Doo'!D: · 4232698
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Benes Responsible for Loss of Pre-WWII Czech Gold in London
Benes Responsible for Loss of pre-WWII Czech Gold in London Gold not stolen but used by Benes for the Czechoslovak Resistance Army It looks to me from the two documents below that president Benes used the Czech Gold as collateral for a loan from Great Britain for Czechoslovak military operations in the U.K. The article from the U.K. is exactly the opposite to what Jan Kuklik writes in his chapter on p. 188 below. Would make an interesting story ! ! ! Recognition of the Czechoslovak Government in Exile 1939-1942 and its international status Jan Kuklik p. 188 in Prague Papers on History of International Relations, Vol. 1 (1997), pp.173-205 Complete file at: http://usd.ff.cuni.cz/?q=system/files/kuklik.pdf Note: Also check FO 417/41 Å I think that this document is the agreement between Czechoslovak Govt-in-Exile and Great Britain over the Czech Gold. Great Britain and its Eastern European allies 1939-1943: the governments of Poland, Czechoslovakia and Yugoslavia in exile in London from the beginning of the war up to the Tehran Conference Grossbritannien und seine osteuropäischen Alliierten 1939-1943: die Regierungen Polens, der Tschechoslowakei und Jugoslawiens im Londoner Exil vom Kriegsausbruch bis zur Konferenz von Teheran p. 86 Detlef Brandes - 1988 - Preview - More editions 40 - FO 371/24290, C7646/2/12; Roberts an Min. of Information v. 8. 10. 40 - FO 371/24292, 315. Financial Agreement u. Korrespondenz Kingsley Wood m. Outrata v. 10. 12. 40 — FO 417/41, C13060/8893/12; Korrespondenz Treasury (S. D. ... U.K. -

Restitution Policies on Nazi-Looted Art in the Netherlands and the United Kingdom: a Change from a Legal to a Moral Paradigm? Tabitha I
International Journal of Cultural Property (2018) 25:139–178. Printed in the USA. Copyright © 2018 International Cultural Property Society doi:10.1017/S0940739118000103 Restitution Policies on Nazi-Looted Art in the Netherlands and the United Kingdom: A Change from a Legal to a Moral Paradigm? Tabitha I. Oost* Abstract: This article considers the constant tension facing several national panels in their consideration of Nazi spoliation claims concerning cultural objects. It will argue that this tension results from a shift in paradigms in dealing with Nazi-related injustices—from a strictly legal paradigm to a new victim groups- oriented paradigm, where addressing and recognizing the suffering caused by the nature of past crimes is central. While these national panels originate from this new paradigm and embody the new venues found for dealing with Nazi-looted art claims, this paradigm change at the same time presents these panels with a predicament. It seems impossible to abandon the legalist paradigm completely when remedying historical injustices in the specific category of cultural objects. Through a comparison between the Dutch and United Kingdom (UK) systems, this article will illustrate from both an institutional and substantive perspective that these panels seem to oscillate between policy-based, morality-driven proceedings (new paradigm) and a legal emphasis on individual ownership issues and restitution in kind (old paradigm). This article addresses this tension in order to provide insights on how we could conceptually approach and understand current restitution cases concerning Nazi-looted art in the Netherlands and the UK. Keywords: looted art, restitution, WW II, reparations, restitution committees, ADR *Department of Constitutional and Administrative Law, University of Amsterdam, The Netherlands; Email: [email protected]. -

History of Nazi Dental Gold: from Dead Bodies Till Swiss Bank
SAJ Forensic Science Volume 1 | Issue 1 www.scholarena.com Research Article Open Access History of Nazi Dental Gold: From Dead Bodies till Swiss Bank Riaud X* Doctor in Dental Surgery, PhD in History of Sciences and Techniques, Winner and Associate Member of the National Academy of Dental Surgery, Member of the National Academy of Surgery, France *Corresponding author: Riaud X, Doctor in Dental Surgery, PhD., in History of Sciences and Techniques, Winner [email protected] and Associate Member of the National Academy of Dental Surgery, Member of the National Academy of Surgery, 145,Citation: route de Vannes, 44800 Saint Herblain, France, Tel: 0033240766488, E-mail: A R T I C RiaudL E I XN (2015) F O History of NaziA DentalB S T Gold: R A CFrom T Dead Bodies till Swiss Bank. SAJ Forensic Sci 1: 105 Article history: The SS Reichsfürher Heinrich Himmler, on the 23rd of September 1940 gave the Received: 02 May 2015 SS doctors orders to collect the golden teeth in the mouth of the dead. Everybody knows that. But, who Accepted: 27 May 2015 knows who were the SS dentists directly implicated in that collection, the real Published: 29 May 2015 figures, how Nazis proceeded? Here are the answers. For the first time. Keywords: History; Dentistry; WWII; Dental gold Introduction rd of September 1940 gave the SS doctors orders to collect the golden teeth in the mouth of the dead, and also “the golden teeth that cannot be repaired”, from the mouth of the people alive. This decree,- The SS that Reichsfürher was part of Heinrich the T4 Operation, Himmler, onwas the not 23 systematically put into practice on the concentration camps prisoners. -

