the Spacebar key. Next line. The default is one line. To display more Enter than one line, enter the number before pressing the Enter key. Enter an Enter or Return key character. Ctrl-m Expand the command or abbreviation. -

UNIX (Solaris/Linux) Quick Reference Card Logging in Directory Commands at the Login: Prompt, Enter Your Username
UNIX (Solaris/Linux) QUICK REFERENCE CARD Logging In Directory Commands At the Login: prompt, enter your username. At the Password: prompt, enter ls Lists files in current directory your system password. Linux is case-sensitive, so enter upper and lower case ls -l Long listing of files letters as required for your username, password and commands. ls -a List all files, including hidden files ls -lat Long listing of all files sorted by last Exiting or Logging Out modification time. ls wcp List all files matching the wildcard Enter logout and press <Enter> or type <Ctrl>-D. pattern Changing your Password ls dn List files in the directory dn tree List files in tree format Type passwd at the command prompt. Type in your old password, then your new cd dn Change current directory to dn password, then re-enter your new password for verification. If the new password cd pub Changes to subdirectory “pub” is verified, your password will be changed. Many systems age passwords; this cd .. Changes to next higher level directory forces users to change their passwords at predetermined intervals. (previous directory) cd / Changes to the root directory Changing your MS Network Password cd Changes to the users home directory cd /usr/xx Changes to the subdirectory “xx” in the Some servers maintain a second password exclusively for use with Microsoft windows directory “usr” networking, allowing you to mount your home directory as a Network Drive. mkdir dn Makes a new directory named dn Type smbpasswd at the command prompt. Type in your old SMB passwword, rmdir dn Removes the directory dn (the then your new password, then re-enter your new password for verification. -

Create Directory on Windows Without the Fleeting DOS Window Hsiwei Yu (Michael), People Technology Solution Inc, Edison, NJ Gary Huang, Infostat Inc., Belle Mead, NJ
Create Directory on Windows Without the Fleeting DOS Window Hsiwei Yu (Michael), People Technology Solution Inc, Edison, NJ Gary Huang, InfoStat Inc., Belle Mead, NJ copy “source directory” “target directory” ABSTRACT for copying files from source directory to target directory. On newer Windows environments, the pipe feature on a filename statement can be used to create directory without the fleeting Most DOS commands return nothing when successful. Some DOS window. This is better than the X command approach. Any commands, like DIR and COPY, return useful information that DOS commands can be used in the filename pipe feature. Finally can be further analyzed. we will show example of managing directories on remote machine Filename fileref PIPE ‘dir “c:\a dir”’; from local SAS session. Data important_message; Infile fileref length= LNG; Input @; INTRODUCTION /* Put _infile_; */ Sometimes we need to create or delete a directory from within a /* Additional logic to parse the directory SAS session. Previously we can use the X command construct to contents for further analysis. */ issue such create directory (MKDIR) command. However this if LNG >= 8 then do; technique results in an annoying DOS window, flashing and input last_modified_date mmddyy8. @; vanishing on screen. On newer Windows environment and with … the filename pipe feature, we can accomplish the same without end; the extra DOS window. Run; THE FILENAME PIPE FEATURE APPLICATON: MANAGE DIRECTORY ON The filename pipe feature is available is in the Windows environment in both SAS 6.12 -

Homework for Chapter 4 in CIS131
CIS131 Chapter 4 When a question asks for a screenshot, please use the snipping tool ‘clip’ the portion of the screen requested. Do not use full desktop screenshots in your answers. When answering questions that ask for an explanation, your answer must be either a bulleted or numbered list of the exact steps taken to complete the task; do not answer in paragraph form. Assume I will follow the steps you provide to perform that task. Please be sure to label each answer with its respective problem number and make sure you answer ALL questions. You need not include the original questions within your homework document however if you choose to include the questions, make sure you use bold text when typing your answers. Do NOT Disable the Firewall on any machine in your domain. If you are not sure what I’m looking for – please ASK! Complete questions 1 thru 9 at the Server 1. Explain at least three different ways to open control panel. 2. Open Folder Options, pick a setting available on the View tab and provide a thorough explanation of the setting’s purpose. DO NOT choose: Always show menus, Hide Extensions for Known File types, Hide Protected Operating Systems files or Hidden files and folders Your answer must include: a. A screenshot of the folder options view tab with the setting you chose highlighted. b. An explanation of what the setting does when selected and what it does when not selected. If the setting you select changes something visually, include a screenshot of what it looks like when selected and when not selected. -

