IBM Security Appscan Source for Analysis: User Guide for OS X Edit Menu
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
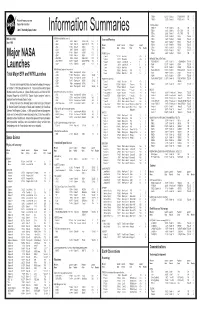
Information Summaries
TIROS 8 12/21/63 Delta-22 TIROS-H (A-53) 17B S National Aeronautics and TIROS 9 1/22/65 Delta-28 TIROS-I (A-54) 17A S Space Administration TIROS Operational 2TIROS 10 7/1/65 Delta-32 OT-1 17B S John F. Kennedy Space Center 2ESSA 1 2/3/66 Delta-36 OT-3 (TOS) 17A S Information Summaries 2 2 ESSA 2 2/28/66 Delta-37 OT-2 (TOS) 17B S 2ESSA 3 10/2/66 2Delta-41 TOS-A 1SLC-2E S PMS 031 (KSC) OSO (Orbiting Solar Observatories) Lunar and Planetary 2ESSA 4 1/26/67 2Delta-45 TOS-B 1SLC-2E S June 1999 OSO 1 3/7/62 Delta-8 OSO-A (S-16) 17A S 2ESSA 5 4/20/67 2Delta-48 TOS-C 1SLC-2E S OSO 2 2/3/65 Delta-29 OSO-B2 (S-17) 17B S Mission Launch Launch Payload Launch 2ESSA 6 11/10/67 2Delta-54 TOS-D 1SLC-2E S OSO 8/25/65 Delta-33 OSO-C 17B U Name Date Vehicle Code Pad Results 2ESSA 7 8/16/68 2Delta-58 TOS-E 1SLC-2E S OSO 3 3/8/67 Delta-46 OSO-E1 17A S 2ESSA 8 12/15/68 2Delta-62 TOS-F 1SLC-2E S OSO 4 10/18/67 Delta-53 OSO-D 17B S PIONEER (Lunar) 2ESSA 9 2/26/69 2Delta-67 TOS-G 17B S OSO 5 1/22/69 Delta-64 OSO-F 17B S Pioneer 1 10/11/58 Thor-Able-1 –– 17A U Major NASA 2 1 OSO 6/PAC 8/9/69 Delta-72 OSO-G/PAC 17A S Pioneer 2 11/8/58 Thor-Able-2 –– 17A U IMPROVED TIROS OPERATIONAL 2 1 OSO 7/TETR 3 9/29/71 Delta-85 OSO-H/TETR-D 17A S Pioneer 3 12/6/58 Juno II AM-11 –– 5 U 3ITOS 1/OSCAR 5 1/23/70 2Delta-76 1TIROS-M/OSCAR 1SLC-2W S 2 OSO 8 6/21/75 Delta-112 OSO-1 17B S Pioneer 4 3/3/59 Juno II AM-14 –– 5 S 3NOAA 1 12/11/70 2Delta-81 ITOS-A 1SLC-2W S Launches Pioneer 11/26/59 Atlas-Able-1 –– 14 U 3ITOS 10/21/71 2Delta-86 ITOS-B 1SLC-2E U OGO (Orbiting Geophysical -

Photographs Written Historical and Descriptive
CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY HAER FL-8-B BUILDING AE HAER FL-8-B (John F. Kennedy Space Center, Hanger AE) Cape Canaveral Brevard County Florida PHOTOGRAPHS WRITTEN HISTORICAL AND DESCRIPTIVE DATA HISTORIC AMERICAN ENGINEERING RECORD SOUTHEAST REGIONAL OFFICE National Park Service U.S. Department of the Interior 100 Alabama St. NW Atlanta, GA 30303 HISTORIC AMERICAN ENGINEERING RECORD CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY BUILDING AE (Hangar AE) HAER NO. FL-8-B Location: Hangar Road, Cape Canaveral Air Force Station (CCAFS), Industrial Area, Brevard County, Florida. USGS Cape Canaveral, Florida, Quadrangle. Universal Transverse Mercator Coordinates: E 540610 N 3151547, Zone 17, NAD 1983. Date of Construction: 1959 Present Owner: National Aeronautics and Space Administration (NASA) Present Use: Home to NASA’s Launch Services Program (LSP) and the Launch Vehicle Data Center (LVDC). The LVDC allows engineers to monitor telemetry data during unmanned rocket launches. Significance: Missile Assembly Building AE, commonly called Hangar AE, is nationally significant as the telemetry station for NASA KSC’s unmanned Expendable Launch Vehicle (ELV) program. Since 1961, the building has been the principal facility for monitoring telemetry communications data during ELV launches and until 1995 it processed scientifically significant ELV satellite payloads. Still in operation, Hangar AE is essential to the continuing mission and success of NASA’s unmanned rocket launch program at KSC. It is eligible for listing on the National Register of Historic Places (NRHP) under Criterion A in the area of Space Exploration as Kennedy Space Center’s (KSC) original Mission Control Center for its program of unmanned launch missions and under Criterion C as a contributing resource in the CCAFS Industrial Area Historic District. -

