Supreme Court of the United States
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Akamai Accelerated Network Program FAQ Akamai Accelerated Network Program Frequently Asked Questions
Akamai Accelerated Network Program FAQ Akamai Accelerated Network Program Frequently Asked Questions Thank you for your interest in the Akamai Accelerated Network What security is there on your boxes? Program. To ensure that you have all your preliminary questions Akamai zealously guards the integrity of our servers. Of course, answered, please review this document. Your Akamai representative we cannot list the steps taken to secure the boxes, but we do have is also available to add more detail or answer additional over 6,000 servers installed in ISPs all over the world, and not one questions that may not be covered. It’s not too late to Accelerate has ever been remotely compromised. Standard security measures Your Network. are taken, such as disabling telnet access, using SSH, turning off daemons not used in production, etc. Server Installation Do you servers work behind a firewall? What do my engineers have to do during the installation? The servers are serving content just as the origin servers – Yahoo!, We ask our partners to simply install the hardware (rack mounted CNN, ESPN, Apple, etc. – would be. The origin servers are not computers and ethernet switches), connect them with the cables behind your firewall, and our servers work best if they are not provided, and finally to assign each computer an IP address and behind your firewall. default gateway. After installation what maintenance and support is Network required? Can we put servers from other content distributors in our The partner is not required to perform any regular maintenance network as well? on Akamai’s equipment. -

Legislators of Cyberspace: an Analysis of the Role Of
SHAPING CODE Jay P. Kesan* & Rajiv C. Shah** I. INTRODUCTION ............................................................................................................................ 4 II. THE CASE STUDIES: THE DEVELOPMENT OF CODE WITHIN INSTITUTIONS.............................. 13 A. World Wide Web......................................................................................................... 14 1. Libwww............................................................................................................ 14 2. NCSA Mosaic .................................................................................................. 16 B. Cookies ........................................................................................................................ 21 1. Netscape’s Cookies .......................................................................................... 21 2. The IETF’s Standard for Cookies .................................................................... 24 C. Platform for Internet Content Selection....................................................................... 28 D. Apache......................................................................................................................... 34 III. LEGISLATIVE BODIES: SOCIETAL INSTITUTIONS THAT DEVELOP CODE ................................. 37 A. Universities.................................................................................................................. 38 B. Firms........................................................................................................................... -

Akamai 2019 State of the Internet / Security Phishing
Akamai Security Research: Cybercriminals Using Enterprise-Based Strategies For Phishing Kit Development And Deployment Oct 30, 2019 09:49 CET Akamai 2019 State of the Internet / Security Phishing Akamai Security Research: Cybercriminals Using Enterprise- Based Strategies For Phishing Kit Development And Deployment Malicious Actors Developing Custom Tools and Processes to Target and Leverage the World’s Largest Tech Brands and Victimize Their Users Cambridge, MA -- October 30, 2019 -- Akamai Technologies, Inc. (NASDAQ: AKAM) today published the Akamai 2019 State of the Internet / Security Phishing: Baiting the Hook report. The research findings indicate that cybercriminals are using enterprise-based development and deployment strategies, such as phishing as a service (PaaS), to leverage some of the world’s largest tech brands, with 42.63% of domains observed targeting Microsoft, PayPal, DHL, and Dropbox. The report details that phishing is no longer just an email-based threat, but has expanded to include social media and mobile devices, creating a wide- reaching problem that touches all industries. This evolving method continues to morph into different techniques, one of which being business email compromise (BEC) attacks. According to the FBI, BEC attacks resulted in worldwide losses of more than $12 billionbetween October 2013 and May 2018. “Phishing is a long-term problem that we expect will have adversaries continuously going after consumers and businesses alike until personalized awareness training programs and layered defense techniques are put in place,” said Martin McKeay, Editorial Director of the State of the Internet/Security report for Akamai. The report shows that cybercriminals are targeting top global brands and their users across various industries through highly-organized and sophisticated phishing kit operations. -

We Need Net Neutrality As Evidenced by This Article to Prevent Corporate
We need Net Neutrality as evidenced by this article to prevent corporate censorship of individual free speech online, whether its AOL censoring DearAOL.com emails protesting their proposed email fee for prioritized email delivery that evades spam filters, AT&T censoring Pearl Jam which this article is about, or Verizon Wireless censoring text messages from NARAL Pro Choice America. If the FCC won't reclassify broadband under Title II the FTC should regulate Net Neutrality, also the DOJ should investigate corporations engaging in such corporate censorship and if they are violating competition laws break them up. Pearl Jam came out in favor of net neutrality after AT&T censored a broadcast a performance they did in Chicago last Sunday. I guess AT&T didn?t like Pearl Jam?s anti-Bush message. I don?t know if Pearl Jam?s sudden embrace of net neutrality is out of ignorance, or if it?s retaliation. It doesn?t really matter because it should help bring some more awareness to the issue. Here?s the issue with net neutrality, in a nutshell. AT&T wants to charge companies like Amazon, eBay, and Google when people like you and me access their web pages. And if the companies don?t pay, AT&T will make the web sites slower. The idea is that if one company doesn?t pay the fees but a competitor does, AT&T customers will probably opt to use the faster services. IT"S WORTH NOTING: Without content, an Internet connection has no value. Proponents say AT&T built the infrastructure, so they have the right to charge whoever uses it. -

