Windows Login Screen Bypass LTAT.06.002 A Ndmeturve
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Managing Debounce When a Switch Or Key Is Pressed, Noise Is Created Along with Its Intended Signal That Can Be Processed As Multiple Entries
Managing Debounce When a switch or key is pressed, noise is created along with its intended signal that can be processed as multiple entries. It is important to manage this noise to prevent undesired repeated keyboard strokes, or, in the case of your AT-104, multiple page turns. MusicReader and Power Music software features built-in debounce control. The default in MusicReader is set at 300 milliseconds. This setting will be sufficient for most switches. However, if you are experiencing difficulty with multiple page turns, access the settings menu by clicking on the More button located at the top of the screen. Select the wrench icon , and then choose the Interface and Controls tab. The drop down menu on the ride side of the screen under the heading Page Turn Block allows adjustment of the timing. This amount may be increased to reduce the likelihood of multiple page turns if experiencing an issue. See Power Music documentation for more information on managing settings. For other software, debounce can be controlled by Windows XP/Vista/7 by altering the keyboard settings. For Windows 10 Users Enter the Control Panel and select the Ease of Access. Choose the Ease of Access Center. Scroll down and select Make the Keyboard Easier to Use. Check the box next to Turn On Filters. 1 Select Set Up Filters, then select Turn On Bounce Keys. Verify the wait time is set to 0.5 seconds. Click the Apply button at the bottom of the window to save the settings. For Windows Vista or 7 Users Enter the Control Panel and select the Ease of Access Center. -

User Account Control - Wikipedia
12/31/2020 User Account Control - Wikipedia User Account Control User Account Control (UAC) is a mandatory access control enforcement facility introduced with Microsoft's Windows Vista[1] and Windows Server 2008 operating systems, with a more relaxed[2] version also present in Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012 and Windows 10. It aims to improve the security of Microsoft Windows by limiting application software to standard user privileges until an administrator authorizes an increase or elevation. In this way, only applications trusted by the user may receive administrative privileges, and malware should be kept from compromising the operating system. In other words, a user account may have administrator privileges assigned to it, but applications that the user runs do not User Account Control "Windows Security" alerts inherit those privileges unless they are approved in Windows 10 in light mode. From top to bottom: beforehand or the user explicitly authorizes it. blocked app, app with unknown publisher, app with a known/trusted publisher. UAC uses Mandatory Integrity Control to isolate running processes with different privileges. To reduce the possibility of lower-privilege applications communicating with higher-privilege ones, another new technology, User Interface Privilege Isolation, is used in conjunction with User Account Control to isolate these processes from each other.[3] One prominent use of this is Internet Explorer 7's "Protected Mode".[4] Contents History Tasks that trigger a UAC prompt Features Requesting elevation Security Criticism See also References External links History https://en.wikipedia.org/wiki/User_Account_Control#Security 1/9 12/31/2020 User Account Control - Wikipedia Operating systems on mainframes and on servers have differentiated between superusers and userland for decades. -
Accessibility Features in Windows 7
Accessibility features in Windows 7 Introduction Windows offers several programs and settings that can make the computer easier to see, hear, and use.You can adjust accessibility settings and programs from within the Ease of Access Centerwhich is location in the Control Panel. To open the Ease of Access Center: Click on the Start button , click Control Panel, click Ease of Access, and then click Ease of Access Center. Examples All the settings below can be adjusted from the Ease of Access Centre. For example, you can have screen text read aloud by using Narrator, or you can have Windows describe screen activity to you. Make the computer easier to see If you occasionally have trouble seeing items on your screen, you can adjust the settings to make text and images on the screen appear larger, improve the contrast between items on the screen • Choose a High Contrast theme • Change the size of text and icons • Turn on Magnifier • Adjust the colour and transparency of window borders National Assistive Technology Training Service Advice and Information: tel: 01 8714000 email: [email protected] web: www.enableireland.ie Enable Ireland Information Sheet Windows Accessibility Features • Make the focus rectangle thicker • Set the thickness of the blinking cursor • Remove background images Use the computer without the mouse or keyboard • Use On-Screen Keyboard • Use Speech Recognition Make the mouse easier to use • Change the colour and size of the mouse pointer • Turn on Mouse Keys • Activate a window by hovering over it with the mouse Make -
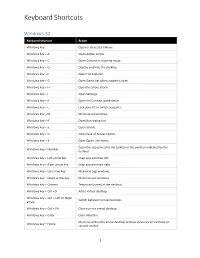
Keyboard Shortcuts
Keyboard Shortcuts Windows 10 Keyboard shortcut Action Windows key Open or close Start Menu. Windows key + A Open Action center. Windows key + C Open Cortana in listening mode. Windows key + D Display and hide the desktop. Windows key + E Open File Explorer. Windows key + G Open Game bar when a game is open. Windows key + H Open the Share charm. Windows key + I Open Settings. Windows key + K Open the Connect quick action. Windows key + L Lock your PC or switch accounts. Windows key + M Minimize all windows. Windows key + R Open Run dialog box. Windows key + S Open Search. Windows key + U Open Ease of Access Center. Windows key + X Open Quick Link menu. Open the app pinned to the taskbar in the position indicated by the Windows key + Number number. Windows key + Left arrow key Snap app windows left. Windows key + Right arrow key Snap app windows right. Windows key + Up arrow key Maximize app windows. Windows key + Down arrow key Minimize app windows. Windows key + Comma Temporarily peek at the desktop. Windows key + Ctrl +D Add a virtual desktop. Windows key + Ctrl + Left or Right Switch between virtual desktops. arrow Windows key + Ctrl + F4 Close current virtual desktop. Windows key + Enter Open Narrator. Minimize all but the active desktop window (restores all windows on Windows key + Home second stroke). 1 Keyboard Shortcuts Keyboard shortcut Action Windows key + PrtScn Capture a screenshot and save in Screenshots folder. Windows key + Shift + Up arrow Stretch the desktop window to the top and bottom of the screen. Windows key + Tab Open Task view. -