Juno User Guide
USER GUIDE Juno™ series Juno SB handheld Juno SC handheld NORTH & SOUTH AMERICA EUROPE & AFRICA ASIA-PACIFIC & MIDDLE EAST Trimble Navigation Limited Trimble GmbH Trimble Navigation 10355 Westmoor Drive Am Prime Parc 11 Singapore PTE Limited Suite #100 65479 Raunheim 80 Marine Parade Road Westminster, CO 80021 GERMANY #22-06 Parkway Parade USA Singapore, 449269 SINGAPORE www.trimble.com USER GUIDE Juno™ series Juno SB handheld Juno SC handheld Version 1.00 Revision B October 2008 F Trimble Navigation Limited Trimble; (ii) the operation of the Product under any specification other 10355 Westmoor Drive than, or in addition to, Trimble's standard specifications for its products; Suite #100 (iii) the unauthorized installation, modification, or use of the Product; Westminster, CO 80021 (iv) damage caused by: accident, lightning or other electrical discharge, USA fresh or salt water immersion or spray (outside of Product www.trimble.com specifications); or exposure to environmental conditions for which the Product is not intended; (v) normal wear and tear on consumable parts Legal Notices (e.g., batteries); or (vi) cosmetic damage. Trimble does not warrant or Copyright and Trademarks guarantee the results obtained through the use of the Product or Software, or that software components will operate error free. © 2008, Trimble Navigation Limited. All rights reserved. NOTICE REGARDING PRODUCTS EQUIPPED WITH TECHNOLOGY Trimble, the Globe & Triangle logo, and GPS Pathfinder are trademarks CAPABLE OF TRACKING SATELLITE SIGNALS FROM SATELLITE BASED of Trimble Navigation Limited, registered in the United States and in AUGMENTATION SYSTEMS (SBAS) (WAAS/EGNOS, AND MSAS), other countries. EVEREST, GeoBeacon, GeoXH, GeoXM, GeoXT, GPS OMNISTAR, GPS, MODERNIZED GPS OR GLONASS SATELLITES, OR Analyst, GPScorrect, H-Star, Juno, TerraSync, TrimPix, VRS, and Zephyr FROM IALA BEACON SOURCES: TRIMBLE IS NOT RESPONSIBLE FOR are trademarks of Trimble Navigation Limited. -

Remote and Robotic Investigations of the Solar System
Remote and Robotic Investigations of the Solar System Remote and Robotic Investigations of the Solar System By C. R. Kitchin CRC Press Taylor & Francis Group 6000 Broken Sound Parkway NW, Suite 300 Boca Raton, FL 33487-2742 © 2018 by Taylor & Francis Group, LLC CRC Press is an imprint of Taylor & Francis Group, an Informa business No claim to original U.S. Government works Printed on acid-free paper International Standard Book Number-13: 978-1-4987-0493-9 (Hardback) This book contains information obtained from authentic and highly regarded sources. Reasonable efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders if permission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmitted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers. For permission to photocopy or use material electronically from this work, please access www.copyright.com (http://www. copyright.com/) or contact the Copyright Clearance Center, Inc. (CCC), 222 Rosewood Drive, Danvers, MA 01923, 978-750- 8400. -

<> CRONOLOGIA DE LOS SATÉLITES ARTIFICIALES DE LA