Understanding and Troubleshooting Ports
UnderStanding and TroubleShooting Ports 1 This document is intended to assist users understand current state of the connection for any Port in the system. How does a system know to which port to address a communication? Many ports are defined by Internet standards as being used for a specific purpose or protocol. The list of ports can be viewed thru’ the below URL http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers Among the different Transport Protocol layers that use ports, users are likely to encounter User Datagram Protocol (UDP) and the Transmission Control Protocol (TCP) very often. There are a total of 65,535 TCP ports and a total of 65,535 different UDP ports. When a user informs that a communication is headed for a particular port (say port 53), then the next question that would usually follow is… if that is TCP port 53 or UDP port 53. For a port to be used to receive a network communication, the port must be associated with some process. The process acts as a listener, waiting for connections to be made requesting some service on its assigned port. In Windows, usually a Service is connected to a specific port (there might be exceptions as well). Using Netstat to analyze and understand Communication thru’ Ports The command “netstat” displays information about the network ports in use on the system. Netstat comes installed on all current releases of Windows systems. Run with no switches, netstat will simply display a list of active connections on the local system. A netstat command with no switches would get you an output similar to the below one (Few digits in IP and few characters in name are masked for security reasons). -
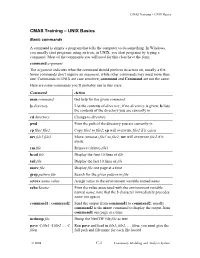
CMAS Training – UNIX Basics
CMAS Training – UNIX Basics CMAS Training – UNIX Basics Basic commands A command is simply a program that tells the computer to do something. In Windows, you usually start programs using an icon; in UNIX, you start programs by typing a command. Most of the commands you will need for this class have the form: command argument The argument indicates what the command should perform its action on, usually a file. Some commands don’t require an argument, while other commands may need more than one. Commands in UNIX are case sensitive; command and Command are not the same. Here are some commands you’ll probably use in this class: Command Action man command Get help for the given command ls directory List the contents of directory; if no directory is given, ls lists the contents of the directory you are currently in cd directory Change to directory pwd Print the path of the directory you are currently in cp file1 file2 Copy file1 to file2; cp will overwrite file2 if it exists mv file1 file2 Move (rename) file1 to file2; mv will overwrite file2 if it exists rm file Remove (delete) file1 head file Display the first 10 lines of file tail file Display the last 10 lines of file more file Display file one page at a time grep pattern file Search for the given pattern in file setenv name value Assign value to the environment variable named name echo $name Print the value associated with the environment variable named name; note that the $ character immediately precedes name (no space) command1 | command2 Send the output from command1 to command2; usually command2 is the more command to display the output from command1 one page at a time ncdump file Dump the NetCDF file file as text pave -f file1 -f file2 … -f Run pave and load in file1, file2, … filen; you must give the filen full path and file name for each file loaded © 2008 C-1 Community Modeling and Analysis System CMAS Training – UNIX Basics Files and directories Files in UNIX are organized into directories, similar to folders in Windows. -

You Can't Do That with Nslookup: a DNS(SEC) Troubleshooting Tutorial
You can’t do that with nslookup: A DNS(SEC) troubleshooting tutorial Michael Sinatra Energy Sciences Network NANOG 53 Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science What this tutorial is about • Learning how to use advanced tools to troubleshoot DNS and DNSSEC issues. • dig • dnscap/nmsg • dnsviz • others • Understanding DNS and DNSSEC pitfalls and where you can get into trouble. • Understanding how DNSSEC complicates the DNS picture. • Learning how basic troubleshooting techniques can help you solve complex problems. Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science What this tutorial is not about • An introduction to DNS. • An introduction to DNSSEC. (See Matt Larson’s excellent DNSSEC tutorial from NANOG 51 or earlier today.) • A commentary on the “complexity” of DNSSEC and why we should throw up our arms and run away (we definitely shouldn’t). • A discussion of DNS and/or DNSSEC implementations, and/or of automation tools for DNSSEC. • I assume a working knowledge of DNS, and also of UNIX, its command line, and how to install and/or compile packages in your favorite modern UNIX variant. Lawrence Berkeley National Laboratory U.S. Department of Energy | Office of Science Why? • You’re here, so you probably have an answer in your head. • In most organizations DNS is a part-time job. • Sometimes it barely works. • Sometimes it doesn’t really work but there’s nobody to fix it. • Even if your organization has a competent DNS person, your users have to get to other people’s resources. • Ever hear the complaint “I can resolve www.foo.com from {home, $ISP, $other_company} but not here.