Managing the Windows 7 Desktop Environment
Chapter 5 Managing the Windows 7 Desktop Environment INFORMATION IN THIS CHAPTER ■ Local Management Tools ■ Managing Hardware Devices and Drivers ■ Managing Disks and File Systems ■ Summary Windows 7 comes with a variety of tools for managing your system. There are tools for managing the local system, managing hardware and devices, and managing disks and file systems. Some of these tools are new, and some have been around for a while. Windows 7 can be a quite complex operating system. So you need to make sure that you understand all the tools that have been created to make the job of managing systems easier. LOCAL MANAGEMENT TOOLS Windows 7 includes many management tools to help manage your system. We will review a few of the most commonly used ones. These are as follows: ■ Control Panel ■ Microsoft Management Console 3.0 ■ Computer Management Console ■ Local Group Policy Editor ■ Windows Registry Each of these management tools serves a different purpose and provides dif- ferent functionality. It’s important that you have a good understanding of all these tools in order to properly manage your system. © 2010 Elsevier Inc. All rights reserved. DOI: 10.1016/B978-1-59749-561-5.00005-X 305 306 CHAPTER 5 Managing the Windows 7 Desktop Environment Control Panel The Control Panel has long been a central place to go to configure your Win- dows system. The look has changed over the years, but tools have stayed pretty similar, with a few additions. The Windows 7 Control Panel is broken down into several categories and subcategories. Control Panel is accessed from the Start menu. -

Windows 10 Step by Step
spine = .8739” The quick way to learn Windows 10 Step by Windows 10 This is learning made easy. Get more done quickly Step with Windows 10. Jump in wherever you need answers—brisk lessons and colorful screenshots IN FULL COLOR! show you exactly what to do, step by step. Windows 10 • Discover fun and functional Windows 10 features! • Work with the new, improved Start menu and Start screen • Learn about different sign-in methods • Put the Cortana personal assistant to work for you • Manage your online reading list and annotate articles with the new browser, Microsoft Edge • Help safeguard your computer, your information, and your privacy • Manage connections to networks, devices, and storage resources Step Colorful screenshots by Step Download your Step by Step practice files at: Helpful tips and http://aka.ms/Windows10SBS/files pointers Lambert Lambert Easy numbered steps MicrosoftPressStore.com ISBN 978-0-7356-9795-9 U.S.A. $29.99 29999 Canada $36.99 [Recommended] Joan Lambert 9 780735 697959 Windows/Windows 10 Steve Lambert PRACTICE FILES Celebrating over 30 years! 9780735697959_Win10_SBS.indd 1 9/24/2015 7:29:34 AM Windows 10 Step by Step Joan Lambert Steve Lambert Win10SBS.indb 1 10/5/2015 6:33:24 PM PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2015 by Joan Lambert All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2014952811 ISBN: 978-0-7356-9795-9 Printed and bound in the United States of America. -