WHITE PAPER Encrypted Traffic Management January 2016
FRAUNHOFER INSTITUTE FOR COMMUNICATION, INFORMATION PROCESSIN G AND ERGONOMICS FKI E WHITE PAPER ENCRYPTED TRAFFIC MANAGEMENT WHITE PAPER Encrypted Traffic Management January 2016 Raphael Ernst Martin Lambertz Fraunhofer Institute for Communication, Information Processing and Ergonomics FKIE in Wachtberg and Bonn. Project number: 108146 Project partner: Blue Coat Systems Inc. Fraunhofer FKIE White paper Encrypted Traffic Management 3 | 33 Contents 1 Introduction .......................................................................................... 5 2 The spread of SSL ................................................................................. 6 3 Safety issues in previous versions of SSL ............................................... 8 4 Malware and SSL ................................................................................... 9 5 Encrypted Traffic Management .............................................................. 11 5.1 Privacy ...................................................................................................................... 12 5.1.1 Requirements ............................................................................................................ 12 5.2 Compatibility ............................................................................................................ 12 5.2.1 Requirements ............................................................................................................ 12 5.3 Performance ............................................................................................................ -

Brief for Plaintiff-Appellant Akamai Technologies, Inc
I]1111IIIIIIIIIIIIIJllJIfllIIIJJIIIttIHJillIJllllIJlllIlJJJFIIflMMIIJillIlJJIIIJ USFC2009-1372-10 {466256B 1-3FB1-4D3A-A6D4-9850D2 B04CA5 } {117249}{54-110705:110649}{062011} APPELLANT'S BRIEF 2009-1372,-1380,-1416,-1417 IN THE UNITED STATES COURT OF APPEALS FOR THE FEDERAL CIRCUIT AKAMAI TECHNOLOGIES, INC., Plaintiff-Appellant, and THE MASSACHUSETTS INSTITUTE OF TECHNOLOGY, Plaintiff-Appellant, V° LIMELIGHT NETWORKS, INC., Defendant-Cross Appellant. App_l's_from"_" __ the United States District Court for the District of Massachusetts in case nos. 06-CV-11109 and 06-CV-11585, Judge Rya W. Zobel. PRINCIPAL BRIEF FOR PLAINTIFF-APPELLANT AKAMAI TECHNOLOGIES, INC. ON REHEARING EN BANC Of Counsel: DONALD R. DUNNER KARA F. STOLL ROBERT S, FRANK, JR, FINNEGAN, HENDERSON, FARABOW, CHOATE, HALL&STEWARTLLP GARRETT & DUNNER, LLP Two lntem_ionalPlace 901 New York Avenue, NW Boston, MA02110 Washington, DC 20001-4413 (202) 408-4000 Attorney for Plaintiff-Appellant The Massachusetts Institute of Technology JENNIFER S. SWAN F1NNEGAN, HENDERSON, FARABOW, GARRETr & DUNNER, LLP 3300 Hillview Avenue Palo Alto, CA 94304-1203 (650) 849-6676 Attorneys for Plaintiff-Appellant June 20, 2011 Akamai Technologies, Inc. CERTIFICATE OF INTEREST Counsel for Akamai Technologies, Inc. certifies the following: 1. The full name of every party or amicus represented by Counsel is: Akamai Technologies, Inc. 2. The name of the real party in interest represented by me is: None ° All parent corporations and any publicly held companies that own 10 percent or more of the stock of the party represented by me are: None o The names of all law finns and the partners or associates that appeared for the party or amicus now represented by me in the trial court or agency or are expected to appear in this Court are: Donald R. -

