Controlling Windows 10 Settings by Tom Krauser
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bitlocker Encryption for USB Drives Bitlocker Is a Security Feature. the Purpose of Bitlocker Is to Encrypt Your Data
BitLocker Encryption for USB Drives BitLocker is a security feature. The purpose of BitLocker is to encrypt your data. This is extremely necessary for any data that is not to be shared with other persons. This will prevent anyone from being able to access your files. In order to have access to your files, you will need to provide a secure password. This password should be unique only to you. More information is provided below on how to make a unique password in step 2. During this process, step 3 offers the option to save a recovery key. The recovery key is 48 characters long and consist of numbers and letters. This key will be saved to Active Directory and allow the IS Department to access your USB/External drive should you forget your password. To get started I would recommend encrypting the USB/External drive BEFORE adding any files. Once the drive is encrypted and you enter your password it will function as any other USB/External drive. So you may add, edit, or delete your files as you normally would. If you have any trouble following this guide or have any questions please do not hesitate to contact the IS department. You will need a USB or External drive in order to successfully complete this process. Multiple ways to navigate to BitLocker: 1. Control Panel System & Security BitLocker Drive Encryption 2. Search bar type in “BitLocker” Manage BitLocker Steps to encrypt your USB drive: Step 1: Click “Turn on BitLocker” Step 2: Check the “Use a password to unlock the drive” and enter your password. -
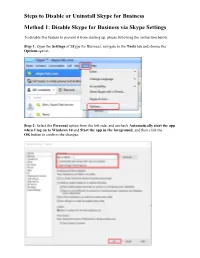
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

The Downadup Codex a Comprehensive Guide to the Threat’S Mechanics
Security Response The Downadup Codex A comprehensive guide to the threat’s mechanics. Edition 2.0 Introduction Contents Introduction.............................................................1 Since its appearance in late-2008, the Downadup worm has become Editor’s Note............................................................5 one of the most wide-spread threats to hit the Internet for a number of Increase in exploit attempts against MS08-067.....6 years. A complex piece of malicious code, this threat was able to jump W32.Downadup infection statistics.........................8 certain network hurdles, hide in the shadows of network traffic, and New variants of W32.Downadup.B find new ways to propagate.........................................10 defend itself against attack with a deftness not often seen in today’s W32.Downadup and W32.Downadup.B threat landscape. Yet it contained few previously unseen features. What statistics................................................................12 set it apart was the sheer number of tricks it held up its sleeve. Peer-to-peer payload distribution...........................15 Geo-location, fingerprinting, and piracy...............17 It all started in late-October of 2008, we began to receive reports of A lock with no key..................................................19 Small improvements yield big returns..................21 targeted attacks taking advantage of an as-yet unknown vulnerability Attempts at smart network scanning...................23 in Window’s remote procedure call (RPC) service. Microsoft quickly Playing with Universal Plug and Play...................24 released an out-of-band security patch (MS08-067), going so far as to Locking itself out.................................................27 classify the update as “critical” for some operating systems—the high- A new Downadup variant?......................................29 Advanced crypto protection.................................30 est designation for a Microsoft Security Bulletin. -

Journey Through the Impact of the Recovery Artifacts in Windows 8 WENDELL Kenneth JOHNSON Iowa State University
Iowa State University Capstones, Theses and Graduate Theses and Dissertations Dissertations 2013 Journey through the impact of the recovery artifacts in Windows 8 WENDELL Kenneth JOHNSON Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/etd Part of the Databases and Information Systems Commons Recommended Citation JOHNSON, WENDELL Kenneth, "Journey through the impact of the recovery artifacts in Windows 8" (2013). Graduate Theses and Dissertations. 13414. https://lib.dr.iastate.edu/etd/13414 This Thesis is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Journey through the impact of the recovery artifacts in Windows 8 by Wendell Kenneth Johnson A thesis submitted to the graduate faculty in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE Co-majors: Computer Engineering; Information Assurance Program of Study Committee: Yong Guan, Major Professor Doug Jacobson Jennifer L. Davidson Iowa State University Ames, Iowa 2013 Copyright © Wendell Kenneth Johnson, 2013. All rights reserved. ii DEDICATION This Thesis is dedicated to my family Jessica, Savannah and Brady. Without your unrelenting support and sacrifices I would not have been able to follow my educational and career dreams. To Lee Adams, while you will never see the finished work, your guiding light and compassion shown to me helped create the person I am today. My drive to succeed and to share my success comes from watching you give so much of your compassion to others. -
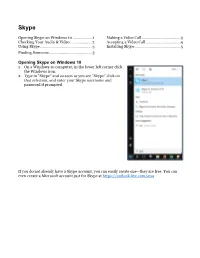
Opening Skype on Windows 10
Skype Opening Skype on Windows 10 ................... 1 Making a Video Call ..................................... 3 Checking Your Audio & Video .................... 2 Accepting a Video Call .................................4 Using Skype ................................................. 3 Installing Skype ........................................... 5 Finding Someone ........................................ 3 Opening Skype on Windows 10 1. On a Windows 10 computer, in the lower left corner click the Windows icon. 2. Type in “Skype” and as soon as you see “Skype” click on that selection, and enter your Skype username and password if prompted. If you do not already have a Skype account, you can easily create one—they are free. You can even create a Microsoft account just for Skype at https://outlook.live.com/owa Checking Your Audio & Video 1. Open Skype. 2. In the left pane, in the top right corner, click on the ellipse (…). 3. Your Settings open. 4. In the left pane, select Audio & Video. 5. In the Camera section your live picture should appear. If it does not, see if there is an option above your picture, and try selecting a different web camera. 6. Scroll down until you see the Audio section. Test your microphone and speakers and adjust the volume as needed. 7. Close the dialog box by clicking the X in the top left corner. Using Skype Once you open Skype, you will select someone to call from the left pane. You have some important options there: Search, Chats, Contacts The first couple times you use Skype you may need to search for your friends and family. You can search by name or email address associated with their Skype account. -