Accessibility in Windows 8
Accessibility in Windows 8 Overview of accessibility in Windows 8, tutorials, and keyboard shortcuts Published by Microsoft Corporation, Trustworthy Computing One Microsoft Way Redmond, Washington 98052 Copyright 2012 Microsoft Corporation. All rights reserved. No part of the contents of this document may be reproduced or transmitted in any form or by any means without the written permission of the publisher. For permissions, visit www.microsoft.com. Microsoft and Windows are trademarks of Microsoft Corporation in the United States and/or other countries. Find further information on Microsoft Trademarks (http://www.microsoft.com/about/legal/en/us/IntellectualProperty/Trademarks/EN-US.aspx). Table of Contents Overview of Accessibility in Windows 8 .................................................................................................. 7 What’s new in Windows 8 accessibility ...................................................................................................................................7 Narrator and touch-enabled devices .................................................................................................................................................. 7 Magnifier and touch-enabled devices ............................................................................................................................................... 9 Ease of Access .............................................................................................................................................. 12 Make -

Accessibility in Windows 7
Accessibility in Windows 7 Windows 7 includes accessibility options and programs that make it easier to see, hear, and use your computer including ways to personalize your PC. Windows 7 includes significant accessibility improvements. Magnifier now includes a lens mode and full-screen mode. On-Screen Keyboard can be resized to make it easier to see and includes text prediction. Windows 7 also gives you more ways to interact with your PC by taking advantage of new strides in speech recognition and touch technology. Ease of Access Center Speech Recognition Provides a centralized location in Command your PC with your the Control Panel where you can voice including the capability to adjust accessibility settings and dictate into most applications. programs. Get recommendations Dictate documents and e-mail and for settings to make your PC easier surf the Web by saying what you to see, hear, and use. see. An easy setup process and an interactive tutorial are available On-Screen Keyboard to familiarize you with the Displays a visual keyboard with speech commands and train all the standard keys. Instead of your computer to better relying on the physical keyboard to understand you. type and enter data, use On-Screen Keyboard to select keys using the Change text size mouse or another pointing device. Make text and icons larger and On-Screen Keyboard can now be easier to see without changing the resized and customized to make screen resolution. it easier to see and use. When text prediction is enabled, a list Personalization of words you might be typing Add a personal touch to your is displayed. -

Windows 7 Accessibility Guide
7 © CALL Scotland 2011: Ease of Access Guide for Windows 7 Contents Windows 7 Ease of Access Centre: Overview ...................................................... 3 High Contrast .......................................................................................... 7 Magnifier ............................................................................................... 9 Narrator ............................................................................................... 12 Change background colours and font styles and sizes .......................................... 14 Voice Recognition .................................................................................... 20 On-Screen Keyboard ................................................................................. 23 Mouse Keys ............................................................................................ 26 Call Scotland .......................................................................................... 28 2 © CALL Scotland 2011: Ease of Access Guide for Windows 7 Windows 7 Ease of Access Centre Overview Microsoft has included a range of accessibility features (Accessibility Options) in its operating systems since Windows 95. Windows 7 incorporates several improvements such as a change of name from ‘Accessibility Options’ to ‘Ease of Access Centre’. These features provide a valuable but often overlooked method of supporting learners with additional support needs. The Ease of Access Centre, found in the Control Panel, brings together all the accessibility -