Download Gtx 970 Driver Download Gtx 970 Driver
download gtx 970 driver Download gtx 970 driver. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67a229f54fd4c3c5 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. GeForce Windows 10 Driver. NVIDIA has been working closely with Microsoft on the development of Windows 10 and DirectX 12. Coinciding with the arrival of Windows 10, this Game Ready driver includes the latest tweaks, bug fixes, and optimizations to ensure you have the best possible gaming experience. Game Ready Best gaming experience for Windows 10. GeForce GTX TITAN X, GeForce GTX TITAN, GeForce GTX TITAN Black, GeForce GTX TITAN Z. GeForce 900 Series: GeForce GTX 980 Ti, GeForce GTX 980, GeForce GTX 970, GeForce GTX 960. GeForce 700 Series: GeForce GTX 780 Ti, GeForce GTX 780, GeForce GTX 770, GeForce GTX 760, GeForce GTX 760 Ti (OEM), GeForce GTX 750 Ti, GeForce GTX 750, GeForce GTX 745, GeForce GT 740, GeForce GT 730, GeForce GT 720, GeForce GT 710, GeForce GT 705. -

Untangling a Worldwide Web Ebay and Paypal Were Deeply Integrated
CONTENTS EXECUTIVE MESSAGE PERFORMANCE Untangling a worldwide web eBay and PayPal were deeply integrated; separating them required a global effort CLIENTS Embracing analytics Securing patient data eBay’s separation bid It was a match made in e-heaven. In 2002, more than 70 During the engagement, more than 200 Deloitte Reducing IT risk percent of sellers on eBay, the e-commerce giant, accepted professionals helped the client: Audits that add value PayPal, the e-payment system of choice. So, for eBay, the • Separate more than 10,000 contracts. Raising the audit bar US$1.5 billion acquisition of PayPal made perfect sense. Not • Build a new cloud infrastructure to host 7,000 Blockchain link-up only could the online retailer collect a commission on every virtual servers and a new enterprise data Trade app cuts costs item sold, but it also could earn a fee from each PayPal warehouse, one of the largest in the world. Taking on corruption transaction. • Prepare more than 14,000 servers to support the split of more than 900 applications. TALENT Over time, however, new competitors emerged and • Migrate more than 18,000 employee user profiles new opportunities presented themselves, leading eBay and 27,000 email accounts to the new PayPal SOCIETY management to realize that divesting PayPal would allow environment. both companies to capitalize on their respective growth • Relocate 4,500-plus employees from 47 offices. “This particular REPORTING opportunities in the rapidly changing global commerce and • Launch a new corporate network for PayPal by engagement was payments landscape. So, in September 2014, eBay’s board integrating 13 hubs and 83 office locations. -

Research Articles in the American Economic Review, the RAND Journal Ofeconomics, The
3 I. Introduction And Qualifications 1. My name is Nicholas S. Economides. I am a Professor ofEconomics at the Stern School ofBusiness ofNew York University, located at 44 West 4th Street New York, NY 10012. 2. I received a B.Sc. degree in Mathematical Economics (first class honors) from the London School ofEconomics in 1976, a Masters degree in Economics from the University of California at Berkeley in 1979 and a Ph.D. degree in Economics from Berkeley in 1981, specializing in Industrial Organization. 3. From 1981 to 1988, I was assistant and then associate professor ofeconomics at Columbia University. From 1988 to 1990, I was associate professor ofeconomics at Stanford University. I have taught at the Stern School ofBusiness since 1990. During the academic year 1996-1997, I was visiting professor at Stanford University. 4. I have published more than seventy research papers in the areas ofindustrial organization, microeconomics, network economics, antitrust, finance, and telecommunications policy, and I have given numerous seminar presentations at academic and government institutions and conferences. I have published academic research articles in the American Economic Review, the RAND Journal ofEconomics, the International Journal ofIndustrial Organization, the International Economic Review, the Journal ofEconomic Theory, and the Journal ofIndustrial Economics, among others. I am currently editor ofthe International Journal ofIndustrial Organization and ofNetnomics. I have served as advisor and consultant to major telecommunications companies, a number of 4 the Federal Reserve Banks, the Bank ofGreece, and major Financial Exchanges. I teach graduate (MBA and Ph.D.) courses in antitrust, industrial organization, microeconomics, and telecommunications. A copy ofmy curriculum vitae is attached as Attachment 1. -