Chapter 2: Windows 7
Chapter 2: Windows 7 When you delete a file, a. A copy of the file will be sent to the desktop b. You send the file to the Recycle Bin. c. The file will not be affected. d. A copy of the file will be stored in your active folder. Which of the following statements is correct about arrange icon on desktop. a. Icons on desktop can be arranged by name. b. Icons on desktop can be arranged by type. c. Icons on desktop can be arranged by size. d. All of the above. Which of the following statements is correct about opening control panel. a. You can open control panel from windows explorer. b. You can open control panel from start menu. c. You can open control panel from my computer. d. All of the above. The documents that is located in start menu store. a. The last 15 files that you have open. b. The last 15 files that you have delete. c. The last 15 files that you have copy. d. None of the above. The desktop is: a. An example of a hardware device. b. A folder. c. A file d. A window. The Shutdown icon on start menu means: a. Close all windows. b. Close the current windows. c. Close your computer. d. None of the above. To open a minimized window, you can click on the:- a. window’s button on the body of the taskbar. b. maximized button on the title bar. c. restore button on the title bar. d. all of the above. -

Laptop Service Guide
Windows Operating System 3 Turn off visual effects 3 Turn off Windows Search Indexing Feature 4 Defragging Hard Drive 5 Step 1: Locating the Defragment Wizard 5 Step 2: Using Defragment Wizard 6 Checking your hard drive 8 Checking your memory 8 Ensure Windows Defender is enabled 9 Perform Disk cleanup to remove clutter 12 Disable Programs that you do not use frequently from starting when system boots 14 14 Perform regular Windows Defender scans on system 15 Uninstall programs that you do not use anymore 17 Regularly turn off your system when not in use 18 How to shut down your windows machine 19 Perform check disk on hard drive regularly 21 Turn Off Windows Tips and Tricks 23 Turn Off Search Indexing 24 Regularly perform backups as well as create restore points 27 Use Powershell to fix corrupt files: 32 Enable fast start-up: 34 Effect of ram on the system 35 2 Windows Operating System Turn off visual effects I. Open the start menu by pressing the Windows key on your keyboard or by clicking on the icon shown below. a. Type “Advanced System Settings” and click on it when it appears in the Menu. b. Navigate to the “Advanced” tab at the top. c. Click on “Settings” in the “Performance” block d. Select “Adjust for best performance”. e. Click “Ok” to finish the setup. 3 Turn off Windows Search Indexing Feature I. Open the start menu by pressing the Windows key on your keyboard or by clicking on the icon shown below. II. Search for “Index” and choose “Indexing Options” when it appears. -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Samsung Galaxy J3 V J327V User Manual
User guide. User guide. User usuario. Guía del Guía GH68-47432D Printed in USA Galaxy J7_COLL-78600-UG-PO-CVR-6x4-V3-F-R2R.indd All Pages 2/2/17 11:00 AM SMARTPHONE User Manual Please read this manual before operating your device and keep it for future reference. Table of Contents Special Features . 1 Navigation . 28 Side Speaker . 2 Entering Text . 30 Getting Started . 3 Multi Window . 33 Set Up Your Device . 4. Emergency Mode . 35 Assemble Your Device . .5 Apps . 37 Start Using Your Device . 10 Using Apps . 38 Set Up Your Device . 11 Applications Settings . 41 Learn About Your Device . .15 Calculator . 45 Front View . 16 Calendar . 46 Back View . .18 Camera and Video . 49 Home Screen . .19 Clock . 54 VZW_J727V_EN_UM_TN_QB1_031717_FINAL Contacts . 57 Connections . 104 Email . 64 Wi‑Fi . 105 Gallery . .67 Bluetooth . 108 Google Apps . 71 Data Usage . 111 Message+ . .74 Airplane Mode . 113 Messages . .77 Mobile Hotspot . .114 My Files . 82 Tethering . 117 Phone . 84 Mobile Networks . 117 S Health . 94 Location . 118 Samsung Gear . 96 Advanced Calling . .119 Samsung Notes . 97 Nearby Device Scanning . .121 Verizon Apps . 99 Phone Visibility . .121 Settings . 101 Printing . .121 How to Use Settings . 102 Virtual Private Networks (VPN) . .121 Change Carrier . 123 Table of Contents iii Data Plan . 123 Smart Alert . 133 Sounds and Vibration . 124 Display . 134 Sound Mode . 125 Screen Brightness . 135 Easy Mute . 125 Screen Zoom and Font . 135 Vibrations . 125 Home Screen . 136 Volume . 126. Easy Mode . 136 Ringtone . .127 Icon Frames . .137 Notification Sounds . 128 Status Bar . .137 Do Not Disturb . 128 Screen Timeout . -