1 SATELITES ARTIFICIALES. Capítulo 5º Subcap. 10 <> CRONOLOGIA DE LOS SATÉLITES ARTIFICIALES DE LA TIERRA. Esta es una relación cronológica de todos los lanzamientos de satélites artificiales de nuestro planeta, con independencia de su éxito o fracaso, tanto en el disparo como en órbita. Significa pues que muchos de ellos no han alcanzado el espacio y fueron destruidos. Se señala en primer lugar (a la izquierda) su nombre, seguido de la fecha del lanzamiento, el país al que pertenece el satélite (que puede ser otro distinto al que lo lanza) y el tipo de satélite; este último aspecto podría no corresponderse en exactitud dado que algunos son de finalidad múltiple. En los lanzamientos múltiples, cada satélite figura separado (salvo en los casos de fracaso, en que no llegan a separarse) pero naturalmente en la misma fecha y juntos. NO ESTÁN incluidos los llevados en vuelos tripulados, si bien se citan en el programa de satélites correspondiente y en el capítulo de “Cronología general de lanzamientos”. .SATÉLITE Fecha País Tipo SPUTNIK F1 15.05.1957 URSS Experimental o tecnológico SPUTNIK F2 21.08.1957 URSS Experimental o tecnológico SPUTNIK 01 04.10.1957 URSS Experimental o tecnológico SPUTNIK 02 03.11.1957 URSS Científico VANGUARD-1A 06.12.1957 USA Experimental o tecnológico EXPLORER 01 31.01.1958 USA Científico VANGUARD-1B 05.02.1958 USA Experimental o tecnológico EXPLORER 02 05.03.1958 USA Científico VANGUARD-1 17.03.1958 USA Experimental o tecnológico EXPLORER 03 26.03.1958 USA Científico SPUTNIK D1 27.04.1958 URSS Geodésico VANGUARD-2A -

Index of Astronomia Nova
Index of Astronomia Nova Index of Astronomia Nova. M. Capderou, Handbook of Satellite Orbits: From Kepler to GPS, 883 DOI 10.1007/978-3-319-03416-4, © Springer International Publishing Switzerland 2014 Bibliography Books are classified in sections according to the main themes covered in this work, and arranged chronologically within each section. General Mechanics and Geodesy 1. H. Goldstein. Classical Mechanics, Addison-Wesley, Cambridge, Mass., 1956 2. L. Landau & E. Lifchitz. Mechanics (Course of Theoretical Physics),Vol.1, Mir, Moscow, 1966, Butterworth–Heinemann 3rd edn., 1976 3. W.M. Kaula. Theory of Satellite Geodesy, Blaisdell Publ., Waltham, Mass., 1966 4. J.-J. Levallois. G´eod´esie g´en´erale, Vols. 1, 2, 3, Eyrolles, Paris, 1969, 1970 5. J.-J. Levallois & J. Kovalevsky. G´eod´esie g´en´erale,Vol.4:G´eod´esie spatiale, Eyrolles, Paris, 1970 6. G. Bomford. Geodesy, 4th edn., Clarendon Press, Oxford, 1980 7. J.-C. Husson, A. Cazenave, J.-F. Minster (Eds.). Internal Geophysics and Space, CNES/Cepadues-Editions, Toulouse, 1985 8. V.I. Arnold. Mathematical Methods of Classical Mechanics, Graduate Texts in Mathematics (60), Springer-Verlag, Berlin, 1989 9. W. Torge. Geodesy, Walter de Gruyter, Berlin, 1991 10. G. Seeber. Satellite Geodesy, Walter de Gruyter, Berlin, 1993 11. E.W. Grafarend, F.W. Krumm, V.S. Schwarze (Eds.). Geodesy: The Challenge of the 3rd Millennium, Springer, Berlin, 2003 12. H. Stephani. Relativity: An Introduction to Special and General Relativity,Cam- bridge University Press, Cambridge, 2004 13. G. Schubert (Ed.). Treatise on Geodephysics,Vol.3:Geodesy, Elsevier, Oxford, 2007 14. D.D. McCarthy, P.K. -

Cosmic Search Issue 13 Page 24