Nazi Bank and Financial Institutions: U.S
http://gdc.gale.com/archivesunbound/ NAZI BANK AND FINANCIAL INSTITUTIONS: U.S. MILITARY GOVERNMENT INVESTIGATION REPORTS AND INTERROGATIONS OF NAZI FINANCIERS, 1945-1949 This publication comprises two collections related to Holocaust Era Assets. The first includes Records Regarding Bank Investigations and Records Relating to Interrogations of Nazi Financiers, from the records of the Office of the Finance Division and Finance Advisor in the Office of Military Government, U.S. Zone(Germany) (OMGUS), during the period 1945-1949. The second comprises Records Regarding Intelligence and Financial Investigations, 1945-1949, from the Records of the Financial Intelligence Group, Office of the Finance Adviser. These collections consist of memorandums, letters, cables, balance sheets, reports, exhibits, newspaper clippings, and civil censorship intercepts on: the financing of the German war effort and German financial institutions; reports on Nazi gold, the use of Swiss banks, and links between German and Swiss banks, inclusive of Commerzbank, Deutsche Bank, Deutsche Golddiskontbank, Dresdner Bank, and Reichs-Kredit-Gesellschaft; information regarding Aryanization, bank operations outside of Germany, industrial ties, liquidation proposals, and the restitution of Hungarian property; records concerning agricultural cooperatives; denazification of German finance personnel; an interrogation report of Hjalmar Schacht, the former Reichsminister of Economics and Plenipotentiary for the War Economy; a report on the operations of I.G. Farben AG; plans for the seizure of Reich ministerial records called "Operation Goldcup"; information relating to fiscal conditions in former German-occupied countries; report of banking in the Soviet Zone; documentation on investigations of Bernhard Berghaus, Alois Alzheimer, August von Finck, Eduard Hilgard, Kurt Schmitt, and Franz Schwede-Coburg; and, files relating to Carlowitz & Company and Japanese firms operating in Germany. -

Final Report of the Nazi War Crimes & Japanese
Nazi War Crimes & Japanese Imperial Government Records Interagency Working Group Final Report to the United States Congress April 2007 Nazi War Crimes and Japanese Imperial Government Records Interagency Working Group Final Report to the United States Congress Published April 2007 1-880875-30-6 “In a world of conflict, a world of victims and executioners, it is the job of thinking people not to be on the side of the executioners.” — Albert Camus iv IWG Membership Allen Weinstein, Archivist of the United States, Chair Thomas H. Baer, Public Member Richard Ben-Veniste, Public Member Elizabeth Holtzman, Public Member Historian of the Department of State The Secretary of Defense The Attorney General Director of the Central Intelligence Agency Director of the Federal Bureau of Investigation National Security Council Director of the U.S. Holocaust Memorial Museum Nationa5lrchives ~~ \T,I "I, I I I"" April 2007 I am pleased to present to Congress. Ihe AdnllniSlr:lllon, and the Amcncan [JeOplc Ihe Final Report of the Nazi War Crimes and Japanese Imperial Government Rcrords Interagency Working Group (IWG). The lWG has no\\ successfully completed the work mandated by the Nazi War Crimes Disclosure Act (P.L. 105-246) and the Japanese Imperial Government DisdoSUTC Act (PL 106·567). Over 8.5 million pages of records relaH:d 10 Japanese and Nazi "'ar crimes have been identifIed among Federal Go\emmelll records and opened to the pubhc. including certam types of records nevcr before released. such as CIA operational Iiles. The groundbrcaking release of Lhcse ft:cords In no way threatens lhe Malio,,'s sccurily. -