The Complete Guide to Windows 10 Privacy Settings Written by Gavin Phillips
! Copyright © 2016 MakeUseOf. All Rights Reserved ®. ! The Complete Guide to Windows 10 Privacy Settings Written by Gavin Phillips Published October 2016. Read the original article here: http://www.makeuseof.com/tag/complete-guide-windows-10- privacy-settings/ This ebook is the intellectual property of MakeUseOf. It must only be published in its original form. Using parts or republishing altered parts of this ebook is prohibited without permission from MakeUseOf.com. Copyright © 2016 MakeUseOf. All Rights Reserved ®. ! Table of contents General 4 Advertising ID 4 SmartScreen Filter 5 Send Info About Writing 5 Access My Language 5 Let Other Devices Open Apps 5 Let Other Devices Open Apps Using Bluetooth 6 Change Privacy Options Roundup 6 Location 7 Location 7 General Location 7 Default Location 7 Location History 8 Geofencing 8 Location Options Roundup 8 Camera 9 Microphone 10 Notifications 11 Speech, Inking, & Typing 13 Account Info 14 Contacts 15 Calendar 16 Call History 17 Email 18 Messaging 19 Radios 20 Other Devices 21 Sync With Devices 21 Use Trusted Devices 21 Feedback & Diagnostics 22 Feedback Frequency 22 Diagnostic and Usage Data 23 Background Apps 25 Is Windows 10 Still a Privacy Nightmare? 26 Copyright © 2016 MakeUseOf. All Rights Reserved ®. ! The Windows 10 Anniversary Update brought forth an almost staggering number of changes. The update arrived in the first week of August, 2016, and its worldwide roll-out is expected to complete this month. This is a good time to explore the changes to all the Windows 10 privacy settings we’re still learning to live with. What follows is a page-by-page guide of Windows 10 Anniversary Update (referred to as AU forthwith) privacy settings, so you know exactly what to toggle, when to toggle it, and why you’d want to toggle it. -
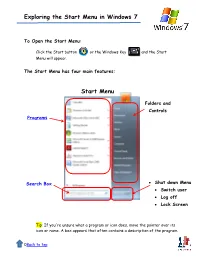
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Ultimate Spider-Man™ README Last Updated: 6/28/05
Ultimate Spider-Man™ README Last Updated: 6/28/05 TABLE OF CONTENTS INTRODUCTION INSTALLATION & SET UP 1. Minimum System Requirements 2. Autoplay 3. DirectX(R) Detection & Installation VIDEO ISSUES 1. Monitors 2. In-game and Desktop Resolutions 3. Graphical Corruption When Changing Video Settings 4. Windowed Mode/Standby Mode 5. Changing Brightness and Contrast GENERAL ISSUES 1. Alt-Tab & Alt-Enter 2. Uninstalling with Antivirus Software Enabled 3. Gamepad Options 4. Invert Controls Setting 5. Options for Lower End Systems INTRODUCTION Refer to this document if you encounter difficulties with one or more aspects of installation or running the Ultimate Spider-Man™ game. Many of the most commonly encountered issues are covered here. INSTALLATION & SET UP 1. Ultimate Spider-Man™ Minimum System Requirements • 3D hardware accelerator card required - 100% DirectX(R) 9.0c-compliant 64 MB video card and drivers* • Microsoft(R) Windows(R) 2000/XP • Pentium(R) III 1.2 GHz or Athlon(TM) 1.2 GHz or higher processor • 256 MB of RAM • 3500 MB of uncompressed hard disk space (plus 400 MB for the Windows(R) swap file) • A 100% Windows(R) 2000/XP - compatible computer system including: • DirectX(R) 9.0c (Included) • 100% DirectX(R) 9.0c-compliant true 16-bit sound card and drivers • 100% Windows(R) 2000/XP - compatible mouse, keyboard and drivers • 100% Windows(R) 2000/XP - compatible quad speed CD-ROM drive (600 K/sec sustained transfer rate) and drivers *Supported Chipsets for Windows 2000/XP All NVIDIA(R) GeForce2(TM) and better chipsets All ATI(R) Radeon 7500(TM) and better chipsets *Important Note: Some 3D accelerator cards with the chipsets listed here may not be compatible with the 3D acceleration features utilized by Ultimate Spider-Man™.