North American AstroPhysical Observatory (NAAPO) Cosmic Search: Issue 13 (Volume 4 Number 1; First half 1982) [Article in magazine started on page 24] ABCs of Space By: John Kraus The Satellite Revolution NASA holds the key to our future more than any other federal agency. What NASA plans now and can subsequently accomplish will determine where the U.S. will be 10, 20, 50 and 100 years from now, not just in space but with respect to our entire economy. • The ultimate goal of astrophysics is to understand the origin and evolution of the universe. When Columbus and other early navigators set out on their voyages of discovery across the oceans, they launched a global diffusion of European culture with an attendant increase in our knowledge of the world and utilization of its resources. Now 500 years later, we have a parallel. Space is a vast ocean and our satellites, probes and astronauts moving out into it can launch a humanization of space with an attendant increase in our knowledge of the universe and utilization of its resources. Sputnik catapulted the world into the Space Age with the first artificial satellite. The earth is now surrounded with thousands of them, like a swarm of bees, most in low orbit circling the Earth in as little as 90 minutes but with others in higher, slower orbits, particularly the Clarke or geostationary orbit where a satellite remains poised above a fixed point on the Earth's equator. When Arthur C. Clarke proposed the geostationary satellite as a solution to the world's communication problems a dozen years before Sputnik, many regarded his idea as visionary and far-fetched. -

Our First Quarter Century of Achievement ... Just the Beginning I
NASA Press Kit National Aeronautics and 251hAnniversary October 1983 Space Administration 1958-1983 >\ Our First Quarter Century of Achievement ... Just the Beginning i RELEASE ND: 83-132 September 1983 NOTE TO EDITORS : NASA is observing its 25th anniversary. The space agency opened for business on Oct. 1, 1958. The information attached sumnarizes what has been achieved in these 25 years. It was prepared as an aid to broadcasters, writers and editors who need historical, statistical and chronological material. Those needing further information may call or write: NASA Headquarters, Code LFD-10, News and Information Branch, Washington, D. C. 20546; 202/755-8370. Photographs to illustrate any of this material may be obtained by calling or writing: NASA Headquarters, Code LFD-10, Photo and Motion Pictures, Washington, D. C. 20546; 202/755-8366. bQy#qt&*&Mary G. itzpatrick Acting Chief, News and Information Branch Public Affairs Division Cover Art Top row, left to right: ffComnandDestruct Center," 1967, Artist Paul Calle, left; ?'View from Mimas," 1981, features on a Saturnian satellite, by Artist Ron Miller, center; ftP1umes,*tSTS- 4 launch, Artist Chet Jezierski,right; aeronautical research mural, Artist Bob McCall, 1977, on display at the Visitors Center at Dryden Flight Research Facility, Edwards, Calif. iii OUR FIRST QUARTER CENTER OF ACHIEVEMENT A-1 -3 SPACE FLIGHT B-1 - 19 SPACE SCIENCE c-1 - 20 SPACE APPLICATIQNS D-1 - 12 AERONAUTICS E-1 - 10 TRACKING AND DATA ACQUISITION F-1 - 5 INTERNATIONAL PROGRAMS G-1 - 5 TECHNOLOGY UTILIZATION H-1 - 5 NASA INSTALLATIONS 1-1 - 9 NASA LAUNCH RECORD J-1 - 49 ASTRONAUTS K-1 - 13 FINE ARTS PRQGRAM L-1 - 7 S IGN I F ICANT QUOTAT IONS frl-1 - 4 NASA ADvIINISTRATORS N-1 - 7 SELECTED NASA PHOTOGRAPHS 0-1 - 12 National Aeronautics and Space Administration Washington, D.C. -

NASA Is Not Archiving All Potentially Valuable Data