426Fa2e023.Pdf
Volume 1 of 2 FOR PUBLICATION UNITED STATES COURT OF APPEALS FOR THE NINTH CIRCUIT EMIL ALPERIN; JEWGENIJA ROMANOVA; MARIA DANKEWITSCH; VLADIMIR MORGUNOV, on behalf of themselves and all other persons similarly situated; ORGANIZATION OF UKRAINIAN ANTIFASCIST RESISTANCE FIGHTERS; UKRAINIAN UNION OF NAZI VICTIMS AND PRISONERS; VLADIMIR BRODICH; WILLIAM DORICH; IGOR NAJFELD, on behalf of themselves and all other persons similarly No. 03-15208 situated; LIZABETH LALICH; MLADEN DJURICICH; ROBERT PREDRAG D.C. No. GAKOVICH; NEVENKA VUKASOVIC CV-99-04941-MMC MALINOWSKI; ELI ROTEM; MILORAD SKORIC; VELJKO MILJUS; FRED ZLATKO HARRIS; MILJA CONGER; ALLEN DOLFI HERSKOVICH; BOGDAN KLJAIC; DAVID LEVY; ZDENKA BAUM RUCHWARGER; VLADAN CELEBONOVIC; DESA TOMASEVIC WAKEMAN; DANIEL PYEVICH; KOVILJKA POPOVIC; JASENOVAC RESEARCH INSTITUTE; THE INTERNATIONAL UNION OF FORMER 4257 4258 ALPERIN v. VATICAN BANK JUVENILE PRISONERS OF FASCISM OF UKRAINE, RUSSIA, AND BELARUS, on behalf of themselves and all others similarly situated, Plaintiffs-Appellants, v. VATICAN BANK, aka Institute of Religious Works aka Instituto per le Opere Di Religione (IOR); FRANCISCAN ORDER (OFM), INCLUDING CROATIAN FRANCISCANS; CROATIAN COFRATERNITY OF THE COLLEGE OF SAN GIROLAMO DEGLI ILLIRICI, and its successors, Swiss, Austrian, Argentine, Spanish, Italian, Portuguese, Vatican & German Banking Institutions; CROATIAN LIBERATION MOVEMENT (HOP), Defendants-Appellees. EMIL ALPERIN; JEWGENIJA ROMANOVA; MARIA DANKEWITSCH; VLADIMIR MORGUNOV, on behalf of themselves and all other persons -

The Disposition of SS-Looted Victim Gold During and After World War II Elizabeth White
American University International Law Review Volume 14 | Issue 1 Article 15 1998 The Disposition of SS-Looted Victim Gold During and After World War II Elizabeth White Follow this and additional works at: http://digitalcommons.wcl.american.edu/auilr Part of the International Law Commons Recommended Citation White, Elizabeth. "The Disposition of SS-Looted Victim Gold During and After World War II." American University International Law Review 14, no. 1 (1998): 213-224. This Article is brought to you for free and open access by the Washington College of Law Journals & Law Reviews at Digital Commons @ American University Washington College of Law. It has been accepted for inclusion in American University International Law Review by an authorized administrator of Digital Commons @ American University Washington College of Law. For more information, please contact [email protected]. THE DISPOSITION OF SS-LOOTED VICTIM GOLD DURING AND AFTER WORLD WAR II ELIZABETH B. WHITE When United States forces entered the Kaiseroda salt mines near Merkers, Germany in April 1945, they discovered the vast treasure hidden there by the Reichsbank, Germany's central bank. In one cor- ner of the mines, separate from the Reichsbank's stocks of gold, cur- rency, and securities, were 207 suitcases, sacks, and boxes that, when opened, were found to contain thousands of pounds of valuable per- sonal items, including jewelry, wedding rings, watches, eyeglass frames, and gold teeth and dental fillings. A Reichsbank official captured with the Merkers treasure revealed that this separate cache represented loot that the SS had robbed from its victims at the con- centration camps and the killing centers in Poland. -