AKAMAI TECHNOLOGIES, INC. (Name of Registrant As Specified in Its Charter) Payment of Filing Fee (Check the Appropriate Box)
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, DC 20549 SCHEDULE 14A (Rule 14a-101) INFORMATION REQUIRED IN PROXY STATEMENT SCHEDULE 14A INFORMATION Proxy Statement Pursuant to Section 14(a) of the Securities Exchange Act of 1934 Filed by the Registrant ☒ Filed by a Party other than the Registrant ☐ Check the appropriate box: ☐ Preliminary Proxy Statement ☐ Confidential, For Use of the Commission Only (as permitted by Rule 14a-6(e)(2)) ☒ Definitive Proxy Statement ☐ Definitive Additional Materials ☐ Soliciting Material Pursuant to Section 240.14a-12 AKAMAI TECHNOLOGIES, INC. (Name of Registrant as Specified In Its Charter) Payment of Filing Fee (Check the appropriate box): ☒ No fee required. ☐ Fee computed on table below per Exchange Act Rules 14a-6(i)(1) and 0-11. 1 Title of each class of securities to which transaction applies: 2 Aggregate number of securities to which transaction applies: 3 Per unit price or other underlying value of transaction computed pursuant to Exchange Act Rule 0-11 (set forth the amount on which the filing fee is calculated and state how it was determined): 4 Proposed maximum aggregate value of transaction: 5 Total fee paid: ☐ Fee paid previously with preliminary materials: ☐ Check box if any part of the fee is offset as provided by Exchange Act Rule 0-11(a)(2) and identify the filing for which the offsetting fee was paid previously. Identify the previous filing by registration statement number, or the Form or Schedule and the date of its filing. 1 Amount previously paid: 2 Form, Schedule or Registration Statement No.: 3 Filing party: 4 Date Filed: Table of Contents Dear Fellow Stockholders: Since our founding in 1998, Akamai has developed unique technology and an unmatched global infrastructure—the Akamai Intelligent Platform. -

Apache Spot: a More Effective Approach to Cyber Security
SOLUTION BRIEF Data Center: Big Data and Analytics Security Apache Spot: A More Effective Approach to Cyber Security Apache Spot uses machine learning over billions of network events to discover and speed remediation of attacks to minutes instead of months—streamlining resources and cutting risk exposure Executive Summary This solution brief describes how to solve business challenges No industry is immune to cybercrime. The global “hard” cost of cybercrime has and enable digital transformation climbed to USD 450 billion annually; the median cost of a cyberattack has grown by through investment in innovative approximately 200 percent over the last five years,1 and the reputational damage can technologies. be even greater. Intel is collaborating with cyber security industry leaders such as If you are responsible for … Accenture, eBay, Cloudwick, Dell, HP, Cloudera, McAfee, and many others to develop • Business strategy: You will better big data solutions with advanced machine learning to transform how security threats understand how a cyber security are discovered, analyzed, and corrected. solution will enable you to meet your business outcomes. Apache Spot is a powerful data aggregation tool that departs from deterministic, • Technology decisions: You will learn signature-based threat detection methods by collecting disparate data sources into a how a cyber security solution works data lake where self-learning algorithms use pattern matching from machine learning to deliver IT and business value. and streaming analytics to find patterns of outlier network behavior. Companies use Apache Spot to analyze billions of events per day—an order of magnitude greater than legacy security information and event management (SIEM) systems. -
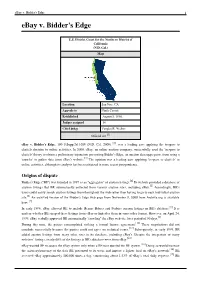
Ebay V.Bidder's Edge
eBay v. Bidder's Edge 1 eBay v. Bidder's Edge U.S. District Court for the Northern District of California (N.D. Cal.) Map Location San Jose, CA Appeals to Ninth Circuit Established August 5, 1886. Judges assigned 14 Chief judge Vaughn R. Walker [1] Official site eBay v. Bidder's Edge, 100 F.Supp.2d 1058 (N.D. Cal. 2000) [2], was a leading case applying the trespass to chattels doctrine to online activities. In 2000, eBay, an online auction company, successfully used the 'trespass to chattels' theory to obtain a preliminary injunction preventing Bidder’s Edge, an auction data aggregator, from using a 'crawler' to gather data from eBay’s website.[3] The opinion was a leading case applying 'trespass to chattels' to online activities, although its analysis has been criticized in more recent jurisprudence. Origins of dispute Bidder’s Edge (“BE”) was founded in 1997 as an “aggregator” of auction listings.[4] Its website provided a database of auction listings that BE automatically collected from various auction sites, including eBay.[5] Accordingly, BE’s users could easily search auction listings from throughout the web rather than having to go to each individual auction site.[6] An archived version of the Bidder’s Edge web page from November 9, 2000 from Archive.org is available here. [7]. In early 1998, eBay allowed BE to include Beanie Babies and Furbies auction listings in BE’s database.[8] It is unclear whether BE scraped these listings from eBay or linked to them in some other format. However, on April 24, 1999, eBay verbally approved BE automatically “crawling” the eBay web site for a period of 90 days.[9] During this time, the parties contemplated striking a formal license agreement.[10] These negotiations did not conclude successfully because the parties could not agree on technical issues.[11] Subsequently, in early 1999, BE added auction listings from many other sites in its database, including eBay’s.