Hearing Text Read Aloud with Narrator
Making your computer easier to use A guide on how to use the Ease of Access Centre written using Windows 7 Specialist Teaching and Preschool Service An Overview The Ease of Access Centre is a central location where you can modify the accessibility settings and programs available in Windows. You can adjust settings that make it easier to see your computer, use the mouse and keyboard, and use other input devices. You can also answer a few questions about your daily computer use that will help Windows recommend accessibility settings and programs for you. 1 Specialist Teaching and Preschool Service Opening the Ease of Access Centre Shortcut: to open the Ease of Access Centre press: Windows logo key + U Step 1: click the Start button on the bottom left corner of the screen Step 2: from the menu on the right select Control Panel 2 Specialist Teaching and Preschool Service Opening the Ease of Access Centre Shortcut: to open the Ease of Access Centre press: Windows logo key + U Step 3: click Ease of Access, located bottom right of the available options Step 4: from the following screen select the Ease of Access Center. The main Ease of Access menu will now open Specialist Teaching and Preschool Service 3 Ease of Access Centre: Main Menu Below shows the main Ease of Access menu screen. We shall cover each available option over the following pages Specialist Teaching and Preschool Service 4 Ease of Access Centre: The Accessibility Options Note: Windows can make recommendations to help you decide which accessibility options are best suited. -
Guide for People Who Have Low Mobility Or Dexterity
Guide for People who have Low Mobility or Dexterity This guide describes accessibility features built into Windows and Microsoft Office, as well as different types of assistive technology products that are designed for individuals who have low mobility or dexterity. Note that some sections of this guide may be useful to individuals with different types of disabilities like learning or vision. Microsoft wants to provide the best possible experience for all our customers. If you have a disability or have questions related to accessibility, please contact the Microsoft Disability Answer Desk for technical assistance. The Disability Answer Desk support team is trained in using many popular assistive technologies and can offer assistance in English, Spanish, French, and American Sign Language. Please go to the Microsoft Disability Answer Desk site to find out the contact details for your region. If you are a government, commercial, or enterprise user, please contact the Enterprise Disability Answer Desk. At Microsoft, our mission is to empower every person and organization on the planet to achieve more. We are committed to delivering great experiences to people with disabilities. If you have feedback to offer, or requests to make of us, we encourage you to let us know through the Microsoft Accessibility Forum. In this Guide: Setup Accessibility Options in Windows Make Accessible Documents with Office Use Accessibility Features in Office Browse the Accessibility Features of Internet Explorer and Edge Assistive Technology for People with Low Mobility or Dexterity Setup Accessibility Options in Windows Ease of Access is a location where you can set up accessibility settings and programs available in Windows. -
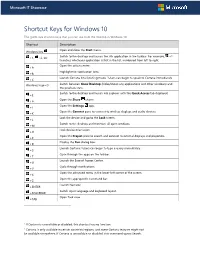
Shortcut Keys for Windows 10
Microsoft IT Showcase Shortcut Keys for Windows 10 This guide lists shortcut keys that you can use from the desktop in Windows 10. Shortcut Description Open and close the Start menu. Windows key Switch to the desktop and launch the nth application in the taskbar. For example, +1 +1, +2, etc. launches whichever application is first in the list, numbered from left to right. Open the action center. +A Highlight the notification area. +B Launch Cortana into listening mode.1 Users can begin to speak to Cortana immediately. +C Windows logo+D Switch between Show Desktop (hides/shows any applications and other windows) and the previous state. Switch to the desktop and launch File Explorer with the Quick Access tab displayed. +E Open the Share charm. +H Open the Settings app. +I Open the Connect pane to connect to wireless displays and audio devices. +K Lock the device and go to the Lock screen. +L Switch to the desktop and minimize all open windows. +M Lock device orientation. +O Open the Project pane to search and connect to external displays and projectors. +P Display the Run dialog box. +R Launch Cortana.2 Users can begin to type a query immediately. +S Cycle through the apps on the taskbar. +T Launch the Ease of Access Center. +U Cycle through notifications. +V Open the advanced menu in the lower-left corner of the screen. +X Open the app-specific command bar. +Z Launch Narrator. +ENTER Switch input language and keyboard layout. +SPACEBAR Open Task view. +TAB 1 If Cortana is unavailable or disabled, this shortcut has no function.