Restitution of Jewish Property in the Czech Republic
Loyola of Los Angeles International and Comparative Law Review Volume 41 Number 3 Article 17 Winter 2018 Restitution of Jewish property in the Czech Republic Jan Kuklik Follow this and additional works at: https://digitalcommons.lmu.edu/ilr Recommended Citation Jan Kuklik, Restitution of Jewish property in the Czech Republic, 41 Loy. L.A. Int'l & Comp. L. Rev. 583 (2019). Available at: https://digitalcommons.lmu.edu/ilr/vol41/iss3/17 This Article is brought to you for free and open access by the Law Reviews at Digital Commons @ Loyola Marymount University and Loyola Law School. It has been accepted for inclusion in Loyola of Los Angeles International and Comparative Law Review by an authorized administrator of Digital Commons@Loyola Marymount University and Loyola Law School. For more information, please contact [email protected]. FINAL TO JCI (DO NOT DELETE) 12/12/2018 6:29 PM Restitution of Jewish Property in the Czech Republic JAN KUKLÍK Restitution of the property confiscated during the communist regime was debated in Czechoslovakia almost immediately after the so-called Velvet Revolution of 1989. The period of transition from the authoritarian communist regime into a democratic system started with discussions about adequate policies to be implemented as not many patterns to follow were available at that time in order to carry out political, economic and social changes.1 The first changes concentrated mainly on the political system and economy. The political and economic leaders of the new democratic Czechoslovak government decided -

Filming the End of the Holocaust War, Culture and Society
Filming the End of the Holocaust War, Culture and Society Series Editor: Stephen McVeigh, Associate Professor, Swansea University, UK Editorial Board: Paul Preston LSE, UK Joanna Bourke Birkbeck, University of London, UK Debra Kelly University of Westminster, UK Patricia Rae Queen’s University, Ontario, Canada James J. Weingartner Southern Illimois University, USA (Emeritus) Kurt Piehler Florida State University, USA Ian Scott University of Manchester, UK War, Culture and Society is a multi- and interdisciplinary series which encourages the parallel and complementary military, historical and sociocultural investigation of 20th- and 21st-century war and conflict. Published: The British Imperial Army in the Middle East, James Kitchen (2014) The Testimonies of Indian Soldiers and the Two World Wars, Gajendra Singh (2014) South Africa’s “Border War,” Gary Baines (2014) Forthcoming: Cultural Responses to Occupation in Japan, Adam Broinowski (2015) 9/11 and the American Western, Stephen McVeigh (2015) Jewish Volunteers, the International Brigades and the Spanish Civil War, Gerben Zaagsma (2015) Military Law, the State, and Citizenship in the Modern Age, Gerard Oram (2015) The Japanese Comfort Women and Sexual Slavery During the China and Pacific Wars, Caroline Norma (2015) The Lost Cause of the Confederacy and American Civil War Memory, David J. Anderson (2015) Filming the End of the Holocaust Allied Documentaries, Nuremberg and the Liberation of the Concentration Camps John J. Michalczyk Bloomsbury Academic An Imprint of Bloomsbury Publishing Plc LONDON • OXFORD • NEW YORK • NEW DELHI • SYDNEY Bloomsbury Academic An imprint of Bloomsbury Publishing Plc 50 Bedford Square 1385 Broadway London New York WC1B 3DP NY 10018 UK USA www.bloomsbury.com BLOOMSBURY and the Diana logo are trademarks of Bloomsbury Publishing Plc First published 2014 Paperback edition fi rst published 2016 © John J. -

Holocaust Restitution, the United States Government, and American Industry Michael J
Brooklyn Journal of International Law Volume 28 | Issue 3 Article 2 2002 Trading With The neE my: Holocaust Restitution, the United States Government, and American Industry Michael J. Bazyler Amber L. Fitzgerald Follow this and additional works at: https://brooklynworks.brooklaw.edu/bjil Recommended Citation Michael J. Bazyler & Amber L. Fitzgerald, Trading With The Enemy: Holocaust Restitution, the United States Government, and American Industry, 28 Brook. J. Int'l L. (2003). Available at: https://brooklynworks.brooklaw.edu/bjil/vol28/iss3/2 This Article is brought to you for free and open access by the Law Journals at BrooklynWorks. It has been accepted for inclusion in Brooklyn Journal of International Law by an authorized editor of BrooklynWorks. File: BAZYLER Base Macro Final_2.doc Created on: 6/24/2003 12:17 PM Last Printed: 1/13/2004 2:22 PM TRADING WITH THE ENEMY: HOLOCAUST RESTITUTION, THE UNITED STATES GOVERNMENT, AND AMERICAN INDUSTRY Michael J. Bazyler∗ & Amber L. Fitzgerald∗∗ I. INTRODUCTION……………………………………………………685 II. THE ROLE OF THE UNITED STATES IN RESTITUTION EFFORTS ABROAD…………………………………………………………...686 A. Switzerland………...……………………………………….689 B. Germany..…………………………………………………...690 C. France......…………………………………………………...697 D. Austria………………..……………………………………..699 E. Israel……………………………...………………………….700 F. Insurance Claims…………………………………………..702 G. Art……………………………………………………………709 H. Role of Historical Commissions..………………………..712 1. Switzerland…………………………………………….712 a. Volcker Report……………………………………713 b. Bergier Final Report…………………………….715 2. Germany………………………………………………..719 3. Austria………………………………………………….720 4. France…………………………………………………..721 5. Other Countries……………………………………….723 ∗ Professor of Law, Whittier Law School, Costa Mesa, California; Fellow, Center for Advanced Holocaust Studies, U.S. Holocaust Memorial Museum (“USHMM”), Washington, D.C.; Research Fellow, Holocaust Educational Trust, London, England; J.D., University of Southern California, 1978; A.B., University of California, Los Angeles, 1974. -