‘“L, United States General Acchunting Office \ Report to the Chairman, Committee on Science, Space and Technology, House of Representatives November 1990 SPACE OPERATIONS NASA Is Not Archiving All Potentially Valuable Data GAO/IMTEC-91-3 Information Management and Technology Division B-240427 November 2,199O The Honorable Robert A. Roe Chairman, Committee on Science, Space, and Technology House of Representatives Dear Mr. Chairman: On March 2, 1990, we reported on how well the National Aeronautics and Space Administration (NASA) managed, stored, and archived space science data from past missions. This present report, as agreed with your office, discusses other data management issues, including (1) whether NASA is archiving its most valuable data, and (2) the extent to which a mechanism exists for obtaining input from the scientific community on what types of space science data should be archived. As arranged with your office, unless you publicly announce the contents of this report earlier, we plan no further distribution until 30 days from the date of this letter. We will then give copies to appropriate congressional committees, the Administrator of NASA, and other interested parties upon request. This work was performed under the direction of Samuel W. Howlin, Director for Defense and Security Information Systems, who can be reached at (202) 275-4649. Other major contributors are listed in appendix IX. Sincerely yours, Ralph V. Carlone Assistant Comptroller General Executive Summary The National Aeronautics and Space Administration (NASA) is respon- Purpose sible for space exploration and for managing, archiving, and dissemi- nating space science data. Since 1958, NASA has spent billions on its space science programs and successfully launched over 260 scientific missions. -
NASA Major Launch Record
NASA Major Launch Record 1958 MISSION/ LAUNCH LAUNCH PERIOD CURRENT ORBITAL PARAMETERS WEIGHT REMARKS Intl Design VEHICLE DATE (Mins.) Apogee (km) Perigee (km) Incl (deg) (kg) (All Launches from ESMC, unless otherwise noted) 1958 1958 Pioneer I (U) Thor-Able I Oct 11 DOWN OCT 12, 1958 34.2 Measure magnetic fields around Earth or Moon. Error in burnout Eta I 130 (U) velocity and angle; did not reach Moon. Returned 43 hours of data on extent of radiation band, hydromagnetic oscillations of magnetic field, density of micrometeors in interplanetary space, and interplanetary magnetic field. Beacon I (U) Jupiter C Oct 23 DID NOT ACHIEVE ORBIT 4.2 Thin plastic sphere (12-feet in diameter after inflation) to study (U) atmosphere density at various levels. Upper stages and payload separated prior to first-stage burnout. Pioneer II (U) Thor-Able I Nov 8 DID NOT ACHIEVE ORBIT 39.1 Measurement of magnetic fields around Earth or Moon. Third stage 129 (U) failed to ignite. Its brief data provided evidence that equatorial region about Earth has higher flux and higher energy radiation than previously considered. Pioneer III (U) Juno II (U) Dec 6 DOWN DEC 7, 1958 5.9 Measurement of radiation in space. Error in burnout velocity and angle; did not reach Moon. During its flight, discovered second radiation belt around Earth. 1959 1959 Vanguard II (U) Vanguard Feb 17 122.8 3054 557 32.9 9.4 Sphere (20 inches in diameter) to measure cloud cover. First Earth Alpha 1 (SLV-4) (U) photo from satellite. Interpretation of data difficult because satellite developed precessing motion. -
Introduction to Space Science and Spacecraft Applications