US Interagency Report on US and Allied
American University International Law Review Volume 14 | Issue 1 Article 8 1998 U.S. Interagency Report on U.S. and Allied Wartime and Post Postwar Relations and Negotiations with Argentina, Portugal, Spain, Sweden, and Turkey on Looted Gold and German External Assets William Z. Slany Follow this and additional works at: http://digitalcommons.wcl.american.edu/auilr Part of the International Law Commons Recommended Citation Slany, William Z. "U.S. Interagency Report on U.S. and Allied Wartime and Post Postwar Relations and Negotiations with Argentina, Portugal, Spain, Sweden, and Turkey on Looted Gold and German External Assets." American University International Law Review 14, no. 1 (1998): 147-153. This Article is brought to you for free and open access by the Washington College of Law Journals & Law Reviews at Digital Commons @ American University Washington College of Law. It has been accepted for inclusion in American University International Law Review by an authorized administrator of Digital Commons @ American University Washington College of Law. For more information, please contact [email protected]. U.S. INTERAGENCY REPORT ON U.S. AND ALLIED WARTIME AND POSTWAR RELATIONS AND NEGOTIATIONS WITH ARGENTINA, PORTUGAL, SPAIN, SWEDEN, AND TURKEY ON LOOTED GOLD AND GERMAN EXTERNAL ASSETS WILLIAM Z. SLANY" INTRODUCTION .............................................. 147 L SPAIN'S COMMISSION ................................... 148 II. SWEDEN'S COMMISSION ................................ 149 III. SWITZERLAND'S INDEPENDENT COMMISSION ....... 150 IV. THE UNITED STATES REPORT ........................... 151 INTRODUCTION Over the last two years, there has been an extraordinary amount of historical research and writing done on the subject of Nazi Gold. Nazi Gold includes not only the fate of monetary gold looted by Nazi Germany from the wartime captive nations of conquered Europe, but also the gold and other valuables stolen from the individual victims of the Nazis, as well as the postwar disposition of the overseas assets of the German government and citizens. -
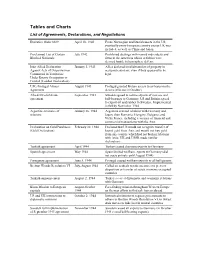
Tables and Charts List of Agreements, Declarations, and Negotiations
Tables and Charts List of Agreements, Declarations, and Negotiations Executive Order 8389 April 10, 1940 Froze Norwegian and Danish assets in the US; eventually every European country except UK was included, as well as China and Japan Proclaimed List of Certain July 1942 Prohibited dealings with named individuals and Blocked Nationals firms in the Americas whose activities were deemed hostile to hemisphere defense Inter-Allied Declaration January 5, 1943 Allies declared invalid transfers of property in Against Acts of Dispossession occupied countries, even if they appeared to be Committed in Territories legal Under Enemy Occupation or Control (London Declaration) U.K.-Portugal Azores August 1943 Portugal granted Britain access to air bases on the Agreement Azores (effective in October) Allied-Swedish trade September 1943 Sweden agreed to reduce exports of iron ore and agreement ball-bearings to Germany; US and Britain agreed to export oil and rubber to Sweden. Implemented in full by November 1944 Argentine severance of January 26, 1944 Argentina severed relations with Germany and relations Japan, then Romania, Hungary, Bulgaria, and Vichy France, including severance of financial and commercial transactions with the Axis Declaration on Gold Purchases February 22, 1944 Declared that US would not recognize transfer of (Gold Declaration) looted gold from Axis and would not buy gold from any country which had not broken relations with Axis; UK and USSR made similar declarations Turkish agreement April 1944 Turkey ceased chromite exports to