INTRODUCTION TO SPACESCIENCES AND SPACECRAFT APPLICATIONS INTRODUCTION TO SPACESCIENCES AND SPACECRAFT APPLICATIONS BRUCEA. CAMPBELL AND SAMUEL WALTER MCCANDLESS,JR. Gulf Publishing Company Houston, Texas Introduction to Space Sciences and Spacecraft Applications Copyright 0 1996 by Gulf Publishing Company, Houston, Texas. All rights reserved. Printed in the United States of America. This book, or parts thereof, may not be reproduced in any form without permission of the publisher. Gulf Publishing Company Book Division P.O. Box 2608 Houston, Texas 77252-2608 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data Campbell, Bruce A., 1955- Introduction to space sciences and spacecraft applications / Bruce A. Campbell, Samuel Walter McCandless, Jr. p. cm. Includes bibliographical references and index. ISBN 0-88415-411-4 1. Astronautics. 2. Space vehicles. I. McCandless, Samuel Wal- ter. 11. Title. TL791.C36 1996 629.4-dc20 96- 14936 CIP Printed on acid-free paper (=) iv Contents Acknowledgments viii About the Authors viii Preface ix CHAPTER 1 Introduction and History 1 Uses of Space, 1. History of Spaceflight, 3. ReferencedAdditional Reading, 23. Exercises, 23. PART 1 SPACE SCIENCES CHAPTER 2 Orbital Principles 26 Orbital Principles, 28. Orbital Elements, 38. Orbital Properties, 39. Useful Orbits, 44. Orbit Establishment and Orbital Maneuvers, 47. ReferencedAdditional Reading, 5 1. Exercises, 5 1. CHAPTER 3 Propulsion 53 First Principles, 54. Orbit Establishment and Orbital Maneuvers, 63. ReferencedAdditional Reading, 74. Exercises, 74. CHAPTER 4 Spacecraft Environment 76 The Sun, 76. The Earth, 87. Spacecraft Effects, 97. ReferencedAdditional Reading, 101. Exercises, 101. V PART 2 SPACECRAFT APPLICATIONS CHAPTER 5 Communications 104 Communications Theory, 104. -

* a Pocket Statistics
-w mn- * A Pocket Statistics 1996 Edit ion POCKET STATISTICS is published by the NATIONAL AERONAUTICS AND SPACE ADMINISTRATION (NASA). Included in each edition is Administrative and Organizational information, summaries of Space Flight Activity including the NASA Major Launch Record, and NASA Procurement, Financial and Workforce data Foreword The NASA Major Launch Record includes all launches of Scout class and larger vehicles. Vehicle and spacecraft development flights are also included in the Major Launch Record. Shuttle missions are counted as one launch and one payload, where free flying payloads are not involved. Satellites deployed from the cargo bay of the Shuttle and placed in a separate orbit or trajectory are counted as an additional payload. For yearly breakdown of charts shown by decade, refer to the issues of POCKET STATISTICS published prior to 1995. Changes or deletions to this book may be made by phone to Ron Hoffman, (202) 358-1596. NATIONAL AERONAUTICS AND SPACE ADMINISTRATION HEADQUARTERS FACILITIESAND LOGISTICS MANAGEMENT Washington, DC 20546 Contents I Sectlon A - Admlnlstratlon and Organlzatlon Sectlon C - Procurement, Funding and Workforce NASA Organization Contract Awards by State NASA Administrators Distributionof NASA Prime Contract Awards National Aeronautics and Space Act Procurement Activity NASA Installations Contract Awards by Type of Effort The Year in Review Distribution of NASA Procurements Principal Contractors Educational and Nonprofit Institutions Sectlon B Space Flight Actlvlty NASA's Budget Authority in 1994 Dollars - Financial Summary Launch History Mission Support Funding Cunent Worldwide Launch Vehicles R&D Funding by Program Summary of Announced Launches Sci, Aero. &Tech Funding NASA Launches by Vehicle R&D Funding by Location Summary of Announced Payloads Human Space Flight Funding Summary of USA Payloads SpFlt.